当前位置:网站首页>The second round of Yunnan Cyberspace Security competition in May 2021
The second round of Yunnan Cyberspace Security competition in May 2021
2022-06-25 17:09:00 【Chinese cabbage is a real dish】
2021 year 5 In June, the title of Yunnan Cyberspace Security skill competition was reproduced .
Task a 、SSH Weak password penetration test
Mission environment description :
ü Server scenario :Linux
ü Server scenario operating system :Linux( Version unknown )
1. In the local PC Penetration testing platform BT5 Use in zenmap Tool scan server scenario Linux Network segment ( for example :172.16.101.0/24) Live hosts in range IP Address and designated open 21、22、23 port . And take the string that must be added in the command used by this operation as FLAG Submit ( Ignore ip Address );
Direct use nmap scanning
flag=-p21,22,23
2. Via local PC Medium penetration test platform BT5 For the server scenario Linux Conduct system service and version scanning penetration test , And display the operation in the result SSH The service port information corresponding to the service is used as FLAG Submit ;
nmap -sV 192.168.19.75
flag=22/tcp
3. In the local PC Penetration testing platform BT5 Use in MSF The module explodes it , Use search command , The name information of the scanning weak password module is used as FLAG Submit ;
flag=search mssql_login
4. On the basis of the previous question, use the command to call the module , And view the information to be configured ( Use show options command ), The target address to be configured in the echo will be displayed , Password guessing Dictionary , Threads , The fields of account configuration parameters are used as FLAG Submit ( Separated by commas , example hello,test,…,…);
flag=rhosts,pass_file,threads,username
5. stay msf Configure the target aircraft in the module IP Address , Use the first two words in the configuration command as FLAG Submit ;
flag=set rhosts
6. stay msf Specify the password dictionary in the module , The dictionary path is /root/2.txt, The user is called test Obtain the password and use the obtained password as FLAG Submit ;
Directly use the dictionary at the game site for blasting , Use set Specify the parameters , direct run Just go .
7. On the basis of the previous question , Use the 6 The obtained password SSH To the target , take test The only suffix in the user's home directory is .bmp The string of the file name of the picture is used as FLAG Submit .
readily solved
Task 2 : Data analysis ack Data packets
1. From the target server FTP Upload and download attack pcapng Package file , By analyzing the data package attack pcapng, Find the hacker's IP Address , And put the hacker's IP Address as FLAG ( form : [IP Address ]) Submit ; (1 branch )
flag:[192.168.8.126]
2. Continue to view the package file attack.pacapng, Analyze the open port of the target scanned by the hacker , Use the open port of the target as FLAG ( form : [ Port name 1, Port name 2. Port name 3… , Port name n]) From low to high ; (1 branch )
flag:[21]
3. Continue to view the package file attack pacapng, Analyze the version number of the operating system obtained after the hacker's successful intrusion , Take the version number of the operating system as FLAG ( form : [ Operating system version number ]) Submit ; (1 branch )
flag:[ anonymous]
4. Continue to view the package file attack pacapng, Analyze the first command executed by the hacker after successful intrusion , And take the first command executed as FLAG ( form : [ The first - Bar command ]) Submit ; (1 branch )
flag:[admin]
5. Continue to view the package file attack.pacapng, Analyze the second command executed by the hacker after successful intrusion , And execute the second command as FLAG ( form : [ The second order ]) Submit ; (2 branch )
flag:[put one.asp]
6. Continue to view the package file attack pacapng, Analyze the return result of the second command executed by the hacker after successful intrusion , And return the result of the second command as FLAG ( form : [ The second command returns the result ]) Submit ; (2 branch )
flag:[Microsof-1IS/7.5]
7. Continue to view the package file attack .pacapng, Analyze the return result of the third command executed after the hacker's successful intrusion , And return the result of the third command as FLAG ( form : [ The third command returns the result ]) Submit .(2 branch )
flag:[Tomorrow]
Task three : Comprehensive penetration test
The main content is to use the Trojan horse to raise the right to obtain the host Shell,
General idea : Login backstage ,msf Generate php Ma rebound to get system permission .
I forgot when I was playing msf Generate php Horse orders ,, Purring
Task 4 :Web penetration
page 1,,,f12 Take it directly flag
page 2,,, See the login box ,,' Wrong number ,, direct nmap Tuoku ,, Get flag.
page 3,,XFF forge IP Local access ...
page 4,, I can't remember ,,, It's simple
front 4 Little topic ,, It's all foundation ,, It's simple .
Page five ,,,,/file=text.txt,,, The problem didn't work out
Scuffle stage
a Linux
to open up 21 22 23 80 3306 port ...
Sweep it out ,,,21 ——>> VSFTPD234 Smiley loopholes exist ..
2.txt Universal Dictionary ( Relatively more ,, Take it to explode ssh and ftp Should be able to explode )
password.txt Dictionaries ...
Phase II summary : Be sure to change the virtual machine configuration , Or you'll get stuck in doubt about life !!!
边栏推荐
- 社交电商如何运营推广?
- 效应与定律
- Babbitt yuan universe daily recommendation: three players holding "tens of millions" of collections have revealed the "three routines" of the digital collection market
- App测试工具大全,收藏这篇就够了
- PLSQL 存储函数SQL编程
- 剑指 Offer II 012. 左右两边子数组的和相等
- 3. conditional probability and independence
- How to talk about salary correctly in software testing interview
- TCP聊天+传输文件服务器服务器套接字v2.8 - 修复已知程序4个问题
- Pytorch official document learning record
猜你喜欢
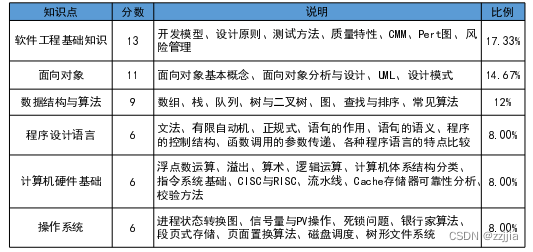
Which is better for intermediate and advanced soft exam?

