当前位置:网站首页>Swintransformer network architecture
Swintransformer network architecture
2022-06-12 16:55:00 【QT-Smile】
SwinTransformer
1. original text :
2.
3.
4.
For different versions of Swin Transformer Model , there C It's different 
5.
Conduct Linear Embedding after , Each channel is also Layer Norm
6.
Both of these are implemented according to the convolution layer 
7.
Here are two Swin Transformer Blocks, But these two are usually used in pairs 
8.
The multi-layer perceptron here is Vision Transformer The author said , So I didn't talk about it in this video 
9.
This position , For classified networks , In fact, there is a network structure behind it , It's just not drawn here 
10.
after Patch Merging Then the length and width of the characteristic matrix will be halved , The number of channels will be doubled 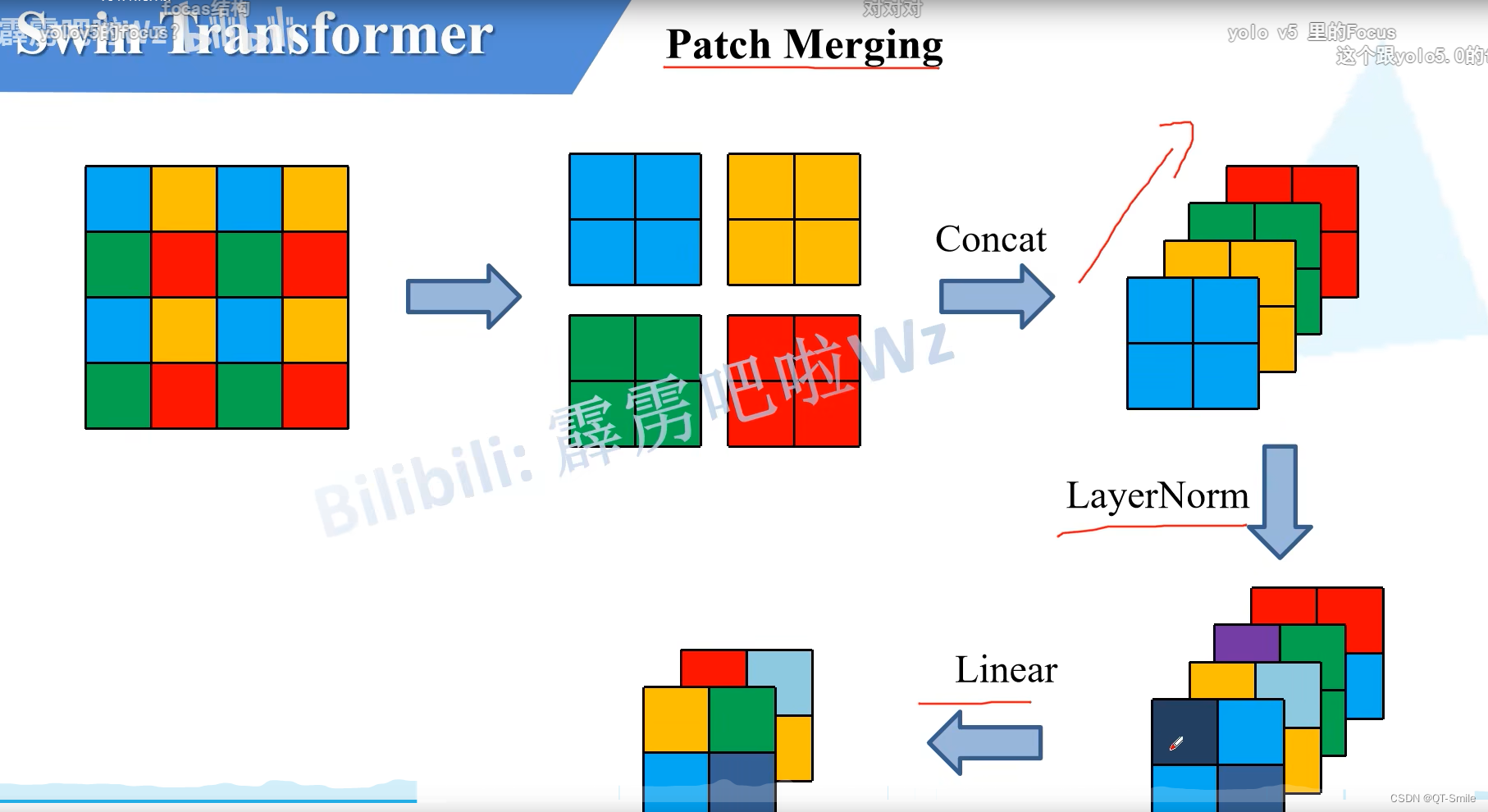

