当前位置:网站首页>Raki's notes on reading paper: discontinuous named entity recognition as maximum clique discovery
Raki's notes on reading paper: discontinuous named entity recognition as maximum clique discovery
2022-06-30 02:39:00 【Sleepy Raki】
Abstract & Introduction & Related Work
- Research tasks
Discontinuous NER - Existing methods and related work
- The composite based model first detects all overlaps span, Then learn to combine these fragments with separate classifiers
- The transition based model passes through a series of shifts - The restoring action is not continuous span Make incremental marks
- Facing the challenge
- The existing method divides it into several successive stages , In the reasoning stage, the model output depends on the previous stage , The deviation will be accumulated
- exposure bias
- Innovative ideas
Will be discontinuous NER It is transformed into a nonparametric process of finding the largest clique in the graph , Avoid the problem of being exposed to deviations - The experimental conclusion
sota, Five times the reasoning speed
Review the largest regiment
The biggest group = Maximal independent set of complementary graphs = Total points − Maximum matching number of complementary graphs
Methodology

Grid Tagging Scheme
Construct a n*n Matrix , To each pair token Between a label , Based on their relationship
Be careful , According to the predefined tag set , A tag pair may have multiple tags
Segment Extraction
This two-dimensional matrix is used to represent
s Represents a continuous entity ,B and I representative beginning and inside
Edge Prediction
- Head to head (X-H2H) It means that it is located in a place ( t i , t j ) (t_i , t_j) (ti,tj), among t i t_i ti and t j t_j tj They are composed of X The starting tag of two fragments of the same entity of type
- Tail to tail (X-T2T) And X-H2H be similar , But the point is on the closing tag
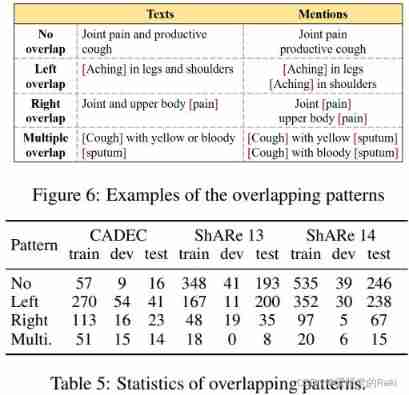
Sever shoulder pain
Decoding Workflow

Model Structure

Token Representation
Coding with a linear layer , But I want to ask the original h i h_i hi Did you jump out of the crack in the stone ? I thought you didn't say ?
Segment Extractor
The probability that a pair of markers are boundary markers of a segment can be expressed as :
Condition layer normalization
A condition vector is used as additional context information to generate gain parameters ,c and x They are the condition vector and the input vector 
be based on CLN Mechanism ,token Yes ( t i , t j ) (t_i , t_j) (ti,tj) The representation of the boundary of a fragment can be defined as :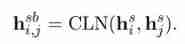
Learn better fragment representation 
Edge Predictor
Edge prediction is similar to segment extraction , Because they all need to learn the representation of each tag pair . The key differences are summarized in the following two aspects .
- The distance between paragraphs is usually uninformative , So the length is embedded e l e n i : j e_{len}^{i:j} eleni:j It is worthless in edge prediction
- Encoding tags between fragments may bring noise semantics of related tags , And increase the burden of training , therefore i:j There is no need for h i : j i n h_{i:j}^{in} hi:jin. Under such consideration , We represent each marker pair used for edge prediction as

