当前位置:网站首页>Alibaba Senior Software Testing Engineer recommends testers to learn -- Introduction to security testing
Alibaba Senior Software Testing Engineer recommends testers to learn -- Introduction to security testing
2022-06-24 08:59:00 【He haha knocks the code】
Security test definition
Security test is a test based on function test , Safety tests provide evidence that , In the face of malicious attacks , The application can still fully meet its needs , It mainly refers to the process of inspecting the product to verify whether it conforms to the definition of safety requirements and product quality standards
The purpose of the safety test 
Improve product safety and quality
Try to find security problems and fix them before release to reduce risks
Measure the security level
Verify whether the protection mechanism installed in the system can protect the system in practical application , So that it will not be illegally invaded
The difference between safety test and routine test 
Safety test type
1. Cross site scripts (XSS)
XSS Also called CSS(CROSS SET SCRIPT), Cross-site scripting attacks . It refers to a malicious attacker WEB Insert malicious html Code , When users browse the page , Embedded in it html Code will be executed , So as to achieve the special purpose of malicious users ;( go fishing 、 Stealing cookie、 Manipulate the victim's browser 、 Worm attack )
2. Reflective Cross Station (Reflected XSS)
Server side access http Parameters in the request , Output directly to the client without filtering . If these parameters are scripts , It will execute on the client ( Fishing is common ).
3. Storage type cross station (Stored XSS)
The data entered by the user is stored on the server ( It usually exists in the database ), When other users visit a page , These data are directly output without filtering . This data may be malicious script , Harm to other users .( Hang a horse
common )
In applications that allow uploading files , An attacker uploads a message containing malicious code html perhaps txt file , Users browse these files to execute malicious code ;
Uploading pictures is the most common in general applications , If the picture contains malicious code html perhaps txt file ,, Lower Edition IE When requesting this picture directly , Will ignore Content-Type Execute the code in the picture .
4.DOM cross-site (DOM-Based XSS)
An attacker constructs a code that contains malicious Javascript Of URL, Then entice the user to request this URL. The server did not return malicious after receiving the request Javascript.
Browser processing URL When data in , Execute malicious code .
5. Cross-site request forgery (CSRF)
Force the victim's browser to a vulnerable Web Applications send requests , Finally, achieve the operation behavior required by the attacker .
Malicious requests will bring the browser Cookie. Attacked Web Application trust browser Cookie.
6.SQL Inject
The data entered by the user is used to construct SQL
Query statement , Query sensitive content in the database , Bypass authentication to add 、 Delete 、 Modifying data 、 Denial of service .
7.XML Inject
and SQL The injection principle is the same ,XML It's where the data is stored , When querying or modifying , If you don't escape , Directly input or output data , Will lead to XML Inject holes . Attackers can modify XML data format , Add new XML node , Impact on data processing flow .
8.URL Jump
Web The application received a URL After the parameter , There is no change to the parameters ” Trust URL” Validation of the , Go back to the user's browser and jump to the URL Instructions .( Phishing attack )
9. File systems span
File system …/ On behalf of the parent directory , Through one or more …/ Cross directory restrictions .
10. System commands
The parameters submitted by the user are used to execute the parameters of the system command .
Use ”|” or ”;” Execute multiple orders .
11. Upload files
Web When an application processes a file uploaded by a user , Did not judge whether the file extension is within the allowed range , Or the legality of the contents of the file is not detected , Just save the file on the server , Even upload the script Trojan horse to web Server , Direct control web The server .( The extension is not restricted 、 File contents not checked 、 Virus files )
12. Download any file
Download attachments and other functions
Apache The virtual directory points to
Java/PHP Read the file
Download database configuration file, etc
Directory browsing
13. Access control
Do you have permission to
Some systems do not require permission control
Have you set permissions
With a powerful authority system , But it's not used
Is there any authority to cut corners
URL Level
Menu level
14. Access control
Horizontal authority
Web The application received a user request , When modifying a piece of data , There's no one to judge who the data belongs to , Or judge who the data belongs to , Submitted from the user request Parameters ( User controlled data ) in , Get who the data belongs to id, A malicious attacker can transform the data ID, Or change who you belong to id, Modify data that does not belong to you .
