当前位置:网站首页>Web middleware log analysis script 3.0 (shell script)
Web middleware log analysis script 3.0 (shell script)
2022-07-26 01:07:00 【Viva alive】
New features
3.0 Version added ssrf、 The directory traversal file contains 、 Optimize automatic directory creation .
In general use 1、6、7 that will do 

3.1 edition
Framework vulnerability detection 、 Cover font color changes

Saved logs
fi
Directory traversal 
sqli
ssrf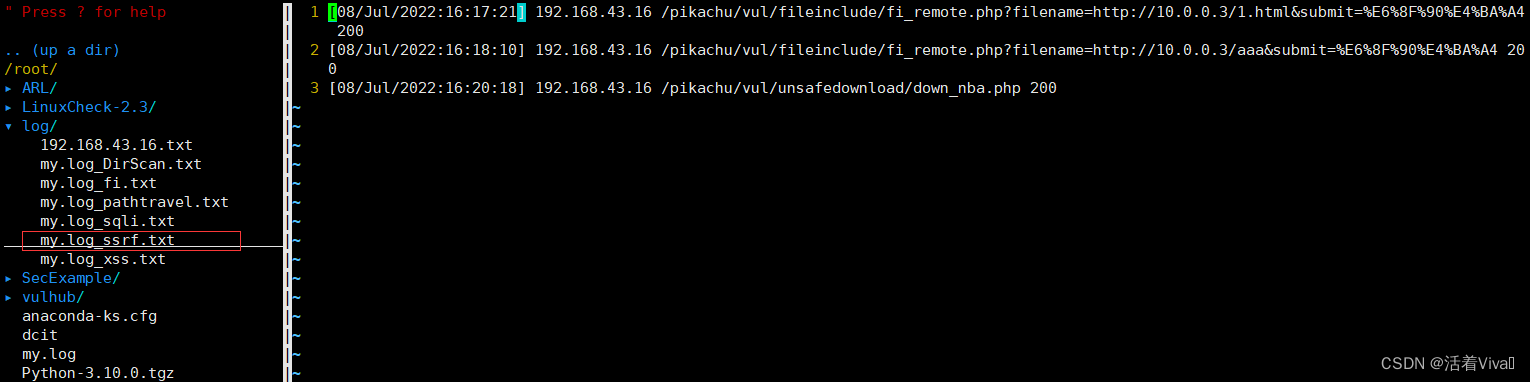
xss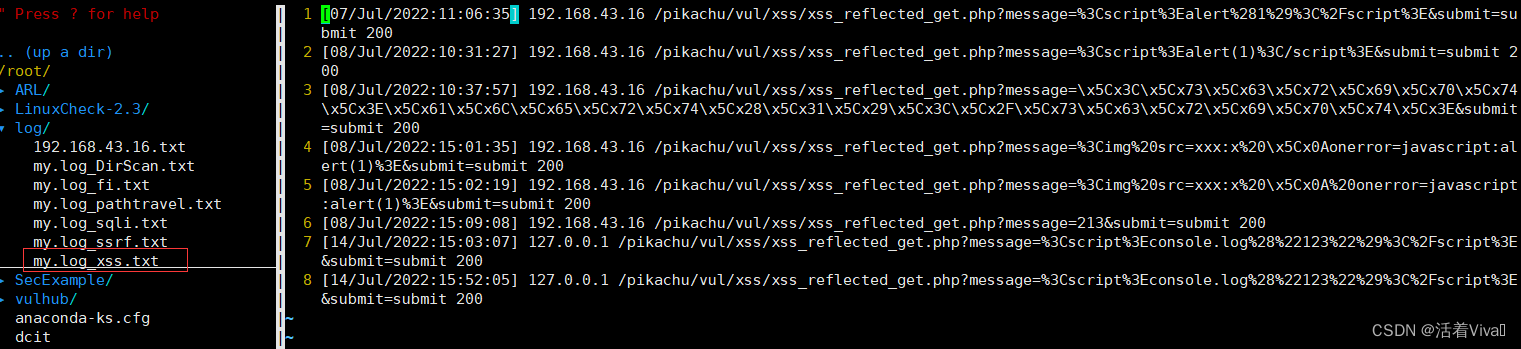
Code
#!/bin/bash
# The font color
Green_font_prefix="\033[32m"
Red_font_prefix="\033[31m"
Font_color_suffix="\033[0m"
# Split line
line(){
for i in {
1..100};do
if [ $i -ne 100 ];then
echo -ne "-"
else
echo -e "-"
fi
done
}
# Option one
diffip(){
line
echo -e " Check the top ( Numbers ):"
read -e -p "( Default : All )" num
[[ -z $num ]] && cut -d- -f 1 "$logfile"|sort| uniq -c | sort -rn || cut -d- -f 1 "$logfile"|sort| uniq -c | sort -rn | head -n $num
}
# Option 2
oneip(){
while true;do
echo -e " Please enter the IP:"
read -e ip
line
if [ "$(grep ^$ip $logfile |wc -l)" -ne 0 ];then
grep ^$ip $logfile| awk '{print $4."]",$1,$7,$9}'
break
else
echo -e "${Red_font_prefix} We didn't find it IP! Please re-enter !!${Font_color_suffix}"
line
continue
fi
done
}
# Save the file
savefile(){
echo -e " Whether to save to file (Y/n):"
read -e -p "( Default : preservation )" choose
[[ -z $choose ]] || [[ $choose == [Yy] ]] && grep ^$ip $logfile| awk '{print $4."]",$1,$7,$9}' > "$path$ip.txt" && echo -e "${Red_font_prefix} Saved to $path$ip.txt in ${Font_color_suffix}"
}
# Option 3
howmanyip(){
line
awk '{print $1}' $logfile|sort|uniq|wc -l
}
# Option four
keyword(){
while true;do
line
read -e -p " Please enter keywords (q To quit ):" key
if [ $key == "q" ];then
break
fi
more "$logfile" | grep "$key" | awk '{print $4."]",$1,$7,$9}'
done
}
# Option five
webshell(){
line
echo -e " Please input the file uploaded URI( Such as upload.php):"
read -e -p "( Default : sign out )" upload
[[ -z $upload ]] || cat $logfile |grep -nP "POST.*$upload.*$upload" > ""$path$filename"_webshell.txt"
time=$(cat ""$path$filename"_webshell.txt" |wc -l )
echo -e " detection complete !! A total of ${Red_font_prefix}$time${Font_color_suffix} Logs "
echo -e " The test results are stored in "$path$filename"_"webshell.txt""
}
# Option 6
dirscan(){
line
echo -e "[+] Detecting directory scanning ..."
for i in $(awk '{print $1}' $logfile|sort|uniq);do
time=$(cat $logfile | grep -P "^$i.*\b404\b" | wc -l)
[[ time -gt 20 ]] && echo -e "$i There may be directory scanning behavior , Total request failed ${Red_font_prefix}$time${Font_color_suffix} Time " && echo -e "$i There may be directory scanning behavior , Total request failed ${Red_font_prefix}$time${Font_color_suffix} Time " >> "$path$filename"_"DirScan.txt"
done
echo -e " detection complete !!"