11.
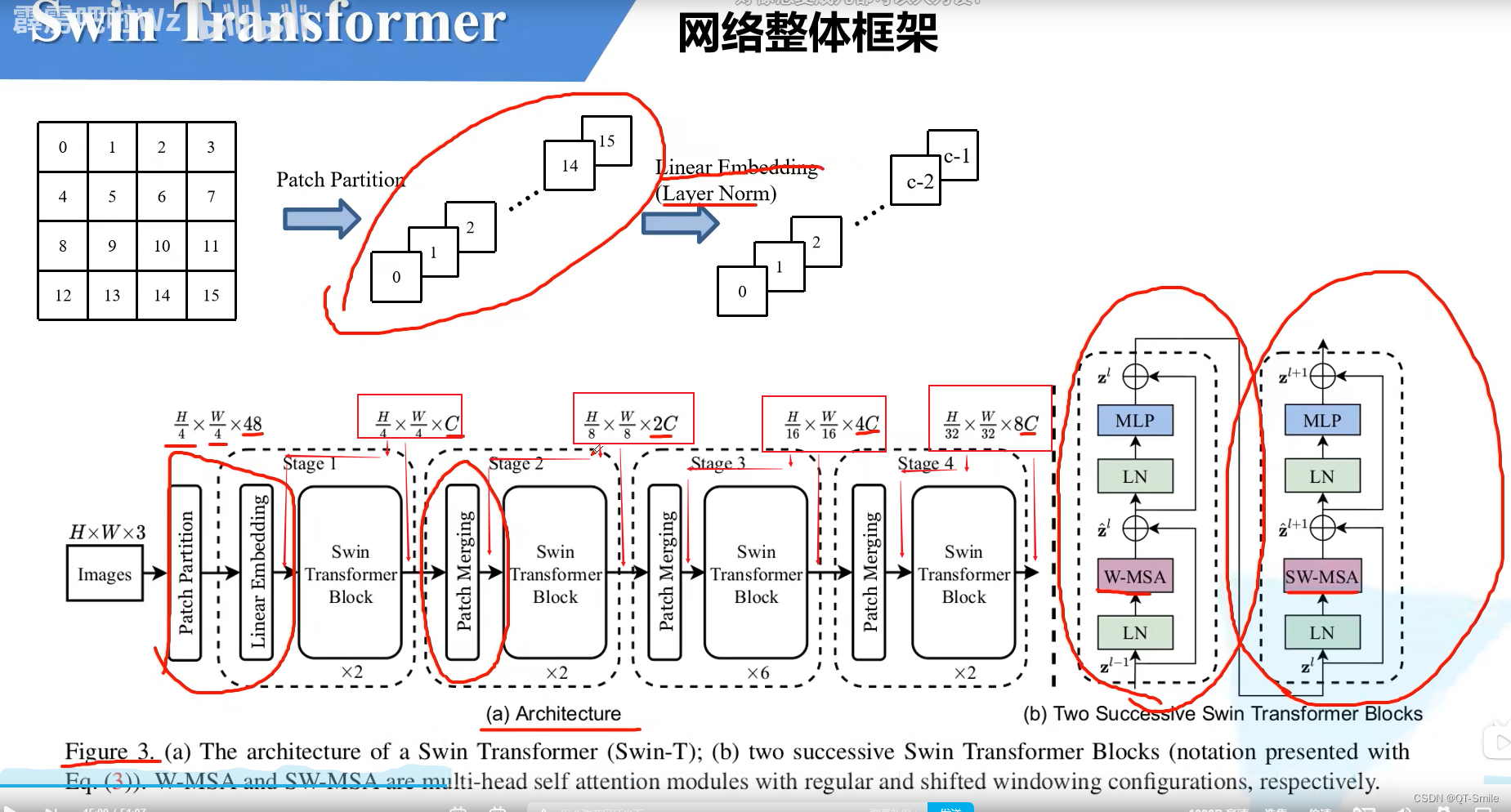
12.
MSA Namely transformer The long attention mechanism in ,MSA That is, every pixel of the characteristic matrix will calculate its Q,K,V, And every pixel will also go with other pixels K Multiply , Calculate the relevant weights , Finally multiply by the relevant V, Finally hungry to the final result .
W-MSA Is to use for each small characteristic matrix MSA, The author did this to reduce the amount of computation .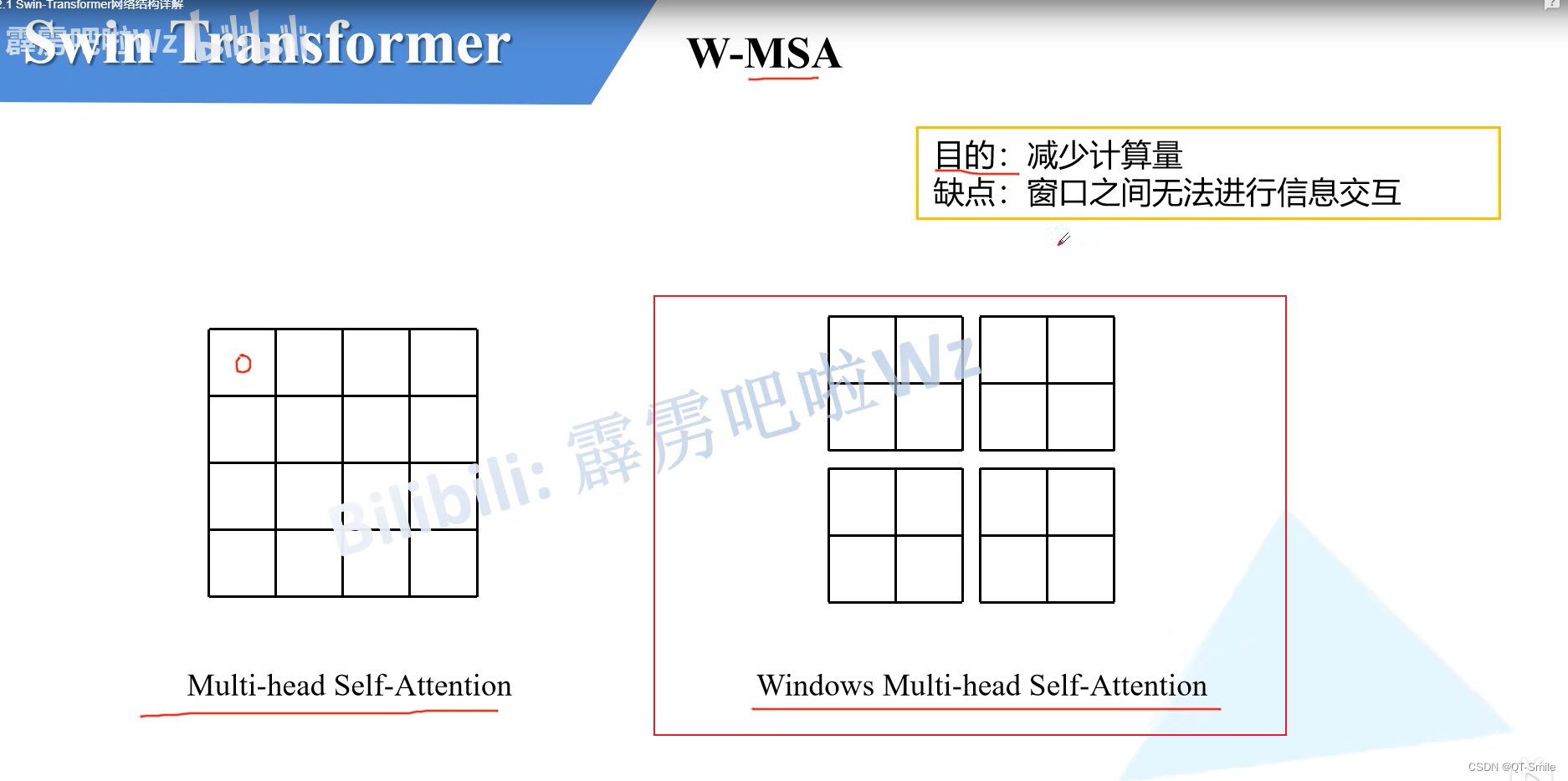
W-MSA shortcoming : There is no information exchange between windows , So I can put MDTA and W-MSA Make two branches , Calculate details and global information respectively , Or use convolution layers and W-MSA Make two branches , Convolution layer calculates global information ,W-MSA Calculate local information . 14.
14.
15.
In order to solve W-MSA The disadvantage of not being able to communicate between different windows , Created SW-MSA

