当前位置:网站首页>Tianyi cloud web application firewall (edge cloud version) supports the detection and interception of Apache spark shell command injection vulnerabilities
Tianyi cloud web application firewall (edge cloud version) supports the detection and interception of Apache spark shell command injection vulnerabilities
2022-07-26 17:46:00 【51CTO】
Dear Tianyi cloud users : In recent days, ,Apache Spark appear shell Command injection vulnerability , The vulnerability is harmful and POC It has been made public . As of the date of issuance , Tianyi cloud Web Application firewall ( Edge cloud ) A large number of related attacks have been monitored and intercepted - blow , Please take relevant protective measures with the user as soon as possible .
Vulnerability description
Apache Spark It's Apache (Apache) A large-scale data processing engine of the software foundation that supports acyclic data flow and in memory computing , If Apache Spark UI To enable the ACL, be HttpSecurityFilter The code path in allows you to simulate execution by providing any user name . Malicious users may be able to access the permission check function , This function will eventually build a Unix shell Command and execute it . This will result in arbitrary shell Command execution .
Vulnerability Details
Vulnerability name :Apache Spark shell Command injection vulnerability
Hole number :CVE-2022-33891
Hole type : Command injection
Component name :Apache Spark
Affects version :Spark Core – Apache<=3.0.3>=3.1.1&&<=3.1.2>=3.2.0&&<=3.2.1
Vulnerability level : High-risk
Self inspection suggestions
obtain spark edition , Determine whether the version is (∞, 3.0.3]、[3.1.1, 3.1.2]、[3.2.0, 3.2.2) In the range .
Bug fix or mitigation recommendations
The manufacturer has released a patch to fix the vulnerability , Please update to the safe version as soon as possible :Apache Spark 3.1.3、 3.2.2 or 3.3.0 Or later .
Tianyi cloud Web Application firewall ( Edge cloud ) Detection and interception of this vulnerability is supported
Tianyi cloud security research team is in 2022 year 7 month 18 The attention and research work on this vulnerability will be started on the th , Early warning and defense of the vulnerability in advance , Has been in 2022 year 7 month 18 This vulnerability protection is supported on the day , And in 2022 year 7 month 20 Capture this day Apache Spark shell Command injection vulnerability attack - Hitting behavior , Attacking - Help users detect and defend in advance before large-scale attacks occur .
Tianyi cloud has been purchased Web Application firewall ( Edge cloud ) Users of can be protected from this vulnerability without any action , For consultation, please call 400-810-9889 turn 1.
Web Application firewall ( Edge cloud )
1、 Order Web Application firewall ( Edge cloud ) after , Access the protection domain name on the self-service customer console , Access protection domain name supports protection by default , There is no need to manually update the rule base and configuration .
2、 Order Web Application firewall ( Edge cloud ) service . First step , Open tianyiyun official website http://www.ctyun.cn, Register and log in ; The second step , Users without real name authentication need to complete real name authentication according to the prompt to open Web Application firewall ( Edge cloud ) service ; The third step ,BCP The portal already supports ordering , Self service opening function after ordering ; Click the business acceptance form - Create acceptance form ( The trial / commercial )- Add resources - Safety products -Web Application firewall ( Edge cloud )- Submit resources .

3、 After the successful opening , Log in to the customer console : https://cdn.ctyun.cn/h5/ctwaf, Access protection domain name , The protection switch is confirmed as on .
First step , Get into Web Application firewall ( Edge cloud ) Console client , choice 【 Domain name management 】, Click on 【 Add domain name 】;
The second step , Fill in the domain name access information , Fill in the origin information of the domain name according to the guidance of the page 、 Request protocol 、 Service port 、 Back to source protocol, back to source port and other information ;
Add domain name configuration page