echo -e " The test results are stored in "$path$filename"_"DirScan.txt""
line
echo -e " Whether to automatically download exceptions IP Access log (Y/n):"
read -e -p "( Default : preservation )" choose1
ip_list=$(cat "$path$filename"_"DirScan.txt" | grep -oE '.* ')
if [[ -z $choose1 ]];then
for ip in $ip_list;do
grep ^$ip $logfile| awk '{print $4."]",$1,$7,$9}' > "$path$ip.txt" && echo -e "${Red_font_prefix} Saved to $path$ip.txt in ${Font_color_suffix}"
done
fi
}
# Option seven
sqlicheck(){
line
echo -e "[+] Detecting ${Red_font_prefix}sql Inject ${Font_color_suffix} in ..."
word="%20select%20|%20and%20|%20or%20|%20exec|%27exec| information_schema.tables|%20information_schema.tables|%20where%20|%20union%20|%20SELECT%20|%2ctable_name%20|cmdshell|%20table_schema"
grep -E "$word" $logfile | awk '{print $4."]",$1,$7,$9}'> ""$path$filename"_sqli.txt"
time=$(cat ""$path$filename"_sqli.txt" |wc -l )
echo -e " detection complete !! A total of ${Red_font_prefix}$time${Font_color_suffix} Logs "
echo -e " The test results are stored in "$path$filename"_sqli.txt"
}
xsscheck(){
line
echo -e "[+] Detecting ${Red_font_prefix}xss${Font_color_suffix} in ..."
grep -E "alert|script|<|>|%3C|%3c|%3e|%3E" $logfile | awk '{print $4."]",$1,$7,$9}' > ""$path$filename"_xss.txt"
time=$(cat ""$path$filename"_xss.txt" | wc -l )
echo -e " detection complete !! A total of ${Red_font_prefix}$time${Font_color_suffix} Logs "
echo -e " The test results are stored in "$path$filename"_xss.txt"
}
ssrfcheck(){
line
echo -e "[+] Detecting ${Red_font_prefix}ssrf${Font_color_suffix} in ..."
grep -E "=http://|=https://" $logfile | awk '{print $4."]",$1,$7,$9}' > ""$path$filename"_ssrf.txt"
time=$(cat ""$path$filename"_ssrf.txt" | wc -l )
echo -e " detection complete !! A total of ${Red_font_prefix}$time${Font_color_suffix} Logs "
echo -e " The test results are stored in "$path$filename"_ssrf.txt"
}
pathtravelcheck(){
line
echo -e "[+] Detecting ${Red_font_prefix} Directory traversal ${Font_color_suffix} in ..."
grep -E "\.\.|\.%2e/|\.%%32%65|%2e%2e" $logfile | awk '{print $4."]",$1,$7,$9}' > ""$path$filename"_pathtravel.txt"
time=$(cat ""$path$filename"_pathtravel.txt" | wc -l )
echo -e " detection complete !! A total of ${Red_font_prefix}$time${Font_color_suffix} Logs "
echo -e " The test results are stored in "$path$filename"_pathtravel.txt"
}
fileinclude(){
line
echo -e "[+] Detecting ${Red_font_prefix} File contains ${Font_color_suffix} in ..."
awk '{print $4."]",$1,$7,$9}' $logfile | grep -E "=.*jsp\b|=.*php\b|=.*txt\b|=.*jpg\b" > ""$path$filename"_fi.txt"
time=$(cat ""$path$filename"_fi.txt" | wc -l )
echo -e " detection complete !! A total of ${Red_font_prefix}$time${Font_color_suffix} Logs "
echo -e " The test results are stored in "$path$filename"_fi.txt"
}
# List the files in the current path
echo -e " Files in the current path " && ls
