当前位置:网站首页>MySQL - SQL execution process
MySQL - SQL execution process
2022-06-24 04:32:00 【Game programming】
One 、 Component is introduced
1、 The connector
1) Responsible for communication with clients , It's half duplex mode , This means that the client can only request from the server or the server can send data to the client at a fixed time , Not at the same time .
2) Verify that the user name and password are correct ( database mysql Of user Verify in the table ), If an error occurs, an error notification is returned (deAcess nied for user ‘root’@‘localhost’(using password:YES)), If correct , Will go mysql Permission table for (mysql Medium user、db、columns_priv、Host surface , The global level is stored separately 、 Database level 、 Table level 、 Column level 、 coordination db Database level for ) Query the permissions of the current user .
2、 cache (Cache)
Also known as query caching , The stored data is stored in the form of key value pairs , If caching is turned on , So in a query sql Statement will first determine whether the cache contains the current sql Statement key value pairs , If there is, return the corresponding result directly , If it doesn't exist, perform the next series of operations . If it is not turned on, skip it directly .
3、 analyzer
From the client sql Analyze , This will include preprocessing and parsing , And the keyword extraction 、 analysis , And make up a parse tree . Specific analytic words include but are not limited to select/update/delete/or/in/where/group by/having/count/limit etc. , If we analyze grammatical errors , Will directly throw the client exception :ERROR:You have an error in your SQL syntax.
such as :select * from user where userId =1234;
In the parser, we use the semantic rules to select from where These keywords are extracted and matched ,mysql Will automatically determine keywords and non keywords , Identify the user's matching fields and custom statements . There will also be some checks at this stage : For example, check whether the current database exists user surface , At the same time, if User There is no userId This field will also report an error : unknown column in field list.
4、 Optimizer
Enter the optimizer description sql The statement conforms to the standard semantic rules and can be executed . The optimizer selects the best choice based on the execution plan , Match the appropriate index , Choose the best solution . For example, a typical example is :
surface T, Yes A、B、C Columns are federated (A,B,C), During the query , When sql The query condition is :select xx where B=x and A=x and C=x. A lot of people think it's useless to use indexes , But it actually uses , Although the index must conform to the leftmost principle to be used , But in essence , The optimizer will automatically send this sql Optimize to :where A=x and B=x and C=X, This optimization will be for the underlying to match the index , At the same time, in this stage, preprocessing is performed automatically according to the execution plan ,mysql Accounting calculates the best time for each method of execution , To finalize an executive sql To the last actuator .
The optimizer will be based on Number of scanning lines 、 Whether to use temporary table 、 Whether to sort, etc. to determine whether to use an index , The number of scanning lines can be estimated through statistical information , Statistics can be regarded as the number of unique indexes , Partial sampling can be used to estimate , Specifically, choice N Data pages , Count the different values of the data on these pages , Get an average of , Then multiply by the number of pages in this index , Got it. . But because the index data will change , So the statistics of the index will also change . When the number of data lines changed exceeds 1/M When , The statistics will be recalculated .
5、 actuator
The executor will call the corresponding storage engine to execute sql. The mainstream is MyISAM and Innodb .MyISAM and Innodb The index data structure is B+ Trees memory The index data structure is hash surface

