当前位置:网站首页>Kali system -- fierce of DNS collection and analysis
Kali system -- fierce of DNS collection and analysis
2022-06-13 00:30:00 【P1n9】
Reprinted from :https://blog.csdn.net/weixin_34236869/article/details/91709966
1> effect : Find target's IP And the host name , Blasting subdomain name, etc
characteristic : You can set multiple discontinuous IP Address , It can be multithreaded
Fierce Is a IP、 Domain name mutual check DNS Tools , Domain transfer vulnerability detection can be performed 、 Dictionary explosion subdomain 、 The check IP paragraph 、 Reverse check the next paragraph of the specified domain name IP, It belongs to a semi lightweight multi-threaded information collection appliance .Fierce Try to build HTTP Connect to determine if the subdomain name exists , This feature is not a lightweight feature , therefore , Defined as semi lightweight .
2> Parameter interpretation :
# Use command : fierce [-dns example.com] [OPTIONS]
Options:
-connect [header.txt] Right RFC1918 address HTTP Connect ( Time consuming 、 There's a lot of traffic ), By default, the response header of the server is returned . Can be specified by file HTTP The request header Host Information , Such as :fierce -dns example.com -connect headers.txt
-delay <number> Specify the time interval between queries
-dns <domain> Specify the domain name to query
-dnsfile <dnsfile.txt> Use the file to specify the DNS Server list
-dnsserver <dnsserver> Specify to initialize SOA Of the query DNS The server .( Only used for out initialization , Subsequent queries will use the... Of the target DNS The server )
-file <domain.txt> Output the results to a file
-fulloutput And -connect combination , Output all the information returned by the server
-help Print help
-nopattern Not applicable to search mode to find host .( This parameter is not used yet )
-range <1.1.1.1/24> Internal IP Range do IP The check ( This parameter is not yet understood ). Must be with dnsserver Parameter matching , Specify internal DNS The server , Such as : fierce -range 111.222.333.0-255 -dnsserver ns1.example.com
-search <Search list> Specify another domain , Search in other domains ( This parameter is not used ), Such as : fierce -dns examplecompany.com -search corpcompany,blahcompany
-tcptimeout <number> Specify the timeout for the query
-threads [number] Specify the number of threads to scan , Default single thread
-traverse [number] Specify the top and bottom of the scan IP Range , Default scan up and down 5 each .
-version Print fierce edition
-wide Scan the portal IP Address of the C paragraph . Generate large flow 、 More information will be collected .
-wordlist <sub.txt> Use the specified dictionary to explode the subdomain
# [] The data in is optional 、<> Inside is the required data
3> It is easy to use
Bring your own dictionary 2280 individual , Very slowly , Just test a few , Use a self built dictionary 

边栏推荐
- PMP renewal | PDU specific operation diagram
- PLC也能制作小遊戲----Codesys編寫猜數字小遊戲
- [GXYCTF2019]禁止套娃--详解
- Packaging and uplink of btcd transaction process (III)
- 2022美容师(技师)上岗证题目及答案
- JPA execution failed in scheduled task -executing an update/delete query transactionrequiredexception
- Masa auth - overall design from the user's perspective
- [LeetCode]20. Valid parentheses thirty-six
- How to quickly query the mobile phone number home and operator
- MASA Auth - 从用户的角度看整体设计
猜你喜欢

Do you have to read for PMP?

3、 Storage system

Several interview questions in TCP three grips and four swings
![[matlab] symbol calculation](/img/a5/7682a465ca2813a83114c091580c53.png)
[matlab] symbol calculation
![[matlab] matrix](/img/15/da3b530fca50080392c89e91998526.png)
[matlab] matrix

Some basic design knowledge

JPA execution failed in scheduled task -executing an update/delete query transactionrequiredexception

Explain bio, NiO, AIO in detail
![BUUCTF之BabySQL[极客大挑战 2019]](/img/6c/957e5e09f252210d0b4cf8771d4ade.png)
BUUCTF之BabySQL[极客大挑战 2019]
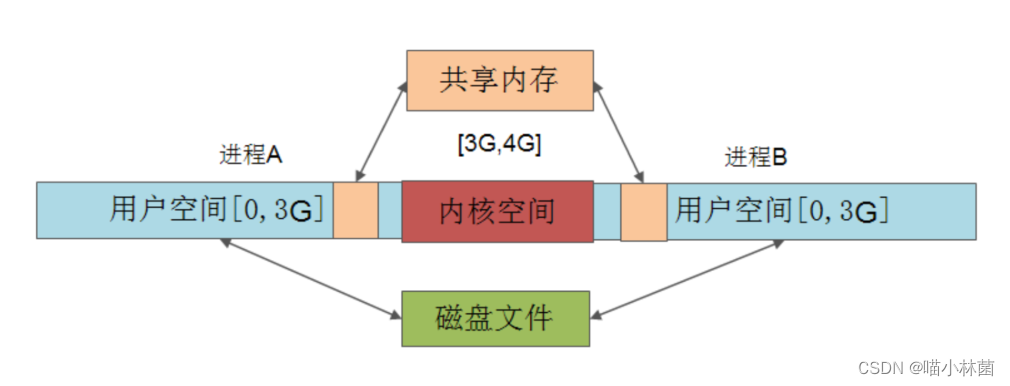
Interprocess communication - shared memory shmat
随机推荐
[matlab] symbol calculation
[LeetCode]28. Implement strstr()
vs studio_ How to use scanf in 2022
Is the brokerage account in qiniu business school safe? Is the account opening rate low
[colorful] Net dto mapping
【HCIE论述】组播IGMP-A
6.824 Lab 1: MapReduce
Kaust:deyao Zhu | value memory map: a graph structured world model based on off-line reinforcement learning
RCC clock configuration of stm32f401
What occupation is suitable for PMP?
Transaction creation of btcd transaction process (I)
[matlab] polynomial calculation
安全事故等级划分为哪几级
中科大USTC:Minrui Wang | 基于Transformer的多智能体强化学习的配电网稳压
新增博客地址
The difference between caching and buffering
Generate two-dimensional code in Delphi
2022施工员-设备方向-通用基础(施工员)操作证考试题及模拟考试
Go custom collation
Tsinghua-Bosch Joint ML Center, THBI Lab:Chengyang Ying | 通过约束条件风险价值实现安全强化学习