当前位置:网站首页>Nacos service discovery data model
Nacos service discovery data model
2022-07-25 01:46:00 【Liu Chu, Ge Nian】
List of articles
Nacos Service discovery data model
1. Namespace Isolation design
Namespace **(Namespace)** For tenant granularity isolation ,Namespace One of the most common scenarios is the isolation of different environments , For example, development testing
The environment and the resources of the production environment ( Such as configuration 、 service ) Isolation etc. .
From a tenant ( user ) From the perspective of , If there are many different environments , At this time, you can create different
namespce, In order to achieve multi environment isolation . for example , You may have development , Three different environments for testing and production , Then use a set of
nacos There are three different clusters namespace. As shown in the figure below :

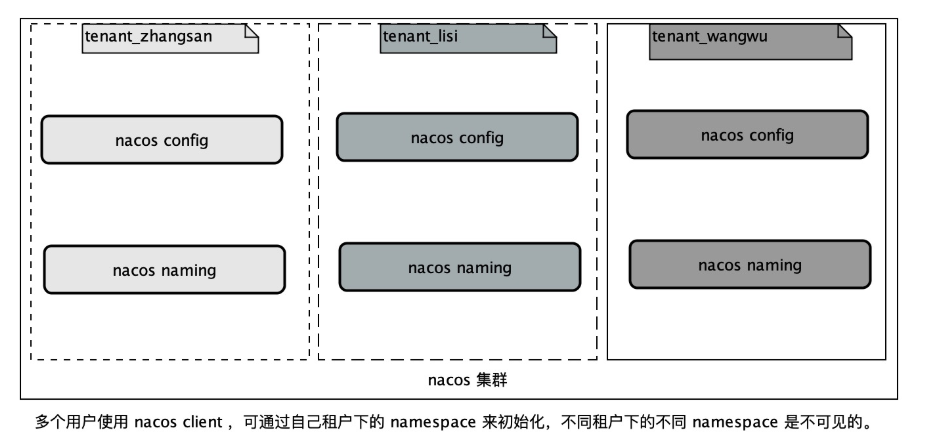
From multiple tenants ( user ) From the perspective of , Every tenant ( user ) It may have its own namespace, Every tenant ( user ) Configuration data and notes
The service data of the volume will belong to its own namespace Next , To achieve data isolation among multi tenants . For example, the super administrator assigned three
Tenants , They are Zhang San 、 Li Si and Wang Wu . After the distribution , All tenants log in with their own account name and password , Create your own naming
Space . As shown in the figure below :
2. Namespace Management
I've already introduced , Namespace (Namespace) Is used to isolate multiple environments ( Such as development 、 test 、 production ), And each application is in a different ring
The same configuration of the environment ( Such as database data source ) The values are different . therefore , We should aim at the actual R & D process of enterprise projects 、 Environmental planning .
For example, a software company has developed 、 test 、 Three sets of production environment , We should establish three environments respectively namespace.

Establish all namespace after , stay Configuration Management And Service management All pages under the module , Will contain for switching namespace( Environmental Science ) Of tab Button , Here's the picture :
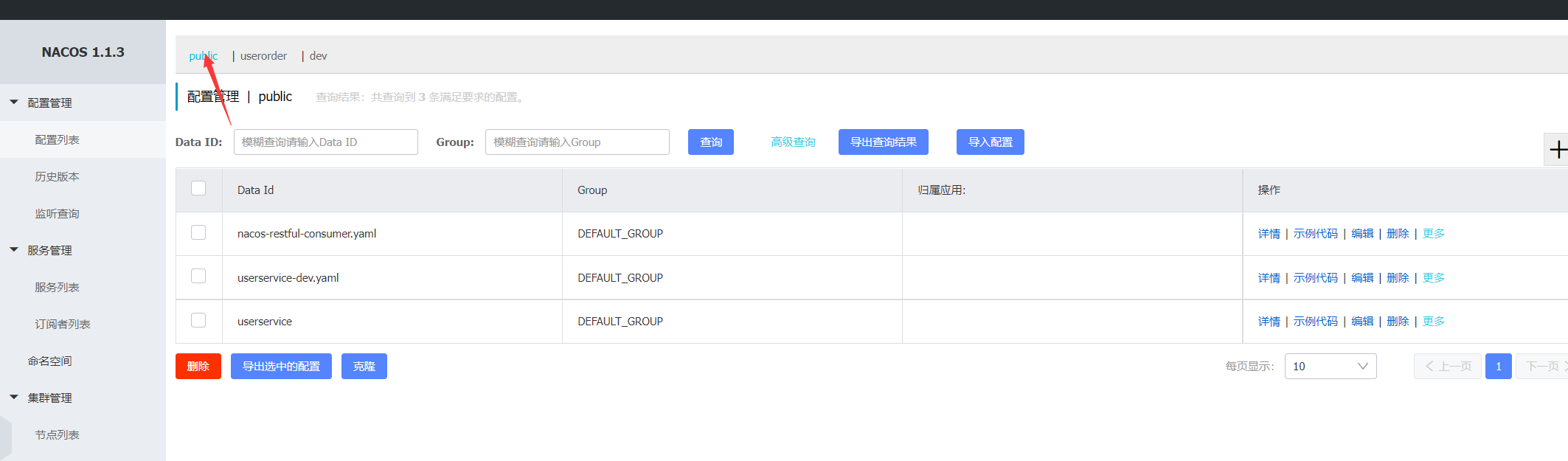
Be careful : namesace by public yes nacos A reserved space for , If you need to create your own namespace, Do not mix public The nuptial , It is named after a real business scenario with specific semantics , So as not to make it literally difficult to distinguish which one you are namespace.
Be careful : When writing the program to get the configuration set , designated namespace Parameters must be filled Namespace ID, Not the name
for example :

