当前位置:网站首页>[try to hack] IP address
[try to hack] IP address
2022-06-23 07:54:00 【Happy star】
Blog home page : Happy star The blog home page of
Series column :Try to Hack
Welcome to focus on the likes collection ️ Leaving a message.
Starting time :2022 year 6 month 18 Japan
The author's level is very limited , If an error is found , Please let me know , thank !
A lot of content comes from This article , Only for your own study
More about subnet addressing , see This article
Navigation assistant
ip Address Overview
IP The address is and the length is 32 bit, from 4 Byte composition . For the convenience of reading and writing ,IP Addresses are usually expressed in dotted decimal numbers .
IPv4 Address range 00000000.00000000.00000000.00000000~11111111.11111111.11111111.11111111, namely 0.0.0.0~255.255.255.255
Subnet mask
LAN communication rules :
In the same LAN , all IP You must be in the same network segment to communicate with each other !
IP Address structure :
Network bit + Host bit ( The network bits are the same IP Address , For the same segment )
Subnet mask :
Used to determine IP Network bit of address
How does the subnet mask confirm the network bit :
And 255 The corresponding number is network bit , And 0 The corresponding number is the host bit
One IP The address must have a subnet mask ( There is a default subnet mask, such as C The subnet mask of the segment is /24)
Subnet mask and ip The address is similar to , It's also 32 Bit binary number
Subnet mask, for example :255.255.255.0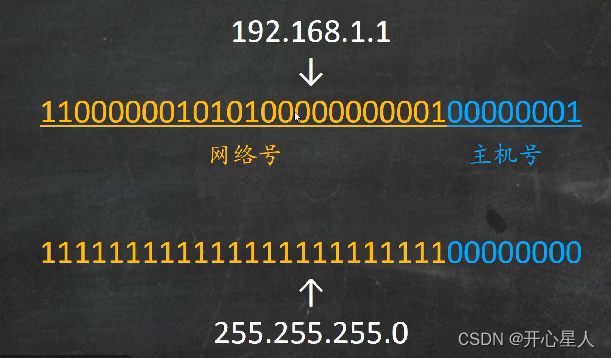
Another representation of subnet mask :192.168.1.1/24
among 24 Indicates the first in the subnet mask 24 Position as 1
Classified addressing
In the length of 32 Bit IPv4 In the address , There is a continuous bit called the network number , There is also a continuous bit called the host number .
A class : The network number is 8 position , The host number is 24 position
B class : The network number is 16 position , The host number is 16 position
C class : The network number is 24 position , The host number is 8 position
A、B、C The three types of subnet masks can be modified
Small exercise :
ip Address 10.1.1.1
Subnet mask 255.255.0.0
ask :10.1.1.1 Which network segment does it belong to ? How many are available in the network segment IP Address ? What is the broadcast address of this network segment ?
answer :
10.1.1.1 Belong to 10.1.0.0 Network segment
Network segment IP Number of addresses :65534(10.1.0.1-10.1.255.254)
The broadcast address of this network segment is :10.1.255.255
special IP Address
Public network IP Address :IP Address by IANA Uniformly distributed , To ensure that any one IP The address in Internet The uniqueness on the Internet . there IP Address refers to the public network IP Address .
The private network IP Address : In fact, some networks do not need to be connected to Internet, For example, the network in a closed laboratory of a University , As long as the network equipment in the same network IP The address does not conflict . stay IP In the address space ,A、B、C Some of the three types of addresses are reserved for the above situation , It's called private network IP Address .
A class :10.0.0.0~10.255.255.255
B class :172.10.0.0~172.31.255.255
C class :192.168.0.0~192.168.255.255
255.255.255.255
This address is called a limited broadcast address , It can be used as a IP The purpose of the message IP Address using .
The router received the destination IP The broadcast address is limited IP After the message , Will stop thinking about this IP Forwarding of messages .
0.0.0.0
If you take this address as the network address , It means “ Any network ” Network address of ; If you use this address as the host interface address , It means “ Host interface on this network ” Of IP Address .
for example : When a host interface has not obtained its own during startup IP Address time , You can send the destination to the network IP The address is limited broadcast address 、 Source IP The address is 0.0.0.0 Of DHCP Request message , hope DHCP After the server receives its own request , Be able to assign one to yourself IP Address .
127.0.0.0/8
This address is the loopback address , It can be used as a IP The purpose of the message IP Address using . Its function is to test the software system of the equipment itself .
Produced by a device 、 Purpose IP The address is the loopback address IP It is impossible for the message to leave the device itself .
169.254.0.0/16
If a network device gets IP The address mode is set to automatic acquisition mode , But the device did not find any available on the network DHCP The server , Then the device will use 169.254.0.0/16 A certain address of the network segment for temporary communication .
notes :DHCP (Dynamic Host Configuration Protocol), Dynamic Host Configuration Protocol , Used to dynamically allocate network configuration parameters , Such as IP Address .
gateway
gateway : An exit to the network ,Gateway=GW, The general gateway is on the router
Router : You can use devices connected to the internal and external network 
The router intranet interface must also be equipped with a IP, And the default address is the first or last of all available addresses ( No matter which enterprise in the world , All LANs ), namely X.X.X.1 or X.X.X.254
( This is why host discovery , The host number is too high or too low )
The router in the figure 192.168.0.1 It is called the outlet of the intranet , It's a level . This IP It is called gateway .
PC If you want to communicate between, you must ensure that you are in the same network segment
a PC Want to access another PC The psychological activities of :
(1) Compare whether they are in the same network segment ;
(2) If you are in the same network segment , Then send it directly , Instead of finding the gateway ;
(3) If not in the same network segment , Then contract directly to the gateway .
边栏推荐
- 1. probability theory - combination analysis
- 快速删除代码里面的node_modules
- 浅谈ThreadLocal和InheritableThreadLocal,源码解析
- [pit stepping record] a pit where the database connection is not closed and resources are released
- On ThreadLocal and inheritablethreadlocal, source code analysis
- 2022山东大学软件学院软件项目管理期末考试(回忆版)
- google常用语法
- MIT CMS. 300 session 12 – identity construction Part 2
- Using jetpack datastore for data storage
- 浅析 Open API 设计规范
猜你喜欢

