当前位置:网站首页>Basic use of Metasploit penetration testing framework
Basic use of Metasploit penetration testing framework
2022-07-03 04:48:00 【m0_ forty-eight million two hundred and ninety-four thousand tw】
1.Metasploit System framework
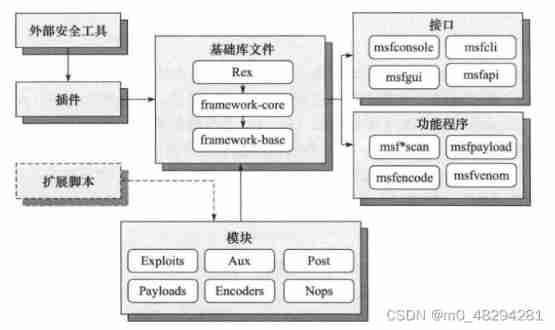
1、 Base library : metasploit The basic library file is located in the root directory of the source code libraries Directory , Include Rex,framework-core and framework-base In the third part of .
Rex It is the most basic components that the whole framework depends on , Such as wrapped network socket 、 Implementation of network application protocol client and server 、 Log subsystem 、 Penetration attack support routines 、PostgreSQL as well as MySQL Database support, etc ;
framework-core The library is responsible for realizing all the interactive interfaces with various types of upper modules and plug-ins ;
framework-base The library has expanded framework-core, Provide simpler packaging routines , It also provides some function classes for dealing with the functions of all aspects of the framework , It is used to support the user interface and function program to call the function of the framework itself and the framework integration module ;
2、 modular : Module organization is divided into... According to different purposes 6 Types of modules (Modules):
Divided into auxiliary modules (Aux)、 Penetration attack module (Exploits)、 Post penetration attack module (Post)、 Attack load module (payloads)、 Encoder module (Encoders)、 Empty instruction module (Nops).
notes : payload Also known as attack payload , It is mainly used to establish a stable connection between the target machine and the attacker , You can go back to shell, Program injection can also be carried out .
3、 plug-in unit : Plug-ins can extend the functions of the framework , Or assemble components with existing functions to form advanced features . The plug-in can integrate some existing external security tools , Such as Nessus、OpenVAS Vulnerability scanner, etc , Provide some new functions for the user interface .
4、 Interface : Include msfconsole Control terminal 、msfcli Command line 、msfgui Graphical interface 、armitage Graphical interface and msfapi Remote call interface .
5、 Function program : metasploit It also provides a series of functional programs that can be run directly , Support penetration testers and security personnel to quickly use metasploit The ability within the framework to accomplish some specific tasks . such as msfpayload、msfencode and
msfvenom The attack payload can be encapsulated as an executable 、C Language 、JavaScript Language and other forms , And can carry out various types of coding .
The software directory is located in :
data: Metasploit Editable files used
documentation: Provide documentation for the framework
lib: Framework code base
modules: Actually MSF modular
plugins: Plugins that can be loaded at run time
scripts: Meterpreter And other scripts
tools: Various useful command line tools
Open the module and you can see the following , If you are interested, you can check the contents of each folder :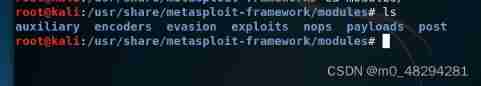
2. Drone aircraft
Target link :
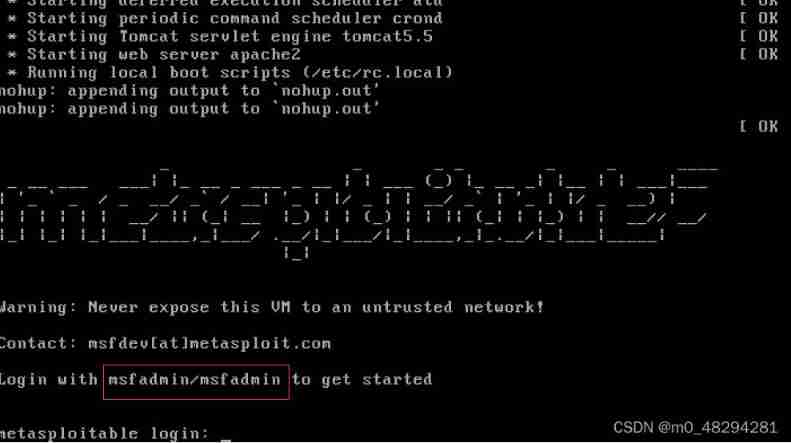
After using the virtual machine to open , Set the network to bridge mode , Login account password
For the convenience of modifying the configuration file , Modify... After login root Account password :
sudo passwd rootSwitch to root Account
su root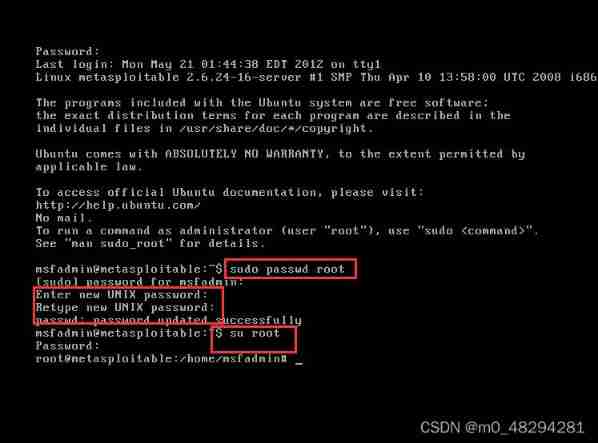
Target's IP No settings , Because the network is a bridge mode , You can use it directly , It will automatically get used ifconfig see :