Training and Inference
Fully connected layer , Used to predict a pair of token The label of 
Cross entropy loss 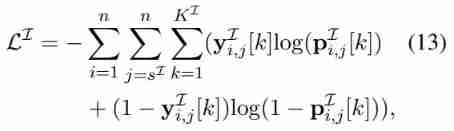
Total loss 
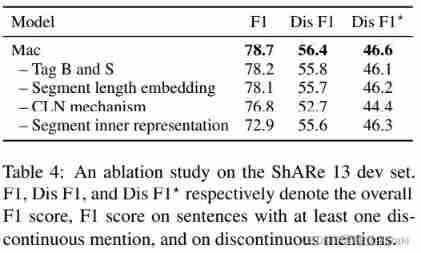
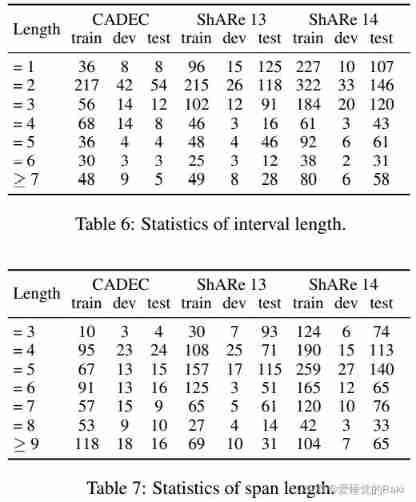
Evaluation






Conclusion
In this paper , We will be discontinuous NER Reformulated as the task of finding the largest clique in the fragment graph , A novel Mac framework . It decomposes the construction of fragment graph into two independent two-dimensional grid marking problems , And solve it together in one stage , It solves the problem of exposure bias in previous studies . Extensive experiments on three benchmark data sets show that ,Mac stay F1 Than before SOTA Method higher than 3.5 percentage , At the same time, the speed is fast 5 times . Further analysis shows that , Our model has the ability to identify discontinuous and overlapping entity references . some time , We hope to explore similar expressions in other information extraction tasks , Such as event extraction and nesting NER
Remark
novelty yes , we have , But it is not beautiful to realize , The experiment was done very well , That's OK
边栏推荐
- What is the difference between a layer 3 switch and a layer 2 switch
- 2.8 【 weight of complete binary tree 】
- Several key points recorded after reviewing redis design and Implementation
- Cmake tutorial series -02- generating binaries using cmake code
- 打造创客教育中精湛技艺
- Shenzhen CPDA Data Analyst Certification in July 2022
- CMake教程系列-05-选项及变量
- 1380. lucky numbers in matrices
- Simple distinction between break and continue
- DigiCert Smart Seal是什么?
猜你喜欢

IBM WebSphere channel connectivity setup and testing

Unity3d ugui force refresh of layout components

直接插入排序

Créer des compétences exquises dans l'éducation des créateurs

Quick sort

What are the requirements for NPDP product manager international certification examination?

如何预防钓鱼邮件?S/MIME邮件证书来支招

Seven common errors of SSL certificate and their solutions

Simple distinction between break and continue

FDA ESG regulation: digital certificate must be used to ensure communication security
随机推荐
微信小程序页面跳转以及参数传递
Unity TimeLine 数据绑定
Traffic, but no sales? 6 steps to increase website sales
FDA ESG regulation: digital certificate must be used to ensure communication security
Global and Chinese markets for wireless security in LTE networks 2022-2028: Research Report on technology, participants, trends, market size and share
What is a self signed certificate? Advantages and disadvantages of self signed SSL certificates?
Xunwei NXP itop-imx6 development platform
选购通配符SSL证书注意事项
Enlightenment from the revocation of Russian digital certificate by mainstream CA: upgrade the SSL certificate of state secret algorithm to help China's network security to be autonomous and controlla
打造創客教育中精湛技藝
什么是证书透明度CT?如何查询CT logs证书日志?
What is digicert smart seal?
Global and Chinese market of mobile commerce solutions 2022-2028: Research Report on technology, participants, trends, market size and share
CMake教程系列-02-使用cmake代码生成二进制
What is an X.509 certificate? 10. 509 certificate working principle and application?
Digicert、Sectigo、Globalsign代码签名证书的区别
day33
Quick sort
Shell Sort
2022 the action of protecting the net is imminent. Things about protecting the net