当前位置:网站首页>Login Module Debugging - Getting Started with Software Debugging
Login Module Debugging - Getting Started with Software Debugging
2022-07-30 16:35:00 【Dema incompetent】
Login module debugging-Getting Started with Software Debugging
前言
写作目的
I have been debugging the software,Interested in reverse,But honestly it's hard to get started.I know a book called 《0day安全:软件漏洞分析技术》,但一直没看,I took a look at it recently and found this book to be very well written,虽然是09Years of the book but many things are actually not out of date.So I wanted to write a blog documenting the experiments in the book.
工具
The tools used in this experiment are as follows(在win10Complete the experiment under the platform):
1. Dev-Cpp 5.11 TDM-GCC 4.9.2 (for writing programs)
2. IDA
3. Ollydbg
4. lordpe
5. winhex
进行实验
在Dev-C++Write the code in and compile it
The code is a very simple login module,If the login is successful, it will jump out of the loop,Otherwise, it has been in a loop,代码如下:
#include<stdio.h>
#define PASSWORD "1234567"
int verify_password(char*password){
int authenticated;
//相同结果为0 不同结果为1
authenticated=strcmp(password,PASSWORD);
return authenticated;
}
int main(){
int valid_flag=0;
char password[1024];
while(1){
printf("Please input the password: ");
scanf("%s",password);
valid_flag=verify_password(password);
if(valid_flag){
printf("The password is wrong,login failed\n");
}
else{
printf("The password is correct,login successful\n");
break;
}
}
}
然后进行编译,Here it is compiled as 32bit的程序.
会生成一个exe文件.点击exe文件: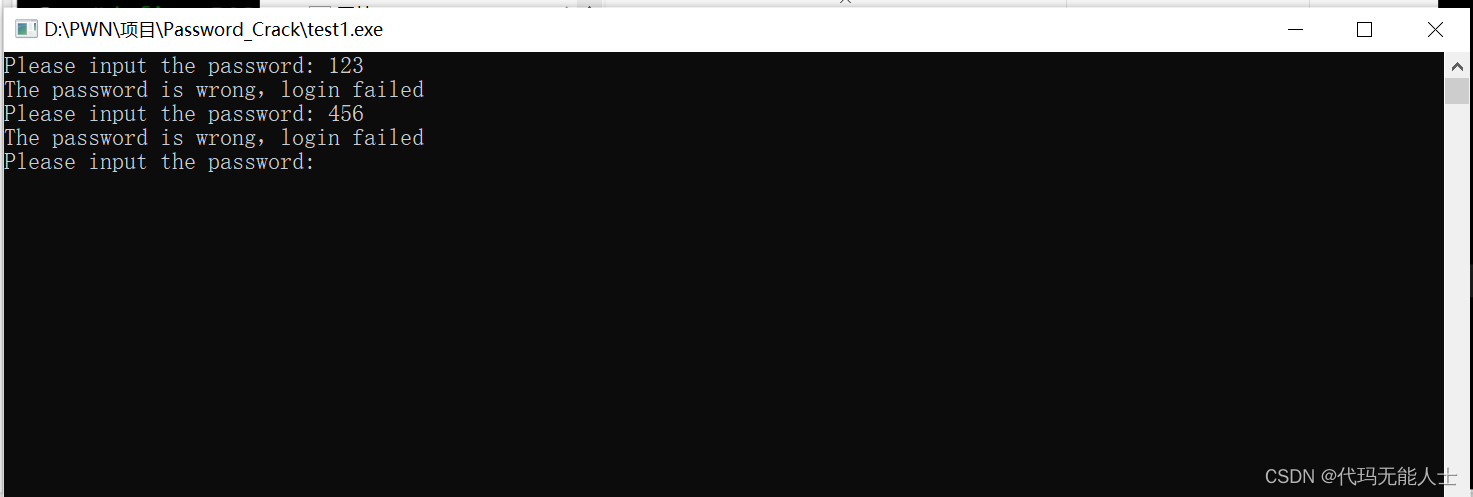
If you enter the correct password1234567It will flash back to indicate that the login is successful.
IDA中打开exefile for static debugging

