当前位置:网站首页>topic: Privacy, Deception and Device Abuse
topic: Privacy, Deception and Device Abuse
2022-06-30 15:46:00 【Deep safety laboratory】
边栏推荐
- Oculus quest2 | unity configures the oculus quest2 development environment and packages an application for real machine testing
- How should we understand the variability of architecture design?
- halcon变量窗口的图像变量不显示,重启软件和电脑都没用
- Curl: (23) failed writing body (1354 i= 1371) problem solving method
- linux下修改mysql密码: ERROR 1396 (HY000): Operation ALTER USER failed for ‘root‘@‘localhost‘
- A little idea about big experiment data
- Simulation of two-color ball system to judge the winning situation
- 智慧风电:数字孪生 3D 风机智能设备运维
- Phone number shielding function
- Basic literacy - four common software architectures
猜你喜欢

What would you choose between architecture optimization and business iteration?

4.4 string

Bye civil engineering, hello CS, can you change the certificate to the Blue Bridge Cup

Parameter optimization - bias and variance

Teach you a learning method to quickly master knowledge

Using asp Net core creating web API series

4.3 variables and assignments

Compare whether the two arrays are the same

Voice codec based on machine learning Agora silver: support high quality voice interaction at ultra-low bit rate
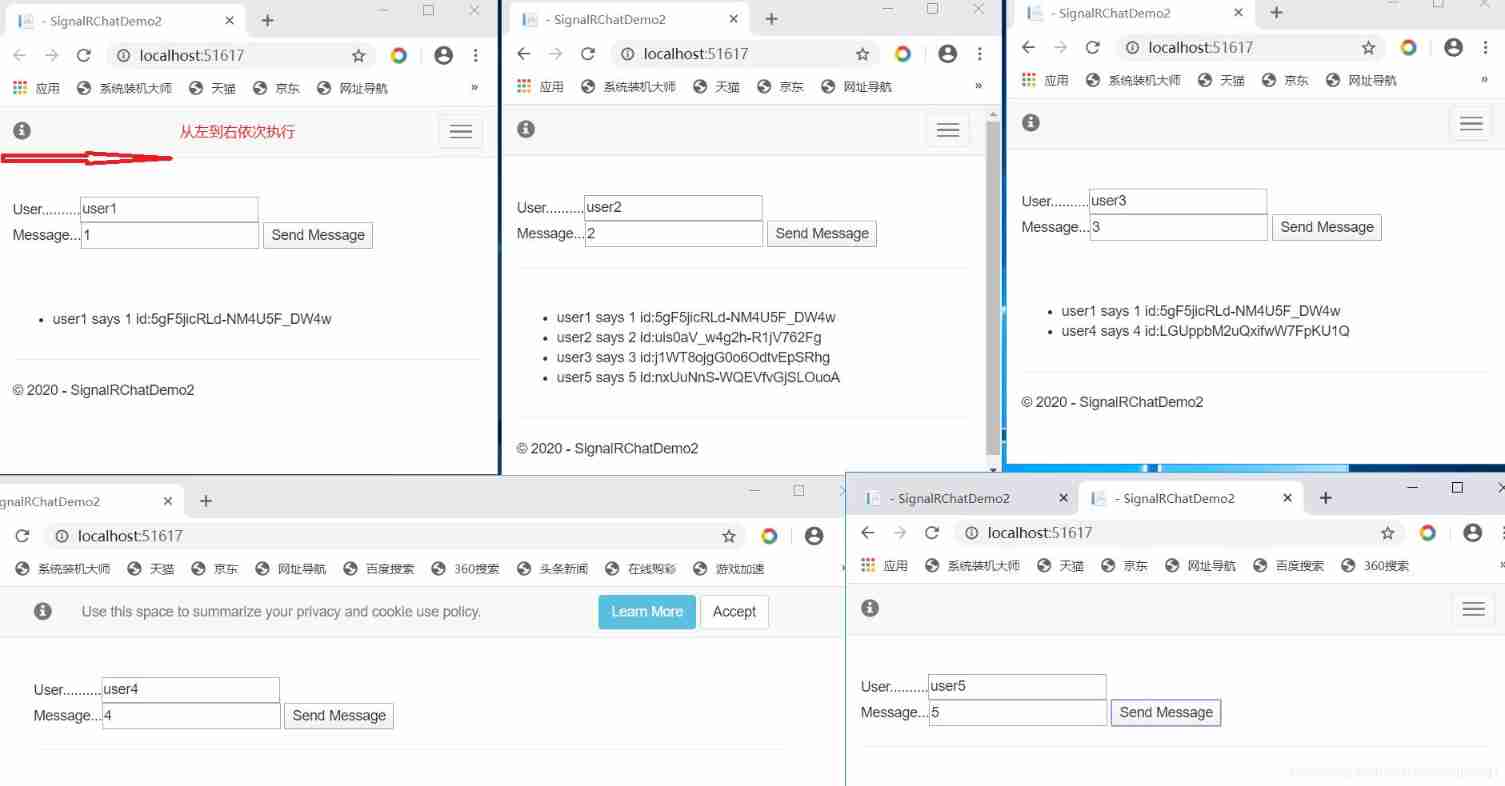
ASP. Net core signalr series hub tutorial
随机推荐
Lecun points out the direction of next generation AI: autonomous machine intelligence
Types of waveguides
Rte2021 review of the practice and the way of AI OPS landing
【子矩阵数量统计】CF1181C Flag子矩阵数量统计
The crystal ball "data insight" was officially launched: insight into the change of consumption trend and the details of interactive experience
Policy Center > Malware > Malware
Swagger's asp Net core web API help page
ADB devices cannot detect the problem of Xiaomi note 3
[ten thousand words long article] thoroughly understand load balancing
深入理解.Net中的线程同步之构造模式(二)内核模式1.内核模式构造物Event事件
国债逆回购在哪个平台上买比较安全?
Pycharm----xx. So cannot open shared object file problem solving
Npumcm selection question 3 and acmc2020a
Help you accumulate audio and video knowledge, Agora developer's roaming guide officially set sail
Modifying MySQL password under Linux: error 1396 (HY000): Operation alter user failed for 'root' @ 'localhost‘
How to browse mobile web pages on your computer
Flask Sqlalchemy - automatically export the table model (flask sqlacodegen) & no single primary key problem ---orm (8)
Policy Center-Permissions and APIs that Access Sensitive Information
数数据可视化实战案例(timeline轮播图,streamlit 控件年份 metabase可视化使用教程)2.0
Review 2021, embrace change and live up to Shaohua
