当前位置:网站首页>模块五(微博评论)
模块五(微博评论)
2022-06-25 12:15:00 【InfoQ】
计算性能预估
非热点事件的高性能架构
分析
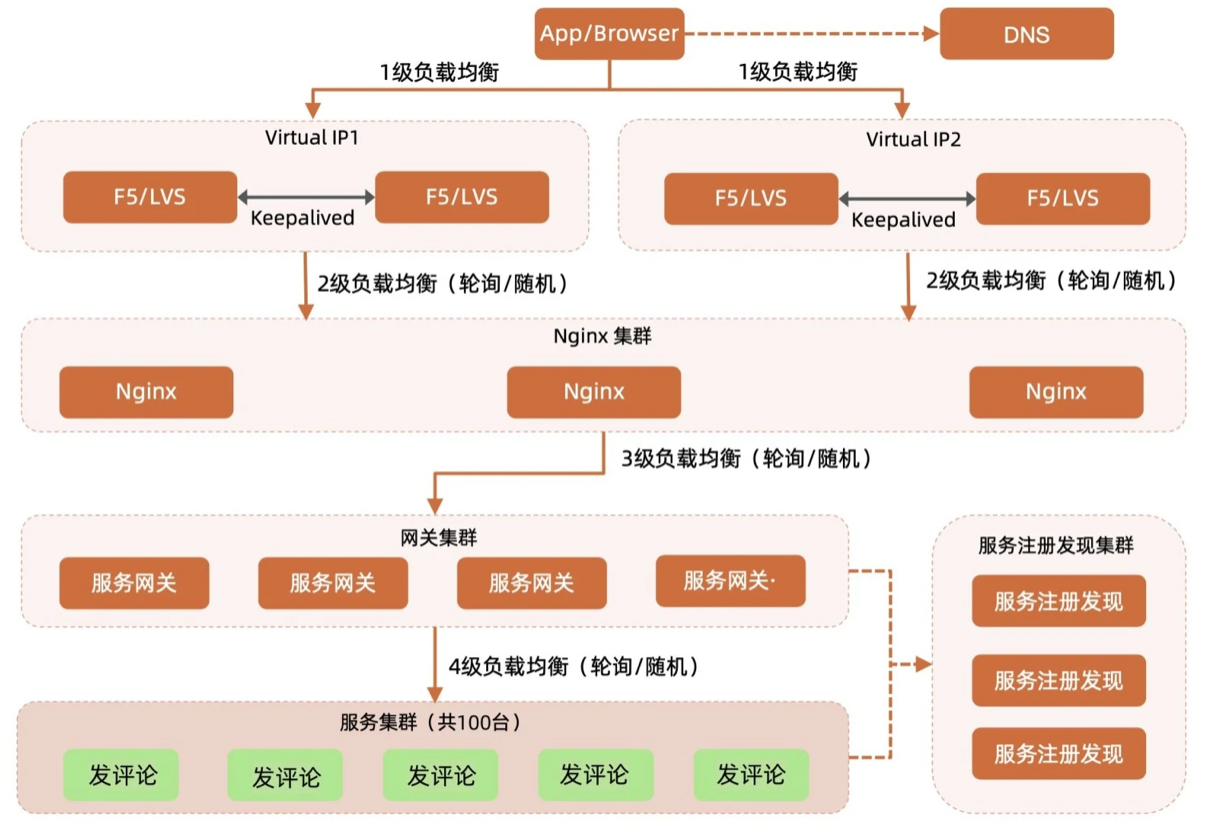
- 写评论的时间段虽然大部分情况下与发微博是相同的,但有时也并不重叠,有时可能是微博发出好几个小时,甚至是几天后才写评论。一条微博,可能有上万人阅读,一,二千人评论,发评论的次数与发微博,看微博的次数是相差比较大的,所以需要将评论设置为单独服务
多级负载均衡架构
热点事件时的高可用计算架构
【业务特性分析】

- 发生热点事件,且判断可能会影响系统可用性时,可通过人工,下达指流指令,限制接收用户评论的接口。
- 在kafka写评论缓存队列时,如果缓存满了,可丢掉后续的写操作
边栏推荐
- Flutter automatically disappears after receiving push
- PHP files running online
- (5) Pyqt5 ---- another method of connecting signals and slots
- Huikan source code -- Huikan app system secondary development source code sharing
- Service charge and time setting code sharing involved in crmeb withdrawal process
- Figure explanation of fiborache sequence
- Geospatial search - > R tree index
- 20220620 面试复盘
- Array reorder based on a field
- Zhangxiaobai's road of penetration (IV) -- detailed explanation of XSS cross site script vulnerabilities
猜你喜欢

Zhangxiaobai's way of penetration (VIII) - detailed operation steps of SQL injection - Boolean blind injection of blind injection

Draw the satellite sky map according to the azimuth and elevation of the satellite (QT Implementation)
![按权重随机选择[前缀和+二分+随机target]](/img/84/7f930f55f8006a4bf6e23ef05676ac.png)
按权重随机选择[前缀和+二分+随机target]

Why are databases cloud native?

2021-09-28

Zhangxiaobai's road of penetration (VI) -- the idea and process of SQL injection and the concat series functions and information of SQL_ Schema database explanation

3+1保障:高可用系统稳定性是如何炼成的?

地理空间搜索 ->R树索引
顺序表的折半查找法

Talk about 11 key techniques of high availability
随机推荐
Ubuntu uninstalling PHP
JQ dynamic setting radio does not take effect when selected
高性能负载均衡架构如何实现?
初识CANOpen
Write regular isosceles triangle and inverse isosceles triangle with for loop in JS
PHP appends the same elements to a two-dimensional array
Zhangxiaobai's way of penetration (III) -- detailed explanation of SQL injection vulnerability principle (SQL Server)
Polling and long polling
Micro engine generates QR code
3+1 guarantee: how is the stability of the highly available system refined?
Select randomly by weight [prefix and + dichotomy + random target]
使用Visio画立方体
3+1保障:高可用系统稳定性是如何炼成的?
CUDA error: unspecified launch failure
Fun pocket mall -- sharing the development source code of fun pocket app system
Idea2017 how to set not to automatically open a project at startup
Lighten the source code -- lighten the app system development function introduction to the beautiful world lighten the app system development source code in China
Tp6 exception handling try catch writing method
Slice() and slice() methods of arrays in JS
Penetration tool environment - Installation of sqlmap