Once opened, it is a flowchart,You can click on the keyboardFn+F12.
可以看到在jz short loc_401588A branch was made at the instruction,Blind guess here is itif语句.Since we want to hack the login procedure,Then the easiest is toif与else反过来,That is, in the above flow chartfalse与trueThe line is reversed,This can be obtained by modifying the judgment condition at the branch,So focus on the assembly statement at the branch.
Let's look at assembly instructions: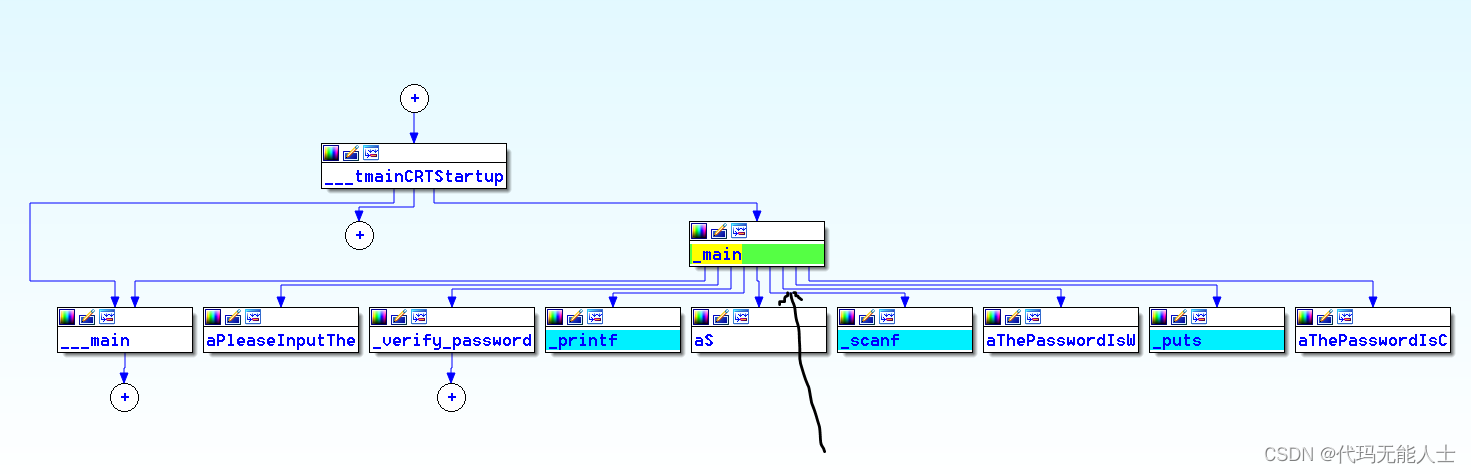
You can click the space at the breakpoint,You can see the flow chart below.Then click the space on the line where I marked to see the assembly code.

So know the address of virtual memory(VA)是00401578(8*4=32位),It should be noted that the addresses seen by the debugging software are virtual memory addresses.
Ollydgb中打开exefile for dynamic debugging
使用ollydbg打开这个exetype on the keyboard after the fileCtrl+GKey combination to enter the address seen in the previous section
Press Enter to locate the branch statement.
汇编中jz与je是一个意思,jne与jeis the opposite.So you can try itje改为jne.Click on the yellow row.
发现74 0E变为了75 0E.
Can run to try,type on the keyboardFn+F9,Found the original login password1234567登录失败了.And just enter a value and log in successfully.It shows that our thinking is correct.
Change the hex of the software itself
退出IDA与Ollydbg,再打开exe文件,It was found that the modification was not successful,Because it was just debugging before,To modify its internal hexadecimal to succeed,使用winhex打开这个exe文件.
太多了,From the previous section we know that we need to put 74 0E改为75 0E,这里打开exe文件左边的offsetis the file offset address,What we have previously grasped is that virtual memory addresses need to be converted.
由于32位的exe文件与dlldocuments, etcPE格式,PEThe mapping diagram of file mapping to virtual memory is as follows(出自《0day安全:软件漏洞分析技术》):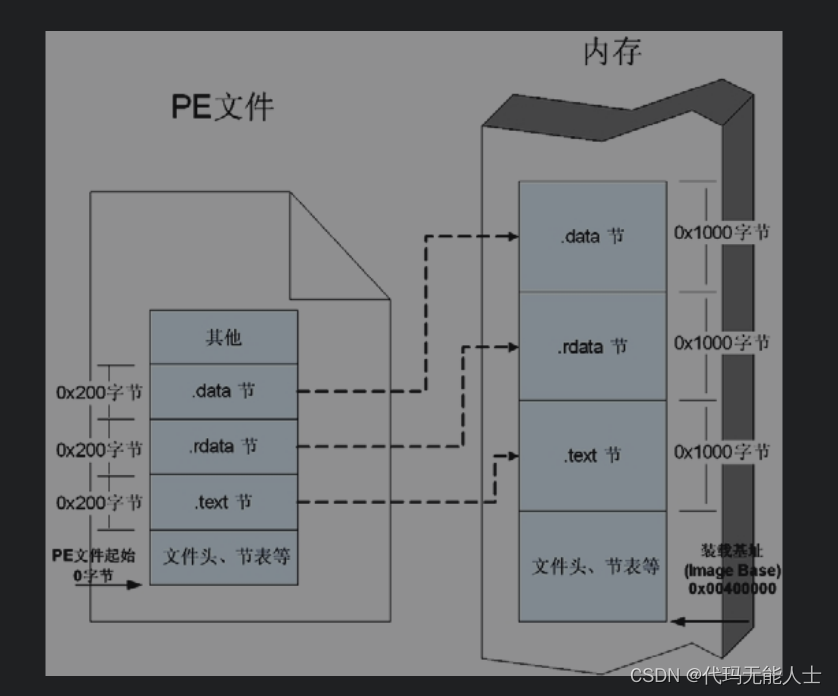
从图中看出PEThe initial address of the file is 0字节,The load base address of virtual memory(Image Base)是0x00400000.根据公式:The offset address of the file=RVA(VA-Image Base)-节偏移(virtualoffset-文件的offset).
Seen through the debugger beforeVA=0x00401578,已知Image Base=0x00400000,所以RVA(Virtual memory relative offset address)=0x00001578.Now to calculate the section offset,使用Lordpe(可免费下载)打开exe文件.
点击PE Editor然后选择exe文件.

