当前位置:网站首页>360edr planing
360edr planing
2022-06-22 02:53:00 【Ink mark vs. breeze】
Catalog
polishing EDR Necessary and critical capabilities
Multiple advantages to solve terminal security threats
advantage 1: High quality data acquisition capability —— Based on the unique nucleation engine
advantage 2: Global vision —— Massive safe big data
advantage 3: Complete safety analysis and detection capabilities
advantage 4:SaaS And intelligence
summary
With the development of Digitalization , Network security threats are evolving ,EDR The product is also expected to really solve the problems faced by the terminal APT、0day、 Blackmail virus and other advanced threats . However, the actual combat proves that : Conventional EDR The product faces many pain points , Cannot solve the security problem of multiple scenarios , For example, tradition EDR product The storage and processing capacity of massive big data is insufficient , Give Way EDR Overall threat identification becomes empty talk ; And so on Do not have the ability to summarize knowledge base and security analysis from actual combat , This makes it difficult for valuable data to be effectively used on the customer side ; Again Lack of flexible performance tuning and adaptive mechanisms , Collecting a large amount of endpoint information leads to the consumption of a large number of valuable resources of terminals and servers .
To make up for the tradition EDR Deficiency , three six zero (601360.SH, Hereinafter referred to as “360”) Its government enterprise security group relies on 360 Secure big data provided by cloud secure brain 、 Powerful capabilities such as Threat Intelligence and attack and defense knowledge base create a future oriented EDR Solution ——360 Terminal detection response system ( hereinafter referred to as “360 EDR”).360 EDR At the same time have SaaS And intelligence , You can continuously monitor endpoint activity behavior , In depth detection of threat risk 、 Intelligent analysis and professional processing , Significantly reduce user costs , Improve deployment efficiency , Linkage of big data across the network , Comprehensively solve the user's terminal security problems .
polishing EDR Necessary and critical capabilities
At the level of terminal security products ,360 Have 17 Years of experience in terminal security attack and defense confrontation , Accumulated a large amount of network wide secure big data , After more than ten years with various Trojans 、APT family 、0day Vulnerability attack and defense practice , Continue to polish the terminal's malicious behavior detection and response capability , Accumulated comprehensive and detailed terminal behavior detection technology , It has created an industry benchmark in the effect of terminal security products . As the leader of terminal security products ,360 From the practical level, the future oriented EDR The key capabilities that the product should have , Specific include :
EDR The product must have the ability to store and process massive big data . Secure big data is the support for building a wide enough coverage 、 Detection and defense model with high enough accuracy , And the necessary basis for finding the trace of the attacker . stay EDR in , All kinds of security behavior data collected by the endpoint are terminal security defense 、 The core basis for detection and response , It's about responding to APT An important means of attack , Through the automation of multi-dimensional and high-quality massive big data 、 Intelligent correlation analysis and operation , The attack process can be traced , Find the source of vulnerability and attack , It is an effective way and method to effectively defend and ensure terminal security .
It shall also have comprehensive and professional safety analysis ability .EDR Products need to have various safety detection and analysis technologies , It can analyze massive heterogeneous data , At the same time, it is combined with the whole network APT intelligence , Ensure that all threats are fully visible . As the clues of advanced threat attacks are often hidden in the similar behaviors of conventional software running , Therefore, the detection needs to conduct security analysis on the terminal massive data , The ability to repeatedly detect historical data is required , All these require the product to have strong big data operation and analysis ability .
In addition, it should also have the ability of actual attack and defense confrontation . Based on the latest vulnerabilities 、APT And so on , Machine learning and big data automated correlation analysis are absolutely essential , However, it is also very important to analyze and interpret the collected data sets manually , Safety experts will pass on safety knowledge and professional skills , And the threat detection and defense model based on the actual combat summary for many years , Conduct real-time and continuous tracking analysis , And provide security solutions for specific scenarios .
With the continuous evolution of offensive and defensive confrontation in the digital age , With SaaS And intelligence EDR Form to help enterprise users solve long-term safe operation problems has become a key capability . By integrating cloud capabilities and terminal resources to SaaS The service form is oriented to large, medium and small customers , It can enhance the threat defense and threat resistance of Intranet endpoints , Ensure the smooth and continuous operation of various production and office businesses , Has become a new generation EDR Coping with predictable trends in advanced attacks .
Multiple advantages to solve terminal security threats
As a future oriented terminal security product , In terms of composition 360 EDR The technical architecture is divided into three parts : Terminal agent 、EDR Server、360 Core safety brain . Where the terminal agent is 360 EDR The core components ,360 EDR Depending on 360 Continuous empowerment of the cloud core security brain 、360 The secure big data platform of the core secure brain gives full play to the terminal agent's acquisition and processing capabilities , At the same time through EDR Sever An efficient data analysis engine , Finally, it can detect and suppress advanced threats .

