当前位置:网站首页>Penetration test - directory traversal vulnerability
Penetration test - directory traversal vulnerability
2022-06-25 04:49:00 【amingMM】
Directory traversal vulnerability
Preface
Web Applications generally have the function of reading and viewing the files of the server
Most of them use the submitted parameters to indicate the file name
Form like :http://www.nuanyue.com/getfile=image.jgp
When the server processes the transmitted image.jpg After the file name ,
Web The application will automatically add the full path ,
Form like “d://site/images/image.jpg”, Return the read content to the visitor
First look , It's just a simple process of file interaction ,
But because the file name can be changed arbitrarily
The server supports “~/”,“…/” And other special symbols ,
Thus, the attacker can access or overwrite sensitive data beyond his authority ,
Such as the configuration file of the website 、 The core file of the system ,
Such a flaw is named path traversal vulnerability .
Checking some routine Web Application time , There are often discoveries , It's just relatively hidden .
Path traversal vulnerability found
Yes Web Application files read interactive function blocks , To test
In the face of such a reading method :
“http://www.xxxx.com/test/downfile.jsp?filename=fan.pdf”Use “../” To testUrl:“getfile=/fan/fan/*53.pdf”,
And the system The resolution is
“d://site/test/pdf/fan/fan/…/…/*53.pdf"
adopt “…/” Jump directory “/fan”, namely “d://site/test/pdf/*53.pdf”,
Returned to the normal page of reading the file .
The path traversal vulnerability is usually hidden in file reading or displaying picture function blocks
The file name submitted through parameters ,
It can be seen from this that it is absolutely necessary to filter interactive data .
Of course, a malicious attacker will use the read permission of the file to access across directories ,
For example, access to some controlled files ,
“../../../../../../../etc/passwd“
perhaps ”../../../../boot.ini“,
Of course, now some websites have similar Waf Protective equipment for ,
As long as there is... In the data /etc /boot.ini Wait for the file name to be blocked directly .
Traversal path attack mutation
Path traversal vulnerabilities are common ,
stay Web Application programming process ,
You will consciously filter or delete the passed parameters ,
Risky filtering methods , Generally, we can make a breakthrough in the following ways :
Here are some ways to bypass , Of course, in the actual operation process , Can be used in combination with .
(1) Data transmitted by encryption parameters ;
stay Web The application encrypts the file name before submitting ,
such as :“downfile.jsp?filename= ZmFuLnBkZg- “,
In the parameter filename It's using Base64 encryption ,
And if the attacker wants to bypass ,
Simply encrypt the file name and then attach the submission .
So , Adopt some regular or easily identifiable encryption methods , There are also risks .
(2) Code bypass ,
Try to use different encoding transformations for filtering ,
such as Url code ,
By modifying the parameters Url Code submitted ,
“downfile.jsp?filename= %66%61%6E%2E%70%64%66“ To bypass .
(3) Directory qualification bypass ;
In some Web Applications are separated by limiting directory permissions .
Of course, such an approach is not desirable ,
An attacker can use some special symbols
“ ~ “ To bypass .
A submission like this “downfile.jsp?filename=~/…/boot”.
Can pass such a symbol , You can jump directly to the hard disk directory .
(4) Bypass file suffix filtering ;
some Web Before the application reads the file ,
The suffix of the submitted document will be detected ,
An attacker can put an empty byte encoding after the file name ,
To bypass the check of such file types .
for example :…/…/…/…/boot.ini%00.jpg,
Web The application uses Api Will allow the string to contain null characters ,
When actually getting the file name , By the... Of the system Api Will be truncated directly , And resolve to “…/…/…/…/boot.ini”.
In the class Unix Can also be used in the system Url Encoded newline character ,
for example :…/…/…/etc/passwd%0a.jpg
If the file system is getting a file name with a newline character , It will be truncated to the file name .
You can also try %20, for example : …/…/…/index.jsp%20
(5) Detour to verify .
Http Referer : HTTP Referer yes header Part of ,
When the browser to web When the server sends the request , Usually with Referer,
Tell the server which page I link from
In some Web In the application , There will be a way to judge the origin of the submitted parameters ,
The method of bypassing can try to submit in the website message or interactive place Url Then click or directly modify Http Referer that will do ,
This is mainly due to Http Referer Is sent by the client browser ,
The server is out of control , It is wrong to treat this variable as a trusted source .

- Special title ---- web The server is not configured properly
 There may be directory traversal
There may be directory traversal
Sensitive document ( Database files , Account file )—> Sensitive files leaked
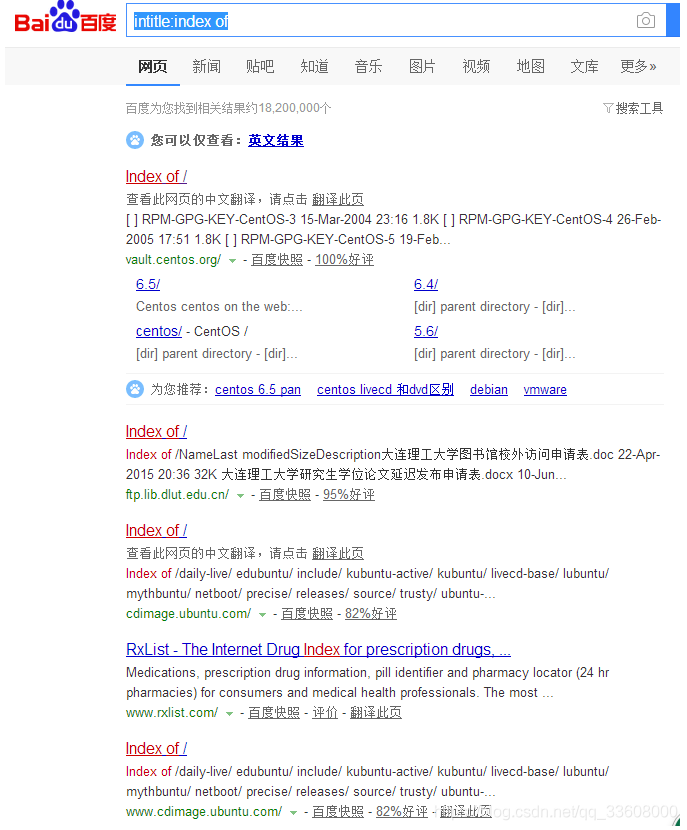
– Try Use Baidu grammar /google Search for
intitle:Index of /

