当前位置:网站首页>Sogou wechat app reverse (II) so layer
Sogou wechat app reverse (II) so layer
2022-07-01 22:46:00 【Codeooo】
Then, above :https://blog.csdn.net/weixin_38927522/article/details/124726015
This analysis Sogou app so Layer encryption related logic .
First, look in the export function :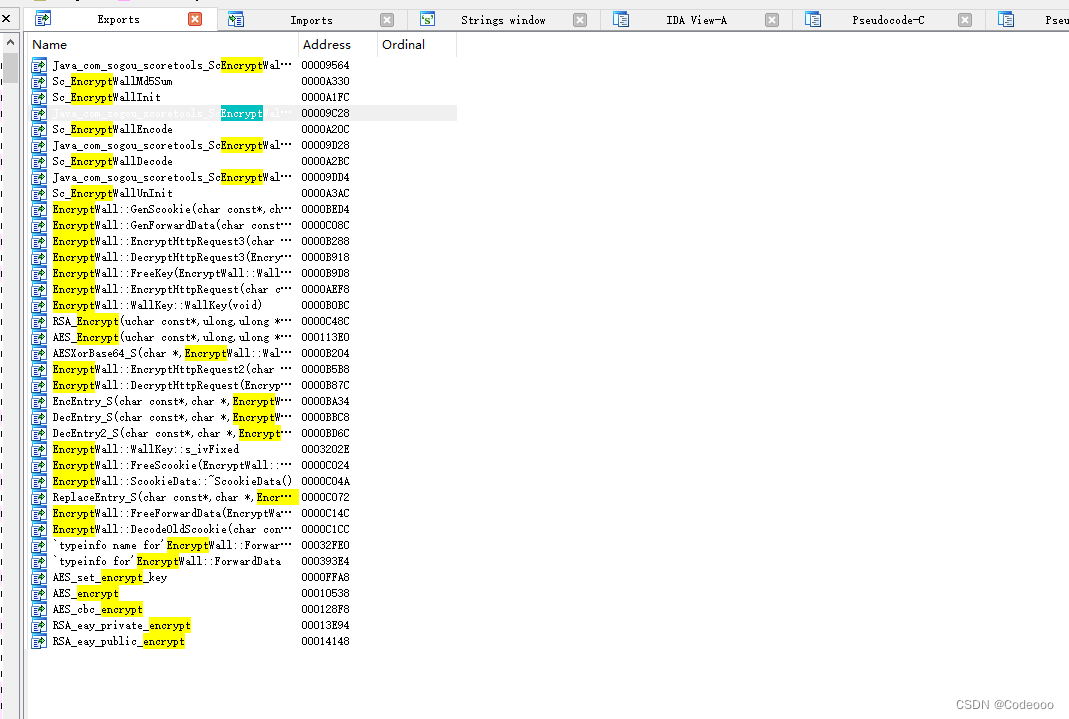
Click in Java_com_sogou_scoretools_ScEncryptWall_encrypt see 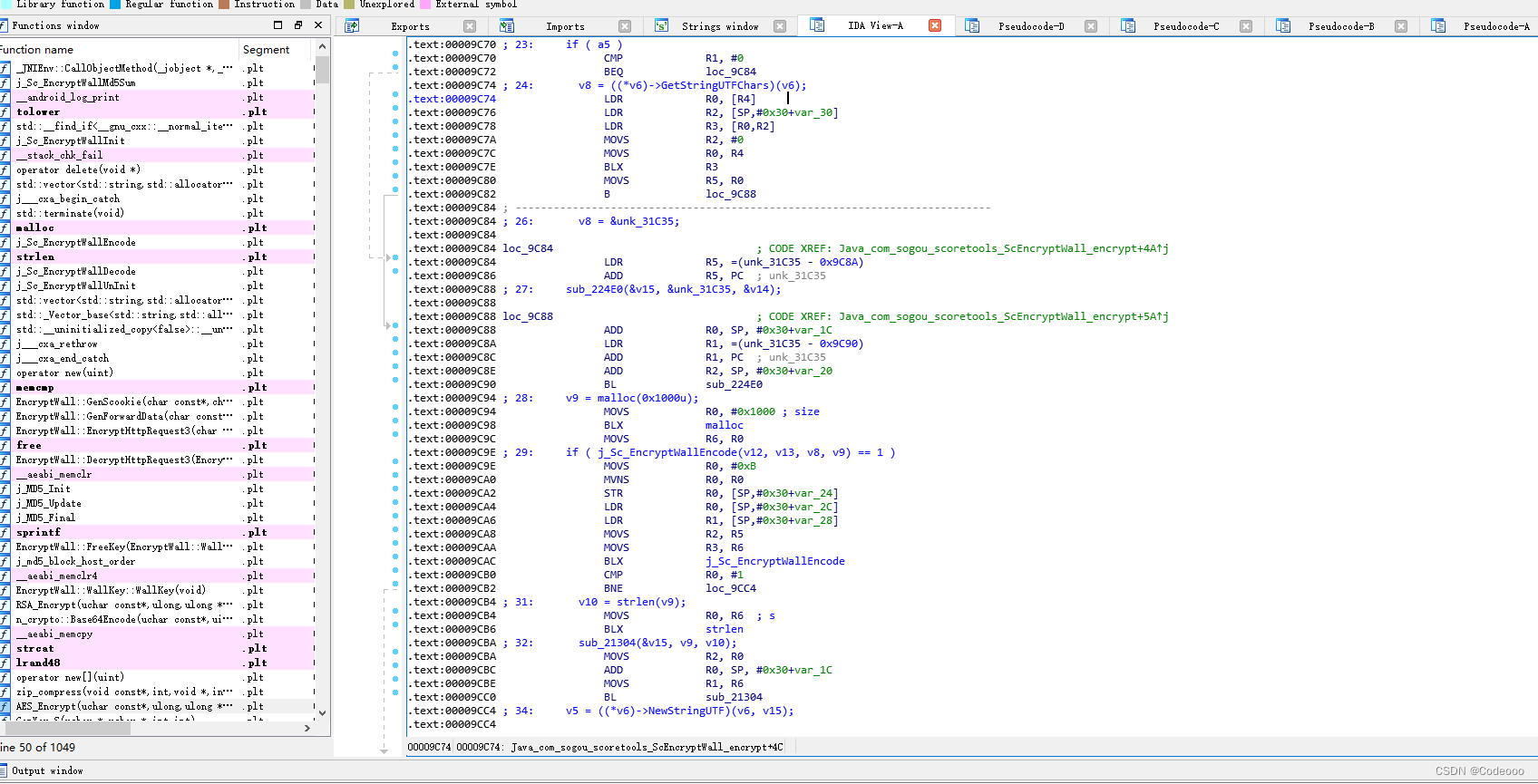

GetStringUTF Turn into C# String ,utf code .