Section offset is just thatVOffset-ROffset,注意这里不是00000600,This is a hexadecimal calculation,Advice to prevent miscalculationHex Calculator.
Section offset is0x00000C00.Then the file offset address is as follows,为0x00000978:
在winhexfind the corresponding address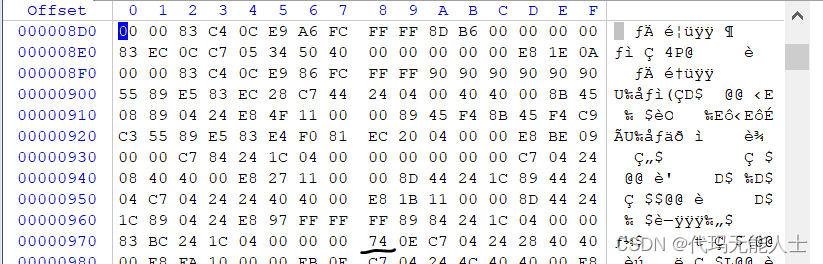
将74改为75然后保存.
再打开exeThe file found an otherwise correct password1234567It says login failed,Although I type one, it crashes(表示登录成功).
总结
The main takeaway from this experiment is understandingPEThe mapping relationship between files and virtual memory,Learned the formulas for converting virtual memory and file offsets,对win32The binaries below have a deeper understanding.
边栏推荐
- 完美绕开CRC32检测的无痕hook
- The service already exists!解决办法
- DTSE Tech Talk丨第2期:1小时深度解读SaaS应用系统设计
- [TypeScript]简介、开发环境搭建、基本类型
- Large-scale integrated office management system source code (OA+HR+CRM) source code sharing for free
- Placement Rules usage documentation
- 游戏多开检测的几种实现方法及破解方法参考
- Windows MySQL 安装配置
- 2022-07-30 Androd 进入深度休眠后把WIFI给关掉,唤醒之后重新打开WIFI
- 绕开驱动层检测的无痕注入
猜你喜欢

华为云数据治理生产线DataArts,让“数据‘慧’说话”

DTSE Tech Talk丨第2期:1小时深度解读SaaS应用系统设计

为什么中年男人爱出轨?

Public Key Retrieval is not allowed报错解决方案

【HMS core】【FAQ】push kit、WisePlay DRM、Location Kit、Health Kit、3D Modeling Kit、SignPal Kit典型问题合集4

Leetcode 119. 杨辉三角 II

Public Key Retrieval is not allowed error solution

应用OPC解决方案实现控制系统数据的安全交换

DTSE Tech Talk丨Phase 2: 1 hour in-depth interpretation of SaaS application system design

Goland 开启文件保存自动进行格式化
随机推荐
【HMS core】【FAQ】push kit, WisePlay DRM, Location Kit, Health Kit, 3D Modeling Kit, SignPal Kit Typical Questions Collection 4
How to implement timing tasks for distributed applications in Golang
How to connect redis in node.js?
Load Base Split usage documentation
为什么中年男人爱出轨?
深度学习区分不同种类的图片
3D激光SLAM:LeGO-LOAM论文解读---特征提取部分
登录模块调试-软件调试入门
win下搭建php环境的方法
Redis 复习计划 - Redis 数据结构和持久化机制
【Linux操作系统】 虚拟文件系统 | 文件缓存
PHP留言反馈管理系统源码
Qt 动态库与静态库
PyQt5快速开发与实战 9.2 数据库处理
The service already exists!解决办法
[TypeScript] Introduction, Development Environment Construction, Basic Types
UI测试新方法:视觉感知测试详解
【HMS core】【FAQ】push kit、AR Engine、广告服务、扫描服务典型问题合集2
归一化与标准化
rhce笔记1