当前位置:网站首页>[download attached] a powerful web automated vulnerability scanning tool - Xray
[download attached] a powerful web automated vulnerability scanning tool - Xray
2022-07-26 11:48:00 【Network security self-study room】
Xray Is a powerful security assessment tool , The main features are :
Fast detection speed . Fast contract awarding ; The vulnerability detection algorithm is efficient . Support a wide range of . Big to OWASP Top 10 General vulnerability detection , As small as all kinds of CMS frame POC, Can support . High code quality . The quality of the people who write the code is high , adopt Code Review、 unit testing 、 Multi layer verification such as integration testing to improve code reliability . High quality can be customized . Various parameters of the engine are exposed through the configuration file , By modifying the configuration file, you can greatly customize the function . There is no threat to safety .xray Positioning as a safety assessment tool , Instead of attacking tools , All built in payload and poc All are harmless tests .
Download address :
GitHub:https : //github.com/chaitin/xray/releases At the end of the paper, we can get Xray Baidu cloud download address
Supported vulnerability detection types :


One . Installation and configuration process :
1. download exe
With windows Download, for example , Download to xray Under the table of contents , For the convenience of operation, the file name is modified as xray.exe;

2. open PowerShell
Enter PowerShell, Click on the open ; Enter the command : ./xray.exe version View version number ;
 Input -h Command to view help information : command : ./xray.exe -h
Input -h Command to view help information : command : ./xray.exe -h

see webscan Help information : command : ./xray.exe webscan -h

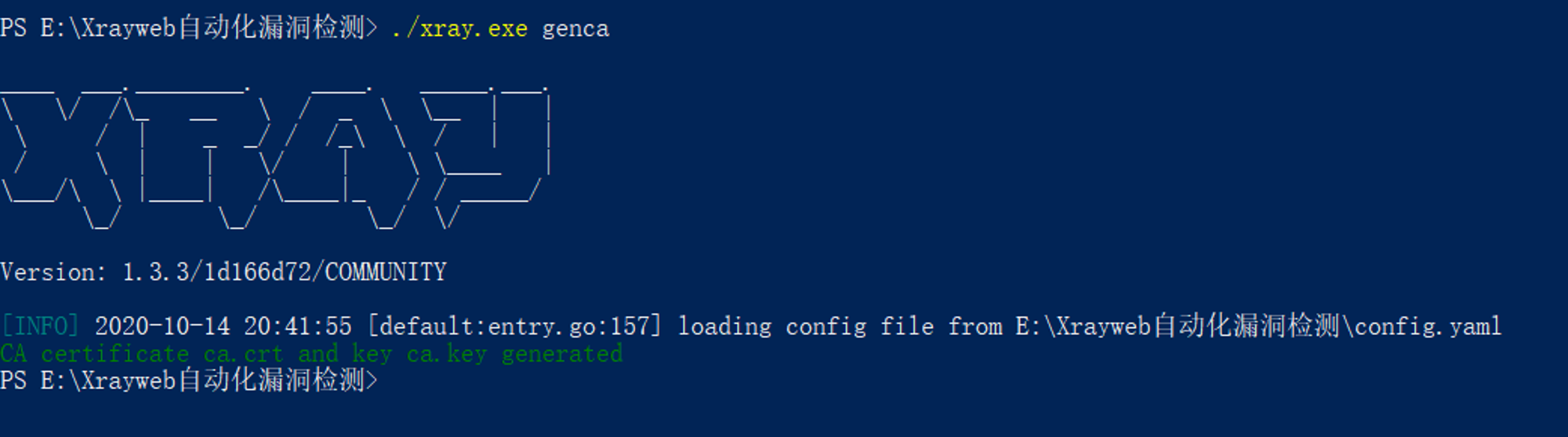
3. Generate Certificate
function ./xray.exe genca Command to generate certificate file ; Get into xray Under the table of contents , Double click Install Certificate ca.crt;
 Installation certificate :
Installation certificate :


Import certificate succeeded !!!