malloc Open up space
j_Sc_EncryptWallEncode According to the code logic, this is the core code
Keep going :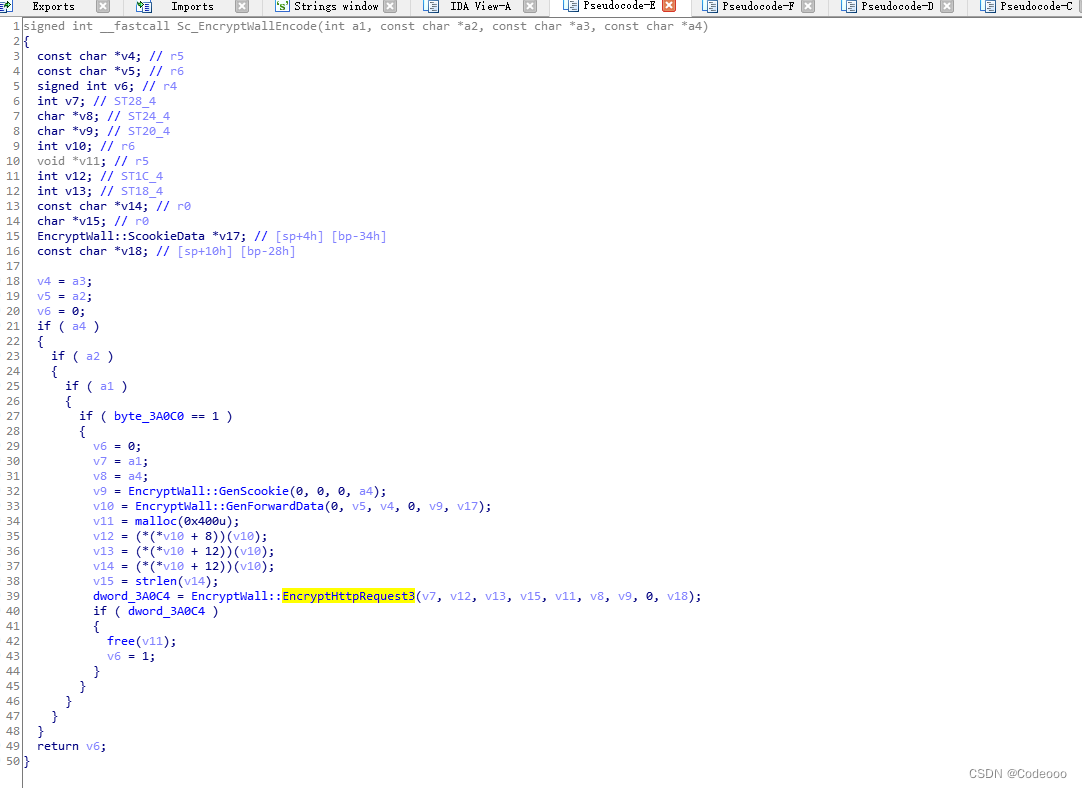
Entering this function, let's look at the parameters , according to jni The first two are fixed , The following parameters are passed in .
Our static analysis , Change it manually jni head , Make it faster and better to recognize .
int __fastcall Java_com_sogou_scoretools_ScEncryptWall_encrypt(JNIEnv *env, jclass clazz, int a3, int a4, int a5)
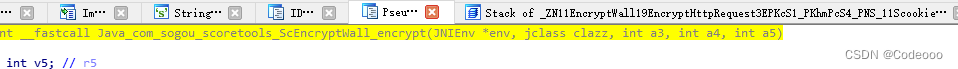
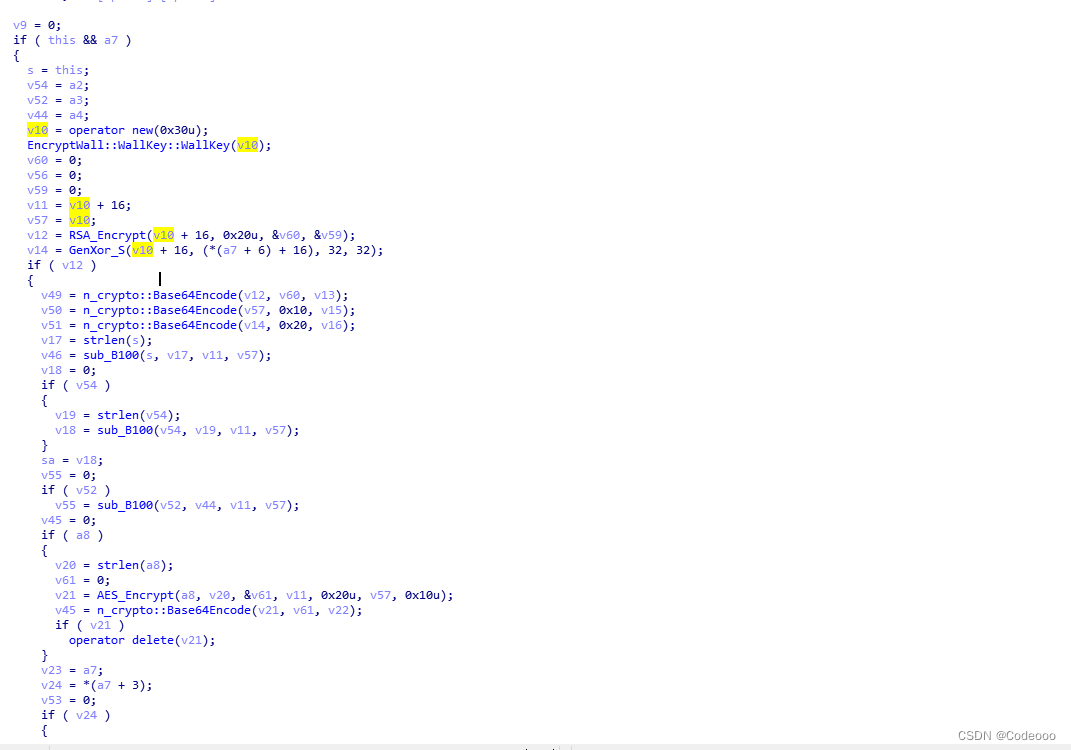
See this one The parameter encrypted string is as follows :
v10 = operator new(0x30u);
EncryptWall::WallKey::WallKey(v10);
Apply for one 30 Byte space memory address assignment v10, take v10 Pass in 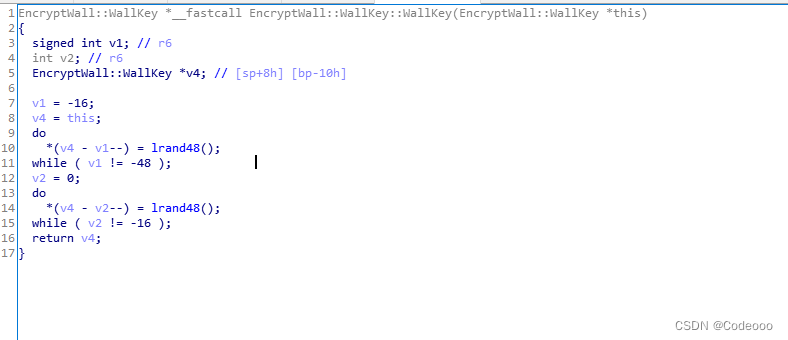
It looks like a cyclic filling , Fill the memory space just now .
