当前位置:网站首页>Artificial Intelligence and Cloud Security
Artificial Intelligence and Cloud Security
2022-07-31 00:49:00 【qq_177803619】
Artificial intelligence is a program that can think and solve problems independently, machine learning is the part of artificial intelligence that uses algorithms to learn from multiple units of data, although it is not 100% safe, artificial intelligence and machine learning can be used toDetect threats in real time.
The focus of AI is detection, but the complete system must also address the response to perceived threats. The basic system can detect attacks, and unknown problems have unknown responses.Humans have to deal with these suspicious transactions, and can then provide feedback to strengthen the system, and depending on the complexity of creating the system, these new rules can be incorporated into new networks or added to the ruleset.
At present, the security requirements of the cloud computing environment mainly come from two aspects, one is the actual business security requirements; the other is the compliance requirements, especially the private cloud for compliance, visibility, sensitive data distributionand other issues are clearly required.
Since the epidemic, the trend of domestic enterprises to migrate to the cloud has increased significantly, especially the demand for SMEs to migrate to the cloud is very significant. In order to cope with the complex and changeable market environment, cloud services have become a must for enterprise business transformation and promote the informatization of the whole industry., digital development, and strong cloud demand have brought new challenges and opportunities to the cloud security market.
my country is very rich in enterprise types, for example, there are many types of industries in the industrial field. Therefore, cloud service providers have very different business requirements and security requirements in different scenarios facing end users.For cloud security in different industries, the protection of data, equipment, and business systems has its own requirements, which requires cloud security providers to have corresponding scenario-based solutions to adapt to different security requirements.
Starting from the essence of cloud security, it is to protect the security of business running on the cloud, and business itself is data, so the implementation of the "Data Security Law" will have an important impact on the development of cloud security.The relevant requirements in the Security Law will also be further integrated into the scope of cloud security.
In addition, from the perspective of supervision, there are obviously some differences between China's laws and regulations in the field of security and foreign laws. For example, the EU's GDPR and China's "Data Security Law" have their own focus, which causesWhen building a cloud architecture, they will also take their own technical means.
In other words, the differences in regulations and architecture of cloud services, and whether they can be protected and managed through a unified security platform in the future will also be a key issue for cloud security.
At present, cloud computing and artificial intelligence are growing in parallel. The complexity of cloud is driving the demand for artificial intelligence, but the complexity of artificial intelligence is also creating a better working efficiency, transparency and control in the cloud environment.demand.
边栏推荐
猜你喜欢
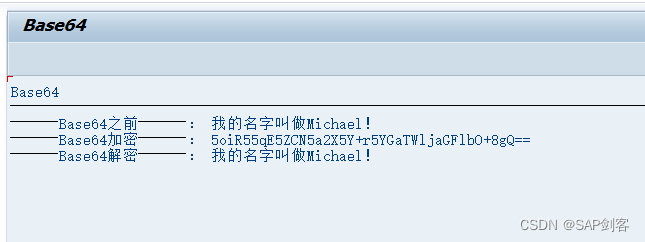
【Demo】ABAP Base64加解密测试

