当前位置:网站首页>CTF introductory learning (WEB direction)
CTF introductory learning (WEB direction)
2022-06-30 02:05:00 【Dayuan Aliang】
Brush questions Edge learning To sum up
1.Robots agreement
“Robots agreement ” Our English full name is Robots Exclusion Protocol, Robot exclusion protocol , It's also called crawler protocol 、 Robot protocol , It refers to a text file placed in the root directory of the website by the website owner , namely robots.txt, Tell the search engine's webbot ( Or web crawler 、 Web spider ) Which pages should not be crawled , Which pages can be crawled , In essence, it is an interactive way between the visited website and the search engine .
robots.txt A file is a text file , Use any common text editor , such as Windows The system is installed Notepad, You can create and edit it [1] .robots.txt It's an agreement , Not an order .robots.txt It's the first file to view when visiting a website in a search engine .robots.txt Files tell the spider what files can be viewed on the server .
When a search spider visits a site , It will first check if the root directory of the site exists robots.txt, If there is , The search robot will follow the contents of the file to determine the scope of access ; If the file does not exist , All search spiders will be able to access all pages on the site that are not password protected . Baidu official suggestion , Only if your website contains content that you do not want to be included by search engines , To use robots.txt file . If you want the search engine to include all the content on the website , Do not create robots.txt file .
If the website is regarded as a room in the hotel ,robots.txt It was hung by the master at the door of the room “ Do not disturb. ” or “ Welcome to clean ” Your sign . This file tells the visiting search engine which rooms can be entered and visited , Which rooms are for storing valuables , Or it may involve the privacy of residents and visitors and not open to search engines . but robots.txt It's not an order , It's not a firewall , Just as the gatekeeper can't stop malicious intruders such as thieves .
The following is a simple application of the protocol :
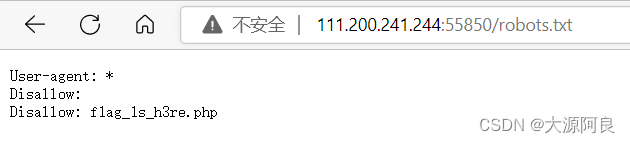
Visit the topic scenario robots.txt The file shows flag Path location ,
Then visit the topic scene path flag_ls_h3re.php obtain flag.
2. Backup file


frequently-used Backup file The suffix of is “.git” 、“.svn”、“.swp”、“.~”、“.bak”、“.bash_history”、“.bkf” etc. . In the input index. php.bak After downloading the file .
After downloading the backup file , take "bak" Format changed to "txt" You can see the script code information in text format , It includes flag
3. sandwich biscuits (cookie)
Cookie Not its original intention “ cookie ” It means , It's a simple text file saved in the client , This file is associated with a specific Web Documents are linked together , Save the client's access to this Web The information in the document , When the client visits this again Web This information is available to the document when the document is created . because “Cookie” It has magical features that can be saved on the client , Therefore, it can help us realize the function of recording users' personal information , And all this doesn't have to use complex CGI Applications such as .
for instance , One Web The site may generate a unique ID, And then to Cookie The file format is kept on each user's machine . If you use a browser to access Web, You will see all saved on your hard disk Cookie. In this folder, each file is a file composed of “ name / value ” For the text file composed of , There is also a file that holds all the corresponding Web Site information . Everyone here Cookie The file is a simple and common text file . Through file name , You can see which Web The site is placed on the machine Cookie( Of course, the site information is also saved in the file )
Here are cookie Simple learning application of the protocol 

