当前位置:网站首页>Cisco -- an external tool for WAN's concept examination
Cisco -- an external tool for WAN's concept examination
2022-07-01 22:57:00 【ThumpBo】


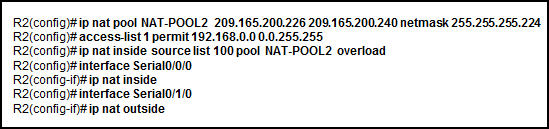
See illustration . The network administrator is PAT To configure R2. Why is the configuration incorrect ?
NAT-POOL2 Bound the wrong ACL
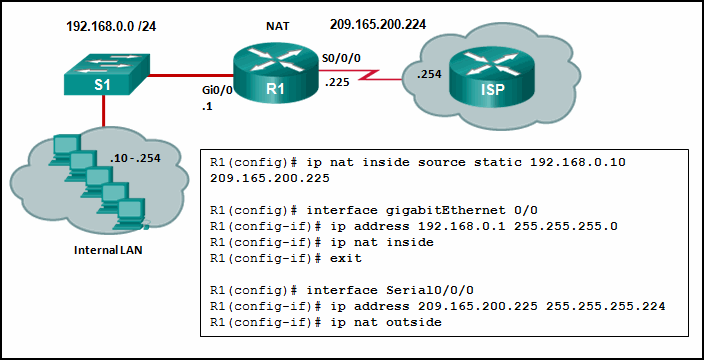
See illustration . According to the command given ,R1 How many hosts can be connected to the LAN at the same time R1 on NAT transformation ?
1
Both sides of the communication use PAT What are the disadvantages of ?
End to end IPv4 Traceability will be lost .
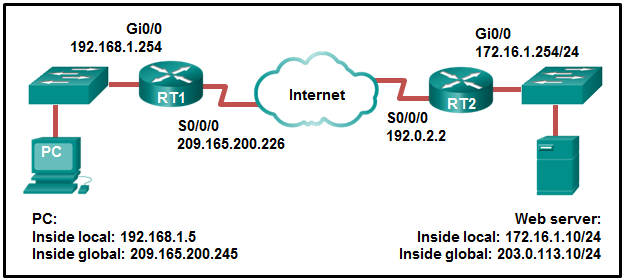
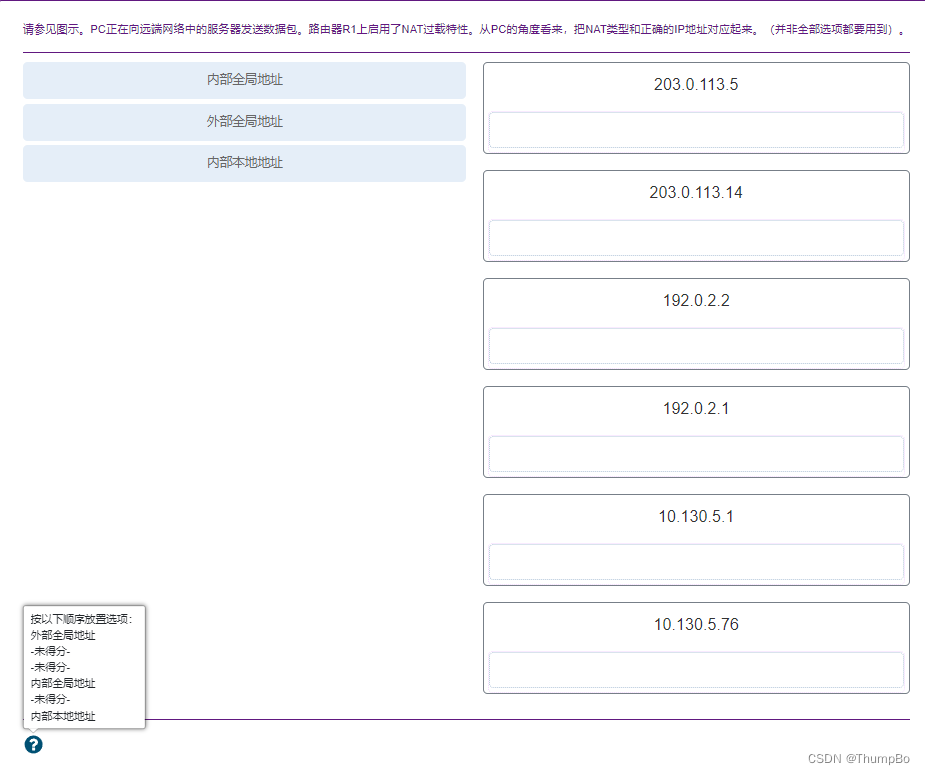
See illustration . stay RT1 and RT2 Configured NAT.PC Sending request to Web The server . Which one? IPv4 The address is RT2 And Web Packet sources between servers IP Address ?
209.165.200.245