Vertical permissions
because web The application does not do permission control , Or just do permission control on the menu , As a result, malicious users only need to guess the properties of other management pages URL, You can access or control data or pages owned by other roles , Achieve the purpose of authority promotion .
15.Session Expires
Session expiration,
The browser is out of date
The server 30 Minutes no action expired
The server 24 Hours mandatory expiration
Keep talking
Safety test tools
1.AppScan
A security vulnerability scanning tool , It's quite so " Explore " and " test " The process of , Finally, a very intuitive test report is generated , It is helpful for R & D personnel to analyze and repair
Official website :https://www.ibm.com/developerworks/downloads/r/appscan/
Reference resources :https://www.cnblogs.com/benpao1314/p/8065720.html
2.BurpSuite
A necessary integrated penetration testing tool for information security practitioners , It uses automatic test and semi-automatic test , Contains Proxy,Spider,Scanner,Intruder,Repeater,Sequencer,Decoder,Comparer And so on ;
Proxy Function can intercept HTTP/S Proxy server for ( Mobile phones and web);
Spide function - Intelligent sensing web crawler ;
Intruder Functions can be web Automated attacks on Applications , Very suitable for safety testing .
By intercepting HTTP/HTTPS Of web Data packets , Act as a middleman for browsers and related applications , To intercept 、 modify 、 Replay packets for testing .
Official website :https://portswigger.net/burp/
Reference resources :https://www.cnblogs.com/nieliangcai/p/6692296.html
3.Nmap
A network connection end scanning software , It is used to scan the open network connection of online computers . Determine which services are running on which connections .
Official website :https://nmap.org/
Reference resources :https://blog.csdn.net/m0_37268841/article/details/80404613
4.sqlmap
An open source penetration testing tool , It can be used for automatic detection , utilize SQL Inject holes , Get database server permissions . It has a powerful detection engine , Function options of penetration testing for different types of databases , Including getting the data stored in the database , Accessing operating system files can even execute operating system commands through an external data connection .
The house needs to be built layer by layer , Knowledge needs to be learned at one point one . We should lay a good foundation in the process of learning , More hands-on practice , Don't talk much , The last dry goods here ! I stayed up late to sort out the stages ( function 、 Interface 、 automation 、 performance 、 Test open ) Skills learning materials + Practical explanation , Very suitable for studying in private , It's much more efficient than self-study , Share with you .
Get off w/x/g/z/h: Software testing tips dao
Typing is not easy , If this article is helpful to you , Click a like, collect a hide and pay attention , Give the author an encouragement . It's also convenient for you to find it quickly next time .
边栏推荐
- MySQL | view notes on Master Kong MySQL from introduction to advanced
- From the Huawei weautomate digital robot forum, we can see the "new wisdom of government affairs" in the field of government and enterprises
- Data middle office: detailed explanation of technical architecture of data middle office
- Data middle office: the data middle office practice scheme of Minsheng Bank
- [quantitative investment] discrete Fourier transform to calculate array period
- every()、map()、forEarch()方法。数组里面有对象的情况
- China chip Unicorn Corporation
- 【量化投资】离散傅里叶变换求数组周期
- Liunx change the port number of vsftpd
- 2138. 将字符串拆分为若干长度为 k 的组
猜你喜欢

华为路由器:GRE技术

I heard that you are still spending money to buy ppt templates from the Internet?