advantage
360 EDR It has the following outstanding advantages in the process of product implementation : Advantages of high-quality data acquisition capability based on the unique nucleation engine 、 The advantages of the whole network perspective based on massive safe big data 、 Complete safety analysis capability and detection capability , as well as SaaS And intelligent capabilities .
advantage 1: High quality data acquisition capability —— Based on the unique nucleation engine
Data acquisition quality , To determine the EDR Real test results .360 EDR Use 360 Kernel analysis technology accumulated in more than ten years 、 The unique kernel hardware virtualization engine and other engines collect security data , On the one hand, it realizes multi-dimensional big data collection , The time dimension includes before the attack 、 In attack 、 After the attack , The behavioral dimension includes standard behaviors 、 Differential behavior 、 Sabotage , The phase dimension includes pre infection 、 Infection , Post infection, etc . On the other hand ,360 EDR Provide monitoring capabilities beyond the kernel level , utilize CPU Enhanced hardware virtualization mechanism 64 Safety protection of bit system , Create... For the process 、 Process injection 、 Module loading 、 The registry value is written to 、 Comprehensive monitoring of file writing and other behaviors , Avoiding tradition EDR Rely heavily on Ring3 Disadvantages of user layer monitoring technology , At the same time, it can directly detect the kernel and application layer 0day Exploit behavior , Effective confrontation APT Bypass attack .
advantage 2: Global vision —— Massive safe big data
Massive big data as 360 EDR Continuous driving force of , Be able to synchronize global threats in real time , Continue to enhance the understanding of APT Detection and perception of attacks . be based on 17 Years of practical experience ,360 A collection of super 300 100 million program file samples ,22 Trillions of security logs 、90 100 million domain name information 、2EB The above security big data , Can instantly call more than one million CPU Participate in calculation 、 Retrieving and correlating multidimensional threat data . This is a 360 EDR Core strengths —— Based on massive terminals 、 Massive secure big data structure obtained in actual combat .
advantage 3: Complete safety analysis and detection capabilities
No, “ visual ” This premise , The handling of any threat is empty talk , And the visualization of threats is 360 EDR Of “ radar ” Ability . This kind of attack “ radar ” Ability , Strong security analysis capability is required .360 As a family with 17 Year old digital security leadership company , Realized from ToC To ToB/G Safety capability accumulation , Therefore, it has the most powerful security analysis capability and technology in China .360 EDR Through various detection and analysis techniques , Analyze massive heterogeneous data , At the same time, it is combined with the whole network APT intelligence , Ensure that all kinds of threats are fully visible .
advantage 4:SaaS And intelligence
besides ,360 EDR The product also has the ability to realize SaaS Intelligent and intelligent . One side ,360 EDR Can be used in the cloud SaaS Multi tenant deployment mode , Provide users with safe big data storage 、 Real time data processing 、 Correlation analysis 、 Parallel query and second response capability , Support security experts to actively hunt threats at any time . On the other hand , Based on the killing engine 、 Knowledge map and AI Technology improvement brought by technology ,360 EDR More and more intelligent , Including the realization of automatic classification of massive security events 、 Automatic prioritization and automatic response to attacks .
summary
Overall speaking ,360 EDR rely on 360 Cloud security brain in data 、 intelligence 、 The empowerment of experts , And the cloud earth Integrated Architecture , Can achieve SaaS And intelligence , Provide the most powerful service for government and enterprise users 、 The most comprehensive safety analysis ability 、 Attack traceability 、 Visual presentation ability 、 Quick response 、 Joint defense and linkage capability 、 Customized security operation capability and rich subscription services , Help users greatly improve the identification of security risks 、 Protect 、 testing 、 Respond to 、 Recovery and other capabilities .
边栏推荐
- 自适应批作业调度器:为 Flink 批作业自动推导并行度
- GraphAcademy 课程讲解:《Neo4j 图数据科学简介》
- Deep Copy
- ZCMU--1052: Holedox Eating(C语言)
- Typora + picGo 配置图床实现图片自动上传
- B-Tree
- Day20qt multiple forms switching idea 2021-10-31
- Li Kou today's question 1108 IP address invalidation
- How to select the appropriate version of neo4j (version 2022)
- Day13QMainWindow2021-09-28
猜你喜欢