Installation successful !!!
Function one . Scanning configuration of agent mode ( The target station can be set independently )**
Modify the configuration file : open config.yaml file ,ctrl+f Search for mitm key word >> Configure target station >> Set the target :

Function 2 . webscan Scan the website for vulnerabilities
Method 1: Set up proxy in browser : ip: 127.0.0.1 port :8080; Output the test results to the html In the format file :
./xray.exe webscan --listen 127.0.0.1:8080 --html-output test.html
Xray Use guide :( With DVWA For example, the range )
./xray.exe webscan --basic-crawler http://127.0.0.1/DVWA/index.php --html-output test.html
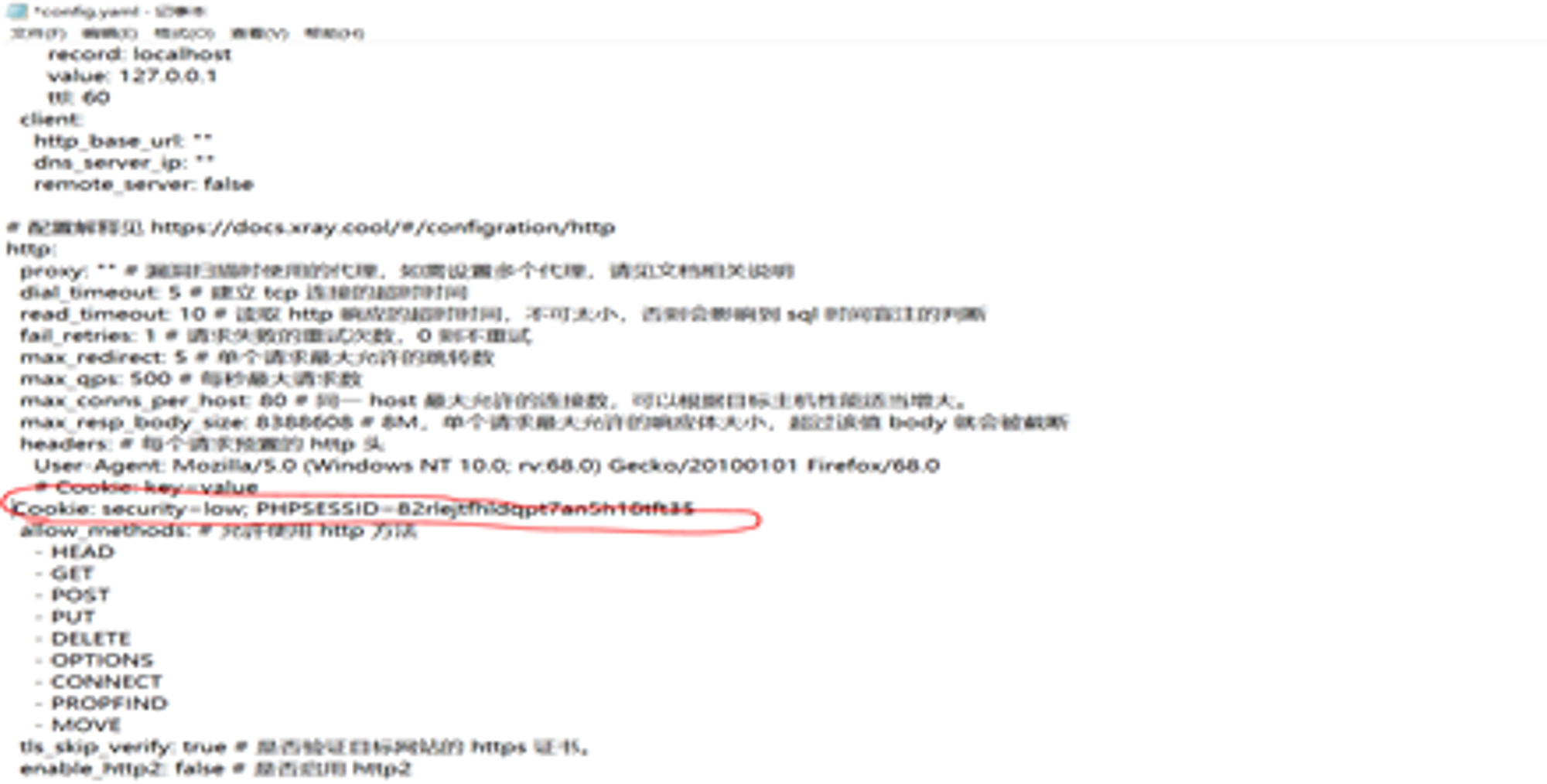
First let's open up DVWA shooting range , Hang up the agent >> Grab the bag >> take DVWA In the data package of the landing page cookie Copy it to our Xray In the configuration file of the scanning tool ;


