当前位置:网站首页>SSO single sign on implementation.
SSO single sign on implementation.
2022-07-02 00:41:00 【ZZ learn java well】
Login of single architecture : adopt cookie and session The conversational mechanism of .
shortcoming : The server should store login information .
sso Single sign on :
Implementation mode I : Parent domain Cookie
Before we actually implement it , Let's talk about it first Cookie Scope of action .
Cookie The scope of is defined by domain Properties and path Attributes together determine .domain The valid value of property is the domain name of the current domain or its parent domain /IP Address , stay Tomcat in ,domain Property is the domain name of the current domain by default /IP Address .path The valid value of the property is in “/” Path at the beginning , stay Tomcat in ,path Property defaults to current Web Context path of application . If you will Cookie Of domain Property to the parent domain of the current domain , Then think of it as the parent domain Cookie.Cookie There is a feature , In the parent domain Cookie Shared by subdomains , In other words , The child domain automatically inherits from the parent domain Cookie. utilize Cookie This characteristic of , It's not hard to imagine. , take Session ID( or Token) Just save it to the parent domain . you 're right , We just need to put Cookie Of domain Property to the domain name of the parent domain ( The main domain name ), At the same time Cookie Of path Property to the root path , In this way, all sub domain applications can access this Cookie 了 . However, this requires the domain name of the application system to be established under a common primary domain name , Such as tieba.baidu.com and map.baidu.com, They're all built on baidu.com Under the main domain name , Then they can achieve single sign on in this way .
shortcoming :1. The server should centrally store a large amount of login information ( use redis Realization ).
2. To share primary domain .
Implementation mode II : authentication center
Speaking of single sign on , I'm sure I'll see the term :CAS (Central Authentication Service), Now let's talk about it. CAS What happened .
If the login has been extracted as a system separately , We can still play like this . Now we have two systems , Namely www.java3y.com and www.java4y.com, One SSOwww.sso.com

First , Users want to access the system Awww.java3y.com Limited resources ( For example, shopping cart function , The shopping cart function can only be accessed after login ), System Awww.java3y.com Found that the user is not logged in , So redirect to sso authentication center , And take your own address as a parameter . The address of the request is as follows :
www.sso.com?service=www.java3y.com
sso The authentication center found that the user was not logged in , Guide the user to the login page , The user enters the user name and password to log in , The user establishes a global session with the authentication center ( Make a copy of Token, writes Cookie in , Save in browser )

And then , The certification authority redirects back to the system A, And put Token Carry the past to the system A, The redirected address is as follows :
www.java3y.com?token=xxxxxxx
next , System A Go to sso The certification center verifies this Token Whether it is right , If correct , System A Establish a local session with the user ( establish Session)( Can also be Token Store in cookie Inside , Next time you come, just call the method verification of the Certification Center ). Here we are , System A And the user is already logged in .

here , Users want to access the system Bwww.java4y.com Limited resources ( For example, order function , The order function can only be accessed after login ), System Bwww.java4y.com Found that the user is not logged in , So redirect to sso authentication center , And take your own address as a parameter . The address of the request is as follows :
www.sso.com?service=www.java4y.com
Be careful , Because before the user and authentication center www.sso.com A global session has been established ( At that time Cookie Saved to browser ), So this time the system B Redirect to the certification authority www.sso.com Yes, you can Cookie Of .
According to the information brought by the Certification Center Cookie It is found that a global session has been established with the user , The certification authority redirects back to the system B, And put Token Carry the past to the system B, The redirected address is as follows :
www.java4y.com?token=xxxxxxx
next , System B Go to sso The certification center verifies this Token Whether it is right , If correct , System B Establish a local session with the user ( establish Session). Here we are , System B And the user is already logged in .

See here , Actually SSO The certification center is like a transit station .
边栏推荐
- Is the securities account given by qiniu business school safe? Where can I open an account
- 449 original code, complement code, inverse code
- B tree and b+tree of MySQL
- Slf4j print abnormal stack information
- How can entrepreneurial teams implement agile testing to improve quality and efficiency? Voice network developer entrepreneurship lecture Vol.03
- Output results of convolution operation with multiple tensors and multiple convolution kernels
- sso单点登录的实现。
- 【opencv】train&test HOG+SVM
- 【微信授权登录】uniapp开发小程序,实现获取微信授权登录功能
- Otaku wallpaper Daquan wechat applet source code - with dynamic wallpaper to support a variety of traffic owners
猜你喜欢
Some understandings of graph convolution neural network r-gcn considering relations and some explanations of DGL official code

2022 pinduoduo details / pinduoduo product details / pinduoduo SKU details

Leetcode skimming: stack and queue 06 (top k high-frequency elements)