Design of temperature detection and alarm system based on 51 single chip microcomputer

Online JSON to CSharp (c) class tool

The Sandbox 与《足球小将》达成合作,将流行的足球漫画及动画带入元宇宙

忽略超长参数违规

论文写作之WPS安装Mathtype插件编写数学公式

AVL树的实现

Can you think of a better way to solve the problem of string inversion?

On ThreadLocal and inheritablethreadlocal, source code analysis

Chain tour airship development farmers' world chain tour development land chain tour development

一篇文章学会er图绘制
随机推荐
启动appium
Make a record of glib2.14 upgrading glib2.18 and the principle of the steps
Unity picture loading and saving
Acwing第 56 場周賽【完結】
Apache Solr 任意文件读取复现
How do I install MySQL on my computer?
socket编程(多线程)
Acwing game 56 [End]
Unity图片加载和保存
Detailed explanation of redis persistence, master-slave and sentry architecture
MIT CMS. 300 session 12 – identity construction Part 2
在kubernetes中部署kubersphere
深度学习------不同方法实现vgg16
QT project error: -1: error: cannot run compiler 'clang++' Output:mingw32-make. exe
论文伪代码规范,伪代码在线编辑器,
ArcMap批量删除距离较近的点
《一周的朋友》
一篇文章学会er图绘制
Qt工程报错:-1: error: Cannot run compiler ‘clang++‘. Output:mingw32-make.exe
On ThreadLocal and inheritablethreadlocal, source code analysis