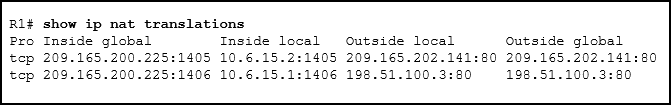
See illustration . Output information according to the displayed command , You can see what type of NAT?
Implemented using external interfaces PAT
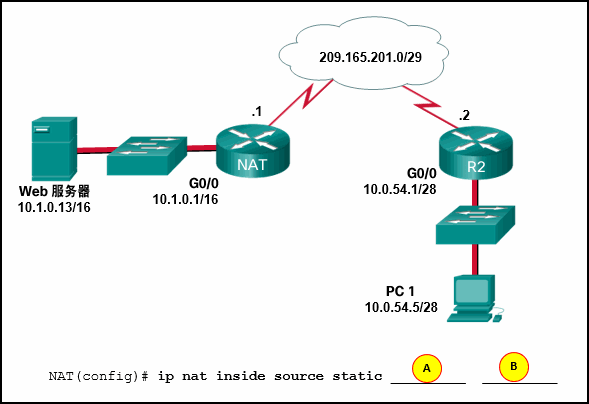
See illustration . Configure static NAT With permission PC 1 Access... On the internal network Web The server . Instead of A and B Complete static NAT What are the two addresses required for configuration ?( Choose two .)
B = 209.165.201.1
A = 10.1.0.13
** ip nat inside source list 1 pool NAT_POOL overload** In the command overload What is the use of keywords ?
Allow multiple internal hosts to share one or more internal global addresses .
See illustration . Router R1 What is the source address of the packet used to forward to the Internet ?
209.165.200.225

