当前位置:网站首页>Why is the field of hacking almost filled with boys?
Why is the field of hacking almost filled with boys?
2022-07-31 15:15:00 【Python_chichi】
This is what you think of a hacker

But actually they are like this:

and this:

The first fat man with a big belly and an ecstatic posture was Richard Stallman, the famous hacker who developed GCC,GDB,GNU Emacs**, the originator of the **GNU project.The second fat man is called Wozniak, a famous geek, Apple Inc. co-founder, when he soldered boards and made computers,Jobs was selling everywhere.
Becoming a hacker requires relatively proficient in computer software and hardware technology, network, security technology, etc., and requires considerable accumulation.Maybe the girl doesn't want to continue doing it if she becomes such a fat person after reading it.
If you want to become a hacker, you must be proficient in a high-level language. It is recommended to use the python language to get started. Of course, this is just my personal opinion.
Introduction to Python
It is an object-oriented, literal computer programming language with a development history of nearly two decades, mature and stable.It includes a set of well-established and easy-to-understand standard libraries that can easily accomplish many common tasks.Its syntax is simple and clear, using as few non-synonymous English words as possible, and unlike most other programming languages, which use curly braces, it uses indentation to define blocks of statements.
Like dynamic languages like Scheme, Ruby, Perl, Tcl, etc., Python has garbage collection capabilities that automatically manage memory usage.It is often used as a scripting language to handle system administration tasks and network programming, however it is also well suited for a variety of advanced tasks.The Python virtual machine itself can run on almost all operating systems.Using tools like py2exe, PyPy, PyInstaller, etc. can convert Python source code into a program that can be run without the Python interpreter.
The official interpreter for Python is CPython, which is written in C and is a community-driven free software currently managed by the Python Software Foundation.
Python supports imperative programming, object-oriented programming, functional programming, side-oriented programming, and generic programming.
3. Sharing of Hacker Learning Resources:
Python all-direction learning route
Python all-direction route is to organize the technical points commonly used in Python to form a summary of knowledge points in various fields. Its usefulness is that you can follow theFind the corresponding learning resources for the above knowledge points to ensure that you can learn more comprehensively.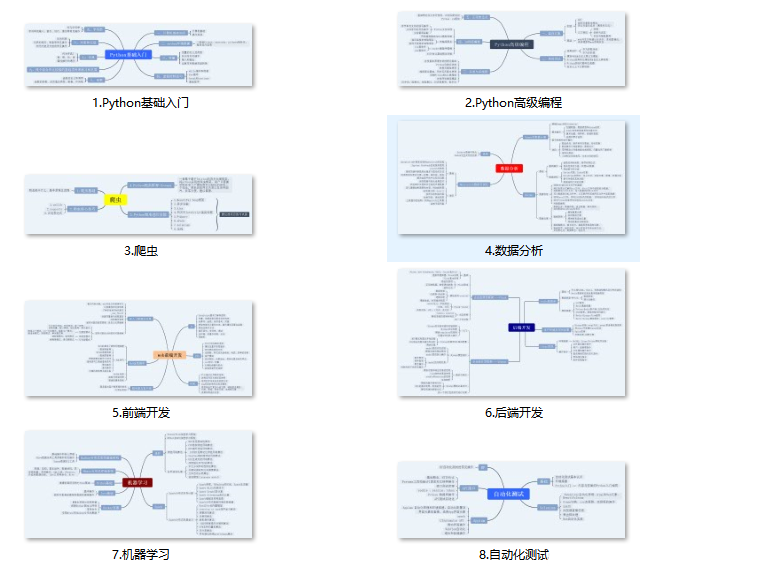
Learning software
To do well, a worker must first sharpen his tool.The common development software for learning Python is here, which saves everyone a lot of time.

Full set of PDF e-books
The advantage of books is that they are authoritative and systematic. At the beginning of learning, you can just watch videos or listen to someone's lectures, but after you finish learning,You think you have mastered it. At this time, it is recommended to read books. Reading authoritative technical books is also the only way for every programmer.
Introductory learning videos
When we watch videos to learn, we can't move our eyes and brains without hands. The more scientific way of learning is to use them after understanding. At this time, the hands-on project is veryfit.
Practical cases
Optical theory is useless, you have to learn to follow along, and you have to practice, in order to apply what you have learned into practice, you can do something at this timePractical cases to learn.
Interview materials
We must learn Python in order to find high-paying jobs. The following interview questions are the latest interview materials from first-tier Internet companies such as Ali, Tencent, and Byte, and there areAli gave an authoritative answer. After reviewing this set of interview materials, I believe that everyone can find a satisfactory job.
If you need the above, I can share it too!Click the csdn certified WeChat card below to get it for free!
边栏推荐
猜你喜欢
![[CUDA study notes] First acquaintance with CUDA](/img/a2/f322ebe9dc483028f68882ee2c866b.png)
[CUDA study notes] First acquaintance with CUDA

乡村基冲刺港交所:5个月期内亏2224万 SIG与红杉中国是股东

Architecture actual combat battalion module 8 message queue table structure design

AVH Deployment Practice (1) | Deploying the Flying Paddle Model on Arm Virtual Hardware
使用 Chainlink Keepers 实现智能合约函数的自动化执行

How useful is four-quadrant time management?
Word table to Excel

OpenCV测量物体的尺寸技能 get~
浏览器自带的拾色器

Internet banking stolen?This article tells you how to use online banking safely
随机推荐
Matlab矩阵基本操作(定义,运算)
R language ggplot2 visualization: use the ggboxplot function of the ggpubr package to visualize the grouped box plot, use the ggpar function to change the graphical parameters (caption, add, modify th
Introductory UnityShader learning (2) - the rendering pipeline
Synchronized and volatile interview brief summary
[CUDA study notes] First acquaintance with CUDA
格林美瑞交所IPO:募资3.8亿美元 更多中国企业将赴欧洲上市
基于极限学习机(ELM)进行多变量用电量预测(Matlab代码实现)
01 邂逅typescript,环境搭建
R语言ggstatsplot包ggbarstats函数可视化条形图、并添加假设检验结果(包含样本数、统计量、效应大小及其置信区间、显著性、组间两两比较、贝叶斯假设)、检验结果报告符合APA标准
SQL、HQL、JPQL 到底有什么区别
11 pinia使用
The R language ggstatsplot package ggbarstats function visualizes bar charts, and adds hypothesis test results (including sample number, statistics, effect size and its confidence interval, significan
R语言计算时间序列数据的移动平均值(滚动平均值、例如5日均线、10日均线等):使用zoo包中的rollmean函数计算k个周期移动平均值
NC | 中国农大草业学院杨高文组揭示发现多因子干扰会降低土壤微生物多样性的积极效应...
MANIFEST.MF文件(PDB文件)
Message queue data storage MySQL table design
【MySQL】Mysql范式及外键作用
TRACE32——基于SNOOPer的变量记录
2021 OWASP TOP 10 Vulnerability Guide
DBeaver连接MySQL 8.x时Public Key Retrieval is not allowed 错误解决