2.Metasploit Use
Metasploit The program needs to use Postgresql database .
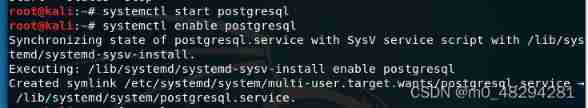
First, in the kali Open the database and set the database to start automatically
systemctl start postgresql
systemctl enable postgresql
 Then initialize the database :
Then initialize the database :
msfdb init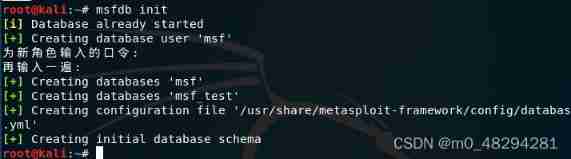
Turn on Metasploit, You can directly use the program to open , You can also use the command line msfconsole open :
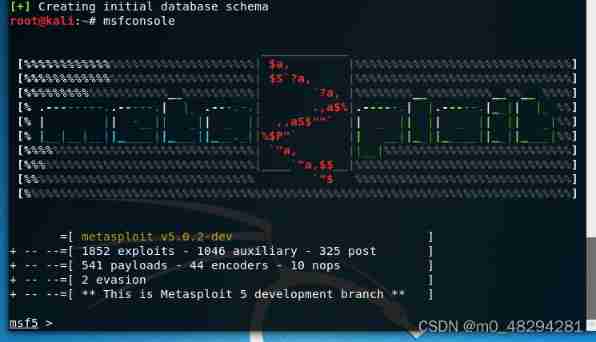
Check it out help
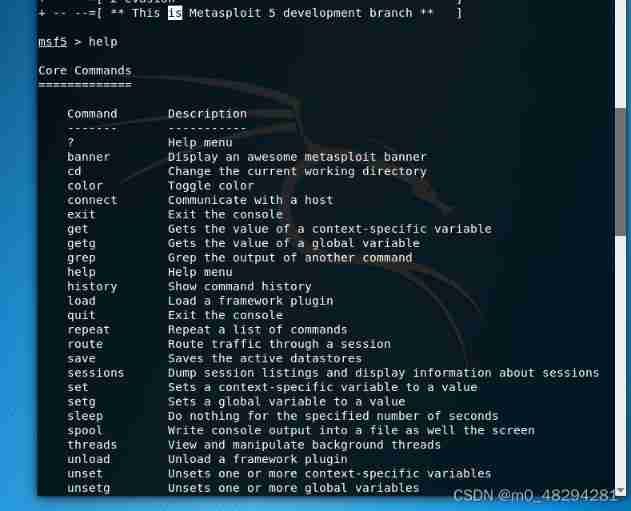
Core Commands # Core command
Module Commands# Module command
Job Commands# Background task command
Resource Script Commands# Resource script command
Database Backend Commands# Database backend command
Credentials Backend Commands# certificate / Voucher backend command
Developer Commands# Developer commands
边栏推荐
- Market status and development prospects of the global IOT active infrared sensor industry in 2022
- 第十九届浙江省 I. Barbecue
- C Primer Plus Chapter 10, question 14 3 × 5 array
- Employee attendance management system based on SSM
- Integration of Android high-frequency interview questions (including reference answers)
- Contents of welder (primary) examination and welder (primary) examination in 2022
- 论文阅读_ICD编码_MSMN
- Market status and development prospect forecast of global heat curing adhesive industry in 2022
- [SQL injection] joint query (the simplest injection method)
- GFS distributed file system (it's nice to meet it alone)
猜你喜欢

Keepalived热备与HAProxy
2022 chemical automation control instrument examination summary and chemical automation control instrument certificate examination

Leetcode simple question: check whether the array is sorted and rotated

FISCO bcos zero knowledge proof Fiat Shamir instance source code

First + only! Alibaba cloud's real-time computing version of Flink passed the stability test of big data products of the Institute of ICT
![[luatos sensor] 2 air pressure bmp180](/img/88/2a6caa5fec95e54e3fb09c74ba8ae6.jpg)
[luatos sensor] 2 air pressure bmp180

【工具跑SQL盲注】

2022 registration of G2 utility boiler stoker examination and G2 utility boiler stoker reexamination examination
When using the benchmarksql tool to test the concurrency of kingbasees, there are sub threads that are not closed in time after the main process is killed successfully

Review the old and know the new: Notes on Data Science
随机推荐
Matplotlib -- save graph
【XSS绕过-防护策略】理解防护策略,更好的绕过
Golang -- realize file transfer
The simple problem of leetcode: dismantling bombs
【工具跑SQL盲注】
What functions need to be set after the mall system is built
论文阅读_中文NLP_ELECTRA
Hire cashier (differential constraint)
Market status and development prospect prediction of global neutral silicone sealant industry in 2022
2022 registration of G2 utility boiler stoker examination and G2 utility boiler stoker reexamination examination
Market status and development prospect forecast of global button dropper industry in 2022
The usage of micro service project swagger aggregation document shows all micro service addresses in the form of swagger grouping
Arthas watch grabs a field / attribute of the input parameter
Market status and development prospects of the global IOT active infrared sensor industry in 2022
Market status and development prospect prediction of global fermentation acid industry in 2022
7. Integrated learning
Market status and development prospect prediction of the global forward fluorescent microscope industry in 2022
Sdl2 + OpenGL glsl practice (Continued)
Caijing 365 stock internal reference: what's the mystery behind the good father-in-law paying back 50 million?
2022 tea master (intermediate) examination questions and tea master (intermediate) examination skills