See illustration . Applied to routers NAT The configuration is as follows :
ERtr(config)#access-list 1 permit 10.0.0.0 0.255.255.255
ERtr(config)#ip nat pool corp 209.165.201.6 209.165.201.30 netmask 255.255.255.224
ERtr(config)#ip nat inside source list 1 pool corp overload
ERtr(config)#ip nat inside source static 10.10.10.55 209.165.201.4
ERtr(config)#interface gigabitethernet 0/0
ERtr(config-if)#ip nat inside
ERtr(config-if)#interface serial 0/0/0
ERtr(config-if)#ip nat outside
According to the configuration and output shown in the figure , Which one can determine NAT state ?
There is not enough information to determine static and dynamic NAT Is it working .
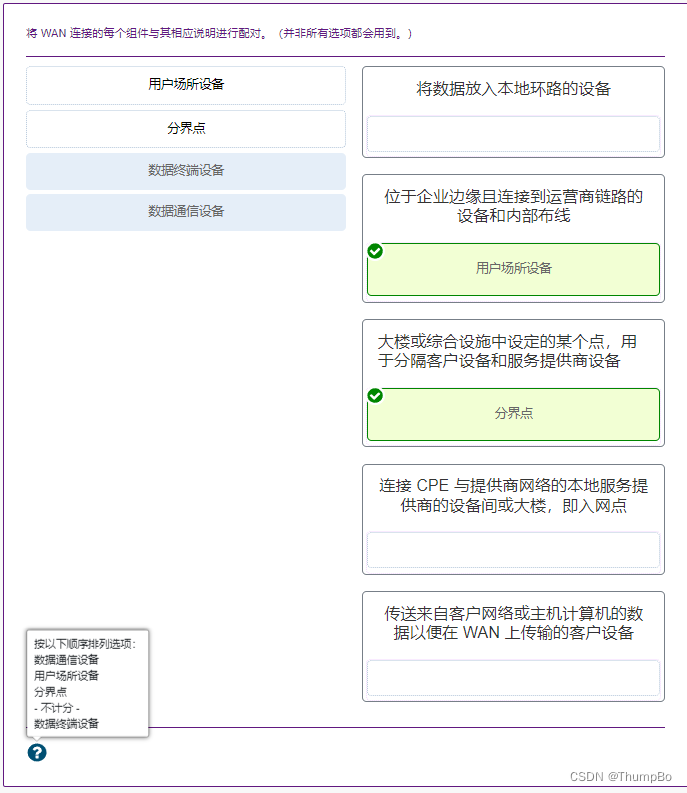
Which of the following describes the transmission of data over a WAN connection ?
Employees share data files with colleagues in branch offices on the other side of the city .
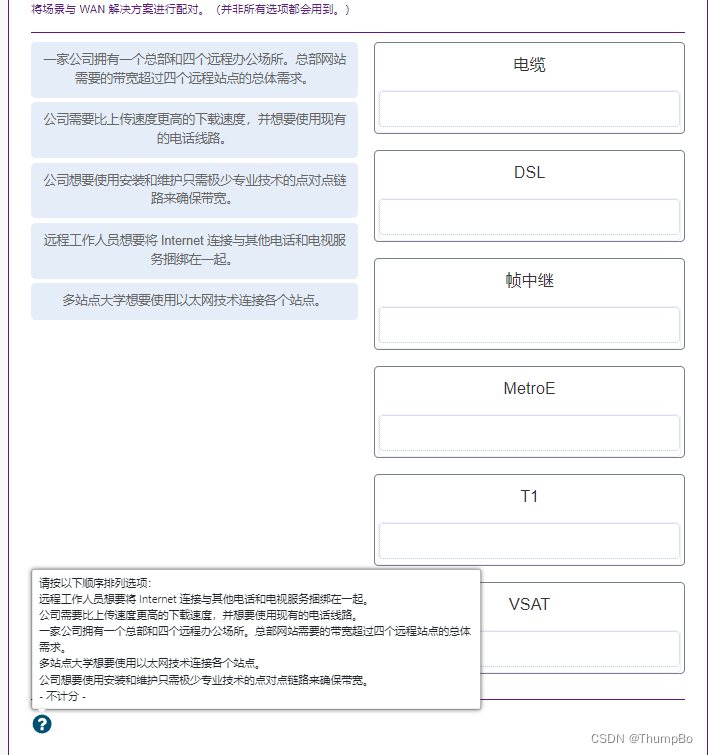
A company is considering upgrading the park WAN Connect . Which two of the following WAN Options are dedicated WAN An example of Architecture ?( Choose two .)
Leased line
Ethernet WAN
Which situation will make the enterprise decide to implement the company WAN?
When employees are distributed in many branches
Set up IPsec VPN when , Hash message authentication code (Hashed Message Authentication Code,HMAC) What is the function of the algorithm ?
Ensure message integrity
IPsec What algorithm is used to provide data confidentiality ?
AES
Which two algorithms can become IPsec Part of the strategy , Protect traffic that needs attention by providing encryption and hashing ?( Choose two .)
AES
SHA
What kind VPN The solution allows Web The browser is established to ASA Remote access security VPN Tunnel ?
No client SSL
What kind IPsec The safety function can ensure that VPN The received data has not been modified during transmission ?
integrity
Which two of the following VPN It belongs to the remote access of enterprise management VPN?( Choose two .)
No client SSL VPN
Client based IPsec VPN
Site to site VPN What you need ?
It needs to make both ends of the tunnel VPN Gateway encrypts and decrypts traffic .
NAT What will overload use to track the traffic of multiple internal hosts using the same internal global address ?
Port number
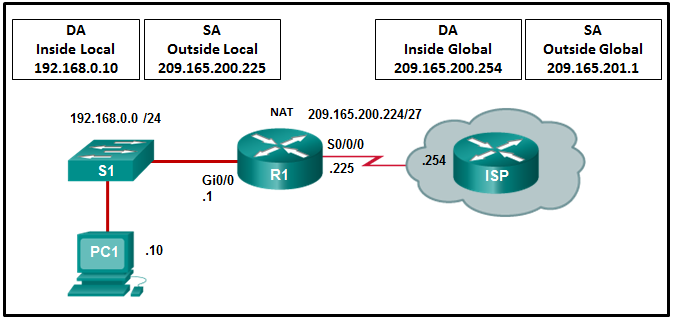
See illustration .R1 The configuration on is static NAT. Which Internet host will use IP Address to access PC1?
209.165.200.225