16.

Put the matrix above , First move two pixels up , Then move two pixels to the left to get the following characteristic matrix 
17.






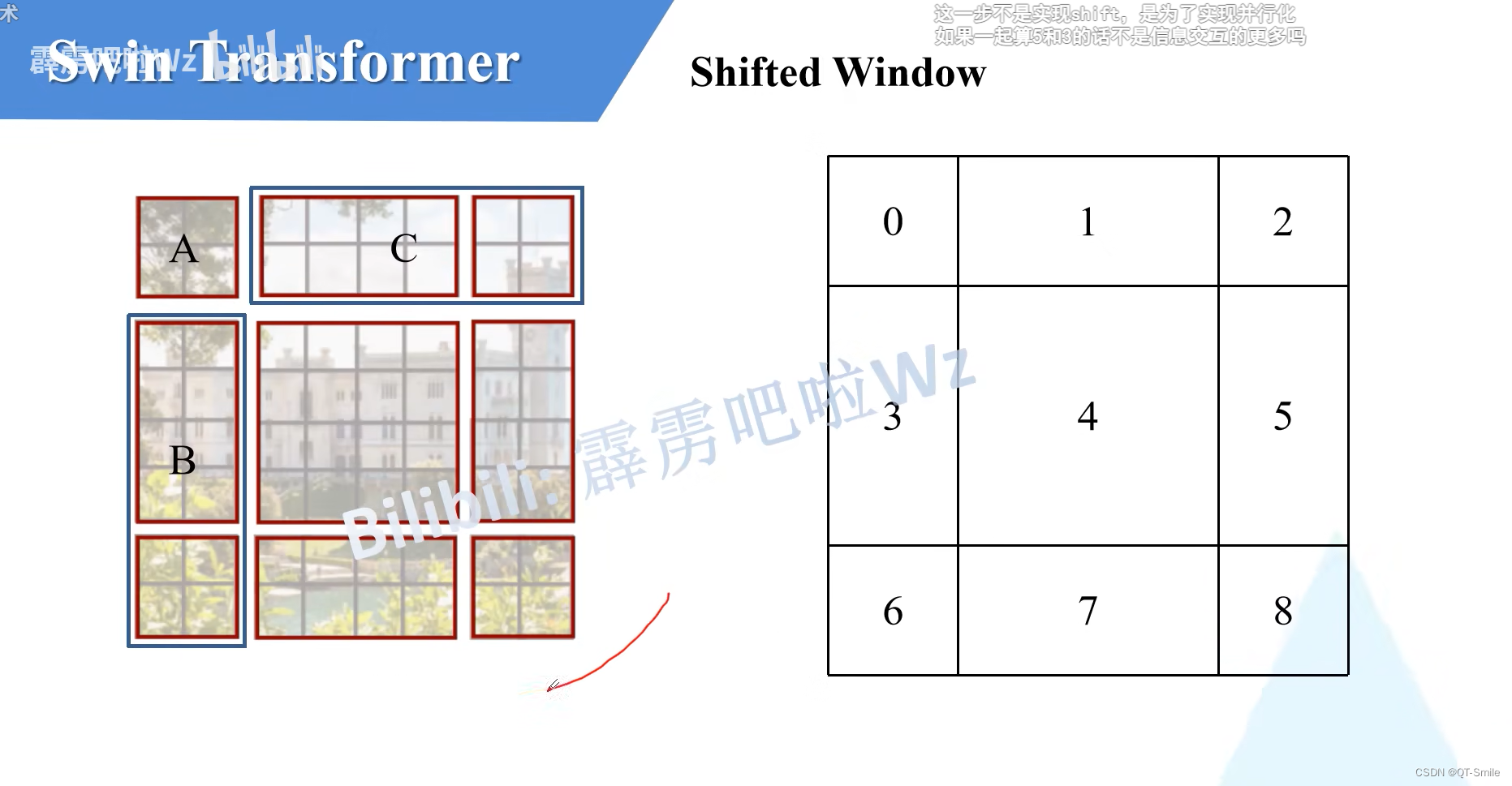
18.







