当前位置:网站首页>Realization of a springboard machine
Realization of a springboard machine
2022-06-28 10:14:00 【InfoQ】
One 、 Introduction to the idea of springboard machine
- Linux The server
- Windows The server
- Other terminals (MySQL terminal 、Redis terminal 、 Network equipment terminal wait )
Two 、 Background knowledge
2.1 Linux Of PAM Mechanism

2.2 PAM The core competencies of

2.3 PAM Module type
- auth
- account
- session
- password
2.4 common PAM modular
- pam_unix.so modular
- pam_cracklib.so modular
- pam_loginuid.so modular
- pam_securetty.so modular
- pam_rootok.so modular
- pam_console.so modular
- pam_permit.so modular
- pam_env.so modular
- pam_xauth.so modular
- pam_stack.so modular
- pam_warn.so modular
3、 ... and 、 Springboard system architecture
3.1 Microservices and high availability design
3.1.1 Microservice design
- monitor 8080 port , Provide http Interface capabilities
- Verify whether an account exists and is normal
- Verify whether an account has login permission to a server
- Verify whether an account has a connection to a server sudo jurisdiction
- Data pulling : account number 、 host 、 Dangerous command library, etc
- yes jmp The only access to the database
- monitor 2200 port , Provide ssh Agency ability
- Direct access to Linux The server 、 Other terminals
- monitor 8080 port , Provide websocket/socket.io Connection ability
- adopt ssh Protocol forwarding socket.io Flow to jmp-ssh
- Support the connection and access of Web terminal
- monitor 8080 port , Provide socket.io Connection ability
- Realization rdp agent , For ease of operation Windows The server
- Support web based Remote Desktop Services
- Provide file upload and download capabilities , Support in jmp Pass through sftp command , Support any sftp Client connection
- visit S3, To access files
- Deployed on every Linux Server
- jmp-agent Resident process
- jmp special pam modular
3.1.2 High availability design
3.2 Interaction diagram of each sub service of the springboard machine
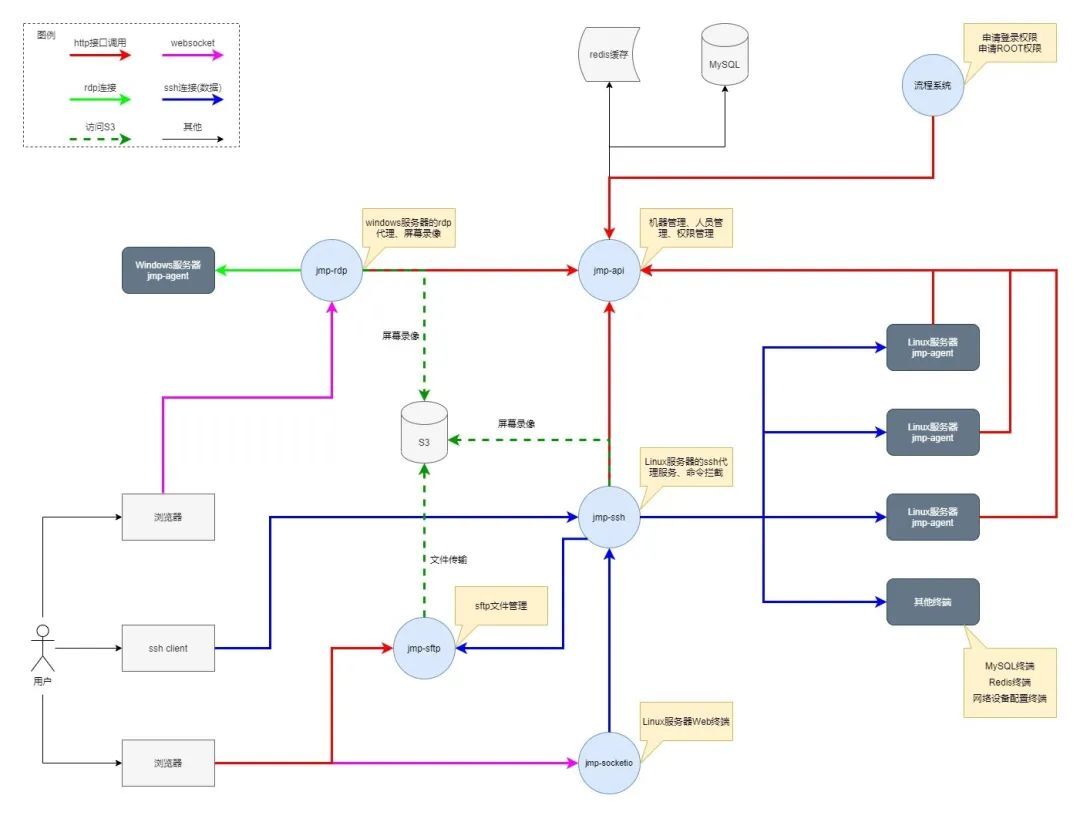
Four 、 Core design ideas
4.1 Log on to the skip machine
- The user to use ssh The client logs in to jmp-ssh service , And jmp-ssh Service interaction .
- jmp-ssh Access to services ssh Account number during session establishment 、 Password after encryption 、 Secondary authentication information .
- jmp-ssh Service access jmp-api service , Submit account number 、 Password after encryption 、 Secondary authentication information , In order to know whether the user is logged in jmp Authority .
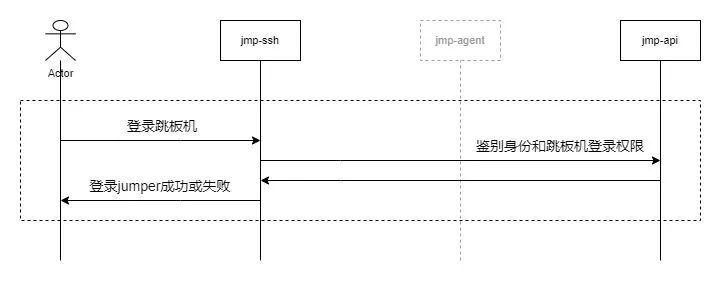
4.2 Log in to the target server
- Only if the user has logged in to jmp-ssh Or it has passed jmp-socket You can log in to the target server only after the front-end authentication of .
- The user is in jmp-ssh Pseudo terminal input provided ssh xxxx(xxxx Is the host name of the target server or IP Address ).
- jmp-ssh adopt ssh Connect to target server , Automatically carry user name information , Try to establish a session .
- Due to... On the target server jmp-agent Took over sshd Identification and authority authentication , therefore jmp.so obtain ssh User name during session establishment , The user name and the local computer IP Address information encryption , call jmp-api Interface for authority authentication .
- jmp-api According to the built-in policy , And query authorization table , Determine whether the user has login permission to the machine .
- jmp-agent Get the authentication result , For those who have authority , be ssh Session successfully established , Otherwise, the session establishment fails .
- jmp-ssh Get the result and reason of session establishment , Return to the user ssh terminal .