Two 、 Execution process
1、 Write operations
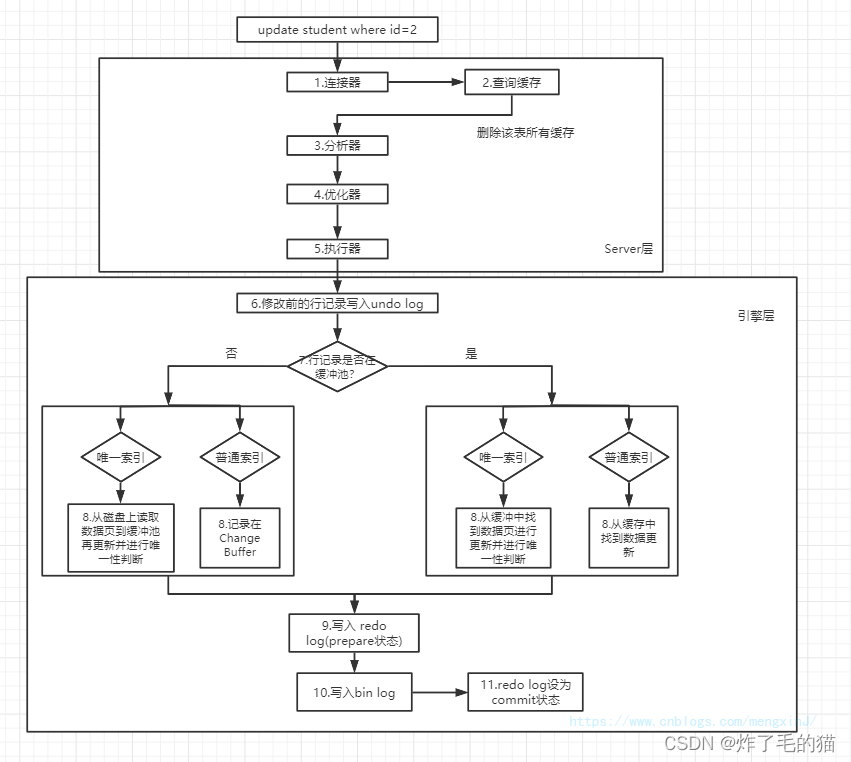
2、 Read operations
The process of query is similar to that of update , But it's a little different , This is mainly due to the differences in their search and filtering , Update because it will be updated after searching , So the query is always in the buffer pool ( The data page that uses the index and contains the data in the buffer pool ). And the query is more complex .
Create table :
create table tbl_test (a int primary key, b int, c int, d int, e varchar(50));create index idx_bcd on tbl_test(b, c, d);insert into tbl_test values (4,3,1,1,'a');insert into tbl_test values (1,1,1,2,'d');insert into tbl_test values (8,8,7,8,'h');insert into tbl_test values (2,2,1,2,'g');insert into tbl_test values (5,2,2,5,'e');insert into tbl_test values (3,3,2,1,'c');insert into tbl_test values (7,4,0,5,'b');insert into tbl_test values (6,5,2,4,'f'); In execution select * from tbl_test where b >= 2 and b < 7 and c > 0 and d != 2 and e != ‘a’; At the time of extraction , Will Where The condition is split into Index Key(First Key & Last Key)、Index Filter And Table Filter .
1、Index Key
Used to determine the SQL The sequential range of queries in the index ( The starting point + Termination point ) Query criteria for , It's called Index Key; Because of a range , It contains at least one starting condition and one ending condition , therefore Index Key Also split into Index First Key and Index Last Key , Respectively used to locate the starting point of index search to the ending point .
Index First Key
Used to determine the starting point of index query range ; Extract rules : Start with the first key value of the index , Check that it's in where Is there... In the condition , If it exists and the condition is =、>= , Then add the corresponding conditions to Index First Key In , Continue reading the next key value of the index , Use the same extraction rules ; If it exists and the condition is > , Then add the corresponding conditions to Index First Key in , To terminate at the same time Index First Key Extraction of ; If it does not exist , Also terminate Index First Key Extraction of .
in the light of SQL:select * from tbl_test where b >= 2 and b < 7 and c > 0 and d != 2 and e != ‘a’, Apply this extraction rule , extracted Index First Key by b >= 2, c > 0 , because c On the condition that >, End of extraction
Index Last Key
The endpoint used to determine the scope of the index query , And Index First Key Just the opposite ; Extract rules : Start with the first key value of the index , Check that it's in where Is there... In the condition , If it exists and the condition is =、<= , Then add the corresponding condition to Index Last Key in , Continue to extract the next key value of the index , Use the same extraction rules ; If it exists and the condition is < , Then add the condition to Index Last Key in , At the same time terminate extraction ; If it does not exist , Also terminate Index Last Key Extraction of
in the light of SQL:select * from tbl_test where b >= 2 and b < 7 and c > 0 and d != 2 and e != ‘a’, Apply this extraction rule , extracted Index Last Key by b < 7 , Because it is < Symbol , End of extraction
