当前位置:网站首页>Self cleaning Manual of mining Trojan horse
Self cleaning Manual of mining Trojan horse
2022-06-24 11:01:00 【purnus】
What is a mining Trojan horse
Mining Trojans will occupy CPU Overclocking operation , Thus, a large amount of CPU resources , Seriously affect the normal operation of other applications on the server . Hackers in order to get more computing resources , Generally, the whole network will be scanned indiscriminately , Simultaneous utilization SSH Attack the host by means of explosion and vulnerability exploitation . Some mining Trojans are worm like , After the host is successfully invaded , Mining Trojans also infiltrate the intranet , And persist on the invaded server to get the maximum benefit . The overall attack process is roughly shown in the figure below :
Two . Mining Trojan horse features
The mining Trojan will use the computing power of the host to mine without the knowledge of the user , The most obvious feature is the host CPU Be consumed in large quantities , View the virtual machine CPU There are two methods of occupancy :
1. Console instance monitoring
2. Host execution TOP command
As shown in the figure below , Through execution top command , You can see the system at that time in the returned results CPU Occupancy rate .
top -c
If your host CPU High occupancy rate , Then the host may have been implanted with a mining Trojan horse , It will affect the normal operation of other applications on the server , It needs to be checked immediately .
3、 ... and . Clear the mining Trojan horse
1. Isolate the host in time
Some mining Trojans with worm function get control of the host , Will continue to other hosts on the public network , Or use the current host as a springboard to penetrate other hosts in the same LAN , So after finding that the host is implanted into the mining Trojan horse , Without affecting the normal operation of the business , The infected host should be isolated in time , Then proceed to the next step of analysis and removal .
Tencent virtual machines can isolate hosts by setting security groups , Refer to the following links for details :https://cloud.tencent.com/document/product/215/20089
2. Block abnormal network communication
The mining Trojan horse will not only connect the ore pool , There is also the possibility of connecting hackers C2 The server , Receive and execute C2 Instructions 、 Deliver other malicious Trojans , Therefore, it is necessary to block the network in time .
(1) Check that the host firewall is currently in effect iptables Whether there are suspicious addresses and ports outside the business scope in the rule , They may be the pit of a mining horse or C2 Address
iptables -L -n
(2) from iptables Clear suspicious addresses and ports from the rules
vi /etc/sysconfig/iptables
(3) Block the network communication of the mining Trojan horse
iptables -A INPUT -s Suspicious address -j DROP iptables -A OUTPUT -d Suspicious address -j DROP
3. Clear scheduled tasks
Most mining Trojans are persistent by writing scheduled tasks to the infected host , If you just clear the mining process , It cannot be eradicated , At the preset time point , The system will plan tasks from hackers C2 The server downloads and executes the mining Trojan horse again .
The common planning task of the mining Trojan horse is to download and execute sh Script , As shown in the figure below :
You can check whether there is a suspicious scheduled task by executing the following command , If you have any , Save relevant records for subsequent analysis , Then delete :
View the scheduled tasks of the current user of the system :
crontab -l
View the scheduled tasks of a specific user of the system :
crontab -u username -l
View other scheduled task files :
cat /etc/crontab cat /var/spool/cron cat /etc/anacrontab cat /etc/cron.d/ cat /etc/cron.daily/ cat /etc/cron.hourly/ cat /etc/cron.weekly/ cat /etc/cron.monthly/ cat /var/spool/cron/
4. Clear startup items
Except for planning tasks , Mining Trojans can also be persistent by adding startup items . You can use the following command to check whether there is any abnormal startup service in the startup item .
CentOS7 The following versions :
chkconfig –list
CentOS7 And above :
systemctl list-unit-files
If a malicious startup item is found , You can close it with the following command :
CentOS7 The following versions :
chkconfig service name off
CentOS7 And above :
systemctl disable service name
in addition , You also need to carefully check the following directories and files , Delete suspicious startup items in time :
/usr/lib/systemd/system /usr/lib/systemd/system/multi-user.target.wants /etc/rc.local /etc/inittab /etc/rc0.d/ /etc/rc1.d/ /etc/rc2.d/ /etc/rc3.d/ /etc/rc4.d/ /etc/rc5.d/ /etc/rc6.d/ /etc/rc.d/
During the investigation , It can be sorted according to the file modification time , Focus on the recently created service items . As shown in the figure below , The system has recently been created with a name of bot.service Service for , The service will be started when the system is started /etc/kinsing This Trojan file , Need to be closed bot service , And delete /etc/kinsing file .
5. Clear preload so
By configuring /etc/ld.so.preload, You can customize the dynamic link library that is loaded before the program runs , Some Trojans modify the file , Add malicious so file , So as to realize the hidden and other malicious functions of the mining process .
Check /etc/ld.so.preload( The file is empty by default ), Clear the abnormal DLL . It can be executed `> /etc/ld.so.preload` Command to clear .
6. eliminate SSH Public key
Mining Trojans are often found in ~/.ssh/authoruzed_keys The hacker's... Is written in the file SSH Public key , In this way, even if the user cleans up the mining Trojan horse , Hackers can still log in to the host without secret , This is also a common means of maintaining server control .
screening ~/.ssh/authorized_keys file , If you find something suspicious SSH Public key , Delete directly .
7. Clear the mining Trojan horse
(1) Clear the mining process
The biggest feature of the mining Trojan horse is that it can be used without the user's knowledge , Use the computing power of the host machine for mining , Thus, a large amount of CPU resources , therefore , Check the system by executing the following commands CPU Process of resources .
top -c ps -ef
After confirming that the relevant process is the mining process , Follow the steps below to clear it :
Get and record the file path of the mining process :
ls -l /proc/$PID/exe
Kill the mining process :
kill -9 $PID
Delete the file corresponding to the mining process
(2) Clear other related malicious processes
Malicious processes and external C2 When communicating with the server , The port is often opened for listening . Execute the following command , Check whether the server has unauthorized ports to listen .
netstat -antp
If there are unauthorized processes , Follow the steps below to clear it :
Get and record the file path of unauthorized process :
ls -l /proc/$PID/exe
Kill unauthorized processes :
kill -9 $PID
Delete the file corresponding to the unauthorized process
You can also use the following command to check newly added files , Clear related Trojans
find /etc -ctime -2 ( The directory specified here is /etc, Get close to 2 New files within days ) lsof -c kinsing ( The file name to be viewed here is kinsing Related process information )
8. Risk investigation 、 Safety reinforcement
Conduct risk screening and security reinforcement for the system , Avoid mining Trojans making a comeback , For details, please refer to the following links :https://cloud.tencent.com/document/product/296/9604
Four . common problem
1. Mingming has just cleaned up the mining Trojan horse , It didn't take long to make a comeback ?
Many users will report that the mining Trojan horse is always not cleaned up , It is Kill The process , Deleted Trojan file , It was not long before ,CPU The occupancy rate has come up again . The essence , Or is it because the removal is not thorough enough . Most users are just Kill Mining process and corresponding documents , Without cleaning up scheduled tasks and daemons .
It is generally recommended to clear the scheduled tasks first 、 Start item 、 Daemon , Then clear the mining process and other malicious processes .
2. How to determine whether a suspicious process is a malicious process ?
As shown in the figure below , Unknown process kinsing Monitor local 31458 port , Very suspicious , It can be determined by the following methods :
(1) perform `ls -al /proc/$PID/exe` Confirm the file corresponding to the suspicious process ;
(2) If the file has not been deleted , Then upload the file directly to Virustotal To test , Or calculate the corresponding md5, Use md5 Go to Virustotal The query ; If the file has been deleted , Executable `cat /proc/$PID/exe > /tmp/t.bin` Process dump Go to a specific directory , Then upload the file to Virustotal Or calculate dump File corresponding md5 To Virustotal The query . If multiple anti-virus engines are detected at the same time , That basically determines that the process is a malicious process .
Virustotal Address :https://www.virustotal.com/gui/s
3. Why the system CPU The occupancy rate is close to 100%, But I can't see which process caused it ?
As shown in the figure below , System CPU The occupancy rate is close to 100%, But I can't see which process caused it , This is usually because the system command has been tampered with by the Trojan horse , Thus hiding the trace of the Trojan horse process , Make it impossible for users to conduct traceability analysis .
There are many ways to tamper with commands , They are as follows :
(1)top The source file has been tampered with , The malicious process information is filtered and returned
Restore by executing the following command :
rm -rf /usr/bin/top && mv /usr/bin/top.original /usr/bin/top
【 Related articles 】https://blog.csdn.net/chenmozhe22/article/details/112578057
(2) Tamper with preload so file ,ls、top、ps And other commands have been hijacked by the dynamic link library of the Trojan horse , Unable to get information about the Trojan horse process
Restore by executing the following command :
> /etc/ld.so.preload && rm -rf malice so File path
【 Related articles 】https://cloud.tencent.com/developer/article/1744547
(3) Tamper with system commands by other unknown means
Try the following two solutions respectively :
i. Copy command source files from other systems of the same version to the current system for overwriting ; You can use uname -a Command to view the current system version ;
ii. Or install busybox To troubleshoot the system .busybox It's an integration 300 Many are most commonly used Linux Software for commands and tools , have access to busybox Check the system instead of the system command ;
yum -y install wget make gcc perl glibc-static ncurses-devel libgcrypt-devel wget http://busybox.net/downloads/busybox-1.33.0.tar.bz2 tar -jxvf busybox-1.33.0.tar.bz2 cd busybox-1.33.0 && make && make install
【 Related articles 】https://www.cnblogs.com/angryprogrammer/p/13456681.html
Ongoing update ...
边栏推荐
- Learn to use the kindeditor rich text editor. Click to upload a picture. The mask is too large or the white screen solution
- Detailed explanation of SQL Sever basic data types
- Petit guide de construction rapide du bras mécanique (II): application du bras mécanique
- [IEEE publication] International Conference on natural language processing and information retrieval in 2022 (ecnlpir 2022)
- Many of my friends asked me what books and online classes I recommended. This time, I contributed all the materials that I had been hiding for a long time (Part 1)
- Distribute proofs of manuscripts by scanning
- What is recursion?
- What is the bin file for? How to open the file correctly
- Attribute observer didset and willset in swift of swiftui swift internal skill
- Redis
猜你喜欢