v12 = RSA_Encrypt(v10 + 16, 0x20u, &v60, &v59);
Push back :v10 : open up 30 Byte memory address +16 Bytes &v60:v60 Address of a pointer , &v59 :v59 Address of a pointer

So this this What is it , In fact, that is url
a2 a3 It's analytical postdata
RSA encryption :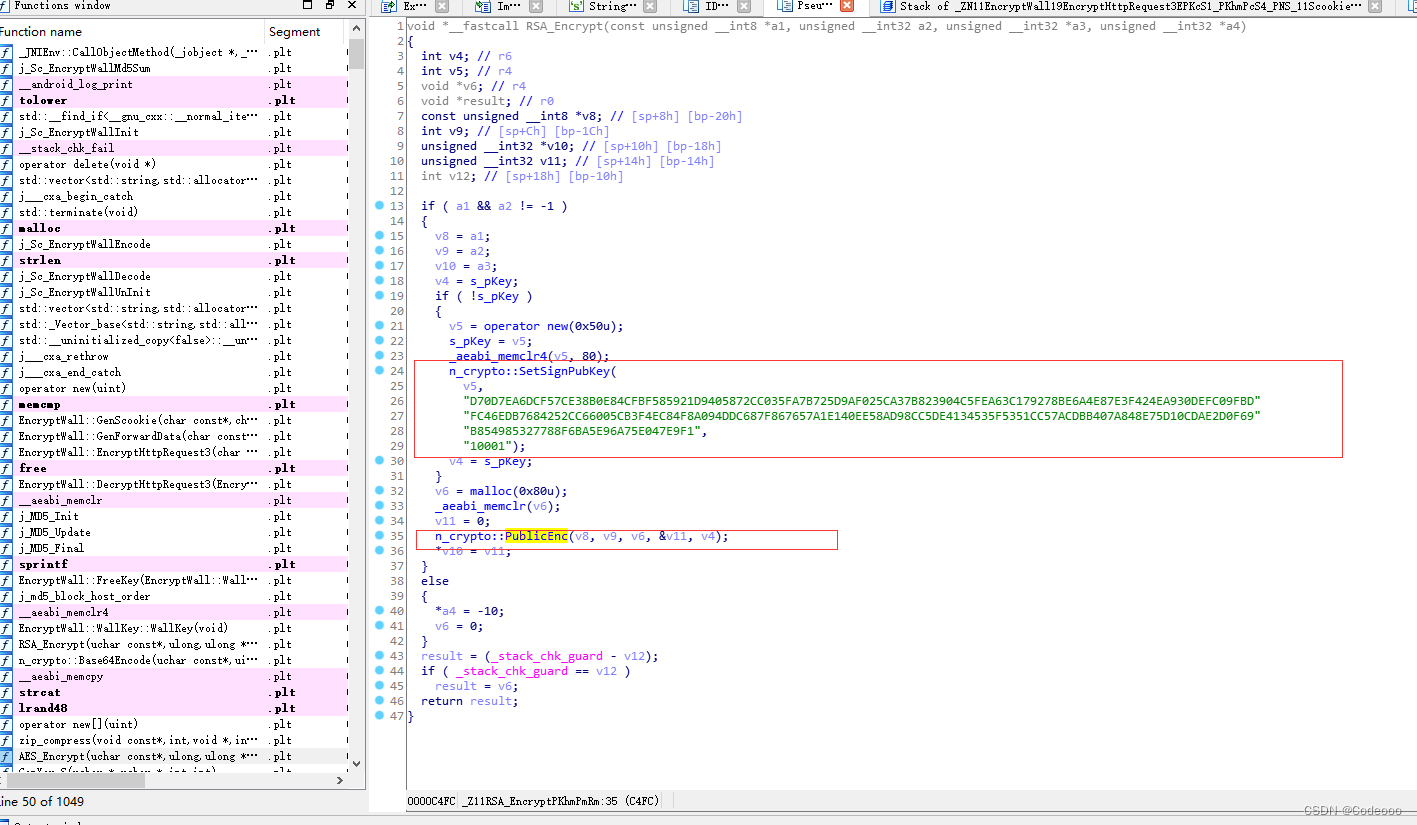
Secret key generation method , One is post generation encryption .
n_crypto::SetSignPubKey : Secret key
n_crypto::PublicEnc It looks like rsa Finally, the encryption method , Let's go check it out 
And we observe the parameters ,n_crypto::PublicEnc(v8, v9, v6, &v11, v4);
v8: a1: Pass in the first parameter
v9: a2: Pass in the second parameter
v6: 80 Byte space memory This can be suspected of being received as a return value
&v11 :v11 Address
v4 : Secret key
I am here HOOK I found that I didn't leave n_crypto::SetSignPubKey( Logic .