4.3 Command interaction
- Only if the user has logged in to a machine , To command interaction .
- When the user ssh Typing characters on the client , Pass on to jmp-ssh,jmp-ssh Determine whether the statement ends .
- When statement ends , be jmp-ssh According to the dangerous order rules of the machine , Match statements entered by the user , Decide to alarm 、 Intercept 、 adopt .
- jmp-ssh Pass the passed statement or the statement requiring alarm to the target server , The target server executes and returns the result .
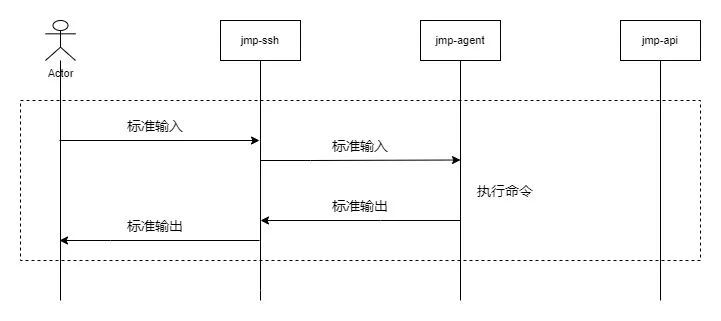
4.4 Switching users / Privileged account
- Only if the user has logged in to a machine , It is possible to trigger the behavior of switching users .
- When the user ssh Client execution sudo xxxx、su、id And so on ,jmp-ssh Transparently transmit commands to the target server .
- On the target server sshd Process execution sudo xxxx、su、id And so on command , Because the target server has been jmp-agent Took over identity failure and authority authentication , Therefore, from jmp.so Get login user name 、 Current user name 、 Local address information 、 Target user name information , transfer jmp-api Interface for sudo Permission authentication .
- jmp-api Judge whether the user has the right to switch the machine to xx Account permissions ( If there is root jurisdiction ).
- sudo、su、id Wait for the process to pass jmp.so The authentication result is obtained , Decide whether to switch users .
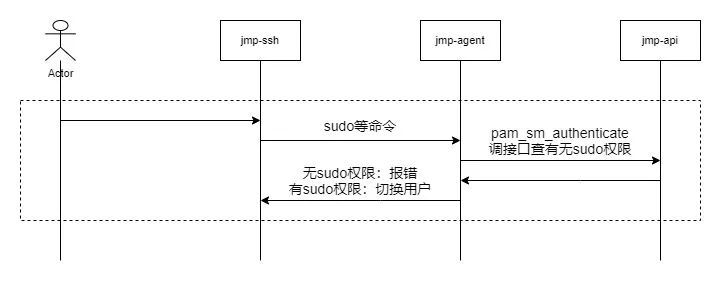
4.5 Use web interaction
- Only if the user has completed login through the web page ( Such as sso) The situation of .
- Users access through web pages jmp-socket service .
- jmp-socket Service to get user name information 、 Website login sso Information , Submit to jmp-api, Generate a temporary login credential .
- jmp-socket visit jmp-ssh, Submit temporary login credentials .
- jmp-ssh Initiate secondary authentication for login , Wait for the user to complete the secondary authentication .
- jmp-socket After the user completes the second authentication , To undertake the ssh Role of client , And jmp-ssh Interaction .
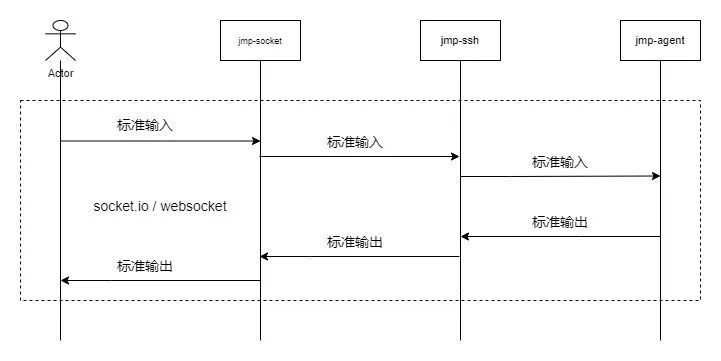
4.6 Dangerous command interception
- jmp-ssh After the user has logged in to the target server , In this session , Load the dangerous command rules of the corresponding service of the target machine , Initialize regular matching logic .
- jmp-ssh At the end of the user input statement , According to the dangerous order rules of the machine , Match statements entered by the user .
- jmp-ssh Match the post strategy according to the dangerous command rules , Decide to do the following for this input : The alarm 、 Intercept 、 adopt .
- For passing ,jmp-ssh Pass the command to the target server .
- For alarm ,jmp-ssh Pass the command to the target server , But to the user 、 The immediate leader of the user 、jmp The system administrator sends a danger command alarm .
- For intercepted ,jmp-ssh Refuse to pass command , At the same time, the user 、 The immediate leader of the user 、jmp The system administrator sends a danger command alarm .