The third step , According to your needs , Fill in the origin information of the domain name 、 Request protocol 、 Service port 、 Back to source protocol, back to source port and other information , Click on 【 next step 】 Fill in the domain name security configuration page ;
Domain name security configuration information page
Step four , Select the protection mode and protection template of the domain name , Click on 【 Submit 】; After successful submission , You can click on the 【 Return to the list of domain names 】 page ;
Step five , Complete the operation of adding a new domain name , When the configuration is complete , The domain name management page provides cname Address ;
Step six , To enable the Web Application Firewall Service , You need to protect the domain name DNS The parsing points to the CNAME, In this way, the request to access the protected domain name can be forwarded to the security node , Achieve protective effect .
边栏推荐
- 【机器学习】Mean Shift原理及代码
- Week 16 OJ practice 1 calculates the day of the year
- JS function scope variables declare that the variables that promote the scope chain without VaR are global variables
- 【集训Day3】delete
- 就这一次!详细聊聊分布式系统的那些技术方案
- PIP installation module, error
- After vs code is formatted, the function name will be automatically followed by a space
- [C language classic topic exercise 2]
- 注意 公安部发出旅游客运交通安全预警
- 6-19 vulnerability exploitation -nsf to obtain the target password file
猜你喜欢

hosts该文件已设置为只读的解决方法
We were tossed all night by a Kong performance bug
图的遍历的定义以及深度优先搜索和广度优先搜索(一)

Definition of graph traversal and depth first search and breadth first search (I)
![[cloud native] IVX low code development was introduced into Tencent map and previewed online](/img/f1/40ca06bf65fbc0097f5b61ec7d2509.png)
[cloud native] IVX low code development was introduced into Tencent map and previewed online
Kudu design tablet

一文详解吞吐量、QPS、TPS、并发数等高并发指标

kaggle猫狗数据集开源——用于经典CNN分类实战

Establishment of Eureka registration center Eureka server
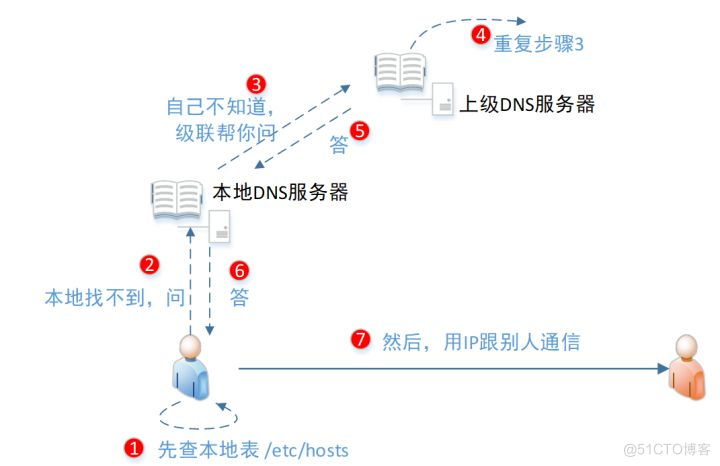
带你熟悉云网络的“电话簿”:DNS
随机推荐
重磅公布!ICML2022奖项:15篇杰出论文,复旦、厦大、上交大研究入选
kaggle猫狗数据集开源——用于经典CNN分类实战
We were tossed all night by a Kong performance bug
Just this time! Talk about the technical solutions of distributed system in detail
Crazy God redis notes 02
JS function scope variables declare that the variables that promote the scope chain without VaR are global variables
一文详解吞吐量、QPS、TPS、并发数等高并发指标
Cloud rendering volume cloud [theoretical basis and implementation scheme]
图的遍历的定义以及深度优先搜索和广度优先搜索(一)
(24)Blender源码分析之顶层菜单显示代码分析
办公软件常用快捷键大全
数据库使用psql及jdbc进行远程连接,不定时自动断开的解决办法
RedisDesktopManager去除升级提示
03 | implement usereducer and usestate
跨站脚本攻击(XSS)
机器视觉在服务机器人中的应用
JS recursive Fibonacci sequence deep cloning
the loss outweighs the gain! Doctors cheated 2.1 million yuan and masters cheated 30000 yuan of talent subsidies, all of which were sentenced!
Basic select statement
第16周OJ实践1 计算该日在本年中是第几天