Prevent traversal path vulnerabilities
In the method of preventing traversal path vulnerability , The most effective is the control of permissions
Handle with caution To the file system API Passed parameter path .
Because most of the configuration files have no reasonable permissions ,
and Web The reading of files by applications mostly depends on the system itself API,
In the process of parameter passing , If there is no strict control , There will be ultra vires .under these circumstances ,Web Applications can take the following defensive measures , It's best to combine .
(1) Data purification , Hard code or uniformly code the file names submitted by website users ,
Whitelist file suffixes , Refuse to include malicious symbols or empty bytes .
(2) Web Applications can use chrooted The environment accesses the directory containing the accessed files ,
Or use absolute path + Parameter to control access to the directory ,
Make it under the specified directory even if it exceeds its authority or crosses the directory .
summary
Path traversal vulnerability allows malicious attackers to break through Web Application security control ,
Direct access to sensitive data the attacker wants ,
Including configuration files 、 journal 、 Source code, etc , With the comprehensive utilization of other vulnerabilities ,
Attackers can easily gain higher privileges , And such loopholes are easy to explore
As long as the Web The read-write function block of the application is directly detected manually , Judge by the content of the returned page , It's intuitive , It is also relatively simple to use .
边栏推荐
猜你喜欢

机器学习深度学习——向量化

高效的NoSQL数据库服务Amozon DynamoDB体验分享

绝了!自动点赞,我用 PyAutoGUI!

The solution of wechat applet switchtab unable to take parameters

js的sort()函数
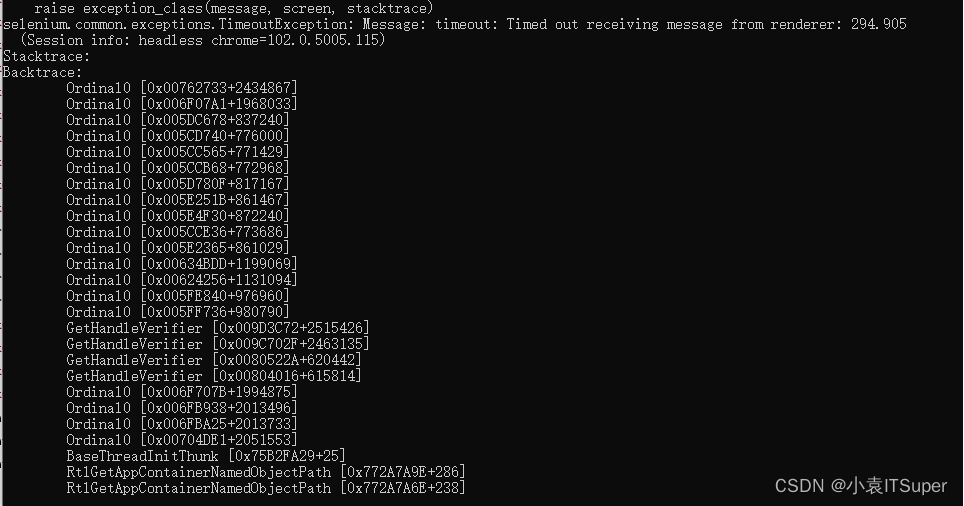
成功解决:selenium.common.exceptions.TimeoutException: Message: timeout: Timed out receiving message from
Triangle class (construction and deconstruction)

Record the problem of C # print size once

固态硬盘开盘数据恢复的方法

Bingbing's learning notes: implementation of circular queue
随机推荐
Use text analysis to identify the main gender in a text
Mongodb cluster
515. find the maximum value / Sword finger offer II 095 in each tree row Longest common subsequence
Vscode 设置clang-format
Codeforces Round #802 (Div. 2) C D
魔法猪系统重装大师怎么使用
融合CDN,为客户打造极致服务体验!
"Daily practice, happy water" 1108 IP address invalidation
LabVIEW development gas regulator
Cannot import name 'escape' from 'jinja2' [solved successfully]
固態硬盤開盤數據恢複的方法
Successfully solved: selenium common. exceptions. TimeoutException: Message: timeout: Timed out receiving message from
JS call() and apply()
Construction scheme of distributed websocket
How to apply for software
OOP vector addition and subtraction (friend + copy construction)
哪个编程语言实现hello world最烦琐?
parallel recovery slave next change & parallel recovery push change
Data import and export for gbase 8s
Huawei Hongmeng development lesson 4