4.7 Not Linux The springboard of the server
- Windows The server
- MySQL Terminals and Redis terminal
- Network device management terminal
5、 ... and 、 Permission rules and approval link design
5.1 Default permissions
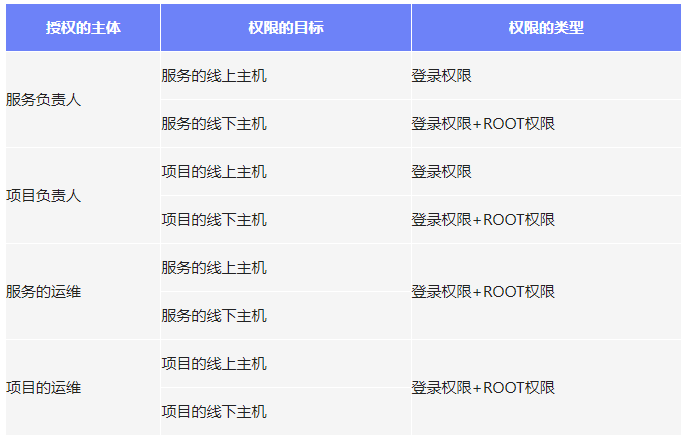
5.2 Approval link of permission application
- If you don't have default permissions , But you need to log in to the machine , Or you need to use ROOT jurisdiction , You need to apply .
- If you apply for permission for an organization , Then the organization ( department ) All members have the permission to apply for locks .