"""20220402"""
SetSignPubKey1 = """
Java.perform(function(){
var str_name_so = "libSCoreTools.so"; // want hook Of so name
var n_addr_func_offset = 0x0111E4;
// After loading into memory Function address = so Address + Function offset
var n_addr_so = Module.findBaseAddress(str_name_so);
console.log("func addr is ---" + n_addr_so);
var n_addr_func = n_addr_so.add(n_addr_func_offset+1);
Interceptor.attach(n_addr_func,
{
onEnter: function(args)
{
console.log("hook on enter no exp");
console.log("-----------0----------")
console.log(hexdump(args[0]))
console.log("-----------1----------")
console.log(hexdump(args[1]))
console.log("------------2---------")
console.log(args[2])
},
onLeave:function(retval)
{
console.log("hook on Leave no exp");
console.log(hexdump(retval))
console.log("return:"+retval);
}
});
});
"""

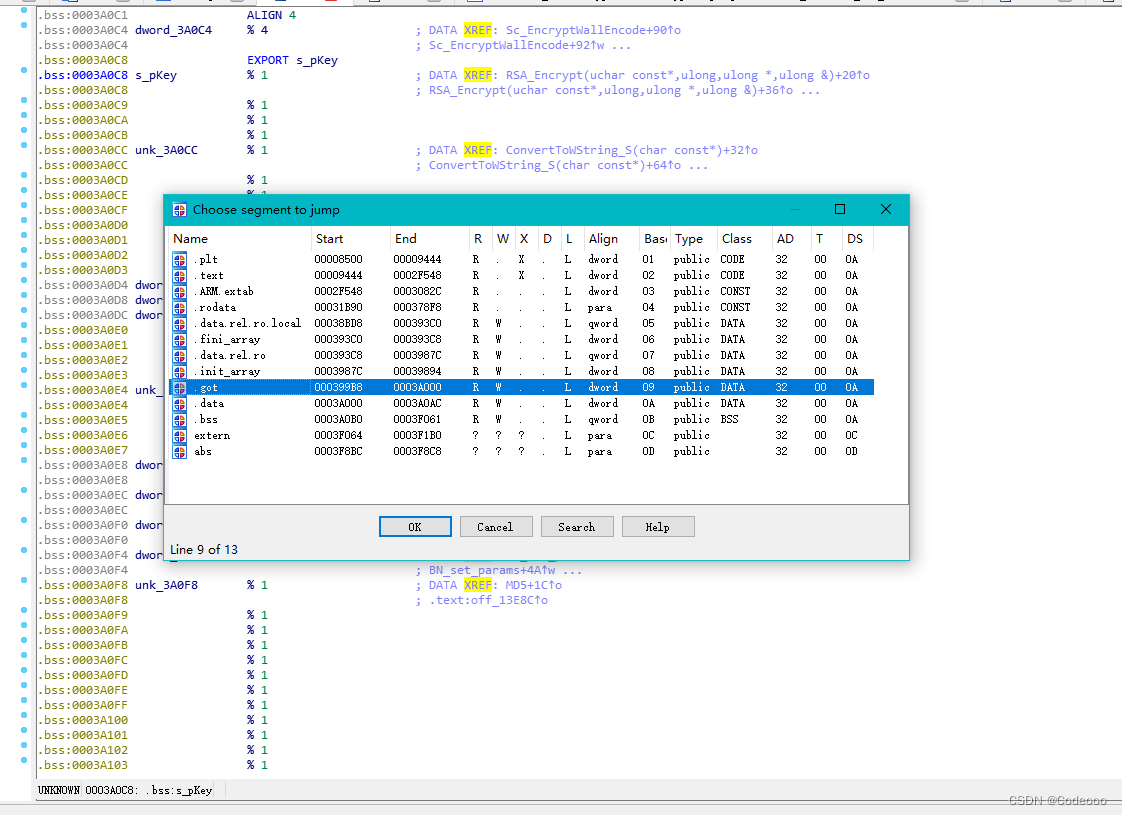
This is a plt section It's for jump Will jump to got surface The two instructions are short instructions Probably hook Less than Keep following
plt:00008A18 ADRL R12, 0x39A20
.plt:00008A20 LDR PC, [R12,#(_ZN8n_crypto12SetEncKeySymEP10aes_key_stPKvi_ptr - 0x39A20)]! ; n_crypt
got:00039C9C _ZN8n_crypto12SetEncKeySymEP10aes_key_stPKvi_ptr DCD _ZN8n_crypto12SetEncKeySymEP10aes_key_stPKvi+1
See a lot of XOR operations ,,,, This is the characteristic of encryption type
so: if ( !s_pKey ) It doesn't work .
We need memory dumps Secret key 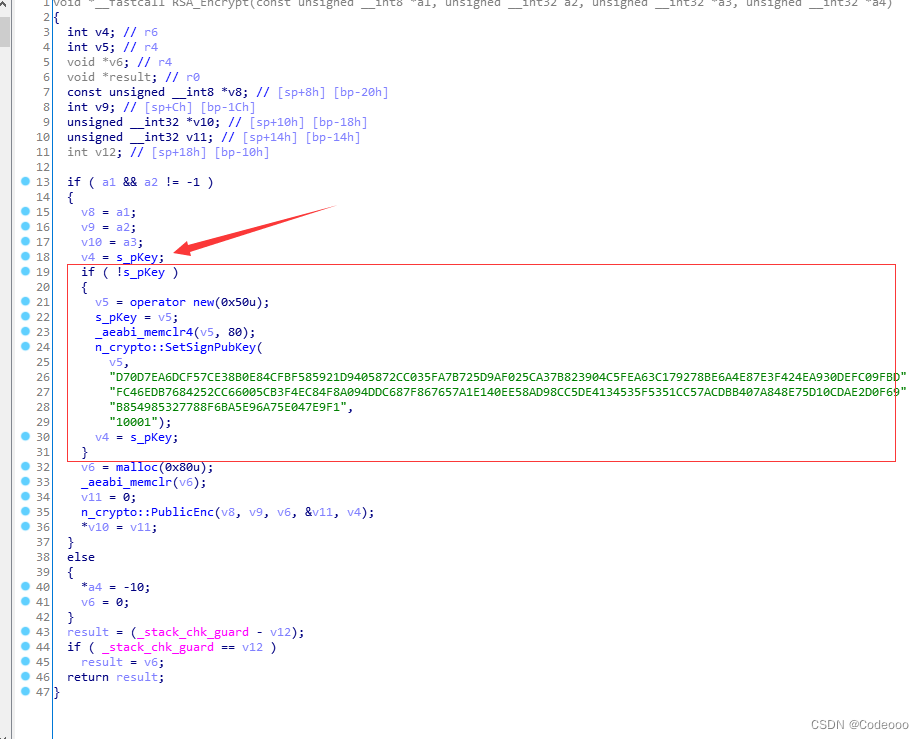
dump Script :

Keep going down , GenXor_S(v10 + 16, (*(a7 + 6) + 16), 32, 32);

This custom some logic , Just pull it out .