And then we go into Xray In the configuration file of the scanning tool , take cookie Import profile , Then use the command :
( Be careful : With powershell Execution time , The order is ./xray.exe; With cmd Runtime , The order is xray.exe)
xray.exe webscan --basic-crawler http://127.0.0.1/DVWA/index.php
Yes dvwa Conduct vulnerability scanning in the shooting range ;( The scanning results are as follows )
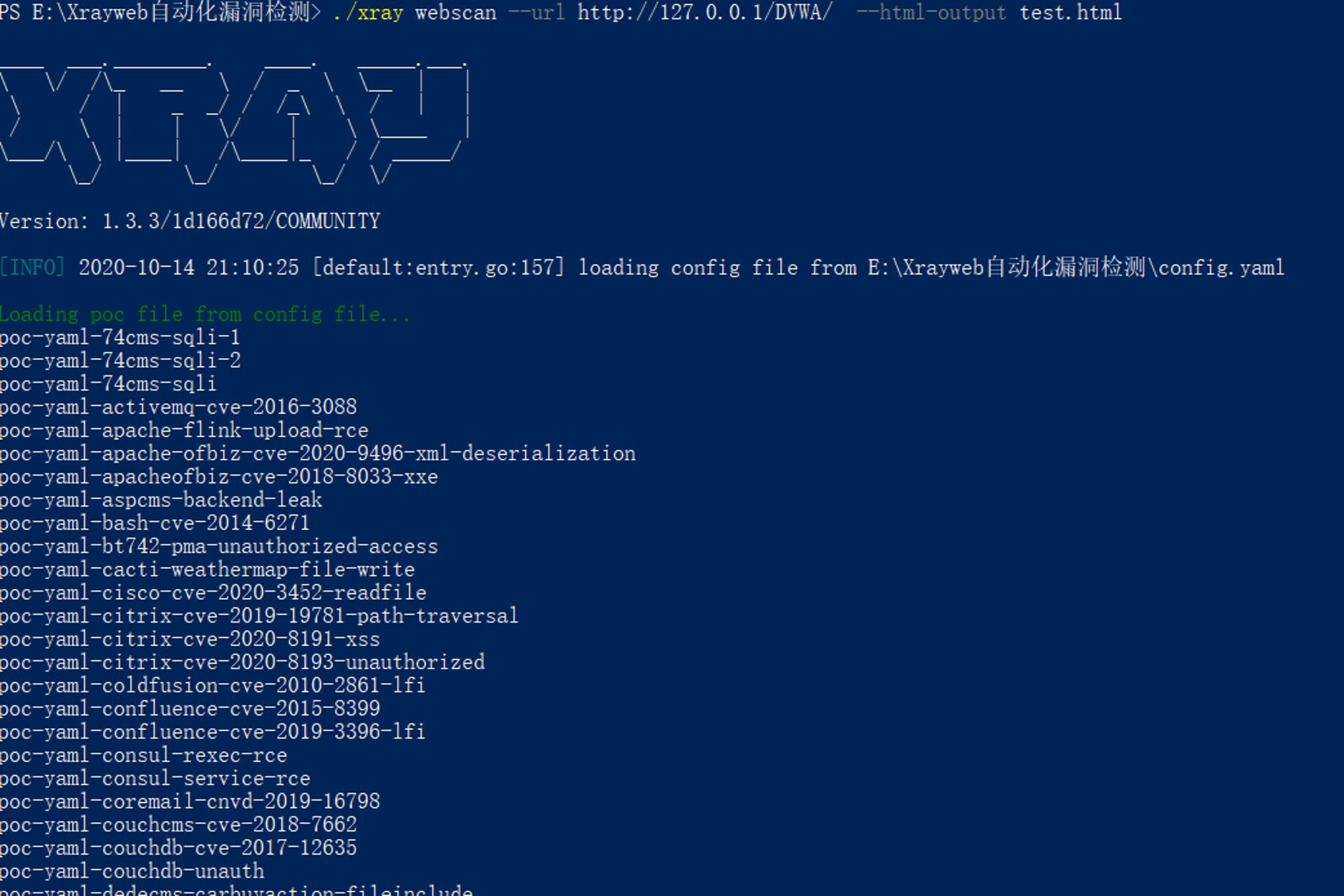