F12 see Cookie Information can be seen in the prompt given by the title “look-here” value cookie.php The script file is added after the title scene path cookie.php Go to the next step .
The next question is “See the http response”. You need to check it here http Of response Information , Use wireshark Software package capture .
The title prompt is to view http Agreed response Field information , Then we can choose the second http( The first is request), Double click and click to get flag.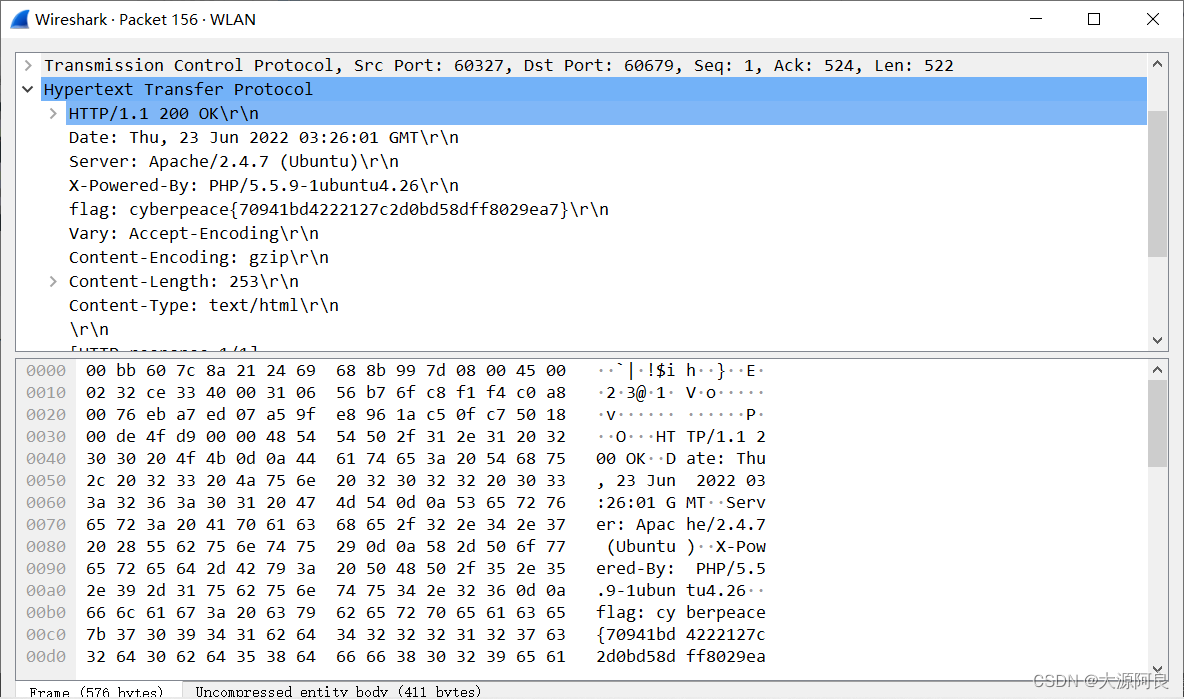
边栏推荐
- MySQL monitoring 3
- Thinking carefully and fearfully: a software can be transmitted online to monitor whether employees want to "run away"
- 209. minimum length subarray - sliding window
- 【银河麒麟V10】【桌面】火狐浏览器设置主页不生效
- [graph neural network] summary of graph classification study [3]: evaluation of graph classification methods and future research directions
- Varnish foundation overview 2
- 210. Schedule II - depth traversal
- C语言 数素数
- [machine learning Q & A] cosine similarity, cosine distance, Euclidean distance and the meaning of distance in machine learning
- Varnish foundation overview 5
猜你喜欢
![[MySQL 04] use MySQL workbench 8.0 CE to back up and restore MySQL databases in Linux](/img/e7/fc2925a10ac5fb370dd221c3f4a46a.png)
[MySQL 04] use MySQL workbench 8.0 CE to back up and restore MySQL databases in Linux

Unity2d-- add keys to animation and bind events

(4) Blender source code analysis flash window display process

Embedded test template
Spark 离线开发框架设计与实现

DTW learning (dynamic time warping) -- Thought and code implementation

8 — router

What problems can cloud storage architecture solve for Devops?

Conjecture of prime pairs in C language

013_ slider
随机推荐
魔百盒CM201-2-CH-Hi3798MV300-300H-EMMC和NAND_红外蓝牙语音_通刷固件包
The birth of the cheapswap protocol
搞透AQS原理(流程圖及同步隊列圖解)
CTF入门学习(Web方向)
Blue Bridge Cup stm32g431 - three lines of code for keys (long press, short press, click, double click)
CheapSwap 协议的诞生
scp远程拷贝命令记录
7 — filter
【MySQL 06】linux + Docker容器环境中备份和还原MySQL数据库
一种跳板机的实现思路
云存储架构能解决 DevOps 的什么问题?
Cookie encryption 15 login encryption
Que se passe - t - il si un faux divorce devient un vrai divorce?
005_ button
Leetcode 46 Full arrangement (February 15, 2022)
Let‘sPlayCurling
Configure cross domain requests
【银河麒麟V10】【桌面】火狐浏览器设置主页不生效
DMX的配置
The (3n+1) conjecture that C language kills people without paying for their lives