Next I see n_crypto::Base64Encode base64 operation
Let's first see if there is a replacement code table , Is there any magic modification method .

Came in and checked , At least the code meter has not been replaced , In the future interview, you will never know base64 How much is the code table ?

Then we click on this function to see :
v11 = zip_compress(v7, v6, v9, v8, &v17);
Compression method : follow-up hook Next parameter .
v12 = AES_Encrypt(v10, v11, &v16, v5, 0x20u, v4, 0x10u);
Next we see AES encryption :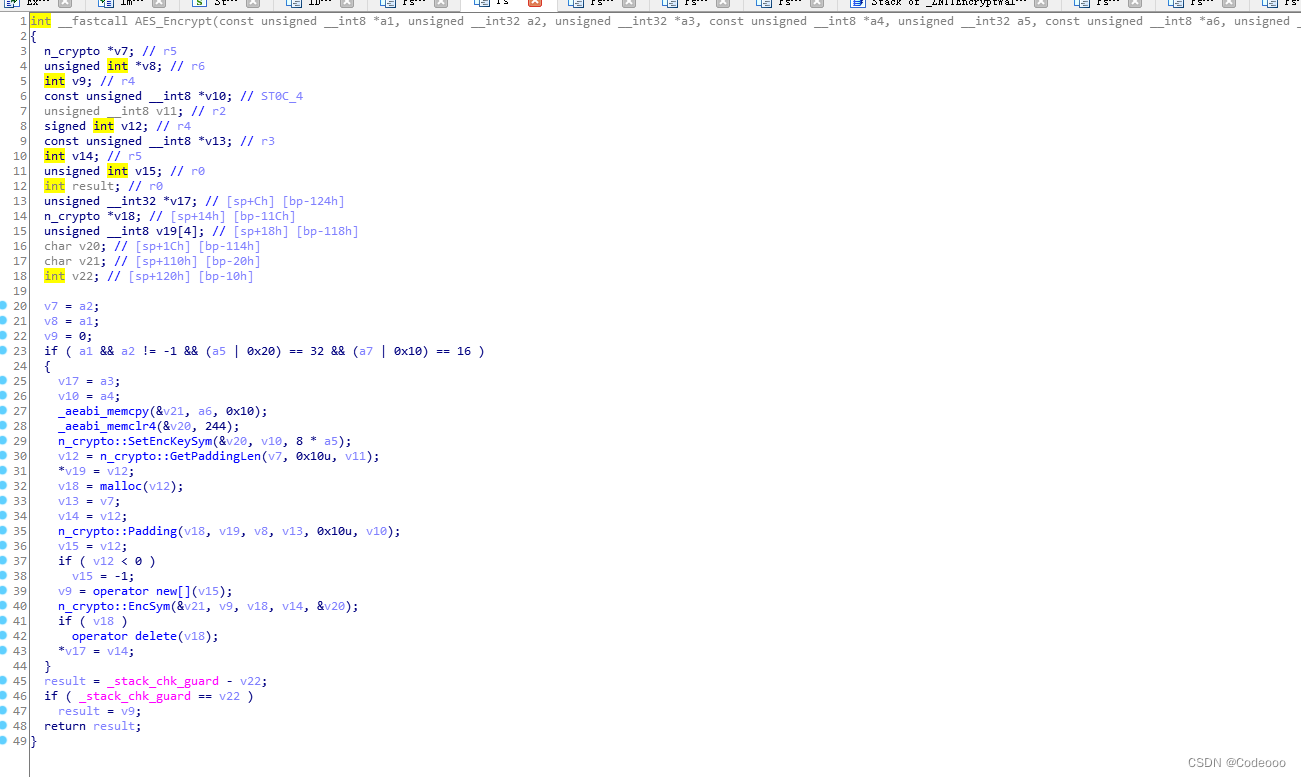
n_crypto::SetEncKeySym Set secret key
routine :
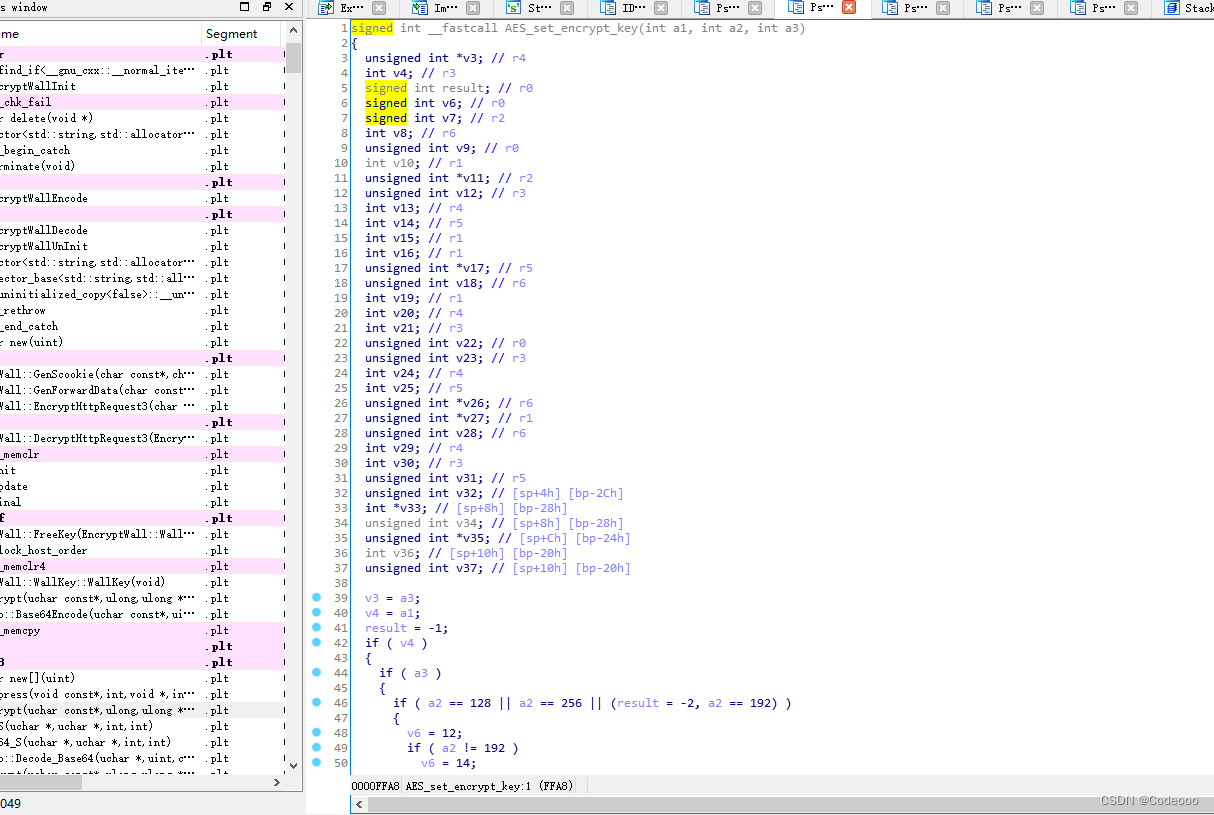
AES_set_encrypt_key(aes_key, sizeof(aes_key) * 8, &enc_key);
n_crypto::SetEncKeySym(&v20, v10, 8 * a5);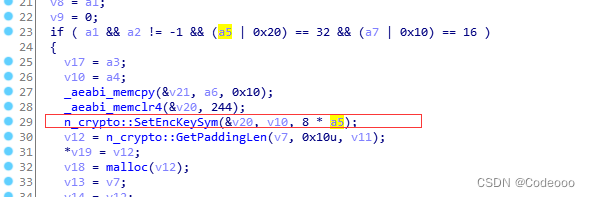
Parametric analysis : v20 Address , v10 = a4; Parameters ,8 * a5 = 8 *32 = 256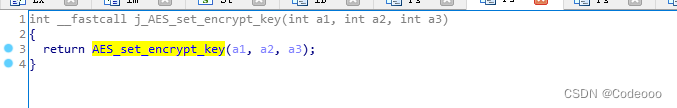
n_crypto::GetPaddingLen fill style
v12 = n_crypto::GetPaddingLen(v7, 0x10u, v11);
Let's take a look at the last encryption process :
n_crypto::EncSym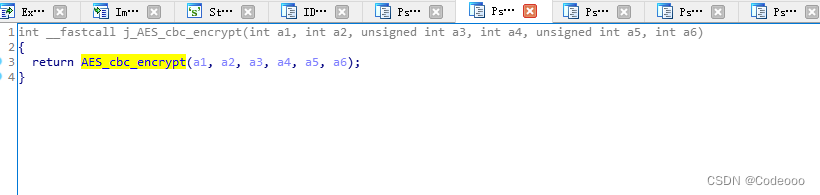
AES Of cbc Pattern aes -cbc -256
n_crypto::EncSym(&v21, v9, v18, v14, &v20);
AES_set_encrypt_key(aes_key, sizeof(aes_key) * 8, &enc_key);
This is the original function type Adopted openssl library
Y3wQ+xj1oWTxGhO3bdsLdPQJCeSCKPfZuK1gQsMAxg8=
uK1gQsMAxg8=....A B C D E F 0123456789ABCDEF
cb2d5b60 c3 11 a3 f5 cc fa 9f 42 eb ef b2 1f 47 57 92 66 .......B....GW.f
cb2d5b70 11 08 ba 88 6b e4 6e 01 f4 a0 4b ed f2 a0 8a b5 ....k.n...K.....
cb2d5b80 54 65 63 68 6e 6f 6c 6f 67 79 20 61 6e 64 20 45 Technology and E
cb2d5b90 6e 67 69 6e 65 65 72 69 6e 67 20 44 65 70 61 72 ngineering Depar
cb2d5ba0 74 6d 65 6e 74 00 00 00 00 00 00 00 00 00 00 00 tment...........
cb2d5bb0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5bc0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5bd0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5be0 77 61 70 2e 73 6f 67 6f 75 2e 63 6f 6d 3a 34 34 wap.sogou.com:44