6、 ... and 、 The advantages of this realization idea
6.1 It is easy to operate , Better experience
6.2 Safe and reliable , Easy to audit
6.3 The responsibilities of the service room are clear
7、 ... and 、 Summary and prospect
边栏推荐
- Comprehensive evaluation of outline note taking software workflow: advantages, disadvantages and evaluation
- PMP Exam key summary IX - closing
- [unity][ecs] learning notes (I)
- Sword finger offer | linked list transpose
- Fabric.js 笔刷到底怎么用?
- 引入 flink-sql-mysql-cdc-2.2.1 好多依赖冲突,有解决的吗?
- Custom exception classes and exercises
- bye! IE browser, this route edge continues to go on for IE
- [Unity][ECS]学习笔记(二)
- 【云驻共创】DWS告警服务DMS详细介绍和集群连接方式简介
猜你喜欢
适配器模式(Adapter)

Dolphin scheduler uses system time

HDI blind hole design, have you noticed this detail?

Unity AssetBundle asset packaging and asset loading

Composite pattern
![[NLP] this year's college entrance examination English AI score is 134. The research of Fudan Wuda alumni is interesting](/img/a8/51b95432a9c8f25d8440cfd80926ce.png)
[NLP] this year's college entrance examination English AI score is 134. The research of Fudan Wuda alumni is interesting

如何查看谷歌浏览器保存的网页密码

Why does istio use spirit for identity authentication?

Teach you how to handle the reverse SVG mapping of JS

缓存之王Caffeine Cache,性能比Guava更强
随机推荐
Custom exception classes and exercises
如何查看谷歌浏览器保存的网页密码
Composite pattern
Sqlcmd database connection error
接口自动化框架脚手架-利用反射机制实现接口统一发起端
引入 flink-sql-mysql-cdc-2.2.1 好多依赖冲突,有解决的吗?
Cisco * VRF(虚拟路由转发表)
==And eqauls()
最小栈<难度系数>
装饰模式(Decorator)
fastposter v2.8.4 发布 电商海报生成器
Correct conversion between JSON data and list collection
Resolution: overview of decentralized hosting solution
Must the MySQL table have a primary key for incremental snapshots?
Summary of MySQL basic knowledge points
增强 Jupyter Notebook 的功能,这里有四个妙招
Installing redis under Linux and windows (ultra detailed graphic tutorial)
读取pdf图片并识别内容
As shown in the figure, the SQL row is used to convert the original table of Figure 1. Figure 2 wants to convert it
Read PDF Text and write excel operation