当前位置:网站首页>Summary of the function and usage of const, volatile and restrict
Summary of the function and usage of const, volatile and restrict
2022-07-05 00:29:00 【Kingston】
const
const(constant) Keywords can modify variables 、 Function parameter 、 Return value or function body .
Define read-only variables .
Limiting function parameters . Prevent accidental modification . Increase program security and reliability .
Such as const char *p Express ,p The value pointed to by the pointer cannot be changed , This pointer cannot be used to modify data
Such as char *const p Express ,p The address pointed to by the pointer cannot be changed
Such as const int arr[] Then the values in the array cannot be modified
const char *const p Express , The value and address pointed to cannot be changed
const double locked[4]
double *pc=rates
pc=locked This sentence is illegal . because locked It can't be modified
In the source file const int i = 1 In other documents extern const int i, If in the header file, apply static const int i = 1, Because each file needs to contain this header file , need static Ensure internality . But if you store arrays in this way , Because each file needs to create this static array , It may take up more storage space , We need to consider its advantages and disadvantages from more aspects .
volatile
volatile Qualifiers indicate that variables can be modified by external agents in addition to programs , For example, the variable saves the current clock time .
The compiler optimizes the compilation and puts the unchanged value in the register , For reading , Mark volatile It can ensure that it is not put into the register .
If it cannot be changed by the program but can be changed by the agent const volatile int i.
restrict
restrict Can only be used for pointers int* restrict ptr, So that makes ptr Is the only way to point to a data block .
It can prevent data from being operated by other pointers . If in memcpy In order to prevent overlapping areas , use restrict Modifies the incoming pointer . meanwhile ,restrict It is also conducive to compiler optimization .
author : Hu hahaha
link :https://www.jianshu.com/p/58f618bd9ea3
source : Simple books
The copyright belongs to the author . Commercial reprint please contact the author for authorization , Non-commercial reprint please indicate the source .
边栏推荐
- Application of multi loop instrument in base station "switching to direct"
- Get to know ROS for the first time
- [error reporting] "typeerror: cannot read properties of undefined (reading 'split')“
- 基于三维gis平台的消防系统运用
- Binary conversion problem
- 2022.07.03 (LC 6109 number of people who know secrets)
- Upload avatar on uniapp
- [IELTS reading] Wang Xiwei reading P4 (matching1)
- Kibana index, mapping, document operation
- The company needs to be monitored. How do ZABBIX and Prometheus choose? That's the right choice!
猜你喜欢
2022.07.03(LC_6108_解密消息)
Relationship between classes and objects
Leetcode70 (Advanced), 322

Data on the number of functional divisions of national wetland parks in Qinghai Province, data on the distribution of wetlands and marshes across the country, and natural reserves in provinces, cities
Specification for fs4061a boost 8.4v charging IC chip and fs4061b boost 12.6V charging IC chip datasheet

IELTS examination process, what to pay attention to and how to review?
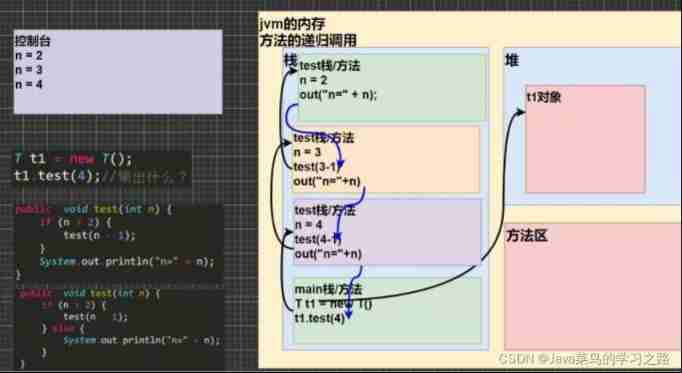
Recursive execution mechanism

npm install报错 强制安装

Illustrated network: what is gateway load balancing protocol GLBP?

【雅思阅读】王希伟阅读P4(matching2段落信息配对题【困难】)
随机推荐
OpenHarmony资源管理详解
跨域请求
Is it safe to open and register new bonds? Is there any risk? Is it reliable?
Daily practice (18): stack containing min function
How to use fast parsing to make IOT cloud platform
P4281 [ahoi2008] emergency assembly / gathering (LCA)
abc 258 G - Triangle(bitset)
Paper notes multi UAV collaborative monolithic slam
基本放大电路的学习
Recursive execution mechanism
GDB常用命令
Power operation and maintenance cloud platform: open the new mode of "unattended and few people on duty" of power system
Distributed base theory
Hisilicon 3559 universal platform construction: YUV422 pit stepping record
Summer challenge brings you to play harmoniyos multi terminal piano performance
模板的进阶
2022.07.03 (LC 6108 decryption message)
Date time type and format in MySQL
How many triangles are there in the golden K-line diagram?
How to avoid arc generation—— Aafd fault arc detector solves the problem for you