当前位置:网站首页>Detailed explanation of dos and attack methods
Detailed explanation of dos and attack methods
2022-06-26 17:49:00 【lmn_】
DoS And attack methods
0x01 DOS Introduction to the attack
DoS(Denial of Service)
DoS Also known as denial of service , cause DoS Is known as DoS attack , Its purpose is to make the computer or network unable to provide normal services , The most common DoS Attacks include computer network broadband attacks and connectivity attacks .
DoS Attack refers to the intentional attack on the defects of the network protocol implementation or the brutal exhaustion of the resources of the attacked object directly through barbaric means , Causes the target system service system to stop responding or even crash , This attack does not include intrusion into the target server or network device .

These service resources include network bandwidth , File system space capacity , An open process or allowed connection . The problem is network bandwidth , Such attacks can lead to a shortage of resources , No matter how fast the computer processes 、 What is the memory capacity 、 The speed of network bandwidth cannot avoid the consequences of this kind of attack .
Common flooding attacks
- Buffer overflow attack : The most common DoS attack , The idea is to send a lot of traffic to a network address .
- ICMP flooding : Take advantage of misconfigured network devices by sending fraudulent packets , These packets ping Every computer on the target network , Not just a specific computer . Then trigger the network to amplify the traffic . This attack is also called death ping.
- SYN flood: Send a request to connect to the server , But the handshake was not completed . Until all open ports are saturated with requests .
0x02 Distributed denial of service attacks DDoS
DDoS(Distributed denial of service attack)
DDoS Also known as distributed denial of service attack , Many computers can be attacked at the same time , Make the target of the attack unusable , Distributed denial of service attacks have occurred many times , As a result, many large websites are unable to operate .

A complete DDoS The attack system is made up of attackers 、 Main control end 、 The agent and the target are composed of four parts .
The master and agent are used to control and actually launch attacks respectively , The master only issues commands and does not participate in the actual attack , The agent sends DDoS The actual attack packet .
For computers on the master and agent side , The attacker has control or partial control , During the attack, it will use various means to hide itself from others . Once the real attacker transmits the attack command to the master , An attacker can shut down or leave the network , The master sends the command to each proxy host .

This allows attackers to evade tracking , Each attack proxy host will send a large number of service request packets to the target host , These packets are disguised , It's impossible to identify its source , And the services requested by these packets often consume a lot of system resources , As a result, the target host cannot provide normal services for users . It even causes the system to crash .
DDoS classification

