当前位置:网站首页>Cookie encryption 6
Cookie encryption 6
2022-06-27 07:31:00 【Fan zhidu】
Target website :
aHR0cHM6Ly9zZWFyY2gua29uZ2Z6LmNvbS9wcm9kdWN0X3Jlc3VsdC8/a2V5PSVFNyVCQSVBMiVFNiVBNSVCQyVFNiVBMiVBNiZzdGF0dXM9MCZfc3RwbXQ9ZXlKelpXRnlZMmhmZEhsd1pTSTZJbUZqZEdsMlpTSjk=
Directly view the home page of the developer tool cookie change , The original cookie yes :

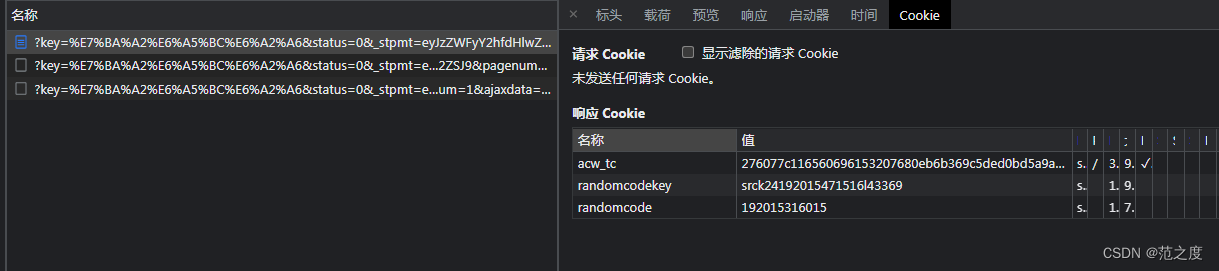
Here simulate the request , Carry three for the first time cookie There is no way to return content .

Carry the cookie

The key to encryption is randomcode
Here is a global search : The following encryption functions are found :

Redo breakpoint :
Successfully stop , Start below fiddker Simulation of the request , Discover and reshape request Of js After the request , The access was successful, but the data was not accessed successfully . Two comparisons , Found a timestamp changing in the URL request :
// for the first time
key: A dream of red mansions
status: 0
_stpmt: eyJzZWFyY2hfdHlwZSI6ImFjdGl2ZSJ9
pagenum: 1
ajaxdata: 1
type: 1
ajaxdata: 3
_: 1656124212160
// The second time
key: A dream of red mansions
status: 0
_stpmt: eyJzZWFyY2hfdHlwZSI6ImFjdGl2ZSJ9
pagenum: 1
ajaxdata: 1
type: 1
ajaxdata: 3
_: 1656126302616Contrast two times cookie, Several fields are changing :
// for the first time
randomcodekey=srck25095106235992vl8186
randomcode=095106544682
randomcodesign=Ul7zTaxI0wRjfWzrJKASPrR3LXr1lxfA633382EzQjhMBCYnBkcaLccKFCeI%2F43Jm0XWDa%2Fjt1K62lgIxAZfXQ%3D%3D
acw_tc=276082a316561218664708696e8e1319c2d6b161a0b8ae6d80c96a79ba20b5
TY_SESSION_ID=19a09479-af25-47b9-9c7e-24d28ad4df10
// The second time
randomcodekey=srck25110502685465otd318
randomcode=110502183005
randomcodesign=I8J9dQDdtXSN04NAdd%2B9r4IUDnZnoTdulHbbwk1Tj7G2UJRm6ct1bNcJuD23pUbVvYxEhIavT8Tb19IoffPumw%3D%3D
acw_tc=276082a016561263023097143ebec60beed6bc71b21fce1a014107e68089da
TY_SESSION_ID=8f5955b7-cf47-4435-adea-ad089ec3e647, Because the first request for a web address only has a template , Can't find fidder The return content in is critical xhr request
So the second request is the key . stay fidder The feedback of the content captured in is as follows :

There are four steps above , The first step of the request is equivalent to loading a template , Set up 3 individual cookie, however

Step 2 request , Although there is no setting cookie, Return any request , But in fact, key fields are set , One feature is the band cookie visit , This is a very important tip

The third step brings two cookie Field ,, The actual test is to generate the fourth... Required by step 4 cookie

The fourth step is to take cookie, Back to json Array

The fourth step is the most critical request , That is, the purpose of setting . The required fields need to be compared , use fidder Simulate the request to test .
The additional knowledge here is : sometimes hookcookie It's no use using plug-ins , It is better to use the browser directly hook, Guess what cookie Where it was generated .
2. yes , we have hook The code can be deleted directly ,js There are two functions , When accessing the first one, set the console you set cookie It's blocked .
边栏推荐
- File 与 MultipartFile概述
- hutool对称加密
- Solve the problem of win10 wsl2 IP change
- Coggle 30 Days of ML 7月竞赛学习
- 高薪程序员&面试题精讲系列116之Redis缓存如何实现?怎么发现热key?缓存时可能存在哪些问题?
- poi导出excle
- 正斜杠反斜杠的由来
- Use uview to enable tabbar to display the corresponding number of tabbars according to permissions
- pytorch Default process group is not initialized
- VNC Viewer方式的远程连接树莓派
猜你喜欢

How to download opencv? How to configure opencv after downloading?

Stream常用操作以及原理探索

Basic knowledge | JS Foundation

Gérer 1000 serveurs par personne? Cet outil d'automatisation o & M doit être maîtrisé

IDEA连接数据库报错

基础知识 | js基础
MySQL

Configuring FTP, enterprise official website, database and other methods for ECS

Error in idea connection database

Xiaomi Interviewer: let's talk about the proficient Registration Center for three days and three nights
随机推荐
sql sever列名或所提供值的数目与表定义不匹配
Window right click management
IDEA连接数据库报错
js打印99乘法表
poi导出excle
POI replacing text and pictures in docx
Interviewer: please introduce cache penetration, cache null value, cache avalanche and cache breakdown, which are easy to understand
Idea method template
什么是浮选机?
R language analyzing wine data
Win10 remote connection to ECS
Date database date strings are converted to and from each other
RNA SEQ data analysis in R - investigate differentially expressed genes in the data!
语音信号处理-概念(二):幅度谱(短时傅里叶变换谱/STFT spectrum)、梅尔谱(Mel spectrum)【语音的深度学习主要用幅度谱、梅尔谱】【用librosa或torchaudio提取】
1-4 进制表示与转换
MySQL
Solve the problem of win10 wsl2 IP change
正斜杠反斜杠的由来
JDBC transaction commit case
Oppo interview sorting, real eight part essay, abusing the interviewer