cb2d5bf0 33 2f 68 74 74 70 5f 6e 65 74 77 6f 72 6b 5f 73 3/http_network_s
cb2d5c00 65 73 73 69 6f 6e 2f 30 2f 31 30 00 ff ff ff ff ession/0/10.....
cb2d5c10 54 65 63 68 6e 6f 6c 6f 67 79 20 61 6e 64 20 45 Technology and E
cb2d5c20 6e 67 69 6e 65 65 72 69 6e 67 20 44 65 70 61 72 ngineering Depar
cb2d5c30 74 6d 65 6e 74 00 6f 2e 2c 20 4c 74 64 2e 00 00 tment.o., Ltd...
cb2d5c40 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5c50 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
Return value : 0x0
Parameter values :
0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
cb2d5b60 c3 11 a3 f5 cc fa 9f 42 eb ef b2 1f 47 57 92 66 .......B....GW.f
cb2d5b70 11 08 ba 88 6b e4 6e 01 f4 a0 4b ed f2 a0 8a b5 ....k.n...K.....
cb2d5b80 54 65 63 68 6e 6f 6c 6f 67 79 20 61 6e 64 20 45 Technology and E
cb2d5b90 6e 67 69 6e 65 65 72 69 6e 67 20 44 65 70 61 72 ngineering Depar
cb2d5ba0 74 6d 65 6e 74 00 00 00 00 00 00 00 00 00 00 00 tment...........
cb2d5bb0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5bc0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5bd0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5be0 77 61 70 2e 73 6f 67 6f 75 2e 63 6f 6d 3a 34 34 wap.sogou.com:44
cb2d5bf0 33 2f 68 74 74 70 5f 6e 65 74 77 6f 72 6b 5f 73 3/http_network_s
cb2d5c00 65 73 73 69 6f 6e 2f 30 2f 31 30 00 ff ff ff ff ession/0/10.....
cb2d5c10 54 65 63 68 6e 6f 6c 6f 67 79 20 61 6e 64 20 45 Technology and E
cb2d5c20 6e 67 69 6e 65 65 72 69 6e 67 20 44 65 70 61 72 ngineering Depar
cb2d5c30 74 6d 65 6e 74 00 6f 2e 2c 20 4c 74 64 2e 00 00 tment.o., Ltd...
cb2d5c40 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5c50 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
Return value : 0x0
Parameter values :
0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
cb2d5b60 c3 11 a3 f5 cc fa 9f 42 eb ef b2 1f 47 57 92 66 .......B....GW.f
cb2d5b70 11 08 ba 88 6b e4 6e 01 f4 a0 4b ed f2 a0 8a b5 ....k.n...K.....