2、Index Filter
At the completion of Index Key After the extraction of , We according to the where Conditions fix the index's query range , So is it that every index item in the range satisfies WHERE The conditions are ? Obviously 4 , 0 , 5 , 2 , 1 , 2 All belong to the scope , But they are not satisfied SQL Query criteria for
therefore Index Filter Used after index range determination , determine SQL What other conditions in can be filtered using indexes ; Extract rules : Start with the first column of the index column , Check that it's in where Is there... In the condition , If it exists and where The condition is only =, Then skip the first column and continue to check the index next column , The next index column takes the same extraction rules as the first one ; if where Condition is >=、>、<、<= Some of them , Skip the first column of the index , Put the rest where All index related columns in the condition are added to Index Filter In ; If the first column of the index where Conditions include =、>=、>、<、<= Other conditions , Then this condition and the rest where All index related columns in the condition are added to Index Filter In ; If the first column does not contain query criteria , All index related conditions are added to Index Filter In
in the light of SQL:select * from tbl_test where b >= 2 and b < 7 and c > 0 and d != 2 and e != ‘a’, Apply this extraction rule , extracted Index Filter by c > 0 and d != 2 , Because the first column of the index only contains >=、< Two conditions , So the first column skips , Put the rest of c、d Add two columns to Index Filter in , End of extraction
3、Table Filter
This is a little bit easier ,where All the conditions that can't be filtered by index are included in this ; Extract rules : All queries that do not belong to index columns , All belong to Table Filter In
in the light of SQL:select * from tbl_test where b >= 2 and b < 7 and c > 0 and d != 2 and e != ‘a’, Apply this extraction rule , that Table Filter for e != ‘a’
stay 5.6 Before , It doesn't matter Table Filter And Index Filter Of , These two conditions are directly assigned to Server Layer to filter . The screening process is based on Index Key The conditions of the engine layer are initially screened , Then get the corresponding primary key value, and query back to the table to get the row records initially screened , Pass in Server Layer for subsequent filtering , stay Server Because the index is not used in layer filtering, the whole table scan will be performed . And the optimization of index push down is to make Index Filter Push to the engine layer , In the use of Index First Key And Index Last Key When screening , Take it Index Filter The conditions are screened again , In this way, we can filter out the primary key values corresponding to unqualified records , Reduce the number of times to return to the table , At the same time Server There will also be fewer layers to record , The efficiency of full table scanning and filtering will also be improved .
Here is not used Schematic diagram of index push down and using index push down :
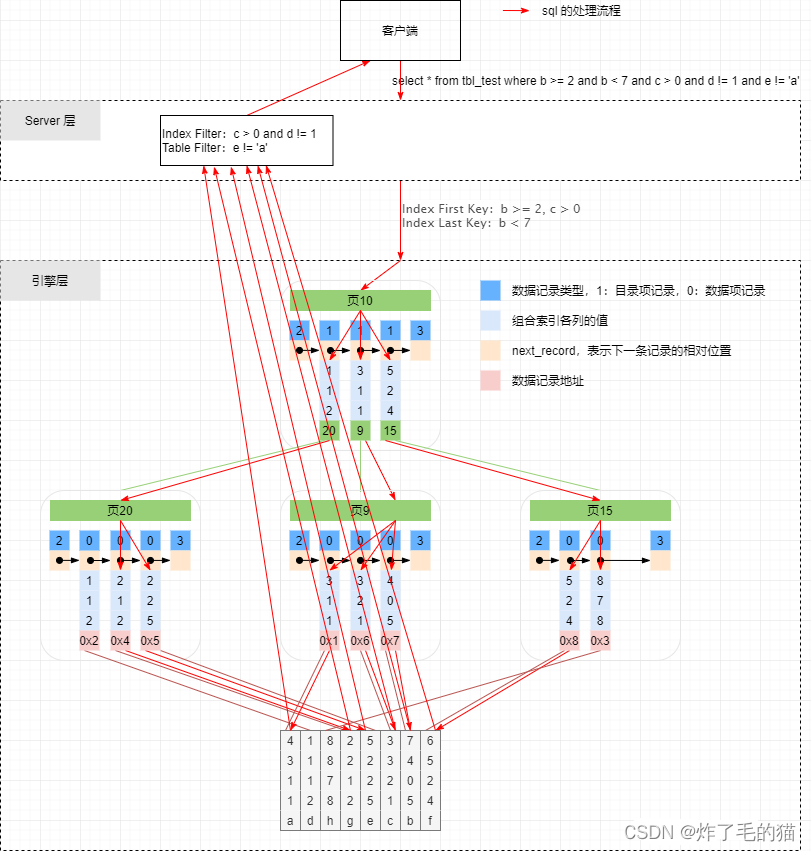
Here is Use Schematic diagram of index push down and using index push down :