Mini Program - Global Data Sharing

小程序-全局数据共享
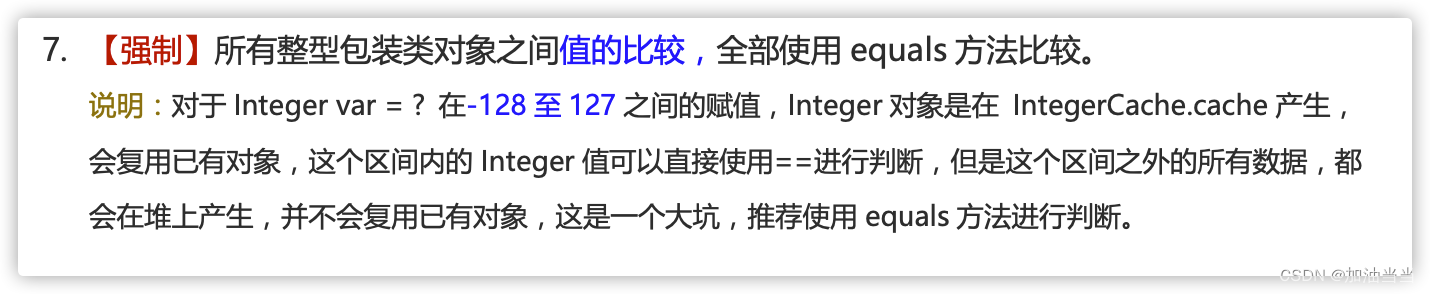
从笔试包装类型的11个常见判断是否相等的例子理解:包装类型、自动装箱与拆箱的原理、装箱拆箱的发生时机、包装类型的常量池技术
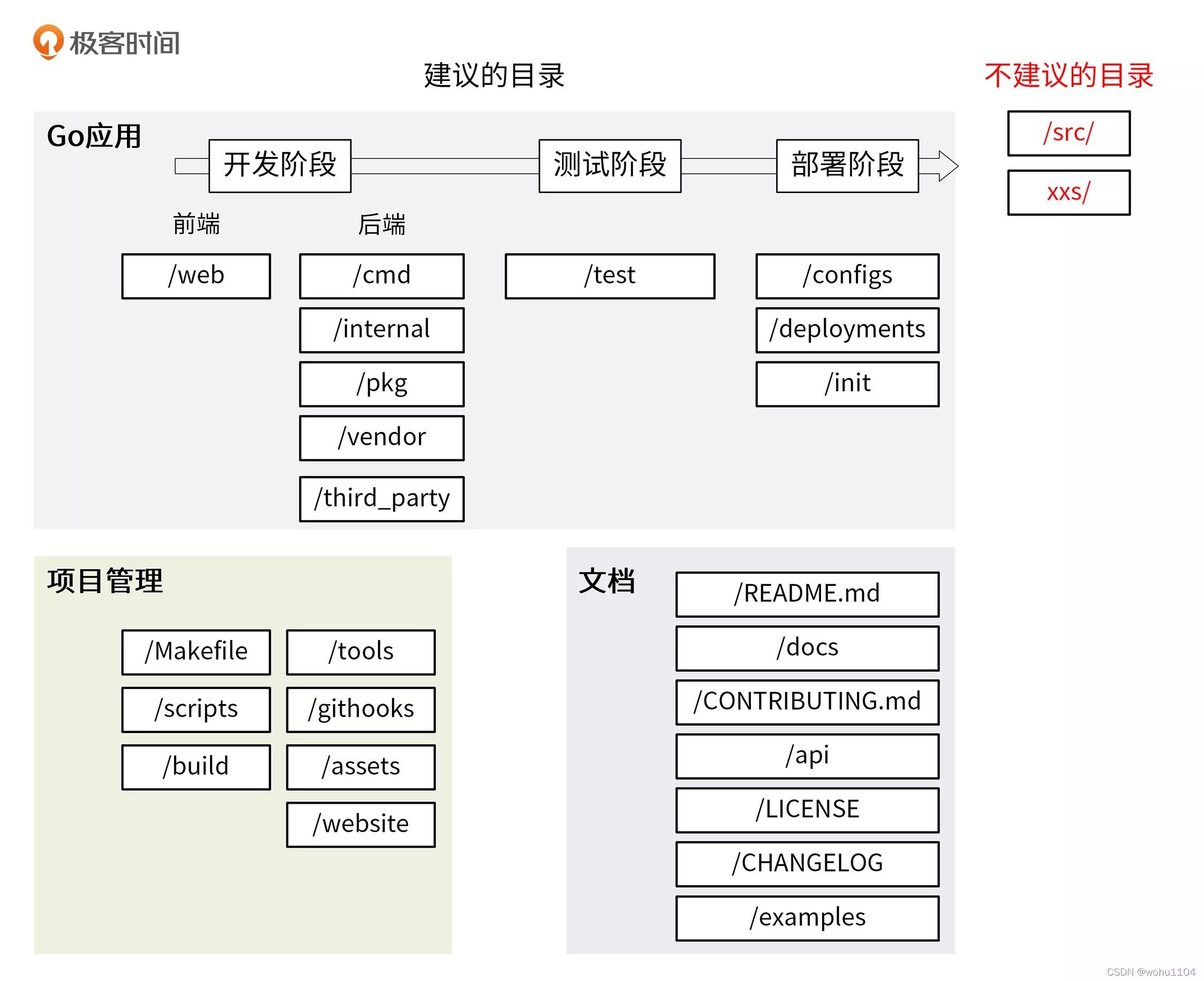
Go study notes (84) - Go project directory structure
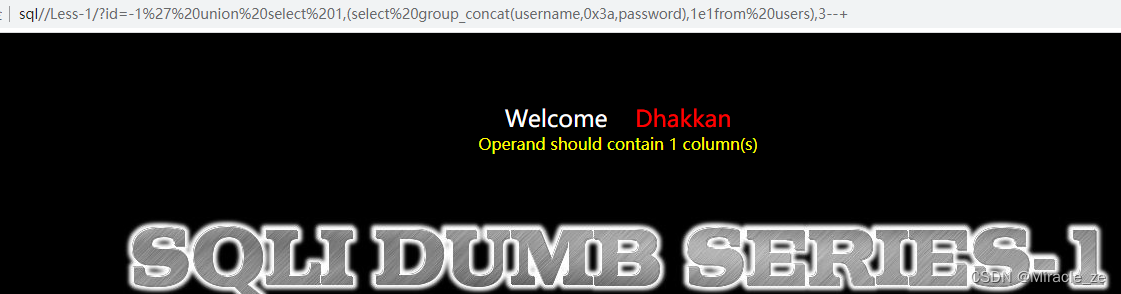
Regular expression password policy and regular backtracking mechanism bypass

ShardingSphere之读写分离(八)
![Xss target drone training [success when pop-up window is realized]](/img/c1/61280bddc9a42a3827735dc31c86e5.png)
Xss target drone training [success when pop-up window is realized]

WMware Tools installation failed segmentation fault solution

响应式布局与px/em/rem的比对
随机推荐
Method for deduplication of object collection
Oracle has a weird temporary table space shortage problem
ShardingSphere之垂直分库分表实战(五)
DOM系列之 client 系列
IOT跨平台组件设计方案
MySql data recovery method personal summary
小程序-全局数据共享
h264和h265解码上的区别
ES6中 async 函数、await表达式 的基本用法
Xss target drone training [success when pop-up window is realized]
【Multithreading】
Asser uses ant sword to log in
registers (assembly language)
BOM系列之Navigator对象
寄存器(汇编语言)
ELK部署脚本---亲测可用
[C language course design] C language campus card management system
ES 中时间日期类型 “yyyy-MM-dd HHmmss” 的完全避坑指南
(五)fastai应用
TypeScript在使用中出现的问题记录