当前位置:网站首页>Stack frame
Stack frame
2022-07-01 00:33:00 【Wan Xi a Shuai】
Stack frame stack frame
Every function call will maintain a stack frame (stack frame), Stack frame is mainly used to pass parameters 、 Save return address 、 Save local variables, etc . First go directly to the previous one 《 Deep understanding of computer systems 》 Original image on .
among ,%rsp Point to the top of the stack ,%rbp Point to the bottom of the stack . And the stack grows from high address to address .
The layout of local variables is determined by the compiler , It may be from a high address to a low address , It may also change from low address to high address .
Before the called function 6 Parameters will be passed in by registers , exceed 6 The part of will be passed through the stack . What needs to be noted here is , In order to get the address of the input parameter in the called function , The called function will be before 6 Parameters are pushed into the stack of the called function .
Function call procedure :
- Parameter stack . In a certain order, the parameters will exceed 6 Stack the parameters after .
- Return the address to the stack . Push an instruction address of the current code onto the stack , Function returns to continue execution .
- Jump into the address of the called function .
- EBP Push , Save the current stack frame state value .
- ESP Value is assigned to EBP.
- Allocate the current stack frame .
Function return procedure :
- Save the return value of the called function to EAX In the register .
- recovery ESP.
- The calling function stack frame saved at the bottom of the called function EBP Value pop in EBP register , Recover the calling function stack frame .
- Pop up the current stack top element , Get the return address from the stack .
Here is an example to verify the next stack frame layout :
Enter the first main Functional func Function call point :

%rbp The value is 0x7fffffffe110,%rsp The value of is 0x7fffffffe0f0. The address of the next instruction can be obtained from disassembly 0x4008f4. Based on this information, we can deduce main Functions and func The stack frame of the function is as follows :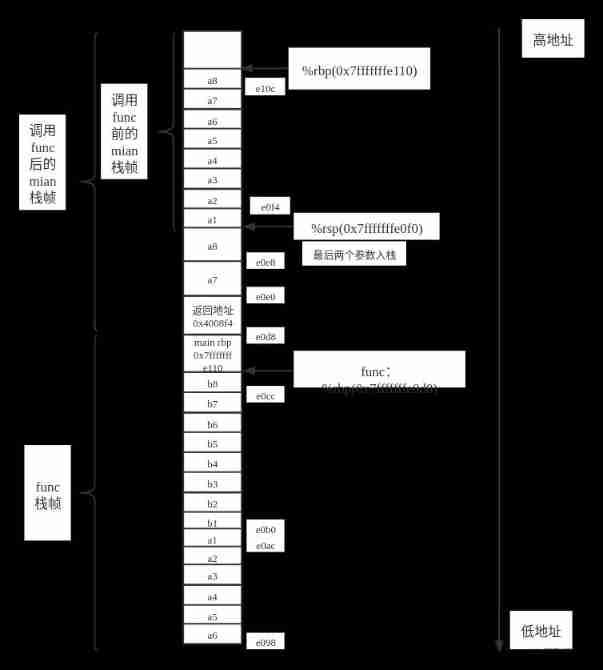
The above stack frame information can dgb Print verification during debugging :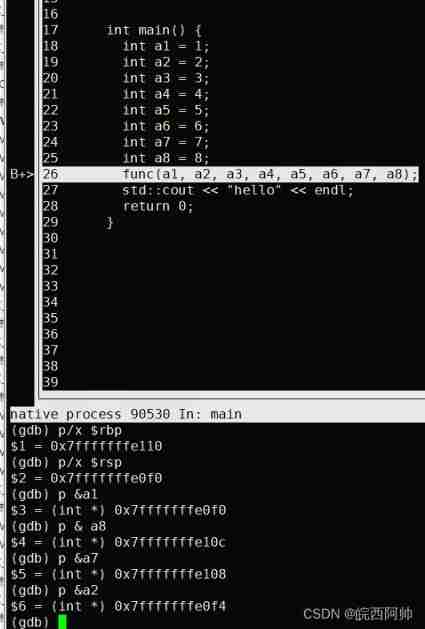


Reference resources :
- Deep understanding of computer systems
边栏推荐
- 2022-2028 global ICT test probe industry research and trend analysis report
- Basic data structure of redis
- Search rotation sort array
- CentOS installation starts redis
- Rust controls Dajiang programmable UAV Tello
- 20220215 CTF misc buuctf Xiaoming's safe binwalk analysis DD command separate rar file archpr brute force password cracking
- Yboj mesh sequence [Lagrange interpolation]
- left join左连接匹配数据为NULL时显示指定值
- Cloud security daily 220630: the IBM data protection platform has found an arbitrary code execution vulnerability, which needs to be upgraded as soon as possible
- Never use redis expired monitoring to implement scheduled tasks!
猜你喜欢

什么是SRM系统,如何规范公司内部采购流程

2022-2028 global ultra high purity electrolytic iron sheet industry research and trend analysis report

Inventory the six second level capabilities of Huawei cloud gaussdb (for redis)

2022-2028 global capsule shell industry research and trend analysis report

20220216 misc buuctf another world WinHex, ASCII conversion flag zip file extraction and repair if you give me three days of brightness zip to rar, Morse code waveform conversion mysterious tornado br

20220215-ctf-misc-buuctf-einstein-binwalk analyze picture-dd command separate zip file -- look for password in picture attribute

Deployment of mini version message queue based on redis6.0

MySQL variables, stored procedures and functions

The programmer's girlfriend gave me a fatigue driving test

20220215 misc buctf easycap Wireshark tracks TCP flow hidden key (use of WinHex tool)
随机推荐
Inventory the six second level capabilities of Huawei cloud gaussdb (for redis)
The principle and related problems of acid in MySQL
需求评审,测试人员应该发挥怎样的价值?两分钟让你不再懵逼
2022-2028 global electric yacht industry research and trend analysis report
如何关闭一个开放的DNS解析器
Thoughts on the future of data analysis in "miscellaneous talk"
Red hat will apply container load server on project atomic
Bugku CTF daily one question dark cloud invitation code
Software engineering best practices - project requirements analysis
[PHP] self developed framework qphp, used by qphp framework
Wordpress blog uses volcano engine veimagex for static resource CDN acceleration (free)
lvm-snapshot:基于LVM快照的备份之准备工作
什么是SRM系统,如何规范公司内部采购流程
MySQL index test
8253A寄存器浅析
VR panorama adds contrast function to make the display of differentiation effect more intuitive!
Introduction to ES6 promise, new features of ES7 and es8 async and await
Solving the weird problem that the query conditions affect the value of query fields in MySQL query
Deployment of mini version message queue based on redis6.0
20220215 CTF misc buuctf Xiaoming's safe binwalk analysis DD command separate rar file archpr brute force password cracking