![[use picgo+ Tencent cloud object to store cos as a map bed]](/img/14/d650960cc77385504ea5e2e138bd46.jpg)
[use picgo+ Tencent cloud object to store cos as a map bed]

Transplantation of xuantie e906 -- fanwai 0: Construction of xuantie c906 simulation environment

A tip to read on Medium for free

One article explains in detail | those things about growth

110. 平衡二叉树-递归法
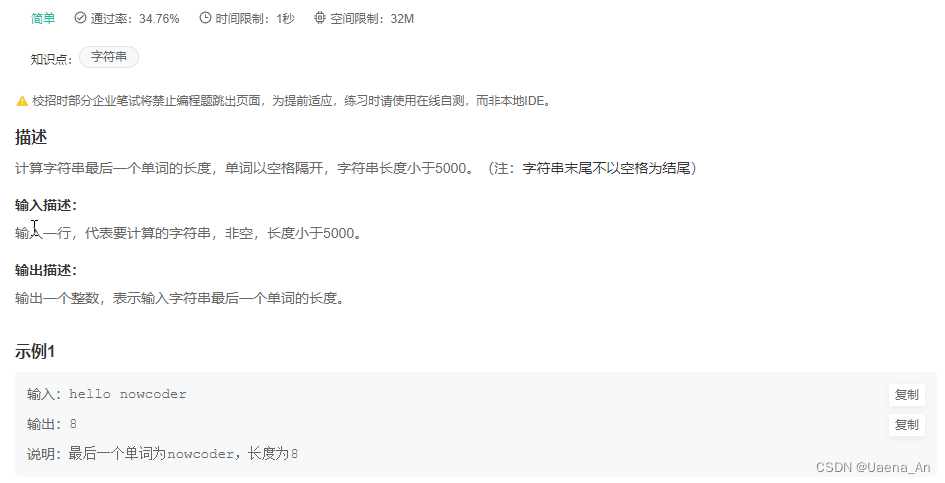
【牛客】HJ1 字符串最后一个单词的长度
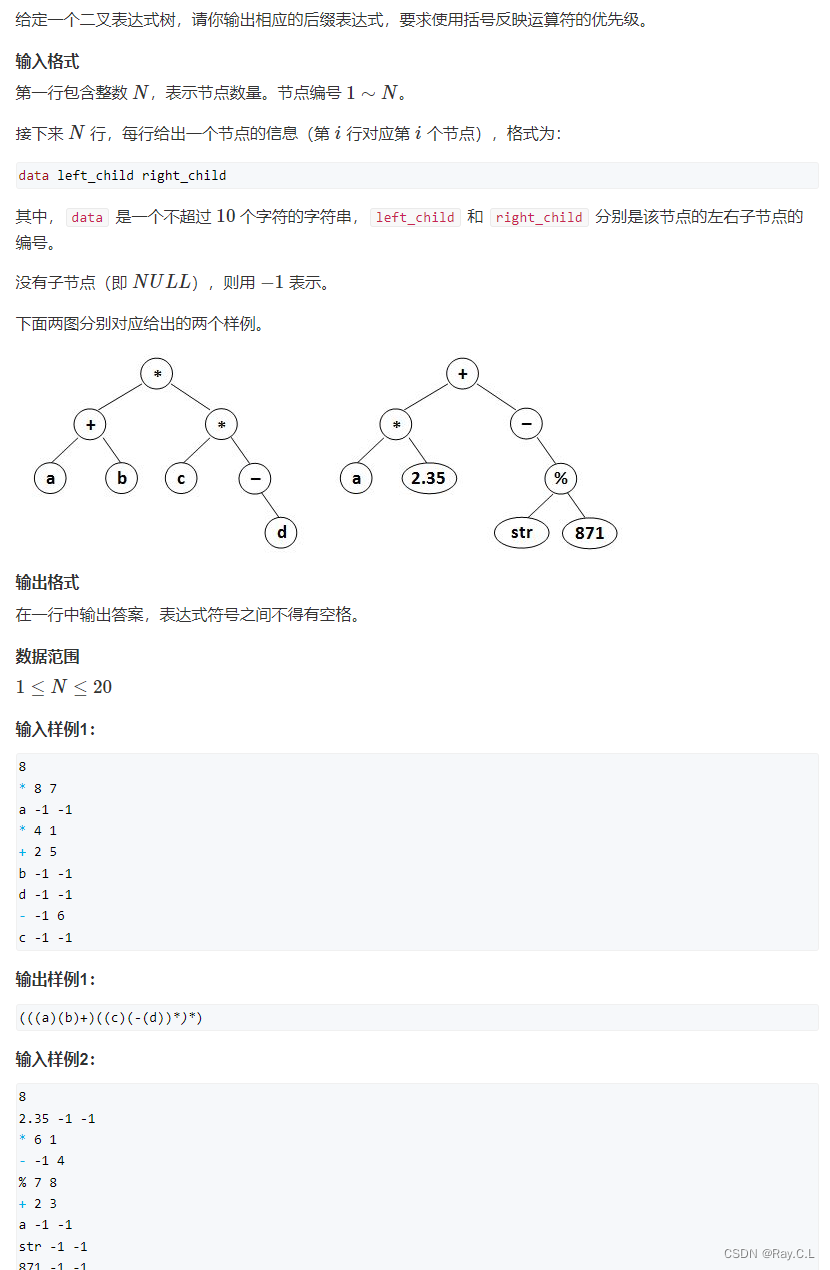
4274. suffix expression
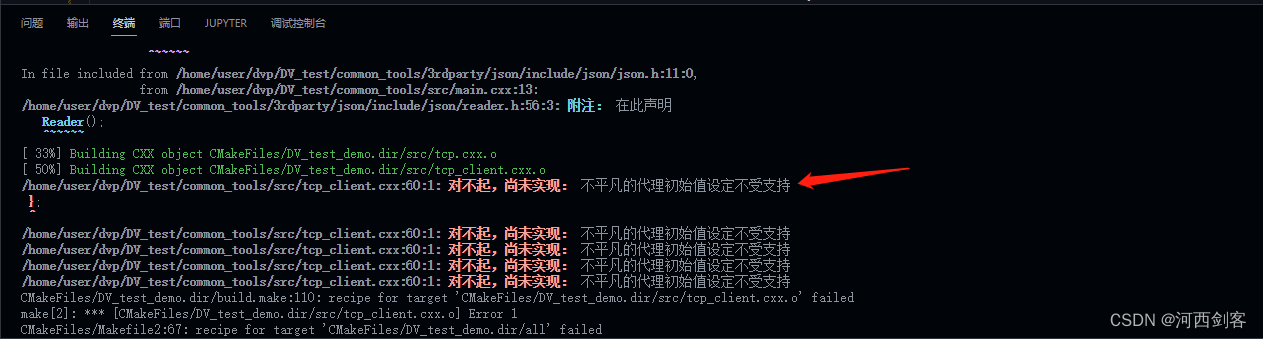
“不平凡的代理初始值设定不受支持”,出现的原因及解决方法
随机推荐
关于 GIN 的路由树
微博撰写-流程图-序列图-甘特图-mermaid流程图-效果不错
A tip to read on Medium for free
所说的Get post:请求的区别,你真的知道了吗??????
数云发布2022美妆行业全域消费者数字化经营白皮书:全域增长破解营销难题
A tip to read on Medium for free
原生小程序用画布制作海报,等比例缩放,和uniapp差不多就是写法有点不同
WebRTC系列-网络传输之5选择最优connection切换
【LeetCode】387. 字符串中的第一个唯一字符
Liunx change the port number of vsftpd
数据中台:民生银行的数据中台实践方案
用VNC Viewer的方式远程连接无需显示屏的树莓派
Kaformer personal notes
PM2 deploy nuxt3 JS project
Mba-day25 best value problem - application problem
linux(centos7.9)安装部署mysql-cluster 7.6
2022.06.23(LC_144,94,145_二叉树的前序、中序、后序遍历)
MySQL | view notes on Master Kong MySQL from introduction to advanced
什么是图神经网络?图神经网络有什么用?
"I can't understand Sudoku, so I choose to play Sudoku."