3. Data model
Nacos After years of production experience in Alibaba, the data model is refined , It's a service - colony - Three layer model of instance , This can basically meet the data storage and management of services in all scenarios .
nacos The data model of service discovery is as follows :
service : Software functions provided to the outside world , Access predefined interfaces over the network .
service name : Identification of service delivery , Through this identification, the service to be accessed can be uniquely determined .
example : Providing one or more services with an accessible network address (IP:Port) The process of , Start a service , There is a service instance .
Meta information :Nacos data ( Such as configuration and service ) Description information , Such as service version 、 The weight 、 Disaster recovery strategy 、 Load balancing strategy 、 Authentication configuration 、 Various custom tags (label), In terms of scope of action , Meta information divided into service levels 、 Meta information of cluster and instance .
colony A collection of service instances , Service instances form a default cluster , Clusters can be further divided into requirements , The unit of partition can be virtual cluster , Only instances in the same cluster can perceive each other .
The data model shows that : Application passed Namespace、Service、Cluster(DEFAULT) Configuration of , Describes the environment to which the service is directed ( Such as development environment ) Which cluster do you belong to
Registration instance .
Configure the hierarchy as shown in the figure below :

The specific application example is shown below :
If some examples of the company are distributed in different computer rooms all over the country , for example :
xxx.xxx.xxx.xxx:8081, In Shanghai
xxx.xxx.xxx.xxx:8082, In Shanghai
xxx.xxx.xxx.xxx:8083, In Hangzhou computer room
Nacos The instance in the same machine room Divided into a cluster . in other words ,userService It's the service name , A service can be composed of multiple service clusters , For example, Hangzhou cluster 、 Shanghai cluster , And there can be multiple service instances under each cluster , Form a hierarchical model , Pictured :
When microservices access each other , You should visit as much as possible The same cluster Service instance under , Because local access under the same cluster is faster . When not available in this cluster , To access other clusters . for example :
In Hangzhou computer room orderService Priority should be given to accessing the same computer room userService, If in Hangzhou machine room userService Services are not available , Will call the userService.

The specific code application example is shown below :
Appoint namespace Of id:f5eec3c1-4f05-40cd-964a-c8d44f342ab4( Pay attention to setting according to your own environment namespace Of id)
Specify cluster name :DEFAULT Represents the default cluster , Not required
spring:
application:
name: transaction‐service
cloud:
nacos:
discovery:
server-addr: 127.0.0.1:8848
namespace: f5eec3c1-4f05-40cd-964a-c8d44f342ab4
Be careful : Cluster as instance isolation , Only instances of the same cluster can perceive each other .
Be careful : namespace、cluster-name If it is not filled in, the default value will be adopted ,namespace The default is public Namespace , cluster-name The default value is DEFAULT colony .
边栏推荐
- What are the important trends revealed by the release of "operator data viability index"?
- How to upload files to the server
- MySQL Basics (concepts, common instructions)
- Several schemes of traffic exposure in kubernetes cluster
- DotNetCore. Cap notes
- Take the first place in the International Olympic Games in mathematics, physics and chemistry, and win all the gold medals. Netizen: the Chinese team is too good
- Take C language from 0 to 1 - program structure and use examples
- Three possible scenarios for SAP Spartacus server-side rendering
- Turn: emotional internal friction is the biggest source of inefficiency in your life
- Data management process model of science and technology planning project
猜你喜欢
![[29. DFS depth is preferred]](/img/f1/f0c4302a1f7c14c206ff0bdf2eed5c.png)
[29. DFS depth is preferred]

July 8, 2022

Fabric. JS centered element
【Power Shell】Invoke-Expression ,Invoke-Expression -Command $activateCommand; Error or power shell failed to activate the virtual environment

Cloud native platform, let edge applications play out!

Specificity and five applications of Worthington alcohol dehydrogenase

Mobile Robotics (3) Kalman filter

Talk about resume optimization and interview skills of algorithm post!

The solution of displaying garbled code in SecureCRT

Inventory of well-known source code mall systems at home and abroad
随机推荐
[27. Expression evaluation (infix expression)]
Fraud detection using CSP
[summer daily question] Luogu p1605 maze
[28. Maximum XOR pair]
Three modes of executing programs, memory and cache
VC hesitates to invest in Henan
Summary of the most complete MySQL data types in history (Part 2)
Digital power supply -- Chapter 1
Web Security Foundation - file upload
Redis tutorial
Hcip - BGP - border gateway protocol
The introduction of 23 Filipino doctors for 18million was a hot topic, and the school teacher responded: expedient
[summer daily question] Luogu P7550 [coci2020-2021 6] bold
Eolink - quickly develop interfaces through document driven
[hero planet July training leetcode problem solving daily] 20th BST
Specificity and five applications of Worthington alcohol dehydrogenase
iptables :chains, target
EasyX realizes button effect
Mongodb security cluster construction
Visual studio code installation package download slow & Installation & environment configuration & new one-stop explanation