当前位置:网站首页>Record of the 25th week
Record of the 25th week
2022-06-25 04:34:00 【3ackr0d】
1、 Through a htb Infiltrating learning linux command
1.1 ssh command
ssh There are two ways to connect , One is password , Second, public key login
ssh [email protected] [-p] # ssh The default port is 22, If there are changes , use -p Parameters Appoint
Public key login process
- ssh-keygen Creating public and private keys
-tSpecify the encryption type-fSpecify the generated file name - ssh-copy-id Upload the public key to the server /.ssh/authorized_keys
-iSpecify the public key file - ssh -i Private key file [email protected]
ssh-keygen -t rsa -f 3ackr0d
ssh-copy-id -i 3ackr0d [email protected]
ssh -i 3ackr0d [email protected]
Be careful : You can only log in with public key , You can change the configuration file
#/etc/ssh/sshd_confing
PasswordAuthentication Change it to no
1.2 ln command
Full name :make links between files, ln What is taken is link Two letters of
Utilization method :
ln On link Downloaded files ( Public key ) and /root/.ssh/authorized_keys, And then you can use it ssh With root Identity login
ln
-s Build soft links , Note that the source file name must be an absolute path
-f If the destination file exists , that -f Parameter will overwrite the target file
1.3 echo command
Output content
-n Get rid of echo The following newline character -e Backslash escape takes effect
Single quotation marks 、 Double quotes 、 The difference without quotation marks
- The contents in single quotation marks are output intact
- Inside the double quotation marks
$\`( The quotation marks ) It will work - Not using quotation marks will explain everything
1.4 base64
Carry on the content base64 Encoding and decoding
echo -n hello | base64
echo -n hello | base64 -d #-d Parameter is decode
2 python Write program debugging
When executing the program use python -i target.py Enter the interactive interface
dir() # Look at the built-in methods
边栏推荐
- CTF_ Web: Advanced questions of attack and defense world expert zone WP (15-18)
- CTF_ Web:php weak type bypass and MD5 collision
- Gbase 8s stored procedure syntax structure
- 讲座记录《惯性导航的新应用——惯性测量》
- Value transfer between parent and child components of wechat applet
- 515. 在每个树行中找最大值 / 剑指 Offer II 095. 最长公共子序列
- Numpy NP tips: squeeze and other processing of numpy arrays
- GBASE 8s的隔离级别介绍
- CMD operation MySQL in Windows
- GBASE 8s的触发器
猜你喜欢

Basic use of OBS browser+ browser

Intel 13th generation core showed its true colors for the first time: 68mb cache improved significantly

什么是存储引擎以及MySQL常见的三种数据库存储引擎

UCLA | generative pre training for black box optimization
单元测试覆盖率
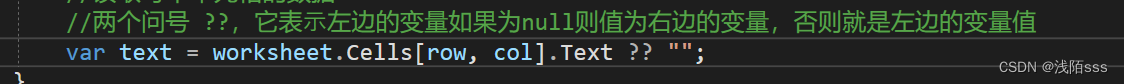
Record small knowledge points

讲座记录《捷联惯导解算的历史及发展》

CTF_ Web:php weak type bypass and MD5 collision

CTF_ Web:8-bit controllable character getshell

Nodejs 通过Heidisql连接mysql出现ER_BAD_DB_ERROR: Unknown database 'my_db_books'
随机推荐
Cascading deletion of gbase 8s
GBASE 8s 索引B+树
SQL injection details
OBS Browser+浏览器的基本使用
Finereport displays and hides column data according to conditions
GBASE 8s存储过程执行和删除
unity Quad剔除背面并剔除透明部分的shader
Nodejs connects to MySQL through heidisql, and ER appears_ BAD_ DB_ ERROR: Unknown database 'my_ db_ books'
CTF_ Variable coverage in web:php
Lecture record: history and development of strapdown inertial navigation solution
BSC smart contract dividend mainstream currency | including marketing wallet | deflation | reflow | dividend free token | available for direct deployment
Lecture record: data processing methods and applications of various spatial geodetic techniques
Gbase 8s parallel operation problem scenario description
冰冰学习笔记:循环队列的实现
CMD operation MySQL in Windows
深度学习——几种学习类型
GBASE 8s的隔离级别介绍
记录小知识点
机器学习深度学习——向量化
What is data persistence?