当前位置:网站首页>Oauth2.0 series blog tutorial summary
Oauth2.0 series blog tutorial summary
2022-07-26 07:22:00 【smileNicky】
OAuth2.0 brief introduction
OAuth 2.0 It's the most popular authorization mechanism , Used to authorize third-party applications
OAuth It's an open protocol , Allow users to let third-party applications access the user's website in a safe and standard way , Secret resources stored on mobile or desktop applications ( Such as user's personal information , Photo , video , contact list ), Instead of providing a user name and password to a third-party application .
OAuth 1.0 agreement (RFC5849) Release as a guidance document , It's the work of a small community .
This standardized specification is in OAuth 1.0 Build on your deployment experience , It also includes other use cases as well as from the broader IETF Scalability requirements collected by the community .
OAuth 2.0 The protocol is not backward compatible OAuth 1.0. These two versions can coexist on the network , Implementers can choose to support them at the same time .
OAuth2.0 Official documents
Official website :https://oauth.net/2/ , There are only English documents on the official website , You can also refer to the translated documents , link :OAuth2 RFC6749 Chinese translation
OAuth2.0 In terms of security, it has made a great improvement , Simply speaking OAuth2.0 It's an authorization agreement , Can be used to authorize , Feel free to click on a website , This kind of website is shown in the picture , Users don't want to register , You can use wechat 、 Alipay login , It's just that scenes are very common , It's also OAuth2.0 Application 
OAuth2.0 principle
OAuth2.0 It's a kind of authorization mechanism , Normal condition , Don't use OAuth2.0 And so on , The client can directly access the resources of the resource server , For users to access data safely , In the middle of the visit Access Token Mechanism . The client needs to carry Access Token To access protected resources . therefore OAuth2.0 Ensure that resources are not accessed by malicious clients , Thus, the security of the system is improved .
OAuth2.0 flow chart
Use the official pictures to introduce OAuth2.0 Overall process :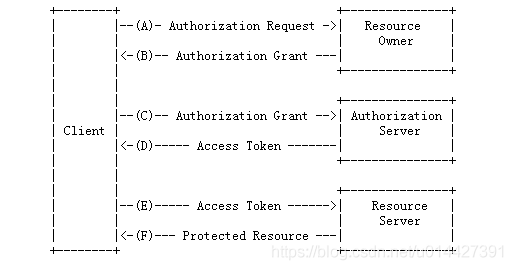
- (A) The client requests authorization from the resource owner .
- (B) The client receives the license , The resource owner grants authorization to the client ( For example, authorization code code)
- (C) The client authenticates with the authorization server and presents the authorization permission ( For example, authorization code code) Request an access token .
- (D) The authorization server verifies the client's identity and verifies the authorization permission , If valid, an access token is issued (accept token).
- (E) The client requests the protected resource from the resource server and presents the access token (accept token) Authentication .
- (F) Resource server authentication access token (accept token), If valid, the request is satisfied .
OAuth2.0 Role
OAuth2.0 Define the following roles :
quote OAuth2 RFC6749 Chinese translation :
- Resource owner (Resource Owner): An entity that can grant access to protected resources . When the resource owner is an individual , It's mentioned as an end user .
- The user agent (User Agent): Refers to some channels authorized by resource owners . Generally speaking, it means browser 、APP
- client (Client) An application that uses the authorization of the resource owner to initiate a request for a protected resource on behalf of the resource owner . The term “ client ” Not specifically any specific implementation feature ( for example : Whether the application is on the server 、 On a desktop or other device ).
- Authorization server (Authorization Server): After the resource owner is successfully verified and authorized, an access token is issued to the client's server .
The interaction between the authorization server and the resource server is beyond the scope of this specification . The authorization server can be the same server as the resource server , It can also be separate individuals . An authorization server can issue access tokens accepted by multiple resource servers .- Resource server (Resource Server): The server hosting the protected resource , Ability to receive and respond to requests for protected resources using access tokens .
OAuth2.0 Authorization mode
OAuth2.0 Yes 4 Authorization mode :
- Authorization code mode (authorization code)
- Simplified mode (implicit)
- Password mode (resource owner password credentials)
- Client mode (client credentials)
One of the most commonly used is the authorization code model ,4 A detailed introduction of the authorization mode can refer to teacher Ruan Yifeng :OAuth 2.0 Four ways of
Series getting started
- OAuth2.0 The basic concept and operation process of the series ( One )
- OAuth2.0 Series of authorization code mode practice tutorial ( Two )
- OAuth2.0 Series of practical tutorials on simplified patterns ( 3、 ... and )
- OAuth2.0 Series of practical tutorials on password mode ( Four )
- OAuth2.0 Series of client mode practice tutorials ( 5、 ... and )
- OAuth2.0 Series of information database storage tutorials ( 6、 ... and )
- OAuth2.0 Information of series Redis Storage practices ( 7、 ... and )
- OAuth2.0 Use of series JWT Token practice tutorial ( 8、 ... and )
Application practice
边栏推荐
- Hands on practice - teach you how to make an intelligent fish tank with STM32
- I don't understand the MySQL 57 version under centos7 when I encounter a problem. I was informed by big Shen who knows it
- Singles cup web WP
- Opencv learning warp Perspective
- anaconda安装教程-手把手教你安装
- How to convert multi row data into multi column data in MySQL
- MySQL安装教程-手把手教你安装
- NFT digital collection system development: Huawei releases the first collector's digital collection
- Opencv learning drawing shapes and text
- NFT数字藏品开发:数字藏品助力企业发展
猜你喜欢

Opencv learning warp Perspective

MySQL安装教程-手把手教你安装

【一库】妙啊!这个库组织npm脚本简直爆炸!

No .egg-info directory found in xxx\pip-pip-egg-info-mq

Image annotation software reference

QT: list box, table, tree control

Apache dolphin scheduler & tidb joint meetup | focus on application development capabilities under the development of open source ecosystem

HCIP---MPLS详解和BGP路由过滤

Summer Challenge harmonyos - hamster game based on arkui (JS)

PR subtitle production
随机推荐
The interface automation test with a monthly salary of 12k+ takes you to get started in 3 minutes
From scratch, we will completely develop an online chess game [Gobang] Based on websocket, and only use dozens of lines of code to complete all the logic.
OAuth2.0系列博客教程汇总
Apache dolphin scheduler & tidb joint meetup | focus on application development capabilities under the development of open source ecosystem
Examples of financial tasks: real-time and offline approval of three scenarios and five optimizations of Apache dolphin scheduler in Xinwang bank
中国联通改造 Apache DolphinScheduler 资源中心,实现计费环境跨集群调用与数据脚本一站式访问
Compose text and icon splicing to realize drawableleft or drawableright
Usage of unity3d object pool
Business secret series -- Talking about the evaluation of commercial passwords from the perspective of Party A and Party B (I)
How can man Bang write a new footnote to the value of the industry's first social responsibility report?
NFT digital collection system development: Huawei releases the first collector's digital collection
Apache dolphin scheduler 2.x nanny level source code analysis, China Mobile engineers uncover the whole process of service scheduling and start
PostgreSQL sequence create alter nextval Curval numerical interval gap
IDEA快捷键
6. Combined data type
4. Data integrity
【Keras入门日志(3)】Keras中的序贯(Sequential)模型与函数式(Functional)模型
NFT digital collection system development: digital collections give new vitality to brands
Typora免费版下载安装
单身杯web wp