当前位置:网站首页>Super scientific and technological data leakage prevention system, control illegal Internet behaviors, and ensure enterprise information security
Super scientific and technological data leakage prevention system, control illegal Internet behaviors, and ensure enterprise information security
2022-07-29 01:45:00 【Super technology】

Internet security incidents occur frequently , Leaks are getting worse . According to statistics ,80% Every year, enterprises in have leaked secrets , Mostly caused by internal , What's more terrible is when there is a crisis , The enterprise is not aware of , Leading to heavy losses of the enterprise . Enterprises must pay attention to data security , Only by fundamentally solving data security can we make development worry free !
Serious harm caused by data leakage
Direct loss of money
Bank accounts and passwords were stolen , Cause economic losses ;
Missed business opportunities
Creative achievements are patented by others, and key customers are lost ;
Damage corporate image
The company fell into a crisis of trust, causing immeasurable losses ;
Loss of customer trust
Lead to the failure of bidding, termination of cooperation and even compensation for losses .
The super scientific and technological data leakage prevention system strictly checks and controls the leakage channels of sensitive data of enterprises , Strengthen sensitive data in creation 、 Storage 、 Use 、 Security management throughout the life cycle of transmission and destruction , Prevent leakage 、 Audit suspected leaks , Protect the overall data security of the enterprise , Provide situation analysis and intelligent control support .
service content

Deep content recognition , Sharp behavioral perception
Based on deep content recognition technology and leading AI technology , Support 1000+ Document type and 30+ Image format recognition 、300+ Document content extraction , Support encryption 、 Compression and compression nesting behavior 、 Identification of data leakage behaviors such as a small amount of multiple data leakage .
Comprehensive flow monitoring , Rapid leak response
Based on the monitoring of data transmission process, draw a comprehensive data flow map , And support the visual display of various elements , Such as the distribution of sensitive data of different types and levels 、 Data transmission mode 、 Data sources IP、 Purpose IP etc. . According to the comprehensive monitoring , Take prompt protective measures against the leakage of sensitive information that violates the security policy , The use of sensitive data 、 Security incidents 、 Audit and analyze the implementation of strategies .
Realize the security protection of terminal data
Illegal use of sensitive data 、 Send, etc. for policy control , The terminal monitors the operation of sensitive data , Ensure the compliant use of terminal sensitive data .
Realize the security protection of stored data
For storage in services 、 database 、 Scan structured and unstructured data in the repository , According to the strategy discovery , Recording sensitive data , And alarm for illegal storage events 、 Isolation etc. , Realize the classification and hierarchical management of sensitive data in storage .
Realize the security protection of network transmission data
Identify at the network exit or security domain boundary 、 Control sensitive data in transmission , Control or monitor by mail 、WEB、FTP Wait for the network protocol to transmit sensitive data . Provide data service interface compliance audit and sensitive data disclosure audit functions , It can be connected with big data and other platforms , Realize data security protection in the platform .
Protect core assets , Provide basis for compliance audit
Define sensitive information of enterprises and institutions , Formulate monitoring and protection strategies for different levels of confidential information , Multidimensional sensitive data detection , Prevent the disclosure of confidential information , Provide relevant basis for internal compliance management and audit , Provide information based on compliance audit , Easily respond to the requirements of the audit department .
Application scenarios

Business owners or executives
Free open 、 see 、 Edit encrypted document , Send it out in clear text so that customers can't view it .
division manager
Forced encryption of sensitive data , Non sensitive and private data are not encrypted , Keep a certain degree of freedom .
Classified employees
Sensitive data must be forcibly encrypted , It can be viewed normally 、 edit 、 Encrypt documents .
Ordinary employees
No sensitive data , No encryption required , Due to the need of work , You need to check the encrypted documents of other departments .
边栏推荐
- Redis installation, cluster deployment and common tuning
- 一文读懂Okaleido Tiger近期动态,挖掘背后价值与潜力
- Comprehensive upgrade, all you can imagine is here -- JD API interface
- Plato launched the LAAS protocol elephant swap, which allows users to earn premium income
- Openpyxl merge cells
- Three ways of creating indexes in MySQL
- OpenGL development with QT (II) drawing cube
- Sigma-DSP-OUTPUT
- Canal real-time parsing MySQL binlog data practice
- els 新的方块落下
猜你喜欢

Openpyxl border
![A ten thousand word blog post takes you into the pit. Reptiles are a dead end [ten thousand word pictures]](/img/aa/a5e7b4516aa395f8d4d0e2eee7d3c7.png)
A ten thousand word blog post takes you into the pit. Reptiles are a dead end [ten thousand word pictures]

PLATO上线LAAS协议Elephant Swap,用户可借此获得溢价收益
![[search] - iteration deepening / bidirectional dfs/ida*](/img/88/d460276a657cfc49eff10015c29e5d.png)
[search] - iteration deepening / bidirectional dfs/ida*

跨模态对齐 20220728

【GoLang】同步锁 Mutex

HCIA configuration instance (ENSP)

mysql的执行顺序
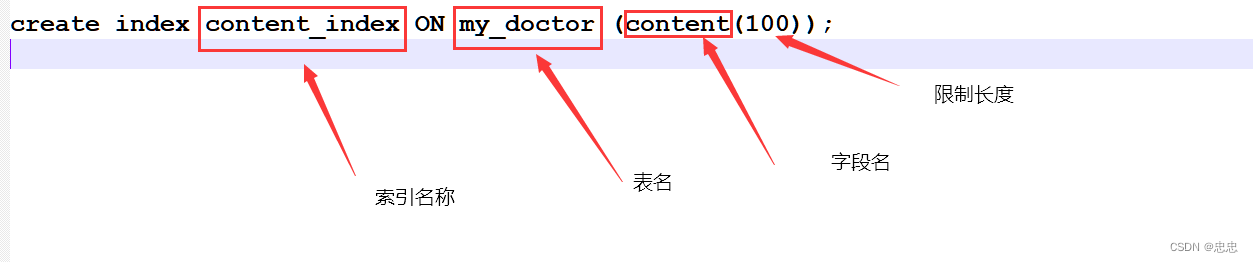
Three ways of creating indexes in MySQL
Docker compose install MySQL
随机推荐
ELS new box falls
Understand various paths
The brutal rule of blackmail software continues, and attacks increase by 105%
JS事件简介
Canal real-time parsing MySQL binlog data practice
代码生成器
ELS square movement
SQL question brushing: find the last of all employees who have been assigned departments_ Name and first_ Name and Dept_ no
Plato launched the LAAS protocol elephant swap, which allows users to earn premium income
了解网址url的组成后 运用url模块、querystring模块和mime模块完善静态网站
Timer of BOM series
J9 number theory: what factors determine the value of NFT?
[SQL's 18 dragon subduing palms] 01 - Kang long regrets: introductory 10 questions
560 和为 K 的子数组
BOM系列之定时器
After understanding the composition of the URL of the website, we use the URL module, querystring module and mime module to improve the static website
Comprehensive upgrade, all you can imagine is here -- JD API interface
Analyze OP based on autoware_ global_ Planner global path planning module re planning
Ruiji takeout project actual battle day01
[机缘参悟-54]:《素书》-1-事物缘起[原始章第一]:大道至简。