The final functions of the two structures are the same 
21.
With Swin-T give an example 


边栏推荐
- VIM from dislike to dependence (16) -- macro
- 云开发坤坤鸡乐盒微信小程序源码
- Information outline recording tool: omnioutliner 5 Pro Chinese version
- Demande de doctorat | xinchao Wang, Université nationale de Singapour
- CVPR 2022 | meta learning performance in image regression task
- [adult Liu Er - pytorch deep learning practice] notes with learning (I)
- Exception assertion of assertj
- How to do a good job of testing in the company (do a good job of testing)
- How to play the map with key as assertion
- js 使用Rsa 加密 解密
猜你喜欢

Qt开发高级进阶:初探qt + opengl

Leetcode 2194. Excel 錶中某個範圍內的單元格(可以,已解决)

初识GO语言

Leetcode 2194. Cells within a range in Excel table (yes, solved)

About component value transfer

Overview of webrtc's audio network Countermeasures

邱盛昌:OPPO商业化数据体系建设实战

快速入门scrapy爬虫框架

Recommend AI intelligent drawing repair software

key为断言的map是怎么玩的
随机推荐
Go的变量
\Begin{algorithm} notes
\begin{algorithm} 笔记
The C programming language (version 2) notes / 8 UNIX system interface / 8.5 instance (implementation of fopen and Getc functions)
JS monitors whether the user opens the screen focus
Object. Keys traverses an object
软件工程 学生信息管理系统 结构化的需求分析
(七)循环语句for
Idea how to set the guide package without * sign
Swin transformer code explanation
叶子分享站PHP源码下载
使用GCC的PGO(Profile-guided Optimization)优化整个系统
JVM memory model and local memory
Différence entre le mode grand et le mode petit
PAT甲级 1139 第一次接触
token与幂等性问题
C#期末复习编程题(老师猜的)
\begin{algorithm} 笔记
反馈式编译
MySQL interview arrangement