See illustration . The network administrator is viewing the command show ip nat translations Output information of . Which of the following correctly describes the router RT2 On going NAT transformation ?
Using static NAT To target the source IPv4 The address is 192.168.254.253, Purpose IPv4 The address is 192.0.2.88 Of traffic .
Which two of the following WAN Infrastructure services are private connections ?( Please choose two .)
Frame relay
T1/E1
Which two of the following correctly describe the relationship between LAN and WAN ?( Choose two .)
Compared with the rate of LAN connecting internal terminal devices , The bandwidth rate of Wan connected to LAN is lower
Wan usually consists of multiple ISP operating , But LAN is usually run by a single organization or individual .
Which of the following describes site to site VPN Characteristics of ?
Must be statically established .
stay VPN How to complete in “ Tunnel ”?
From one or more VPN The new header of the protocol will encapsulate the original packet .
Which of the following is true VPN Correct description of ?
VPN Use virtual connections to create private networks over public networks
Lead to PC-A What is the problem of being unable to access the Internet ?
Not properly allocated NAT Interface .
64.101.198.197 What kind of address ?
Public address
What kind of VPN Allow safe site to site VPN Send multicast and broadcast traffic ?
be based on IPsec Of GRE
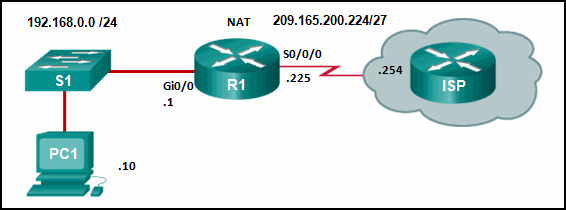
See illustration . from R1 (NAT Router ) From the perspective of , Which address is the internal global address ?
209.165.200.225
Both sides of the communication use PAT What are the disadvantages of ?
End to end IPv4 Traceability will be lost .
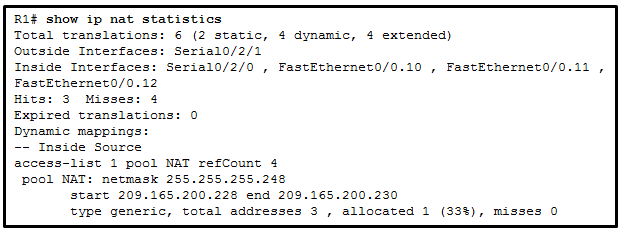
See illustration . The network administrator has just configured address translation , Validating configuration . Which three items can the administrator verify ?( Please select three items .)
Address translation works normally .
The number is 1 The standard access list of is used as part of the configuration process .
Two types of NAT.
static state NAT Which two addresses are specified in the configuration ?
Internal local and internal global
IPsec AH What are the two hash algorithms used to ensure authenticity ?( Choose two .)
MD5
SHA
Which two terminals can be used ASDM Configured ASA Intersite VPN On the other end of ?( Choose two .)
ISR Router
the other one ASA
Which two of the following technologies provide for enterprise management VPN Solution ?( Choose two .)
Intersite VPN
The remote access VPN
Diffie-Hellman Algorithm in IPsec What are the functions within the framework ?
Allow peers to exchange shared keys
128.107.240.239 What kind of address ?
Public address
That type of VPN At the same time, it supports the 2 Tier and tier 3 Layer implementation ?
MPLS VPN
Which two technologies can be classified as dedicated WAN infrastructure ? ( Choose two .)
Frame relay
MetroE
Which network situation needs to be used WAN?
Employees need to pass VPN Connect to the company email server
Which protocol creates virtual point-to-point connections , To transmit unencrypted traffic between Cisco routers through various protocols ?
GRE
10.100.126.126 What kind of address ?
Private address
10.131.48.7 What kind of address ?
Private address