# Select the log to analyze
while true;do
read -e -p " Please enter the log to be analyzed :" logfile
find "$logfile" &>/dev/null
if [ $? -ne 0 ];then
echo -e "${Red_font_prefix} No logs found , Please enter the file name or absolute path !!${Font_color_suffix}"
line
else
break
fi
done
filename=$(echo -e "$logfile"| awk -F '/' '{print $NF}') # bbb.log
if [[ $logfile == */* ]];then # logfile=aaa/bbb.log
# 1. Absolute path
path=$(echo -e "$logfile"|grep -o '.*/') # aaa/bbb.log -> aaa/
dirName=$(echo -e "$filename"| awk -F '.' '{print $2}') # log (dir)
[[ -d $dirName ]] || mkdir $path$dirName #aaa/log
path="$path$dirName/" # aaa/log/
# 2. Relative paths # logfile=bbb.log
else
dirName=$(echo -e "$logfile"| awk -F '.' '{print $2}') # log
[[ -d $dirName ]] || mkdir $path$dirName
path="$dirName/" # log/
fi
# *****************************************
# ************** Lord Noodles plate ****************
# *****************************************
line
while true; do
echo -e "web Middleware log analysis script ${Red_font_prefix}[v1.0]${Font_color_suffix} ${Green_font_prefix}1.${Font_color_suffix} Different IP Number of visits ${Green_font_prefix}2.${Font_color_suffix} single IP Access content ${Green_font_prefix}3.${Font_color_suffix} IP Statistics of visits ${Green_font_prefix}4.${Font_color_suffix} Keyword screening ${Green_font_prefix}5.${Font_color_suffix} Upload webshell testing ${Green_font_prefix}6.${Font_color_suffix} Directory scan detection ${Green_font_prefix}7.${Font_color_suffix} Routine vulnerability detection (sqli、xss、ssrf、 Directory traversal 、 File contains ) ${Green_font_prefix}8.${Font_color_suffix} Exit script "
read -e -p " Please enter a number [1-8]:" num
if [ "$num" == "1" ];then
diffip
elif [ "$num" == "2" ];then
oneip
savefile
elif [ "$num" == "3" ];then
howmanyip
elif [ "$num" == "4" ];then
keyword
elif [ "$num" == "5" ];then
webshell
elif [ "$num" == "6" ];then
dirscan
elif [ "$num" == "7" ];then
sqlicheck
xsscheck
ssrfcheck
pathtravelcheck
fileinclude
elif [ "$num" == "8" ];then
echo -e ""
echo -e "${Green_font_prefix} ***************************************** *********** Thank you for using , bye ************ ***************************************** ${Font_color_suffix}"
exit 0
else
echo -e "${Red_font_prefix} Please enter the correct number !!${Font_color_suffix}"
line
continue
fi
line
done
边栏推荐
- [Code] refers to the repeated number in the offer 03 array
- 【软件开发规范四】《应用系统安全编码规范》
- 数据库系统原理与应用教程(056)—— MySQL 查询(十八):其他类型函数的用法
- Django数据库增删改查
- Lock upgrade: no lock, bias lock, lightweight lock, heavyweight lock
- 【RTOS训练营】课程学习方法和结构体知识复习 + 链表知识
- [CTF] crypto preliminary basic outline
- Implementation process of adding loading effect to easycvr page
- Half of the people in the country run in Changsha. Where do half of the people in Changsha run?
- Cf1494f delete the edges (Euler circuit)
猜你喜欢