使用Process Monitor工具监测进程对注册表和文件的操作
![[JS reverse sharing] community information of a website](/img/71/8b77c6d229b1a8301a55dada08b74f.png)
[JS reverse sharing] community information of a website
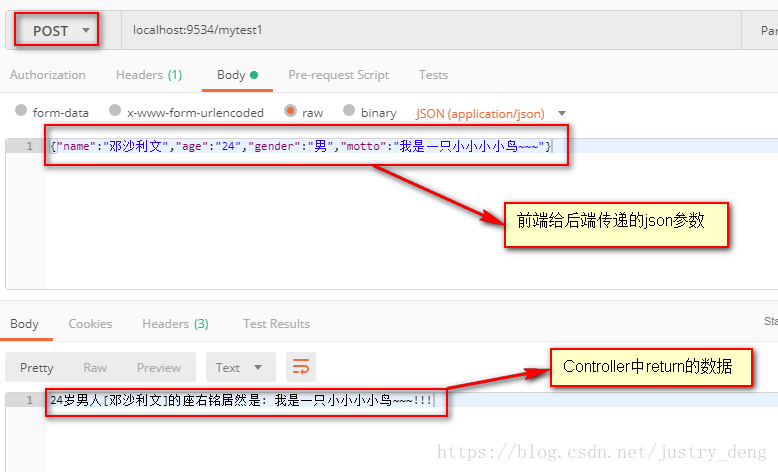
@RequestBody注解