See illustration . In order to complete the R1 Static on NAT To configure , Which of the following actions must be performed ?
**
Public address
That type of VPN At the same time, it supports the 2 Tier and tier 3 Layer implementation ?
MPLS VPN
Which two technologies can be classified as dedicated WAN infrastructure ? ( Choose two .)
Frame relay
MetroE
Which network situation needs to be used WAN?
Employees need to pass VPN Connect to the company email server
Which protocol creates virtual point-to-point connections , To transmit unencrypted traffic between Cisco routers through various protocols ?
GRE
10.100.126.126 What kind of address ?
Private address
10.131.48.7 What kind of address ?
Private address
[ Outside the chain picture transfer in …(img-NuoMVoUn-1655986692000)]
See illustration . In order to complete the R1 Static on NAT To configure , Which of the following actions must be performed ?
You should use ip nat outside Command configuration interface S0/0/0
边栏推荐
- Mysql database detailed learning tutorial
- 今日睡眠质量记录71分
- General use of qstringlist
- Origin2018 installation tutorial "recommended collection"
- Deep learning -- data operation
- Efficiency improvement - encourage personalized container development environment
- Lc669. Prune binary search tree
- nn.Parameter】Pytorch特征融合自适应权重设置(可学习权重使用)
- ECMAScript 2022 was officially released. Have you heard about it?
- Share some feelings of a programmer who has experienced layoffs twice a year
猜你喜欢
Turn -- bring it and use it: share a gadget for checking memory leaks

The fixed assets management subsystem reports are divided into what categories and which accounts are included

Appium automated testing foundation - Supplement: introduction to desired capabilities parameters
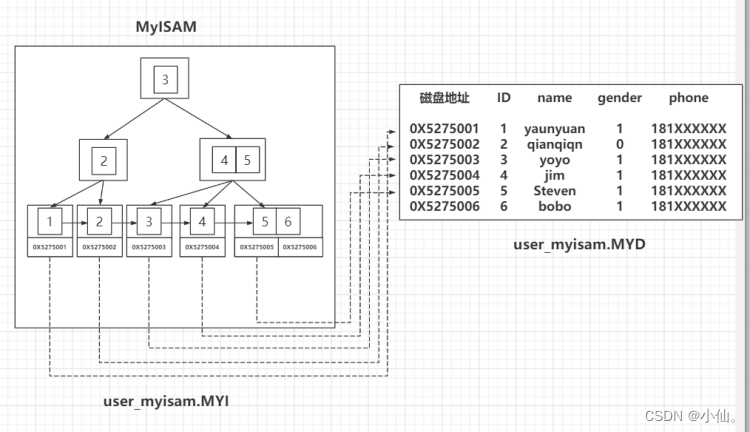
MySQL -- index of MyISAM storage engine

3DE resources have nothing or nothing wrong

Metauniverse may become a new direction of Internet development

Daily question brushing record (10)

正则系列之组和范围(Groups and Ranges)
使用 EMQX Cloud 实现物联网设备一机一密验证

思科--WAN 的概念考试外部工具
随机推荐
QStringList 的常规使用
Congratulations on the release of friends' new book (send welfare)
使用3DMax制作一个象棋棋子
MySQL -- deduction of index storage model
Understanding of indexes in MySQL
Pytorch nn.functional.unfold()的简单理解与用法
pytorch训练自己网络后可视化特征图谱的代码
rxjs Observable of 操作符的单步调试分析
There is no signal in HDMI in computer games caused by memory, so it crashes
A few minutes before work, I found out V-model and The difference between sync
聊一聊Zabbix都监控哪些参数
Multi picture alert ~ comparison of Huawei ECs and Alibaba cloud ECS
[MySQL] index classification
Talk about what parameters ZABBIX monitors
Appium automated testing foundation - Supplement: introduction to desired capabilities parameters
Turn -- the underlying debugging principle of GDB is so simple
Genicam gentl standard ver1.5 (4) Chapter 5 acquisition engine
Resttemplate remote call tool class
Appium自动化测试基础 — APPium安装(一)
Efficiency improvement - encourage personalized container development environment