0x03 DoS Attack process
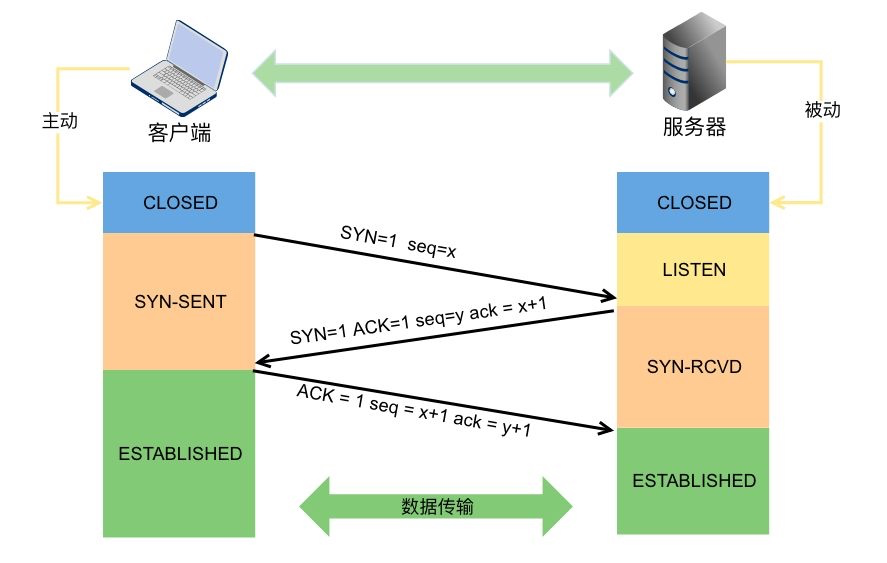
Picture address :https://hmurl.cn/aHk40hhW
Before the sender , Will first send a synchronization packet to the receiver (SYN), The receiver returns a synchronization packet (SYN), An answer packet (ACK), Then the sender sends a reply packet (ACK) Respond
When the connection status is in “ Half a connection ” In the state of , received SYN The package has not been received yet ACK Connection at package time , That is, those who have not yet completed three handshakes TCP Connect . If you keep sending something like “ Half a connection ” Status packets , This will cause a large number of server resources to be occupied , And occupy network bandwidth .
0x04 Common attacks
SYN Flood attack
By destroying the complete TCP/IP Three handshakes of the connection session , Detailed see 0x03.
smurf attack
smurf An attack is a virus attack , With the program that originally launched this attack “Smurf” Named after the ,smurf Attacks also belong to dos attack , It's a flooding attack , Use the victim's IP Address as source IP Address forgery broadcast ping, In combination with IP Deception and ICMP The reply method makes a lot of network transmission flood the target system , Cause the target system to refuse to service the normal system .
smurf Attack detection :
- ICMP Response to storm detection
- The increase of message loss rate and retransmission rate
- Unexpected connection resets often occur
fraggle attack
fraggle Belong to dos attack ,fraggle Use UDP port 7 and 19 instead of smurf The attack uses ICMP, forge IP The address to send .
When not necessary , Turn off the broadcast address feature of the router or firewall , And filter it out on the firewall UDP message , And prevent the destination port or source port number from being 7 or 19 Of UDP A message through .
Death ping
(pingofdeath)DengKelen
“PingofDeath” It's a test that deliberately produces deformities Ping(PacketInternetGroper) package , Claim to be bigger than ICMP ceiling , That is to use an oversized ping package , The loaded size exceeds 64KB ceiling , Make unprotected network system memory allocation error , Lead to TCP/IP Protocol stack crash , Finally, the receiver goes down , Now dead ping Packages are not common .
Teardrop attack
Teardrop attack is a kind of denial of service attack , It is the attacker who takes advantage of TCP/IP The protocol stack implementation cannot be restored IP The information in the fragments to achieve their own attacks . That is, the forgeries sent overlap with each other IP Packet packets , The receiving host is difficult to reassemble .
This attack can be carried out by TCP/IP In the protocol stack, the code is reorganized in pieces bug To disable different operating systems
Land(LandAttack) attack
LAND attack
The attacker used the victim's IP Address as source address and destination address , By sending carefully constructed spoofing packets , Send fake
SYN Packets to victims , I keep responding , Cause the target equipment without corresponding protection mechanism to be paralyzed .
Reference:
Baidu Encyclopedia _ The world's leading Chinese encyclopedia
边栏推荐
- Quantitative contract system development analysis case - detailed explanation of contract quantitative system development scheme
- Necessary decorator mode for 3 years' work
- 分布式缓存/缓存集群简介
- ZCMU--1367: Data Structure
- #26class中get和set设置
- Platform management background and merchant menu resource management: Design of platform management background data service
- 【万字总结】以终为始,详细分析高考志愿该怎么填
- Several key points in divorce agreement
- 解决pycharm里面每个字母占一格空格的问题
- 14《MySQL 教程》INSERT 插入数据
猜你喜欢

Troubleshooting ideas that can solve 80% of faults!

LeetCode——226. 翻转二叉树(BFS)

RSA概念详解及工具推荐大全 - lmn

Viewing the task arrangement ability of monorepo tool from turborepo

Notes on flowus

并发之线程安全

Vscode usage - Remote SSH configuration description

vutils.make_grid()与黑白图像有关的一个小体会

The king of Internet of things protocol: mqtt

When I was in the library, I thought of the yuan sharing mode
随机推荐
How does Guosen Securities open an account? Is it safe to open a stock account through the link
[recommendation system learning] recommendation system architecture
Strength and appearance Coexist -- an exclusive interview with Liu Yu, a member of Apache pulsar PMC
深层次安全定义剖析及加密技术
Here comes the hero League full skin Downloader
Tsinghua & Shangtang & Shanghai AI & CUHK proposed Siamese image modeling, which has both linear probing and intensive prediction performance!
陈强:阿里千亿级大规模数字商业知识图谱助力业务增长
股票开账户如何优惠开户?现在在线开户安全么?
Uncover the secret of Agora lipsync Technology: driving portraits to simulate human speech through real-time voice
I want to know. I am in Zhaoqing. Where can I open an account? Is it safe to open an account online?
The king of Internet of things protocol: mqtt
KDD 2022 | how to use comparative learning in cross domain recommendation?
丰富专业化产品线, 江铃福特领睿·极境版上市
halcon之区域:多种区域(Region)特征(5)
请指教同花顺开户选选择哪家券商比较好?现在在线开户安全么?
【Unity】在Unity中使用C#执行外部文件,如.exe或者.bat
SIGIR 2022 | 港大等提出超图对比学习在推荐系统中的应用
[buuctf.reverse] 126-130
Distributed Architecture Overview
Rich professional product lines, and Jiangling Ford Lingrui · Jijing version is listed