Thread operation principle

Rising bubble canvas breaking animation JS special effect
Quick completion guide for mechanical arm (zero): main contents and analysis methods of the guide

Quick completion guide for manipulator (III): mechanical structure of manipulator

Any 与 TypeVar,让 IDE 的自动补全更好用

今日睡眠质量记录76分

Programmers spend most of their time not writing code, but...
随机推荐
Which map navigation is easy to use and accurate?
Rising bubble canvas breaking animation JS special effect
How does easydss use go fastdfs distributed file servers to reduce service pressure?
09. Tencent cloud IOT device side learning -- RRPC and behavior
Tencent's open source project "Yinglong" has become a top-level project of Apache: the former long-term service wechat payment can hold a million billion level of data stream processing
SQL Server about like operator (including the problem of field data automatically filling in spaces)
Svg+js drag slider round progress bar
[activities this Saturday] NET Day in China
Niuke-top101-bm28
26. delete duplicates of ordered array
126. word Solitaire II BFS
Which is a good CAD drawing software? How to select good software
Cook a delicious cli
Differences among cookies, session, localstorage and sessionstorage
[data analysis data source] coordinates of provinces, cities and administrative regions across the country (including boundary coordinate points and central coordinate points)
Self service troubleshooting guide for redis connection login problems
Plant growth H5 animation JS special effect
Several stacks of technology sharing: product managers' Online Official answers to several stacks of knowledge
Tencent wetest platform will bring new benefits in 2021 with 618 special offers!
程序员在技术之外,还要掌握一个技能——自我营销能力