cb2d5b80 54 65 63 68 6e 6f 6c 6f 67 79 20 61 6e 64 20 45 Technology and E
cb2d5b90 6e 67 69 6e 65 65 72 69 6e 67 20 44 65 70 61 72 ngineering Depar
cb2d5ba0 74 6d 65 6e 74 00 00 00 00 00 00 00 00 00 00 00 tment...........
cb2d5bb0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5bc0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5bd0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5be0 77 61 70 2e 73 6f 67 6f 75 2e 63 6f 6d 3a 34 34 wap.sogou.com:44
cb2d5bf0 33 2f 68 74 74 70 5f 6e 65 74 77 6f 72 6b 5f 73 3/http_network_s
cb2d5c00 65 73 73 69 6f 6e 2f 30 2f 31 30 00 ff ff ff ff ession/0/10.....
cb2d5c10 54 65 63 68 6e 6f 6c 6f 67 79 20 61 6e 64 20 45 Technology and E
cb2d5c20 6e 67 69 6e 65 65 72 69 6e 67 20 44 65 70 61 72 ngineering Depar
cb2d5c30 74 6d 65 6e 74 00 6f 2e 2c 20 4c 74 64 2e 00 00 tment.o., Ltd...
cb2d5c40 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5c50 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
Return value : 0x0
Parameter values :
0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
cb2d5b60 c3 11 a3 f5 cc fa 9f 42 eb ef b2 1f 47 57 92 66 .......B....GW.f
cb2d5b70 11 08 ba 88 6b e4 6e 01 f4 a0 4b ed f2 a0 8a b5 ....k.n...K.....
cb2d5b80 54 65 63 68 6e 6f 6c 6f 67 79 20 61 6e 64 20 45 Technology and E
cb2d5b90 6e 67 69 6e 65 65 72 69 6e 67 20 44 65 70 61 72 ngineering Depar
cb2d5ba0 74 6d 65 6e 74 00 00 00 00 00 00 00 00 00 00 00 tment...........
cb2d5bb0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5bc0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5bd0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5be0 77 61 70 2e 73 6f 67 6f 75 2e 63 6f 6d 3a 34 34 wap.sogou.com:44
cb2d5bf0 33 2f 68 74 74 70 5f 6e 65 74 77 6f 72 6b 5f 73 3/http_network_s
cb2d5c00 65 73 73 69 6f 6e 2f 30 2f 31 30 00 ff ff ff ff ession/0/10.....
cb2d5c10 54 65 63 68 6e 6f 6c 6f 67 79 20 61 6e 64 20 45 Technology and E
cb2d5c20 6e 67 69 6e 65 65 72 69 6e 67 20 44 65 70 61 72 ngineering Depar
cb2d5c30 74 6d 65 6e 74 00 6f 2e 2c 20 4c 74 64 2e 00 00 tment.o., Ltd...
cb2d5c40 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
cb2d5c50 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
Return value : 0x0
[Pixel:: Sogou search ]->
[Pixel:: Sogou search ]->
[Pixel:: Sogou search ]->
[Pixel:: Sogou search ]->
[Pixel:: Sogou search ]-> Parameter values :
0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
cb2d3130 44 72 b6 41 a7 94 3f 45 68 38 f4 d1 c7 93 fb 01 Dr.A..?Eh8......
cb2d3140 79 f4 2e b8 99 69 20 19 2c 82 ae 0e 4f 2d 3d 05 y....i .,...O-=.
cb2d3150 fc 25 4f ee 24 00 00 00 04 4e 41 ee 00 00 6f 00 .%O.$....NA...o.
cb2d3160 00 00 00 00 61 00 63 00 00 00 00 00 00 00 00 00 ....a.c.........
cb2d3170 00 00 00 00 00 00 73 00 00 00 00 00 00 00 00 00 ......s.........
cb2d3180 4c 6f 63 61 6c 41 73 79 6e 63 20 54 68 72 65 61 LocalAsync Threa
cb2d3190 64 20 23 33 30 00 20 6d 61 6e 61 67 65 64 20 70 d #30. managed p
cb2d31a0 65 65 72 3e 00 00 00 00 00 00 00 00 00 00 00 00 eer>............
cb2d31b0 46 72 65 73 63 6f 44 65 63 6f 64 65 45 78 65 63 FrescoDecodeExec
cb2d31c0 75 74 6f 72 2d 33 00 6d 61 6e 61 67 65 64 20 70 utor-3.managed p
cb2d31d0 65 65 72 3e 00 79 00 2f 2e 2e 2e 00 70 73 3b 00 eer>.y./....ps;.
cb2d31e0 fc 25 4f ee 24 00 00 00 04 4e 41 ee 00 72 69 74 .%O.$....NA..rit
cb2d31f0 00 00 00 00 74 77 6f 72 00 00 00 00 00 00 00 00 ....twor........
cb2d3200 01 00 00 00 00 63 79 3b 00 00 00 00 00 00 00 00 .....cy;........
cb2d3210 00 00 00 00 d0 9e 5a a8 31 00 00 00 24 00 00 00 ......Z.1...$...
cb2d3220 b0 2e 31 cd 31 00 00 00 24 00 00 00 70 32 2d cb ..1.1...$...p2-.
Return value : 0x0
Parameter values :
0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
cb2d3130 44 72 b6 41 a7 94 3f 45 68 38 f4 d1 c7 93 fb 01 Dr.A..?Eh8......
cb2d3140 79 f4 2e b8 99 69 20 19 2c 82 ae 0e 4f 2d 3d 05 y....i .,...O-=.
cb2d3150 fc 25 4f ee 24 00 00 00 04 4e 41 ee 00 00 6f 00 .%O.$....NA...o.
cb2d3160 00 00 00 00 61 00 63 00 00 00 00 00 00 00 00 00 ....a.c.........
cb2d3170 00 00 00 00 00 00 73 00 00 00 00 00 00 00 00 00 ......s.........
cb2d3180 4c 6f 63 61 6c 41 73 79 6e 63 20 54 68 72 65 61 LocalAsync Threa
cb2d3190 64 20 23 33 30 00 20 6d 61 6e 61 67 65 64 20 70 d #30. managed p
cb2d31a0 65 65 72 3e 00 00 00 00 00 00 00 00 00 00 00 00 eer>............
cb2d31b0 46 72 65 73 63 6f 44 65 63 6f 64 65 45 78 65 63 FrescoDecodeExec
cb2d31c0 75 74 6f 72 2d 33 00 6d 61 6e 61 67 65 64 20 70 utor-3.managed p
cb2d31d0 65 65 72 3e 00 79 00 2f 2e 2e 2e 00 70 73 3b 00 eer>.y./....ps;.
cb2d31e0 fc 25 4f ee 24 00 00 00 04 4e 41 ee 00 72 69 74 .%O.$....NA..rit
cb2d31f0 00 00 00 00 74 77 6f 72 00 00 00 00 00 00 00 00 ....twor........
cb2d3200 01 00 00 00 00 63 79 3b 00 00 00 00 00 00 00 00 .....cy;........
cb2d3210 00 00 00 00 d0 9e 5a a8 31 00 00 00 24 00 00 00 ......Z.1...$...
cb2d3220 b0 2e 31 cd 31 00 00 00 24 00 00 00 70 32 2d cb ..1.1...$...p2-.