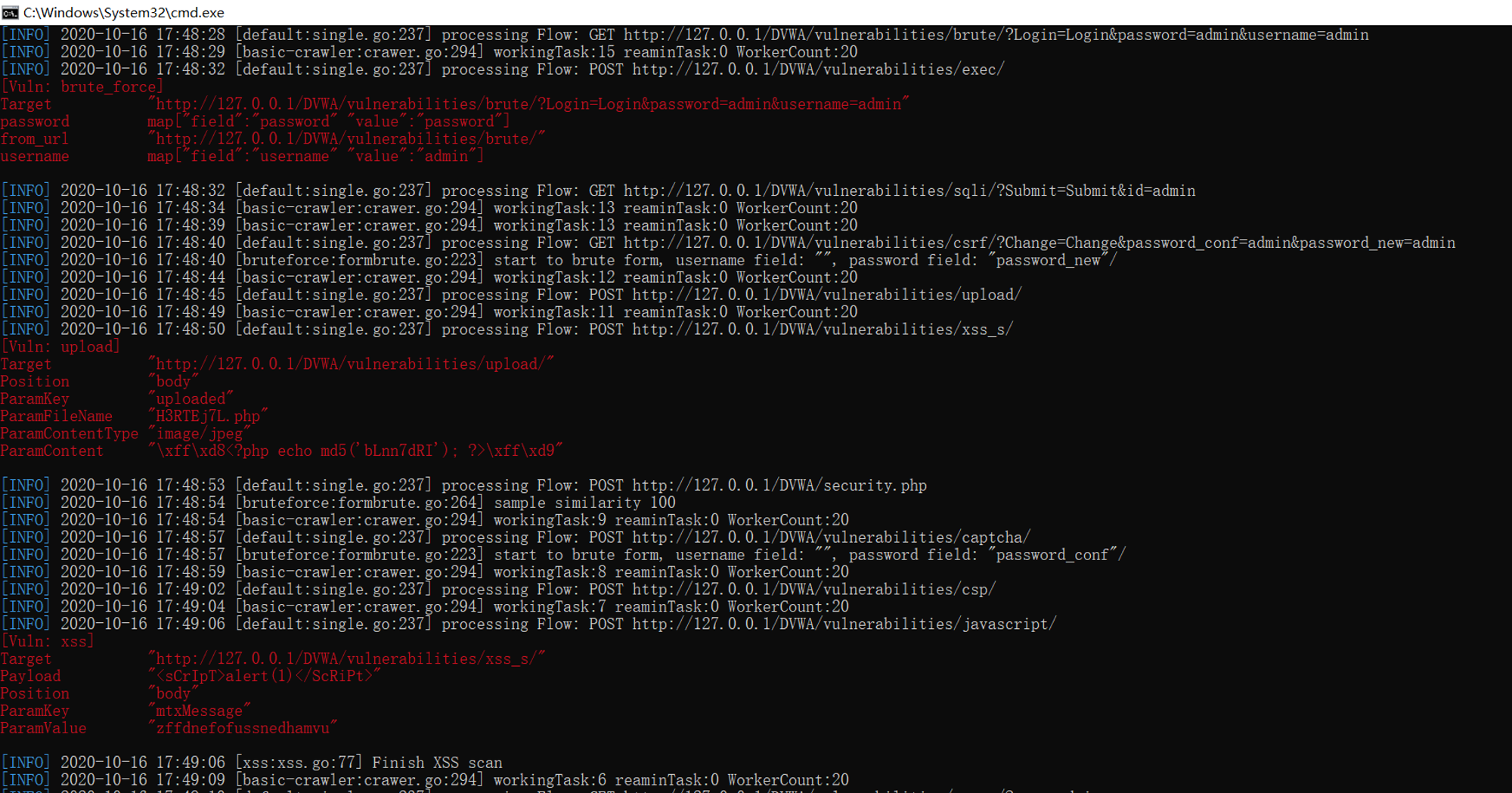

The test results are output to our defined html Format file :( You can see that the scan shows DVWA Brute force cracking in the shooting range , Upload files ,sql Inject ,xss, Command line injection and other vulnerabilities )

Specify the scan plug-in :
Use --plugins Parameter can choose to enable only part of the scanning plug-in , Multiple plug-ins can be separated by commas , Such as :
./xray webscan --plugins cmd_injection --url http://example.com/
Use basic crawler crawling or crawler crawling links for subdivision scanning :
./xray.exe webscan --basic-crawler http://example.com
Be careful : With powershell Execution time , The order is ./xray.exe; With cmd Runtime , The order is xray.exe
summary :
ctrl + c Command exit ; 2 If the generated result report shows that it already exists , The folder report file can be deleted , Regenerate can also change the name of the report file to regenerate ; The browser opens and we are config.yaml The target station set by the configuration file , The scanning test will be carried out automatically ; A report will not be generated if it is terminated halfway ; 
边栏推荐
- 10 reduce common "tricks"
- Data Lake (19): SQL API reads Kafka data and writes it to iceberg table in real time
- System call capture and analysis - ring layer kprobe hijacks system calls
- 《微信小程序-进阶篇》Lin-ui组件库源码分析-Button组件(一)
- 3.1 创建菜单与游戏页面——上
- 7月27日19:30直播预告:HarmonyOS3及华为全场景新品发布会