Automated tools - monitoring file changes
![Comprehensive interpretation by enterprise reviewers: enterprise growth of [State Grid] China Power Finance Co., Ltd](/img/4e/345ceb4e91aae844d7ab53ad3fd988.png)
Comprehensive interpretation by enterprise reviewers: enterprise growth of [State Grid] China Power Finance Co., Ltd
![[5. high precision subtraction]](/img/87/52b154ba5816e1d6541c885b680a1f.png)
[5. high precision subtraction]

Select for i/0 multiplexing

Brief analysis of application source code of neo4j intelligent supply chain

The brand, products and services are working together. What will Dongfeng Nissan do next?
ACL 2022 | multilingual knowledge map reasoning based on self supervised graph alignment
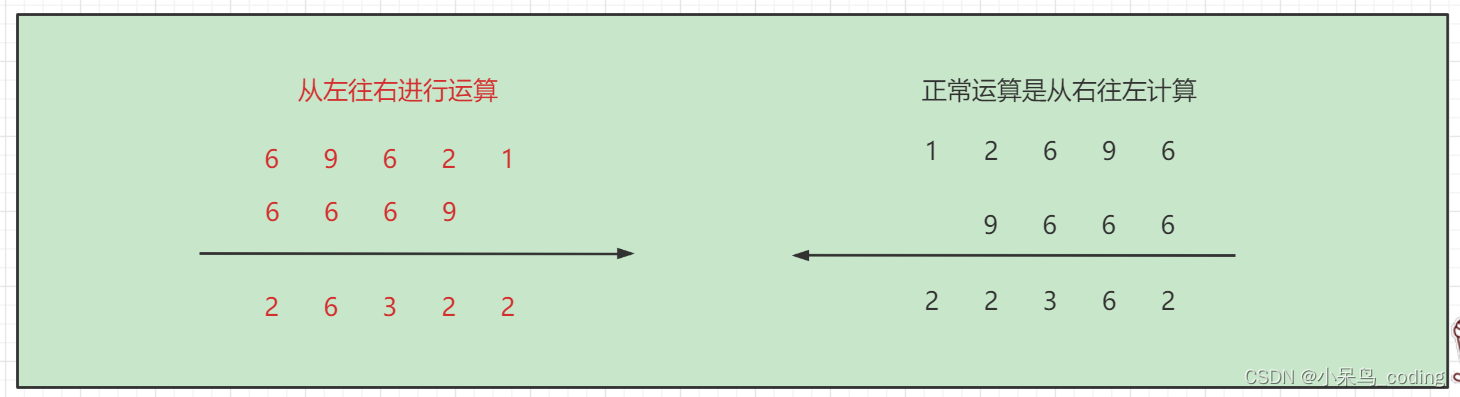
【4. 高精度加法】

最新发布:Neo4j 图数据科学 GDS 2.0 和 AuraDS GA

Figure data platform solution: cluster deployment
随机推荐
Starting WDA with tidevice
【8、一维前缀和】
使用 Neo4j 沙箱学习 Neo4j 图数据科学 GDS
Brief analysis of application source code of neo4j intelligent supply chain
Sword finger offer 37 Serialized binary tree
Sword finger offer 56 Delete duplicate nodes of the linked list
【9. 子矩阵和】
Graphacademy course explanation: introduction to neo4j graph data science
Flink CDC MongoDB Connector 的实现原理和使用实践
Day16QtQLabel2021-10-22
关于mysql的int型主键自增问题
【Docekr学习遇到的坑】
银联支付 返回商户 Nignx post请求405
Extending kubernetes API with CRD
B-Tree
PMP项目管理知识该如何运用?
Game Jam开发周期
Microblog closes publishing multiple part-time fraud information illegal accounts: how to crack down on data fraud
GraphAcademy 课程讲解:《Neo4j 图数据科学简介》
Sword finger offer 12 Path in matrix