3、 summary

Note here that if you don't use the index in the beginning , The data pages on the disk will be read to the buffer pool for query in turn .
3、 ... and 、 summary

Original address :https://www.cnblogs.com/mengxinJ/p/14045520.html#_label2
author : Fried cat
Game programming , A game development favorite ~
If the picture is not displayed for a long time , Please use Chrome Kernel browser .
边栏推荐
- Tencent ECS installs the Minio object storage tool
- What is FTP? What is the FTP address of the ECS?
- How to identify information more quickly and accurately through real-time streaming media video monitoring?
- Easyanticheat uses to inject unsigned code into a protected process (1)
- ribbon
- Worthington木瓜蛋白酶化学性质和特异性
- What is etcd and its application scenarios
- Making a Chatbot based on gpt2
- Mac CentOS installation phpredis
- How to remote server is the price of the server expensive
猜你喜欢

大一下学期期末总结(补充知识漏洞)
Abnova membrane protein lipoprotein solution

Clang代码覆盖率检测(插桩技术)

How does the compiler put the first instruction executed by the chip at the start address of the chip?
Application practice | Apache Doris integrates iceberg + Flink CDC to build a real-time federated query and analysis architecture integrating lake and warehouse

由浅入深的混合精度训练教程

Opengauss version 3.0 source code compilation and installation guide

apipost接口断言详解

Congratulations to Zhong Jun for becoming the maintainer of chaos metric model working group

External network access SVN server (external network access SVN server deployed on the cloud)
随机推荐
How to draw the flow chart of C language structure, and how to draw the structure flow chart
mysql - sql执行过程
Kubernetes 资源拓扑感知调度优化
Download files and close the enhanced module security configuration to visit the website for the first time using IE browser
ribbon
Abnova fluorescence in situ hybridization (FISH) probe solution
Lldb common commands
Gpt/gpt2/dialogpt detailed explanation comparison and application - text generation and dialogue
What is a virtual host server? What are the advantages?
Web technology sharing | [map] to realize customized track playback
15+城市道路要素分割应用,用这一个分割模型就够了
Submit sitemap to Baidu
Summary of the activation function sigmoid relu tanh Gelu in machine learning and deep learning
胶原蛋白酶——Worthington四种类型的粗胶原酶
The official overclocking tool of Intel XTU supports win11 22h2 and 13th generation core Raptor Lake processors
Openeuler kernel technology sharing issue 20 - execution entity creation and switching
How to monitor the operation of easygbs service in real time?
What is etcd and its application scenarios
事件
ribbon