- 外包干了四年,废了...
- Didi was fined 8billion! The era of making money from user data is over
- 【万字长文】使用 LSM-Tree 思想基于.Net 6.0 C# 实现 KV 数据库(案例版)
- swagger2.9.2教程 与swagger3.0.0教程
猜你喜欢

国内11所“袖珍”大学!在校园跑步,还没加速就出校门了...

。。。。。。

数据中台建设(二):数据中台简单介绍

ESP8266-Arduino编程实例-开发环境搭建(基于Arduino IDE)

测试用例千万不能随便,记录由一个测试用例异常引起的思考
梅科尔工作室-华为14天鸿蒙设备开发实战笔记八
《微信小程序-进阶篇》Lin-ui组件库源码分析-Button组件(一)

Wulin headlines - station building expert competition

28. Implementation of file directory parsing code

Meiker Studio - Huawei 14 day Hongmeng equipment development practical notes 8
随机推荐
Mongodb - use $type to query whether the type of a field is XXX
。。。。。。
Scrapy IP agent is not responding
ESP8266-Arduino编程实例-GPIO输入和输出
GA-RPN:引导锚点的建议区域网络
Basic recursive equation of DP
Esp8266 Arduino programming example - development environment construction (based on platformio)
JS use webuploader to do blocking and breakpoint continuation of large files
Esp8266 Arduino programming example - know esp8266
ESP8266-Arduino编程实例-认识ESP8266
Esp8266 Arduino programming example - development environment construction (based on Arduino IDE)
Static routing and dynamic routing
征婚故事
五万美元的年薪是如何花光的
Colt DCS is serious about building a green data center!
ESP8266-Arduino编程实例-开发环境搭建(基于Arduino IDE)
打造绿色数据中心,Colt DCS 是认真的!
Leetcode / Scala - sum of two numbers, three numbers, four numbers, and N numbers
How to use data pipeline to realize test modernization
[error reporting] what do you read in the log