当前位置:网站首页>【Mongodb】READ_ ME_ TO_ RECOVER_ YOUR_ Data, the database is deleted maliciously
【Mongodb】READ_ ME_ TO_ RECOVER_ YOUR_ Data, the database is deleted maliciously
2022-06-24 22:44:00 【Gu Niao】
1. Introduce
My personal Baidu cloud server installed MongoDB, Default configuration used ( Port is the default port , There's no password ), Then I forgot about it , Also because I often use the wireless network card to access the Internet ,ip It is often dynamic , The security group of the ECS releases all ip. It is a database running naked on the cloud , A few days later, I found MongoDB Client connection failure , Reconnected MongoDB, The library built is missing , Left a new library :READ_ME_TO_RECOVER_YOUR_DATA, There's only one watch in it :README, The general content is that they were attacked , You need to pay bitcoin to recover .

2. resolvent
I use the method of configuring user name and password to access the server now mongodb database , There are other ways . I access the terminal through the pagoda panel tool , You can also use other shell Tools .
Connect mongodb

Add users and read / write permissions to the database
use hcs-server db.createUser({ user: "guniao", pwd: "123456", roles: [{ role: "readWrite", db: "hcs-server" }] })verification , Output 1 Indicates that the verification is successful
db.auth("guniao","123456")modify mongodb In the configuration file authorization by enabled, And restart

Use Mongodb Compass The visualizer verifies the user and password again , And re import the data


Modify background connection mongodb Of URL Address

Refer to the connection :
https://blog.csdn.net/qq_34241004/article/details/120704586
https://www.freesion.com/article/3431841152/
边栏推荐
- 使用Aggregated APIServer扩展你的kubernetes API
- NIO、BIO、AIO
- Description of software version selection of kt6368a Bluetooth dual-mode transparent chip
- 源码阅读 | OpenMesh读取文本格式stl的过程
- Based on the codeless platform, users deeply participated in the construction, and digital data + Nanjing Fiberglass Institute jointly built a national smart laboratory solution
- Servlet details
- Yyds dry goods inventory junit5 learning II: assumptions class
- Docker 安装 MySQL 8.0,详细步骤
- 如何比较两个或多个分布:从可视化到统计检验的方法总结
- 详细了解Redis的八种数据类型及应用场景分析
猜你喜欢

Redis-跳表

In the era of full programming, should I give up this road?

Principles of Ethernet port mirroring, link aggregation and VLAN Technology

Seven principles of software design

Leetcode: push domino (domino simulation)

CDN principle
![[personal experiment report]](/img/04/c9e1bee19bff9d55b73c531f7b17f4.png)
[personal experiment report]