AIX存储管理之卷组属性的查看和修改(二)
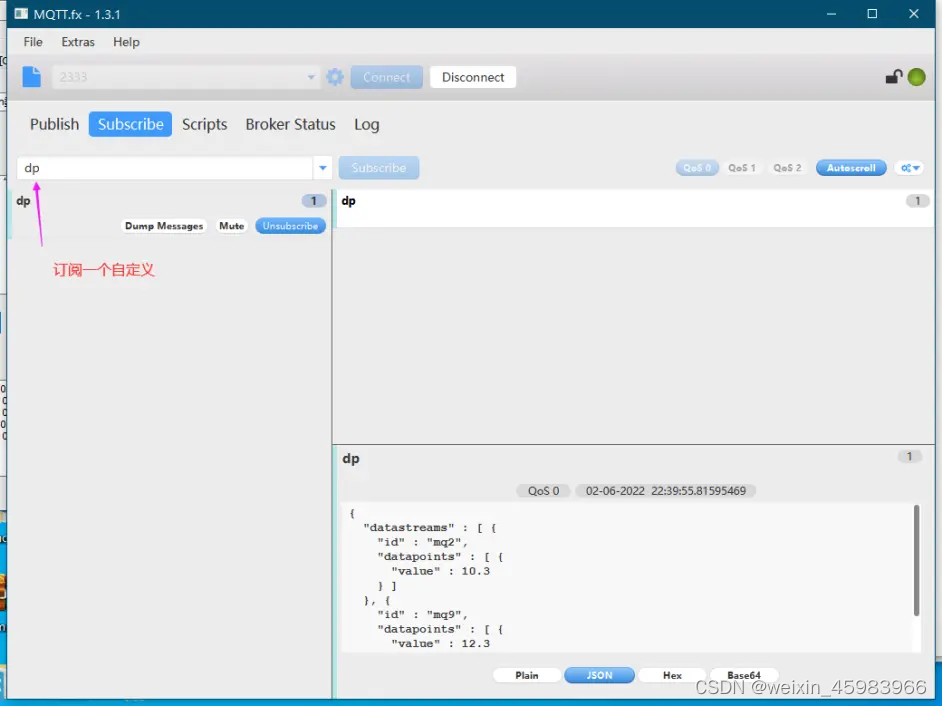
Bc35 & bc95 onenet mqtt (old)

Leetcode skimming: stack and queue 01 (realizing queue with stack)
![[wechat authorized login] the small program developed by uniapp realizes the function of obtaining wechat authorized login](/img/c1/23be4399119f42d85a7b86fc8a59fc.png)
[wechat authorized login] the small program developed by uniapp realizes the function of obtaining wechat authorized login

excel查找与引用函数
EMC circuit protection device for surge and impulse current protection
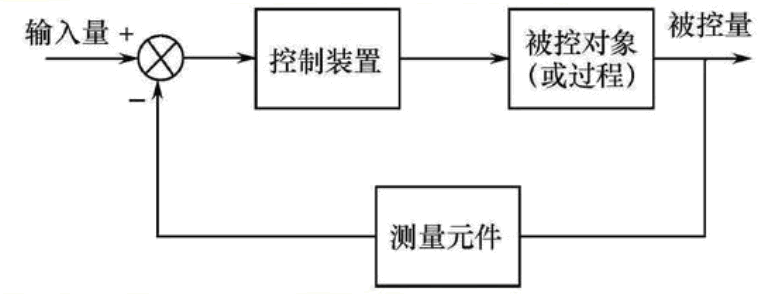
What does open loop and closed loop mean?
随机推荐
[bottom pop-up selector] uniapp picker component - scroll selector popped up at the bottom
Accelerator systems initiative is an independent non-profit organization
Node - generate wechat permission verification configuration
股票开户哪个证券公司比较安全
Schrodinger's Japanese learning applet source code
Heketi record
Ldr6035 smart Bluetooth audio can be charged and released (5.9.12.15.20v) fast charging and fast releasing device charging
【微信授权登录】uniapp开发小程序,实现获取微信授权登录功能
Leetcode skimming: stack and queue 06 (top k high-frequency elements)
Use es to realize epidemic map or take out order function (including code and data)
How to open an account for individual stock speculation? Is it safe?
Using multithreaded callable to query Oracle Database
使用 ES 实现疫情地图或者外卖点餐功能(含代码及数据)
From 20s to 500ms, I used these three methods
BPR (Bayesian personalized sorting)
UVM tutorial
Which securities company is safer to open a stock account
Leetcode skimming: binary tree 02 (middle order traversal of binary tree)
Leetcode96 different binary search trees
使用多线程Callable查询oracle数据库