Return value : 0x0
Parameter values :
0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
cb2d3130 44 72 b6 41 a7 94 3f 45 68 38 f4 d1 c7 93 fb 01 Dr.A..?Eh8......
cb2d3140 79 f4 2e b8 99 69 20 19 2c 82 ae 0e 4f 2d 3d 05 y....i .,...O-=.
cb2d3150 fc 25 4f ee 24 00 00 00 04 4e 41 ee 00 00 6f 00 .%O.$....NA...o.
cb2d3160 00 00 00 00 61 00 63 00 00 00 00 00 00 00 00 00 ....a.c.........
cb2d3170 00 00 00 00 00 00 73 00 00 00 00 00 00 00 00 00 ......s.........
cb2d3180 4c 6f 63 61 6c 41 73 79 6e 63 20 54 68 72 65 61 LocalAsync Threa
cb2d3190 64 20 23 33 30 00 20 6d 61 6e 61 67 65 64 20 70 d #30. managed p
cb2d31a0 65 65 72 3e 00 00 00 00 00 00 00 00 00 00 00 00 eer>............
cb2d31b0 46 72 65 73 63 6f 44 65 63 6f 64 65 45 78 65 63 FrescoDecodeExec
cb2d31c0 75 74 6f 72 2d 33 00 6d 61 6e 61 67 65 64 20 70 utor-3.managed p
cb2d31d0 65 65 72 3e 00 79 00 2f 2e 2e 2e 00 70 73 3b 00 eer>.y./....ps;.
cb2d31e0 fc 25 4f ee 24 00 00 00 04 4e 41 ee 00 72 69 74 .%O.$....NA..rit
cb2d31f0 00 00 00 00 74 77 6f 72 00 00 00 00 00 00 00 00 ....twor........
cb2d3200 01 00 00 00 00 63 79 3b 00 00 00 00 00 00 00 00 .....cy;........
cb2d3210 00 00 00 00 d0 9e 5a a8 31 00 00 00 24 00 00 00 ......Z.1...$...
cb2d3220 b0 2e 31 cd 31 00 00 00 24 00 00 00 70 32 2d cb ..1.1...$...p2-.
Return value : 0x0
Parameter values :
0 1 2 3 4 5 6 7 8 9 A B C D E F 0123456789ABCDEF
cb2d3130 44 72 b6 41 a7 94 3f 45 68 38 f4 d1 c7 93 fb 01 Dr.A..?Eh8......
cb2d3140 79 f4 2e b8 99 69 20 19 2c 82 ae 0e 4f 2d 3d 05 y....i .,...O-=.
cb2d3150 fc 25 4f ee 24 00 00 00 04 4e 41 ee 00 00 6f 00 .%O.$....NA...o.
cb2d3160 00 00 00 00 61 00 63 00 00 00 00 00 00 00 00 00 ....a.c.........
cb2d3170 00 00 00 00 00 00 73 00 00 00 00 00 00 00 00 00 ......s.........
cb2d3180 4c 6f 63 61 6c 41 73 79 6e 63 20 54 68 72 65 61 LocalAsync Threa
cb2d3190 64 20 23 33 30 00 20 6d 61 6e 61 67 65 64 20 70 d #30. managed p
cb2d31a0 65 65 72 3e 00 00 00 00 00 00 00 00 00 00 00 00 eer>............
cb2d31b0 46 72 65 73 63 6f 44 65 63 6f 64 65 45 78 65 63 FrescoDecodeExec
cb2d31c0 75 74 6f 72 2d 33 00 6d 61 6e 61 67 65 64 20 70 utor-3.managed p
cb2d31d0 65 65 72 3e 00 79 00 2f 2e 2e 2e 00 70 73 3b 00 eer>.y./....ps;.
cb2d31e0 fc 25 4f ee 24 00 00 00 04 4e 41 ee 00 72 69 74 .%O.$....NA..rit
cb2d31f0 00 00 00 00 74 77 6f 72 00 00 00 00 00 00 00 00 ....twor........
cb2d3200 01 00 00 00 00 63 79 3b 00 00 00 00 00 00 00 00 .....cy;........
This is the key point of the function encryption
Every call will go
See a lot below XorBase64_S To assign other parameters , Let's go in and have a look :
Its logic is indisputable from the above .
边栏推荐
猜你喜欢
完全注解的ssm框架搭建

Fiori 应用通过 Adaptation Project 的增强方式分享
陈天奇的机器学习编译课(免费)

Appium automated testing foundation - Supplement: introduction to desired capabilities parameters

CIO's discussion and Analysis on the definition of high-performance it team

Ffmpeg learning notes

3DE resources have nothing or nothing wrong

Slope compensation
性能测试计划怎么编写

Selection of all-optical technology in the park - Part 2
随机推荐
spark analyze命令使用及其作用 map join broadcast join 广播join
YOLOv5.5 调用本地摄像头
小红书Scheme跳转到指定页面
RestTemplate 远程调用工具类
元宇宙可能成为互联网发展的新方向
[jetcache] how to use jetcache
awoo‘s Favorite Problem(优先队列)
互联网的智算架构设计
Pytorch's code for visualizing feature maps after training its own network
高攀不起的希尔排序,直接插入排序
Configure filter
Sonic cloud real machine learning summary 6 - 1.4.1 server and agent deployment
Rust语言——小小白的入门学习05
Kubernetes创建Service访问Pod
GenICam GenTL 标准 ver1.5(4)第五章 采集引擎
Explain kubernetes network model in detail
Mysql5.7 set password policy (etc. three-level password transformation)
Yolov5.5 call local camera
【JetCache】JetCache的使用方法与步骤
Relationship and difference between enterprise architecture and project management