当前位置:网站首页>Use eventlog analyzer for log forensics analysis
Use eventlog analyzer for log forensics analysis
2022-07-26 03:12:00
【There is Xiao Deng in operation and Build a crime scene to find the root of security vulnerabilities Most of the time , The company cannot trace the network intruder who initiated the network violation . Although the best precautions have been taken to prevent attacks , But it is impossible to protect your network from any attack . All attackers will leave traces , And your event log data and syslog Data is the only factor that can help you identify the cause of violations , You can even narrow it down to tell you who initiated the violation . The log data forensics analysis report can be used as court evidence . Log analysis report Every time there is activity on the network , Contains network devices ( Such as router 、 Switch 、 A firewall 、 The server etc. ) Your network infrastructure will generate event log data and syslog data . Event log data and system log data activity records are like digital fingerprints left by everyone accessing network devices and Applications . These digital fingerprints can tell you when the network activity starts 、 What happened and who started the activity . These digital fingerprints will help you build the entire crime scene . Data fingerprint Without proper log forensics tools , Manually check your event log data and syslog Data forensics is painful and time-consuming . Besides , You need to ensure that the log data can be safely stored and not tampered , In order to conduct accurate log forensics analysis . For log forensics EventLog Analyzer EventLog Analyzer Allows you to collect 、 file 、 Search and analyze from various systems 、 Machine generated logs obtained by network devices and Applications , And generate evidence collection report ( Such as user activity report 、 System audit report 、 Regulatory compliance statements, etc ). EventLog Analyzer This log analysis and compliance reporting software can help you collect these logs for network forensics , And detect network or system abnormalities . These machine generated event logs and syslog Will be archived for future forensic analysis , It will also be encrypted to ensure that the collected system logs are not tampered with and stored safely . You can drill down into the original log events and complete the root cause analysis in a few minutes . Log analysis Use log search for forensic analysis EventLog Analyzer It is very easy to conduct forensic investigation through the following methods : It allows you to use its powerful log search engine to search both original logs and formatted logs , And according to the search results, the forensics report is generated in real time . This log forensics software allows network administrators to search the original log to accurately find the exact log entries that lead to security activities , Find the exact time when the corresponding security event occurred 、 Who starts the activity , And the place where the event was launched . EventLog Analyzer This search function of will help you quickly track network intruders , It is very useful for law enforcement departments to collect evidence and analyze . By searching the original event log , You can import archived logs and perform safety accident mining . This makes forensic investigations easier , Otherwise, this is a task that requires a lot of human effort . 版权声明



本文为[There is Xiao Deng in operation and [email protected]]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/201/202207182324568733.html
边栏推荐
- How to install with USB flash disk?
- Safety margin of mass consumption
- STM32 - PWM learning notes
- Three years of software testing experience, salary has been stuck at 10K, how to improve and develop automated testing?
- Is the galaxy VIP account opened by qiniu safe?
- dataframe整理:datetime格式分拆;删除特定行;分组整合。
- The source of everything, the choice of code branching strategy
- 实现一个方法,找出数组中的第k大和第m大的数字相加之和
- LeetCode·83双周赛·6128.最好的扑克手牌·模拟
- Machine learning foundation plan 0-2: what is machine learning? What does it have to do with AI?
猜你喜欢

Functions and usage of snownlp Library

Opencv报错:(parameter or structure field))Unrecognized or unsupported array type in functon ‘cvGetMat‘

ES6 set and map
![[Yuri crack man] brings you easy understanding - deep copy and shallow copy](/img/26/b7330c7f5fdac55c8f5e9fa24658ee.png)
[Yuri crack man] brings you easy understanding - deep copy and shallow copy
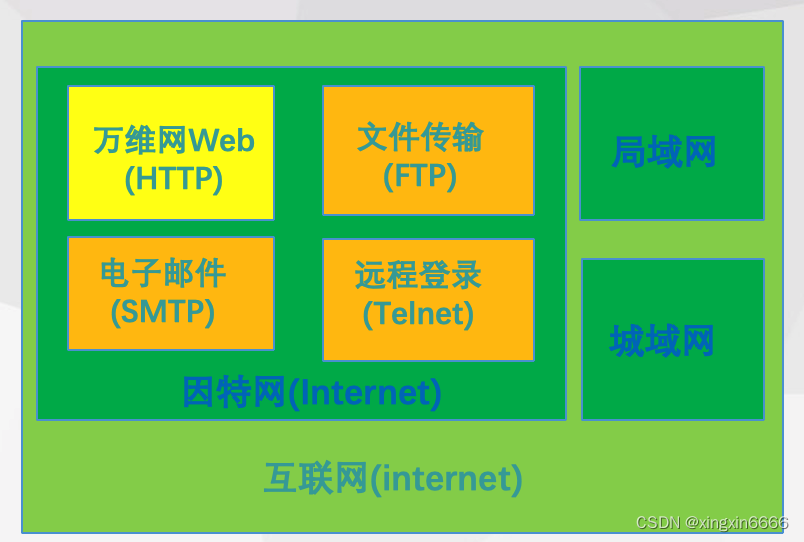
万维网、因特网和互联网的区别
![[C language] deeply understand integer lifting and arithmetic conversion](/img/5c/21d0df424c034721c64b0653edc483.png)
[C language] deeply understand integer lifting and arithmetic conversion

Leetcode · daily question · sword finger offer | | 115. reconstruction sequence · topological sorting

图解LeetCode——5. 最长回文子串(难度:中等)

Quick check of OGC WebGIS common service standards (wms/wmts/tms/wfs)

Implement a method to find the sum of the number k and m in the array
随机推荐
Usage of fuser and lsof
Canvas -- drawing of rectangle -- making of histogram
What are the methods of array sorting in JS
Swin Transformer【Backbone】
(9) Attribute introspection
Type the URL to the web page display. What happened during this period?
The difference between the world wide web, the Internet and the Internet
一篇文章让你理解 云原生 容器化相关
Pit trodden when copying list: shallow copy and deep copy
Multithreaded programming
Win11 method of changing disk drive letter
Influence of middle tap change on ZVS oscillation circuit
在混合云中管理数据库:八个关键注意事项
LeetCode·每日一题·919.完全二叉树插入器·层次遍历·BFS
规范自己debug的流程
经典面试问题——OOP语言的三大特征
JVM memory model parsing
Be highly vigilant! Weaponization of smartphone location data on the battlefield
Win11更改磁盘驱动器号的方法
万维网、因特网和互联网的区别