2022-06-17 advanced network engineering (IX) is-is- principle, NSAP, net, area division, network type, and overhead value
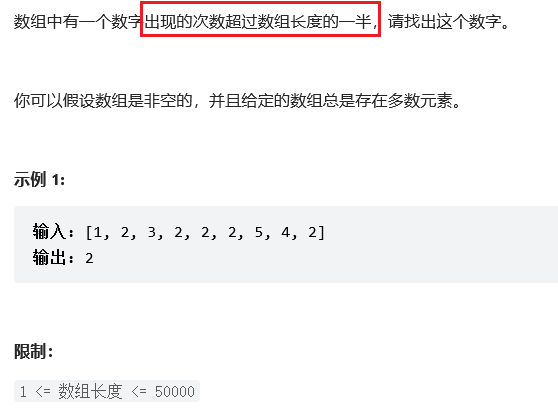
Sword finger offer 39 Numbers that occur more than half the time in the array

Do you know all the configurations of pychrm?

Difference between app test and web test

六大专题全方位优化,阿里巴巴性能优化小册终开源,带你直抵性能极致

软考中的嵌入式系统设计师为什么考的人少?

2022-06-17 网工进阶(十)IS-IS-通用报头、邻接关系的建立、IIH报文、DIS与伪节点
Uncover ges super large scale graph computing engine hyg: Graph Segmentation

How did I get a salary increase of 13k+ after one year of employment?
随机推荐
Redis系列——概述day1-1
通过深度可分离卷积神经网络对七种表情进行区分
How do components communicate
[Jianzhi offer II 091. painting the house]
从业一年,我是如何涨薪13K+?
Notes: lbcf: a Large Scale budget Constrained causal Forest Algorithm
软件测试面试如何正确谈薪
剑指 Offer II 012. 左右两边子数组的和相等
组件通讯的方式有哪些
Kalman time series prediction
Kalman filter meets deep learning: papers on Kalman filter and deep learning
微信公众号服务器配置
Sword finger offer II 025 Adding two numbers in a linked list
try with resource
Wireshark network card cannot be found or does not display the problem
千万级购物车系统缓存架构方案
Problems encountered in using MySQL
知道这些面试技巧,让你的测试求职少走弯路
PLSQL storage function SQL programming
Home office earned me C | community essay