当前位置:网站首页>Small list of iptables common commands
Small list of iptables common commands
2022-07-24 15:37:00 【InfoQ】
iptables Small list of common commands
iptables brief introduction
- filter surface: Control whether packets are allowed in and out and forward , The links that can be controlled are INPUT、FORWARD and OUTPUT.
- nat surface: Control address translation in packets , The links that can be controlled are PREROUTING、INPUT、OUTPUT and POSTROUTING.
- mangle: Modify the original data in the packet , The links that can be controlled are PREROUTING、INPUT、OUTPUT、FORWARD and POSTROUTING.
- raw: control nat The enabled status of the connection tracking mechanism in the table , The links that can be controlled are PREROUTING、OUTPUT.
- INPUT( Inbound data filtering )、
- OUTPUT( Outbound data filtering )、
- FORWARD( Forward data filtering )、
- PREROUTING( Filtering before routing )
- and POSTROUTING( Post routing filtering ),

iptables grammar
iptables [-t table] command [match] [target]
command
match
1、 Universal matching
2、 Show match
target
iptables Input order of command options :
iptables -t Table name <-A/I/D/R> Rule chain name [ Rule number ] <-i/o adapter name > -p The name of the agreement <-s Source IP/ Source subnet > --sport Source port <-d The goal is IP/ Target subnet > --dport Target port -j action
- raw: Advanced features , Such as : Website filtering
- mangle: Packet modification (QOS), To achieve quality of service
- net: address translation , For gateway routers
- filter: Packet filtering , For firewall rules
- INPUT chain : Processing input packets
- OUTPUT chain : Processing output packets
- PORWARD chain : Processing forwarding packets
- PREROUTING chain : For target address translation (DNAT)
- POSTOUTING chain : For source address translation (SNAT)
- accept: Receive packets
- DROP: Discard packets
- REDIRECT: Redirect , mapping , Transparent proxy
- SNAT: Source address translation
- DNAT: Target address translation
- MASQUERADE:IP camouflage (NAT), be used for ADSL
- LOG: logging
example
Clear existing iptables The rules
iptables -F
iptables -X
iptables -Z
Develop the specified port
iptables -A INPUT -s 127.0.0.1 -d 127.0.0.1 -j ACCEPT # Allow local loopback interface ( That is, run native to access native )
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT # Allow established or associated traffic
iptables -A OUTPUT -j ACCEPT # Allow all native outbound access
iptables -A INPUT -p tcp --dport 22 -j ACCEPT # allow access to 22 port
iptables -A INPUT -p tcp --dport 80 -j ACCEPT # allow access to 80 port
iptables -A INPUT -p tcp --dport 21 -j ACCEPT # allow ftp Service 21 port
iptables -A INPUT -p tcp --dport 20 -j ACCEPT # allow FTP Service 20 port
iptables -A INPUT -j reject # Prohibit other rules that are not allowed to access
iptables -A FORWARD -j REJECT # Prohibit other rules that are not allowed to access
shielding IP
iptables -I INPUT -s 123.45.6.7 -j DROP # Shield individual IP The order of
iptables -I INPUT -s 123.0.0.0/8 -j DROP # Seal the whole section from 123.0.0.1 To 123.255.255.254 The order of
iptables -I INPUT -s 124.45.0.0/16 -j DROP # seal IP Segment from 123.45.0.1 To 123.45.255.254 The order of
iptables -I INPUT -s 123.45.6.0/24 -j DROP # seal IP Segment from 123.45.6.1 To 123.45.6.254 The order is
View the added iptables The rules
iptables -L -n -v
Chain INPUT (policy DROP 48106 packets, 2690K bytes)
pkts bytes target prot opt in out source destination
5075 589K ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
191K 90M ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22
1499K 133M ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
4364K 6351M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED
6256 327K ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 3382K packets, 1819M bytes)
pkts bytes target prot opt in out source destination
5075 589K ACCEPT all -- * lo 0.0.0.0/0 0.0.0.0/0
Will all iptables Display with serial number mark , perform :
iptables -L -n --line-numbers
Delete added iptables The rules
iptables -D INPUT 8
iptables debugging
1. Get ready ipt_LOG The kernel module
modprobe ipt_LOG
modprobe nf_log_ipv4
sysctl net.netfilter.nf_log.2=nf_log_ipv4
2. Use raw surface , Add tracking rules
iptables -t raw -A PREROUTING -p icmp -j TRACE
iptables -t raw -A OUTPUT -p icmp -j TRACE
iptables -t raw -A PREROUTING -p tcp -dport 80 -j TRACE
iptables -t raw -A OUTPUT -p tcp -dport 80 -j TRACE
3. Check the log
tail -f /var/log/kern.log
Reference source :
边栏推荐
- Analysis of some difficulties in VAE (variational self encoder)
- 2022 RoboCom 世界机器人开发者大赛-本科组(省赛)-- 第二题 智能服药助手 (已完结)
- Class assignment (6) - 575. Word division (word)
- 【Flutter -- 布局】流式布局(Flow和Wrap)
- MySQL function
- 4279. Cartesian tree
- 2022 robocom world robot developer competition - undergraduate group (provincial competition) -- question 3 running team robot (finished)
- Huffman tree (optimal binary tree)
- MySQL学习笔记(总结)
- From which dimensions can we judge the quality of code? How to have the ability to write high-quality code?
猜你喜欢

力扣 31.下一个排列--双指针法

From which dimensions can we judge the quality of code? How to have the ability to write high-quality code?
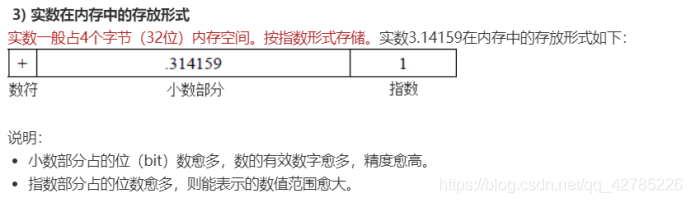
Existence form and legitimacy of real data in C language (floating point number)

Reentrantlock reentrant lock

什么是防火墙?防火墙能发挥什么样的作用?

Arduino ide esp32 firmware installation and upgrade tutorial

AttributeError: module ‘seaborn‘ has no attribute ‘histplot‘

ReentrantLock 可重入锁

Windows10 installation free redis

2022 robocom world robot developer competition - undergraduate group (provincial competition) rc-u4 strategy team (completed)
随机推荐
上课作业(6)——#575. 单词的划分(word)
Citic securities account opening process, is it safe to open an account on your mobile phone
微调LayoutLM v3进行票据数据的处理和内容识别
报错【项目报错】
公钥私钥传输,以及对CA证书的理解
Database learning – select (multi table joint query) [easy to understand]
Huffman tree (optimal binary tree)
被攻击怎么解决?DDoS高防IP防护策略
Introduction to single chip microcomputer: LED bidirectional water lamp
【Flutter -- 布局】流式布局(Flow和Wrap)
Exomeiser annotates and prioritizes exome variants
应用修改日志路径log4j.properties
Sklearn.metrics module model evaluation function
26. Code implementation of file using disk
C# - partial 关键字
[fluent -- layout] flow layout (flow and wrap)
【OpenCV 例程300篇】238. OpenCV 中的 Harris 角点检测
kubernetes多网卡方案之Multus_CNI部署和基本使用
[TA frost wolf \u may - hundred people plan] Figure 3.4 introduction to delayed rendering pipeline
C# SQLite Database Locked exception