【RTOS训练营】课程学习方法和C语言知识(指针、结构体、函数指针、链表)和学员问题

What is the dynamic IP address? Why do you recommend dynamic IP proxy?
![[RTOS training camp] task scheduling (Continued), task comity, scheduling summary, queue and evening class questions](/img/0f/ca576a2f90aba4ddbb1f8b3e8a8ced.jpg)
[RTOS training camp] task scheduling (Continued), task comity, scheduling summary, queue and evening class questions

Lua基础语法

ASP. Net core configuration

【RTOS训练营】作业讲解、队列和环形缓冲区、队列——传输数据、队列——同步任务和晚课提问
【RTOS训练营】站在更高的角度学习C语言

AI knows everything: build and deploy sign language recognition system from 0
![[laser principle and application -3]: foreign brands of lasers](/img/8a/620544bb52c6b8c4db83f9a14783bb.png)
[laser principle and application -3]: foreign brands of lasers

Spine_ Adnexal skin
随机推荐
编程学习过程中有哪些快速提高编程技巧的方法?
手游多开用模拟器多开游戏如何切换IP搬砖
Working principle of ZK rollups
jupyter更改主界面并且导入数据集
AI knows everything: build and deploy sign language recognition system from 0
The difference and application of in and exists in SQL statement
1.30 升级bin文件添加后缀及文件长度
JDBC connection database (idea version)
【秒杀概念】原反补
场景之分页查询设计
RHCE之at和crontab命令详解及chrony部署
【RTOS训练营】继续程序框架、tick中断补充、预习、课后作业和晚课提问
Centrosymmetric binary mode cslbp, matlab
Using questpdf operation to generate PDF is faster and more efficient!
Zabbix监控主机及资源告警
【Code】剑指offer 03数组中重复的数字
Detailed explanation of at and crontab commands of RHCE and deployment of Chrony
typing‘ has no attribute ‘_ SpecialForm‘
[RTOS training camp] review of the previous section, idle tasks, timer tasks, execution sequence, scheduling strategy and evening class questions
Lock upgrade: no lock, bias lock, lightweight lock, heavyweight lock