Cache control of HTTP
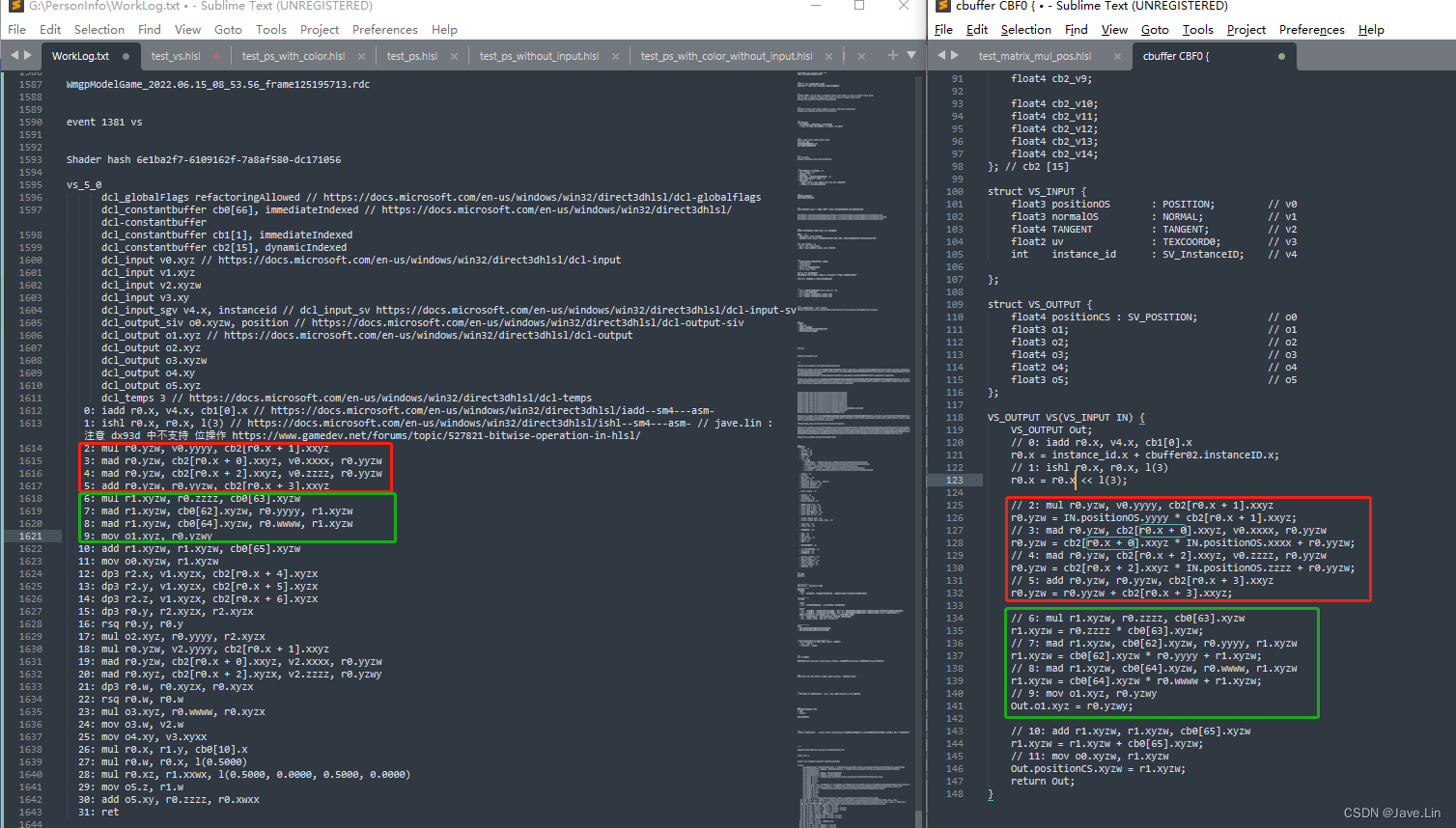
DX 的 HLSL 和 GL 的 GLSL的 矩阵构建的行列区别

Description of transparent transmission function before master and slave of kt6368a Bluetooth chip, 2.4G frequency hopping automatic connection
随机推荐
Visitor tweets tell you which groups are consuming blind boxes
Interrupt, interrupted, isinterrupted differences
JMM 最最最核心的概念:Happens-before 原则
AttacKG: Constructing Technique Knowledge Graph from Cyber Threat Intelligence Reports代码复现
Docker installs redis-5.0.12. Detailed steps
Redis-跳表
Short video mall system, how does scroll view adapt to the remaining height of the page
Docker installs MySQL 8.0. Detailed steps
2022-06-16 work record --js- judge the number of digits in string type digits + judge the number of digits in numeric type digits + limit the text length (display n words at most, exceeding...)
Dynamic memory management (1)
开发规范~参数校验异常、异常返回提示切面
Layer 2 and layer 3 forwarding principle based on VLAN
如何比较两个或多个分布:从可视化到统计检验的方法总结
Database transaction Transanction
Huada 04A operating mode / low power consumption mode
OA system -- save the verification code to session
重磅!法大大上榜“专精特新”企业
2022-06-16 工作记录--JS-判断字符串型数字有几位 + 判断数值型数字有几位 + 限制文本长度(最多展示n个字,超出...)
High level application of SQL statements in MySQL database (II)
Chapter 10 project stakeholder management